Welcome back, friends! Many times, businesses, friends, and family will lock their zip files with a password to keep their files secure. It is reasonable, and understandable. Well, thanks to hackers, there are many ways to get past this wall of security.

With each day that dawns, there is a new, major hack that makes the news headlines. If you are paying attention, there are usually numerous hacks each day and far more that never make the news or are kept private by the victims. Every so often, a hack is so important that I feel compelled to comment on it here to help us learn something about the nature of hacking and IT security. This is one of those cases. Last week, the U.S. Office of Personnel Management (OPM) revealed that they had been ...
Keeping expensive mobile devices safe and secure is a priority for most of us, but the process of repeatedly unlocking a phone or tablet can seem like a pointless task. This leads to disabling the lock screen altogether, especially when in a safe place (e.g., home, office, car, etc.).

Most of you already know that a zero-day exploit is an exploit that has not yet been revealed to the software vendor or the public. As a result, the vulnerability that enables the exploit hasn't been patched. This means that someone with a zero-day exploit can hack into any system that has that particular configuration or software, giving them free reign to steal information, identities, credit card info, and spy on victims.

Welcome back, my budding hackers! When we are looking for ways to hack a system, we need a specific exploit to take advantage of a certain vulnerability in the operating system, service, or application. Although I have shown you multiple ways to exploit systems here in Null Byte, there are still many more exploits available that I have not yet shown you.

There's a lot of personal information residing on your phone, possibly even more than on your computer, so it's only a matter of time before someone tries to access it.

Welcome back, my fledgling hackers! The database is the hacker's "pot-of-gold," as it contains information that is very valuable to both the business and the hacker. In this, the second of my series on hacking databases, we're on the "hunt" for Microsoft's SQL Server. Although far from the most commonly used database (Oracle hold's that title), Microsoft's SQL Server is very often found in small-to-medium sized businesses. Even a few big businesses use it.

Welcome back, my greenhorn hackers! Continuing with my Wi-Fi hacking series, this article will focus on creating an invisible rogue access point, which is an access point that's not authorized by the information technology staff and may be a significant security vulnerability for any particular firm.

Welcome back , my fledgling hackers! Lately, I've been focusing more on client-side hacks. While web servers, database servers, and file servers have garnered increased protection, the client-side remains extremely vulnerable, and there is much to teach. This time, we'll look at inserting a listener (rootkit) inside a PDF file, exploiting a vulnerability in Adobe's Reader.

Do you ever wonder how all these celebrities continue to have their private photos spread all over the internet? While celebrities' phones and computers are forever vulnerable to attacks, the common folk must also be wary. No matter how careful you think you were went you sent those "candid" photos to your ex, with a little effort and access to public information, your pictures can be snagged, too. Here's how.

It's no secret that there's a lot of surveillance going on these days. It's easier than ever to end up in a database, and even former government agents are speaking out about the atrocious amount of spying being done against our own citizens. They've targeted our laptops, cars, IP addresses, and now they're coming for our iPhones. AntiSec hackers managed to get their hands on a list of over 12 million Apple UDIDs (Universal Device IDs) from an FBI computer, and they published 1,000,001 of the...

Dress up Johnny Knoxville as his old man counterpart. He then needs to strip down to his underwear at a MLB or soccer game and streak across the field. If possible he should really bring a walker and hold it out while he is scrambling from security. Most people wont know who he is, but it will be a huge hit with all of us fans who will recognize him immediately and be thrilled with the opportunity to see a prank in action without being able to interfere with the filming.

Half-hitches are great knots, but only when use in combination with other knots. By itself, a half-hitch is unsafe and unreliable, but when joined with other knots, can be quite the opposite. Tying two half hitch knots together is great for attaching a rope or line to any object. The half hitch and double half hitch are used throughout specialities, most notably as a boating knot, outdoor knot, and paddling knot.

Check out our video walk-through of part one of the final boss encounter in Resident Evil 5! This includes lots of game spoilers.

The figure eight follow through boating knot is one of the strongest knots. (also can be used for paddling). It is generally rated at 70% - 75% of rope strength. Due to it's strength and the fact that it is easy to visually inspect, it is commonly used by climbers as their "tie-in knot" - the knot that connects the climber to the rope. It forms a secure non-slip loop at the end of a rope. For even greater security, finish the tag end with a backup knot such as one side of the double fisherman...

Video: . Recycle your hard drive into a hidden flash memory device that only you know how to turn on and use in secret. This DIY hack project allows you to recycle your broken hard drives back to life and turn them into something useful.

Another week has passed on the online battlefield as the CISPA legislation continues to grind away at our freedom. Here at Null Byte, we try to keep our community informed and knowledgeable at the same time—and that means creating content for them to learn from.

Representative Henry A. Waxman is in charge of California’s 30th Congressional district. He is part of the House Energy and Commerce Committee. Ever since he began his career in the government business, he has been involved with health and environmental issues. He represents cities such as Santa Monica, Beverly Hills, Agoura Hills, Calabasas, Hidden Hills, Malibu, Westlake Village and West Hollywood, as well as such areas of Los Angeles as Beverly-Fairfax, Pacific Palisades, Brentwood, Beverl...

Here's another delicious Byte. Ucha Gobejishvili, a Georgian Security Researcher under the handle of longrifle0x, discovered two cross site scripting (XSS) vulnerabilities on the official website of Forbes. He discovered the hole in two different locations on the site, and has already informed the website of the vulnerability.

In Linux, all password hashes are normally stored using the MD5 hashing algorithm in the /etc/shadow file, but MD5 is algorithmically weak due to collision vulnerabilities. The new recommended standard are the higher level SHA-2 hashing algorithms, SHA256 or SHA512. As a friend pointed out to me, Ubuntu is currently the only distro implementing SHA-2 as the default. With SHA-2, your passwords take an unreasonably larger amount of time to calculate. This will greatly decrease how many password...

Hideo Kojima is one of the biggest names in Japanese game design. He's the man behind every Metal Gear game, each of which has been beautiful but divisive. He's an auteur, a rarity in AAA game design, managing business, design, and programming for Kojima Productions. Last week he made a rare public appearance at the USC School of Cinematic Arts, which contains the school's video game programs, and gave a 90-minute talk about his career, influences, and the specifics of his new Fox game design...

Lifehacker posts an article on the art of cracking weak passwords, courtesy of Internet standards expert, CEO of web company iFusion Labs, and blogger John Pozadzides. Pozadzides certainly knows a thing or two about password logic. (Note: this information is not intended to hack into accounts, but rather to protect you from using weak passwords).

On the latest iOS software, your iPhone comes with significant privacy and security enhancements to protect your data even more than Apple did before. From safeguarding your iPhone to passcode-protecting files to making it easier to browse the web safely, there's a lot you need to know and start using.

With the nation facing a shortage of ventilators for COVID-19 patients and no apparent ramp-up in the production of new ones, engineers, medical resistents, and do-it-yourselfers are sharing plans for homemade versions.

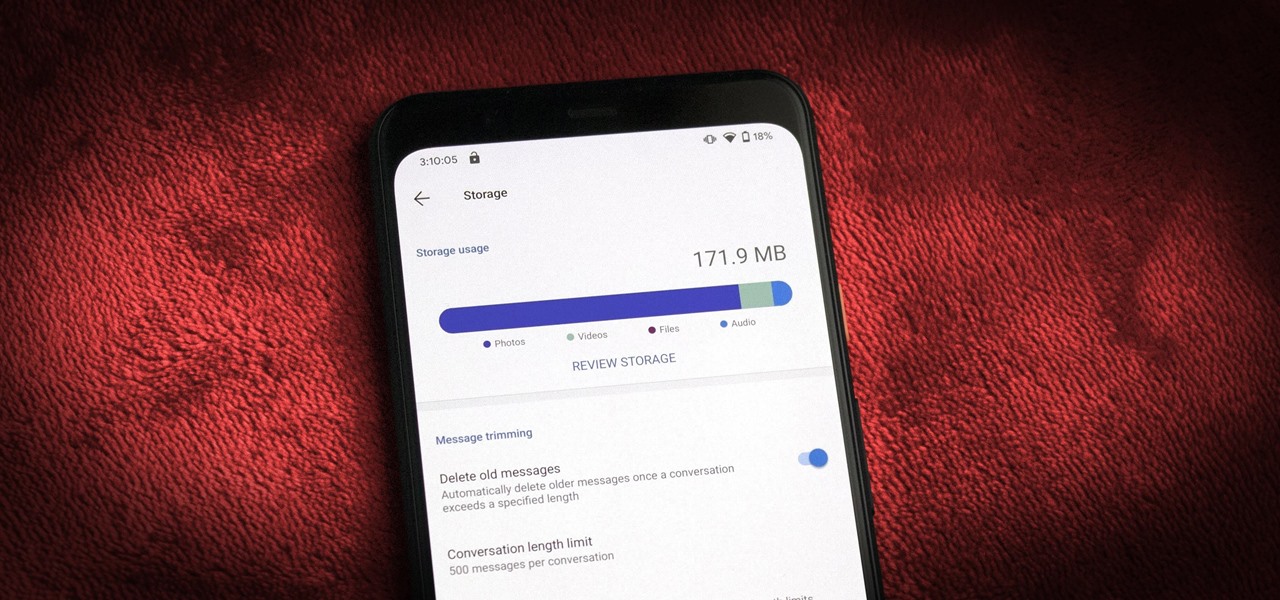
Thanks to backups, Signal conversations can span over multiple years and multiple phones. These archives can get rather large as you share photos, videos, and other files with friends. But between the other apps and large files on your phone, you might not be able to afford to keep all those messages.

As fun as Twitter is, it can also quickly turn scary. Anonymous, aggressive, and troll accounts can attack you for your tweets and stalk your every move. While you could make your profile private and block users, there are lesser-known privacy and security features that you can switch to improve your safety online.

As long as you're on the internet, you can be hacked. With an estimated 2.65 billion social media users, these apps are prime targets for hackers.

It's been proven that hackers can manipulate your screen with fake taps through specific exploits, so they can potentially hit the "Grant" button when you get a superuser request. This is the last thing you'd want to happen since the malicious app from that point forward has full system privileges. Luckily, using a fingerprint to lock your superuser requests can prevent this.

With HoloLens 2 (hopefully) just around the corner, Microsoft has announced that it will no longer be providing any major operating system updates to the original HoloLens.

Firewall solutions for macOS aren't impervious to attacks. By taking advantage of web browser dependencies already whitelisted by the firewall, an attacker can exfiltrate data or remotely control a MacBook, iMac, Mac mini, or another computer running macOS (previously known as Mac OS X).

Apple's Gatekeeper security software for macOS (Mac OS X) is vulnerable to remote attacks up to version 10.14.5. An attacker that's anywhere in the world can exploit MacBooks and other Mac computers by sharing a single ZIP file.

By far the most significant development for AR in the coming months and years — the development that will drive AR adoption — will be our reliance upon the AR cloud.

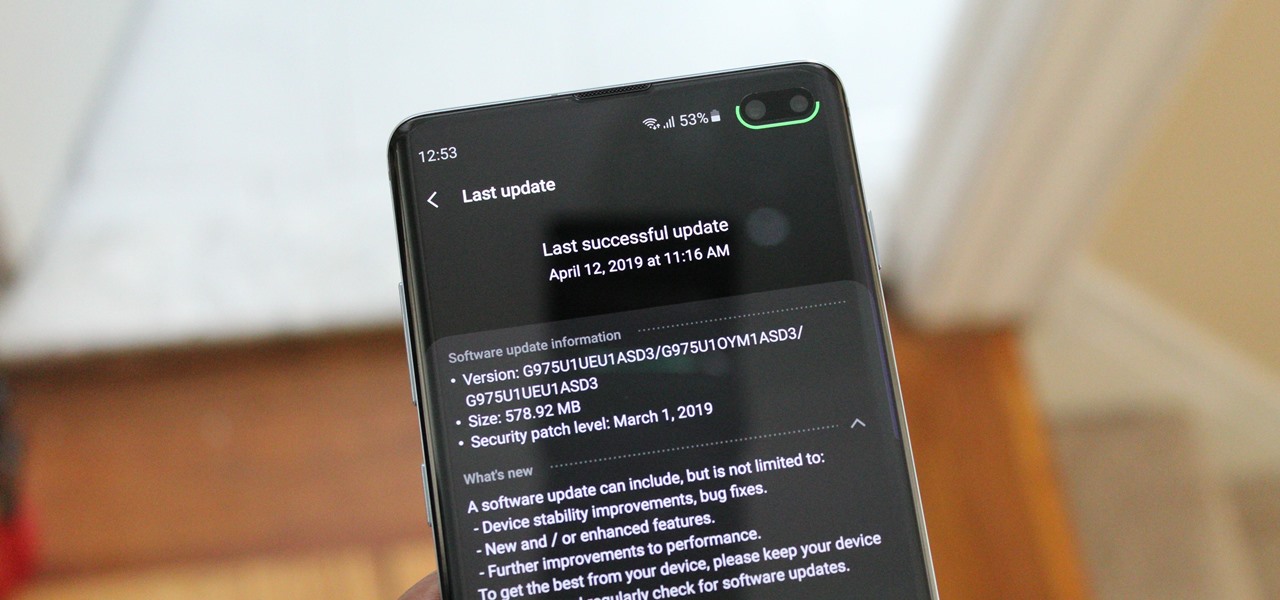
The Galaxy S10 is one of the best phones in years from world's largest smartphone OEM. With its astonishing display, new UI, and top-tier cameras, there isn't much to complain about. The one major gripe we've had is the in-display fingerprint scanner and just how slow it is. Thanks to a recent update, it just got a whole lot faster.

Whether we like it or not, our personal information and smartphones are tied together at the hip. The former needs the latter to deliver a personalized experience that matches our individual needs. This personal data, however, makes your phone a prime target for thieves of all sorts to turn your privacy into illicit profit.

There have been concerns with how much personal information Google tracks and all the things they know about us. Of course, that's what makes Google services so useful, they can use that information to cater to each of us individually. So yes, it serves a purpose, but it's not great for personal data security.

Switching phones has never been easier. Google backs up most of your app data on the cloud, which can then be restored onto your new phone. Sadly, Signal doesn't use this feature since it could compromise your security. Instead, Signal stores encrypted backups locally, requiring a bit of work to restore these messages.

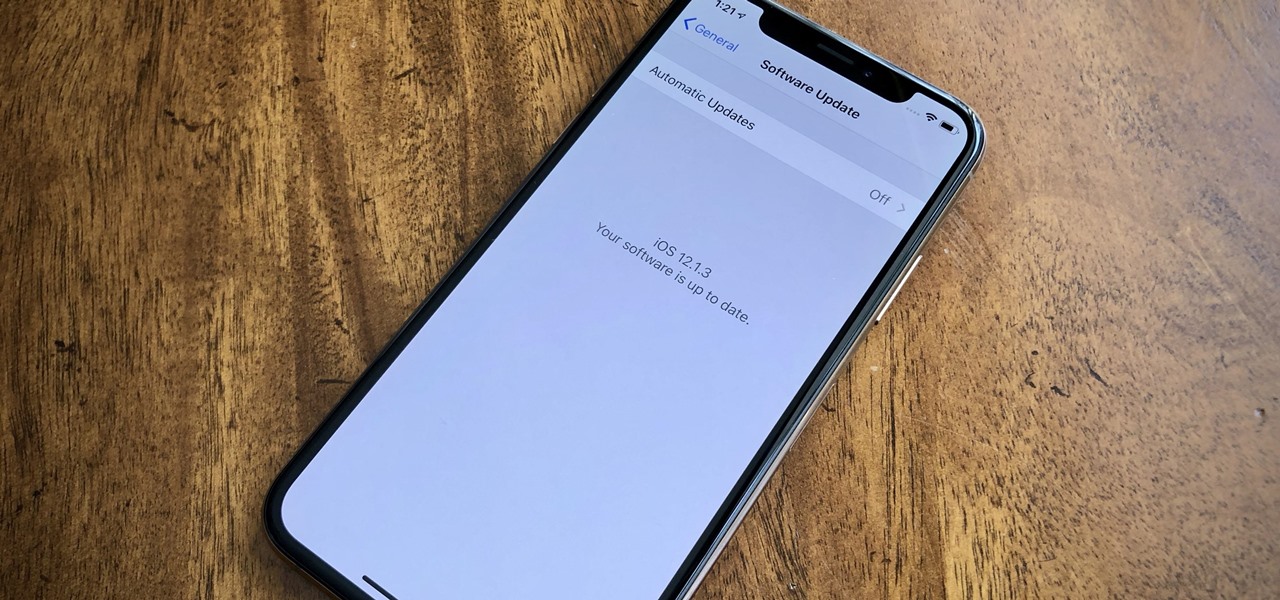
Just after a month of testing, iOS 12.1.3 has been released for iPhones. Like the previous iOS 12.1.2 update, there's not much to get excited about. There are no new features discovered yet, but there are a few fixes for issues with photos in Messages, imperfect pics when using the share sheet, and disconnecting CarPlay.

In the business world, it's sometimes said that "where there's smoke, there's fire." At Snapchat parent company Snap, Inc., it appears the equivalent of smoke is executive turnover.

QR codes have become a staple in our everyday lives. Companies use them for everything from marketing promotions to movie tickets thanks to security they provided for these types of transactions. But for years, Android users had to download an app to scan these codes. Well, not anymore.