
How To: Set up two monitors on one computer
This video will show you how to connect two monitors to one computer for more work space and comfortability.


This video will show you how to connect two monitors to one computer for more work space and comfortability.

Does your video camera not have a headphone jack? This cool idea enables you to use a pair of headphones to monitor what your video camera is hearing in real time.

The video is a demonstration of how to get your nose pierced by yourself at home. The things you are going to need for this are a sterile needle, rubbing alcohol, cotton swab, rubber gloves, a nose ring, ice cubes, eraser and of course pain tolerance. The lady also tips you to first numb your nose with ice cubes if you wish and it helps a lot. Then she asks you to put on the gloves, take the cotton swab and put some rubbing alcohol on it and then clean the inside and outside area where you ar...

So you want to know what that person who is always on their phone is up to? If you're on the same Wi-Fi network, it's as simple as opening Wireshark and configuring a few settings. We'll use the tool to decrypt WPA2 network traffic so we can spy on which applications a phone is running in real time.

We are most certainly not machines. We all need some downtime every once in a while to set our sanity scales back in balance, which in turn, makes us more productive workers. This is a premise that several forward-thinking employers fully understand, but these types of companies are few and far between in corporate America.

Welcome back, my aspiring hackers! In many of my earlier tutorials, I mentioned the complementary nature of hacking and forensics. Both disciplines, hacking and forensics, benefit from a knowledge of the other. In many cases, both disciplines will use the same tool. In this tutorial, we will use another tool that can be used in either discipline—Sysinternals—a suite of tools developed by Mark Russinovich.
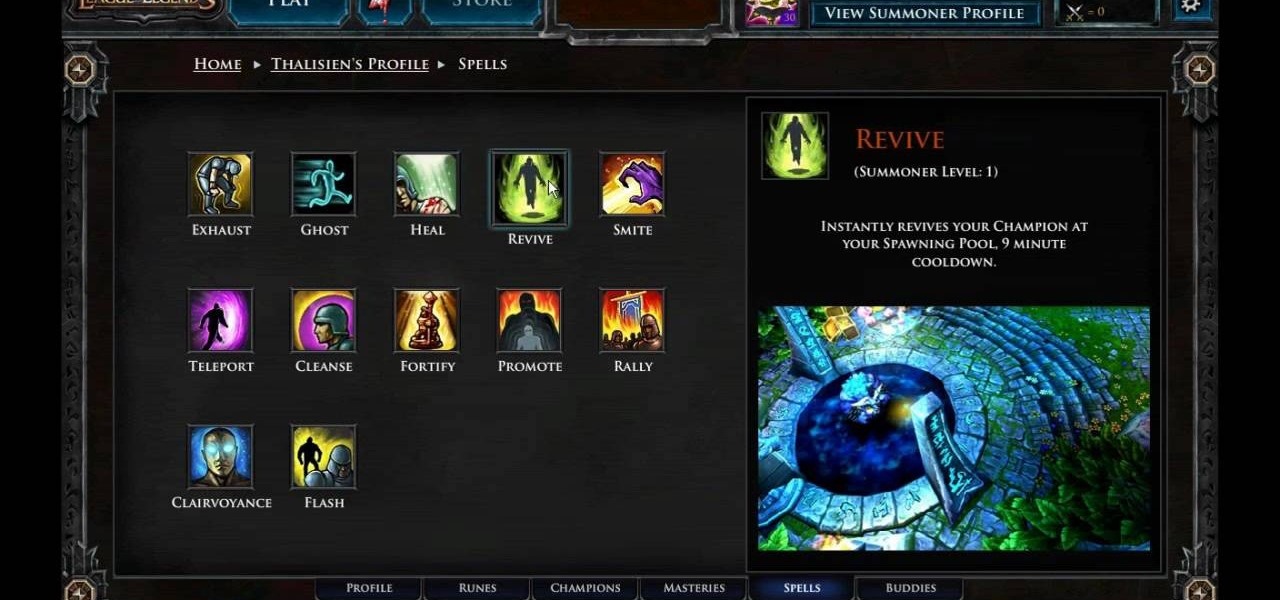
Your summoner is the core character in your League of Legends game, the one who summons the champions to fight on your behalf on the Fields of Justice. Going screenshot by screenshot, the summoner aspect of the game is explained. Stay up to date on your score, monitor your champions and keep track of your points!

Micro misters allow for low volume of water over a wide area. They give good moisture coverage. Systems can be pulled up, changed and made into what you need it to be. Keep potted plants separate from other plants. They should have their own system. There is a system to encourage growth of root systems of various plants. Shrubs get two emitters in case one clogs up, the plant still has moisture. Having the water at the base of the plant limits weed growth. There is a temporary system to get t...

Absinthe and caviar have extremely strong, distinctive flavors that many folks can't handle easily on their own, but adrenaline rush connoisseurs will get a kick out of the recipe presented in this video. Combining absinthe with caviar, you'll make a distinctive tasting caviar.

Identify pinion needle scaleWe are going to look at this insect because eggs are being laid. Two year old needles are being cast off. This is a sign of infestation. There is also sparse, open foliage. This tends to be a chronic infestation. The insect is the pinion needle scale. You can see tiny, bean shaped bumps on the 2 year old needles. The insects move to last years new growth and feast on the sap of the needle all summer. You can see egg masses and web on the trunk of the tree. The inse...

Long-time packeteer Bob Bruninga, WB4APR, developed the Automatic Packet Reporting System (APRS), which allows packet radio to track real-time events. It deviates markedly from the usual message- and text-transfer activity. Instead, APRS concentrates on the graphic display of station and object locations and movements.

Projectors can be pretty pricey. 1080p projectors even worse. If that isn't reason enough for you to build your own, then what is? Systm shows you the complete, detailed process of building your own 1080p HD projector, so pay attention and take some notes!

If you've gone through the process of refilling your ink cartridges and your printer still isn't printing, don't get your hair in a bunch, watch this video! This video will give you some tips on how to get that old print cartridge working again for your Brother MFC-240C. This video uses rubbing alcohol and soft cloth.

If you’re a dancer, athlete or just breaking in a new pair of shoes you know that blister can add pain and discomfort long after they’re formed. By keeping a blister sterile and away from further friction you can get your blister to heal quickly.

In this video we are given a brief history followed by an extremely detailed procedure on the art of tie dying. We are shown each step, everything from drawing your own designs to applying small amounts of alcohol to your artwork. After everything has been soaked in water a final tie shirt has been created. A project perfect for the kids considering it has a safe and easy to understand procedure that would finish with a beautiful piece of art in merely minutes.

Always smudge when using Copics? This tutorial takes you through how to use Copics, alcohol-based markers, by applying the specific pigment-ink evenly throughout so to not smudge when coloring.

This tutorial is set-up for the novice or beginning body painter or face painter, giving step by step instructions on how to body paint a dragon on someone's leg. Paint colors needed include blue, white, black, red, yellow, gold sparkles and green. Materials are a must and include: A plastic plate or pallet, brushes, make-up or body paint, rubbing alcohol, paper towels, and a model over 18 (with at least one leg).

Useful biking video that shows how to clean your disc brakes. Best thing to use is rubbing alcohol.

Want to get some free drinks at a bar? Learn how to with this trick, needing: 2 coins, and 2 shots, 1 of them filled with alcohol. This trick is being able to not touch either of the glasses and not dropping the coins.
I have owned quite the plethora of electronics in my life. A commonality between most of these devices' screens is frozen or dead pixels. This is probably the most annoying thing about buying new hardware—your LCD, or worse, LED display has one or more pixels that continues to stay lit. Most of the time, this will appear in the form of a brightly colored pixel that never changes, or a pixel that never displays the right color. Once you notice it's there, you just can't stop staring at it. It ...
If you've rooted your Motorola Droid chances are that you are enjoying the results, but are concerned about the consequences if you phone updates or in any way become incapacitated since your phone manufacturer will not be pleased with what you've done to the phone. One way to ameliorate these fears is to back up your phone. This video will show you how to use Nandroid to make a backup of your rooted phone.
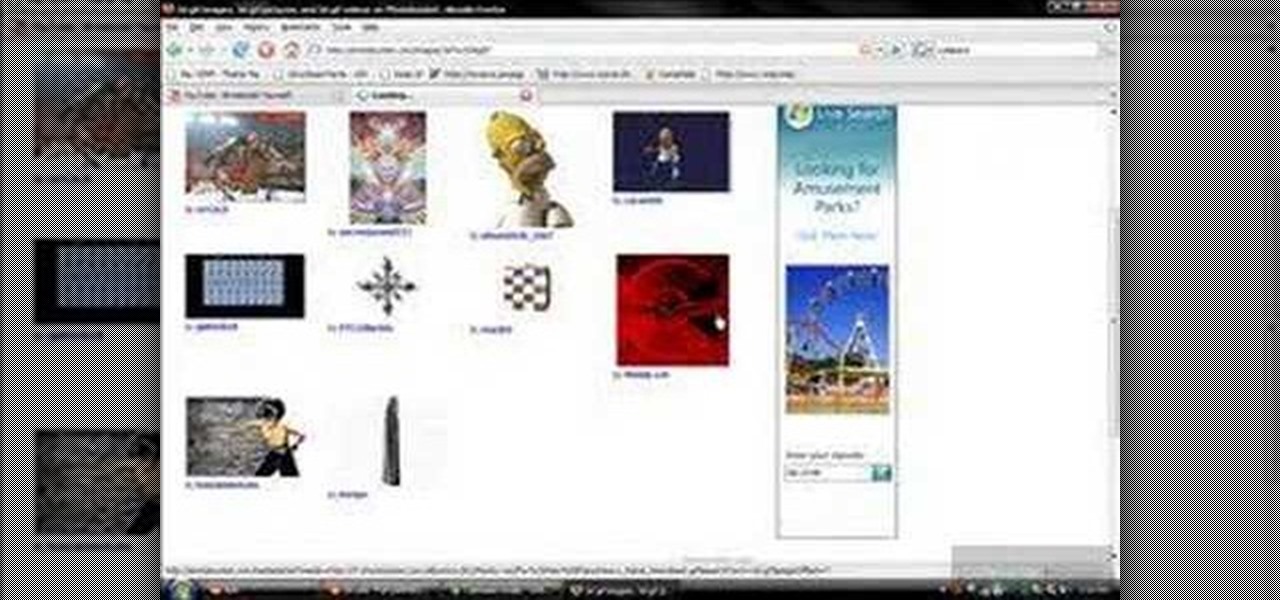
First of all you have to go to Photobucket. In the search option you have to type in '3d gif''. Now click 'search'. You shall get a number of photos and you can select the image that has red color moving screen. It is better to get image this way without a virus. Now you have to right click on the image and save as '3d image animation wallpaper' and click save and then save it on your desktop. Now right click on your desktop and click on the properties. Now go to the desktop and then select ‘...
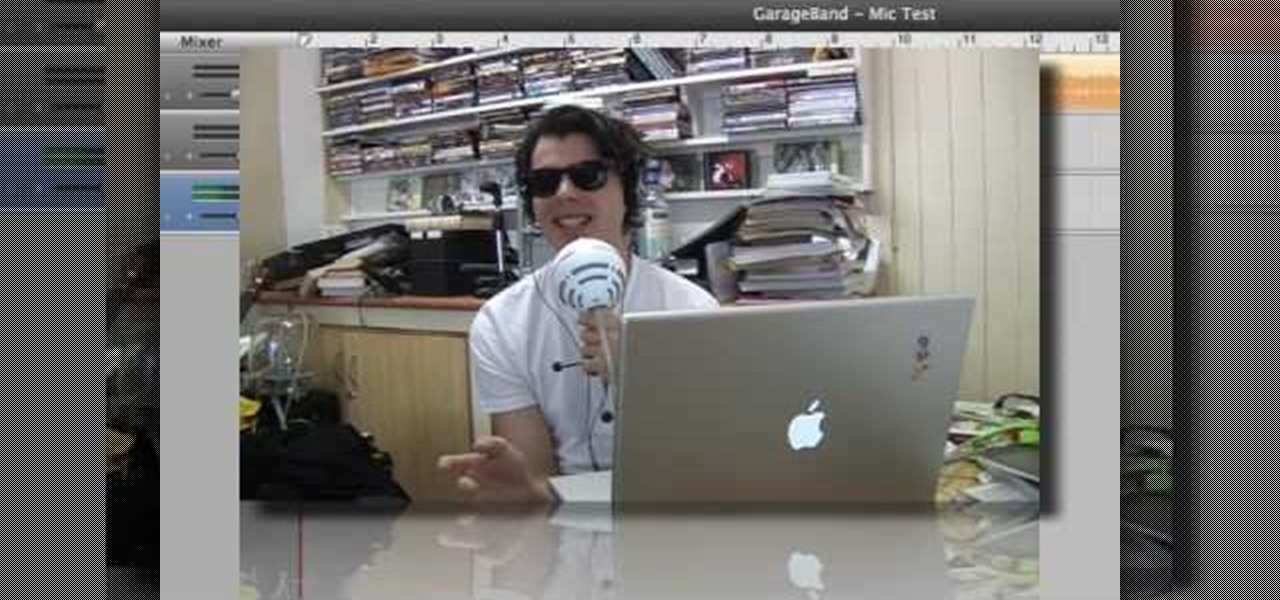
Yes, you can use GarageBand's Auto Tune to sound like T Pain and Kanya West. To start with, in GarageBand, click the plus sign in the bottom left hand corner to create a new track. A window will pop up, Real Instrument Track should be selected by default. Click the Create button. In the Track Info window check to make sure your Monitor is set to On. In the bottom left hand corner, click on the button with the scissors in the middle of the sound wave. This is the Edit Track button. Click on Ad...

Circuit bending an audio device typically involves removing the rear panel of the device and connecting any two circuit locations with a "jumper" wire, sending current from one part of the circuit into another. Results are monitored through either the device's internal speaker or by connecting an amplifier to the speaker output. If an interesting effect is achieved, this connection would be marked for future reference or kept active by either soldering a new connection or bridging it with cro...

Stop a bladder or urinary tract infection in its tracks by learning what to look for and how to prevent it from getting worse.

You Will Need * A fire extinguisher

Systm is the Do-It-Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. They will help you avoid pitfalls and get your project up and running fast. In this DIY episode, see how to broadcast live online.

Buying a digital camera doesn't mean your old prints, slides, or negatives are obsolete. You can easily convert them with a scanner to bring them into the 21st century. Watch this video to learn how to convert photos to digital.

Your tooth is throbbing, your head is pounding, and the oral surgeon can't see you until this afternoon. You'll need something to take the edge off until the good doctor can fit you in.
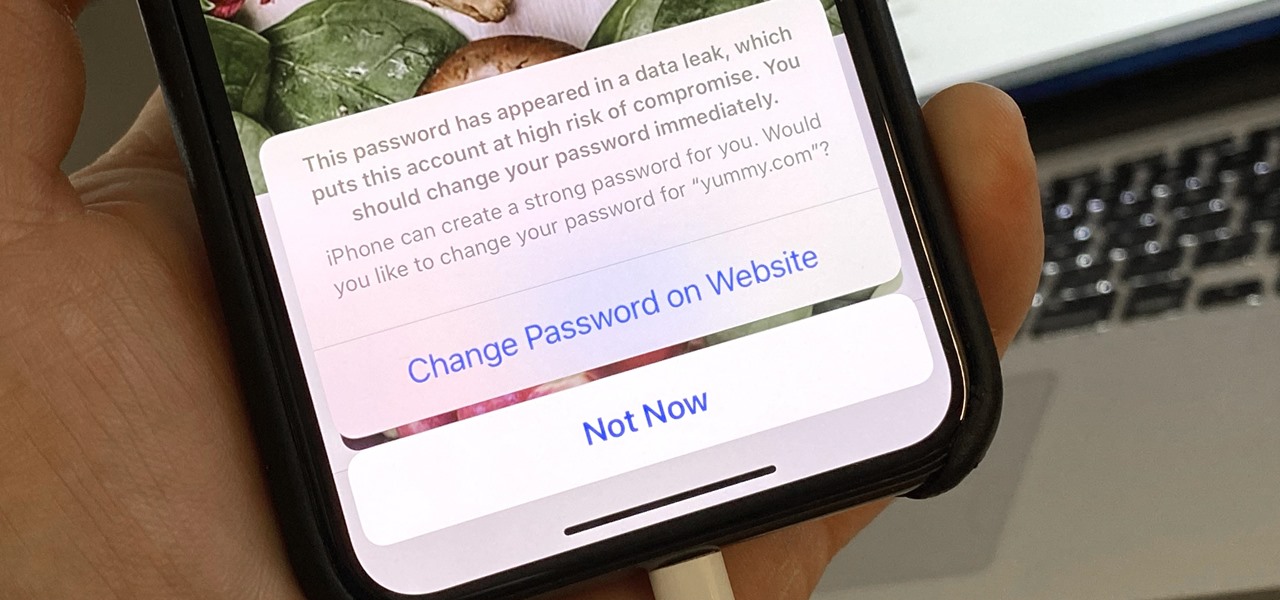
Everything lives online these days, so it's not uncommon to have hundreds of credentials for different accounts on apps and websites. That's why a password manager is a must, and your iPhone has one built right into iOS that you can start using today. In iOS 14, it's gotten even more useful since it can now monitor your passwords regularly to see if any match leaked password lists online.
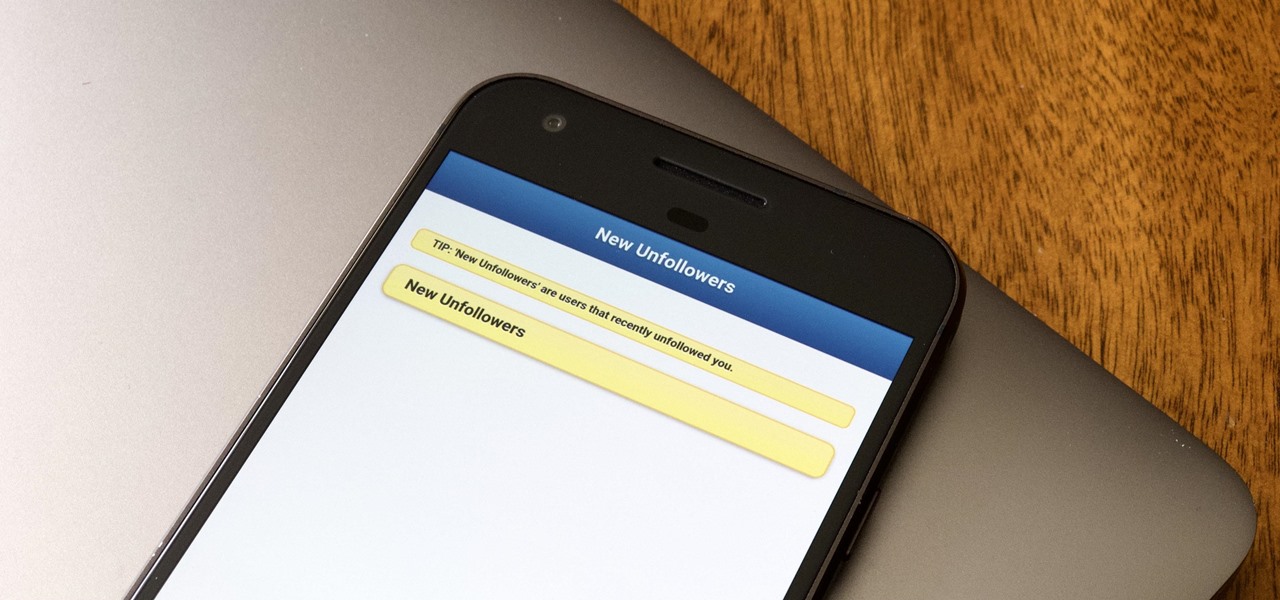
Followers are everything. After all, you need someone to listen to your tweets about last night's episode of your favorite TV show. But what about when people unfollow your account? Not only have you lost part of your follower base, you have no idea who left. Luckily, there are tools out there to help you learn just that, even if Twitter itself won't give up the info.

To hack a Wi-Fi network using Kali Linux, you need your wireless card to support monitor mode and packet injection. Not all wireless cards can do this, so I've rounded up this list of 2019's best wireless network adapters for hacking on Kali Linux to get you started hacking both WEP and WPA Wi-Fi networks.

Devastating and deadly, land mines are a persistent threat in many areas of the world. Funding to clear regions of land mines has been decreasing, but new research may offer a less dangerous method of locating hidden, underground explosives by using glowing bacteria.

Harry Potter fans got a treat last week when Pottermore, a site created by Harry Potter author, J. K. Rowling, released a test that let users learn what form their Patronus protective charm would take.

Starbucks last big hit was definitely their Vanilla Sweet Cream Cold Brew, which became a permanent menu item—not just a summer fling—on May 31, 2016. It's the perfect blend of 20-hour cold brew and vanilla sweet cream; The result not only tastes great, but the cream makes is visually mesmerizing as it floats down through the brew.

Welcome back, my greenhorn hackers! Over the years, I have written many articles here on Null Byte chronicling the many the hacks of the NSA, including the recent hack of the Juniper Networks VPN. (By the way, my speculation in that article has proven to be correct. The NSA did embed a backdoor on those devices.)

Throwing a party means making sure everyone has fun, but that pursuit can quickly get out-of-hand. Before you know it, you're once laid back get-together has received so many RSVPs that it becomes obvious you're throwing the party of the century. With an over-abundance of beer and an inflated guest list, your newly-formed epic reputation must live up to the hype.

Welcome back, my nascent hackers! In previous tutorials for my Wi-Fi Hacking series, I have shown you how to crack WEP and WPA2 passwords, break a WPS PIN, and create Evil Twin and Rogue access points. In this continuation of the series, let's look at slightly different approach to attacking wireless.

Welcome back, my nascent hackers! Like anything in life, there are multiple ways of getting a hack done. In fact, good hackers usually have many tricks up their sleeve to hack into a system. If they didn't, they would not usually be successful. No hack works on every system and no hack works all of the time.

Welcome back, my budding hackers. So many of you are interested in hacking Wi-Fi that I have decided to revisit my Wi-Fi Hacking series with some updated and more in-depth material. I strongly suggest that you look at some of my earlier posts, such as "Getting Started with Terms and Technologies" and "Getting Started with the Aircrack-ng Suite of Wi-Fi Hacking Tools," before continuing here. If you're ready, you can also check out our updated 2017 buying guide here.