
Alcohol Monitoring Search Results


How To: See-Through DIY Rocket Engine Lets You Watch Fuel Combustion in Action
Ever wondered what the inside of a burning rocket looks like? Well, thanks to Valve engineer Ben Krasnow, now we know. He built a homemade hybrid rocket engine that's see-through so you can actually watch how it works. And even though it's probably a really bad idea to try this at home, he made a video so you can build one, too. Just don't say I didn't warn you.

How To: Customize Your USB Keyboard with a DIY Illuminated Base with Built-In Phone Stand
I've never really liked to type on a flat or low keyboard. Even the small flip-up stands underneath most keyboards were not good enough for me, as those little legs aren't usually more than 2 or 3 centimeters high. I'd like a minimum of 5 cm, so I decided to make this keyboard base for myself. Aside from giving me the right height and angle, this DIY keyboard base also features LEDs that light up my monitor, the table, and gives a nice background to my desktop. It's even got a built-in stand ...

How To: See If Anyone's Hacked into Your Dropbox, Facebook, or Gmail Accounts
Dropbox announced Tuesday that a recent security breach compromised a list that included the email addresses of certain Dropbox users. To avoid future complications, the service announced that it would be implementing two-factor authentication, and even more useful, a security page that lets you monitor all activity on your account. In light of this and other recent web security threats, you might also want to know that services like Gmail, Facebook, and Yahoo! Mail have similar pages where y...

News: This Mini "Jesus Bug" Robot, Soon-to-Be Spy, Walks and Jumps on Water
Gerridae—you've probably seen these weird bugs gliding across the surface of the water when you're out swimming or fishing. These insects are commonly referred to as water striders, or more cleverly, Jesus bugs, for their ability to "walk on water". It's a pretty cool trick, but what could it do for science, right? Turns out, quite a bit. Photo by felixtsao

How To: Make Glowing Green Candy
If there ever was a day to eat green candy, St. Patrick's Day would be it. But is there something better than the banality of green candy swarming the streets on St. Patty's Day? Yes—glowing green candy, and Instructables user BrittLiv wants us to show you how it's done.

How To: Eat for maximum energy
Candy bars are tasty but all they do is spike your blood-sugar momentarily leaving you with and energy crash. For high, sustained energy you will need a balanced diet full of complex carbohydrate and protein.

How To: Use the recovery position [signed] (British Red Cross)
Even those with hearing impairments need to know basic first aid procedures, because everyone, including deaf people, can save a life one day. People may collapse unexpectedly for a number of reasons, and people who faint periodically, or those who suffer frequent seizures or from epilepsy need help from others, so it's important that everyone know the proper first aid procedure for saving a collapsed victim casualty.

How To: Fix Blurry Photos in Photoshop
It's very easy to get a slightly blurry photograph due to a moving subject, camera shake, or just an incorrect auto-focus, but you don’t have to let that ruin an otherwise terrific picture. All it takes is a little finesse in Photoshop or another photo editing software. This guide covers sharpening a blurry image using Photoshop specifically.

How To: Perform Paper Chromatography in the Chemistry Lab
Find out how everything in a chemistry lab works, from pipettes to burners to recrystallization to storage. You'll get precise instructions on how to work and perform certain scientific duties in the chem lab, whether it's chemical or just ordinary high school science.

How To: Use S-Video to view your computer screen on a TV
This video shows you how to easily use an S-Video cable to view you computer screen on a TV set. The first thing you have to do is buy an S-Video cable. Plug the 2 sides of the cable in TV and in PC or laptop. Turn your television to either AV1 or AV2. At this point, the computer screen should appear as well on TV as on the PC monitor or laptop monitor. Next, you can personalize your monitor or TV Resolution by right-clicking anywhere on the desktop and then clicking Personalize. In the poppe...

How To: Create floating panels in After Effects
This video shows you how to create floating panels in After Effects. This is extremely helpful if you can work with multiple monitors.
How To: Change your monitors resolution and color quality
A quick and easy demonstration showing how to change your computer resolution and color quality. If you don't know how to change these things, this video will help.

News: 13 Ways a Good Smartwatch Can Enhance Your Workout
Thanks to numerous smartwatch deals this holiday season, many people are receiving their first one. But what exactly can they do? In regards to fitness, quite a lot. With a growing list of sensors and software updates, these small devices can be the very thing you need to ultimately reach your fitness goals.
How To: The 5 Best Meal Tracking Apps for Managing Your Diet & Counting Calories
Whether it's for health reasons or just to look better, many of us want to get in shape. It's a long process that starts with nutrition, and dieting is never easy. Fortunately, there are some great food-tracking apps that will make it a lot easier to become a healthier version of yourself.

How To: Use MDK3 for Advanced Wi-Fi Jamming
You may have heard of a signal jammer before, which usually refers to a device that blasts out a strong enough radio signal to drown out the reception of nearby devices like cell phones. Purpose-built jammer hardware is outright illegal in many countries. Still, Wi-Fi is vulnerable to several different jamming attacks that can be done with Kali Linux and a wireless network adapter.

How To: Hack WPA & WPA2 Wi-Fi Passwords with a Pixie-Dust Attack Using Airgeddon
Design flaws in many routers can allow hackers to steal Wi-Fi credentials, even if WPA or WPA2 encryption is used with a strong password. While this tactic used to take up to 8 hours, the newer WPS Pixie-Dust attack can crack networks in seconds. To do this, a modern wireless attack framework called Airgeddon is used to find vulnerable networks, and then Bully is used to crack them.

How To: Change Your Own Oil — A Beginner's Guide
If you're one who enjoys a good DIY project, or if you're just tired of paying exorbitant labor fees to have your vehicle serviced every 5,000 miles, changing your own oil can be a rewarding endeavor. Even though cars and trucks are becoming increasingly over-engineered these days, manufacturers generally see to it that the basic maintenance items can still be taken care of in your driveway with a few common tools.

How To: Remove caulk
If you’re doing some spring cleaning and decide to throw in a little home improvement in as well you may want to remove old caulk. As we all know, old caulk is unattractive and will make areas look dirty or unfinished.

How To: Remove bike handlebar grips
With a few easy steps you can remove the handlebars from your bike to change the grips, for maintenance or for whatever other reason you might want handlebars off of a bike. Now you'll never have to suffer though old handlebar grips again.
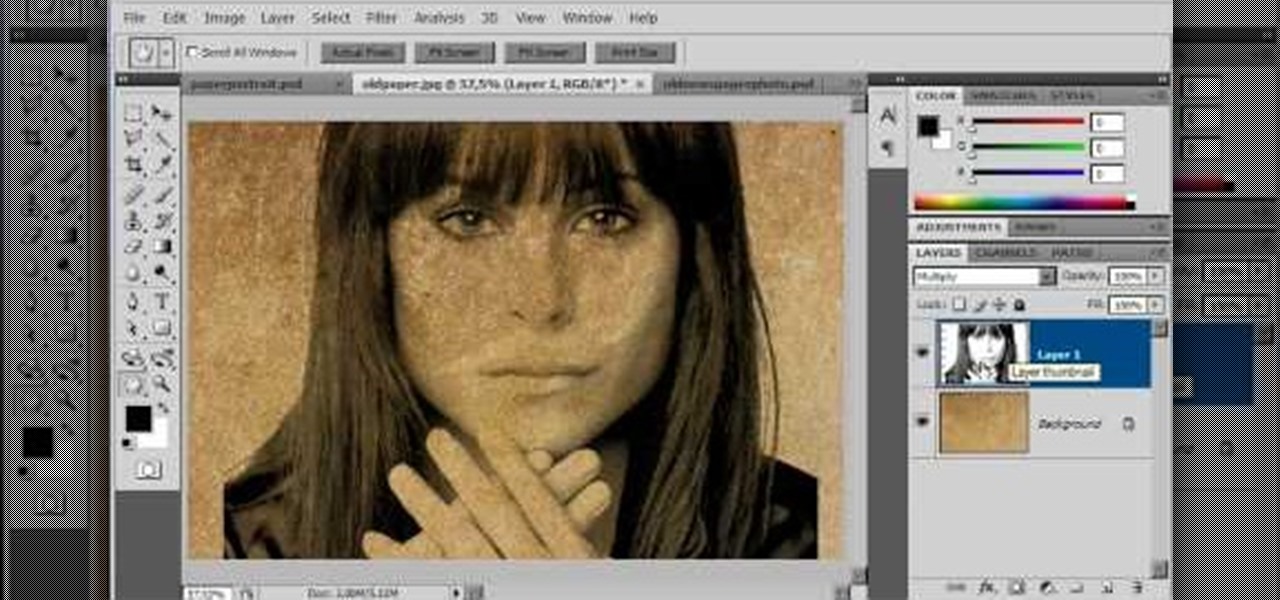
How To: Create an old faded newspaper effect in Photoshop
The video is about how an old stalled photographic image with faded backgrounds to a normal image. A nice clean digital image is taken and is mixed with a texture of a paper and produces a final composite image of all effects combined. The procedure is not that difficult but it needs to be followed in a proper order. First the paper texture is taken as a base and then the clean digital image is dragged onto this texture. The blending mode is adjusted from normal to multiplied blending mode, w...

How To: Make Arabic (or Turkish) coffee
Enjoyed throughout the Middle East, Arabic coffee is deliciously rich, and easy to make at home. Watch this video to learn how to make Arabic (or Turkish) coffee.

How To: Get your body bikini ready
Learn how to get your body bikini ready. Try these proven methods to get an awesome bathing suit bod.
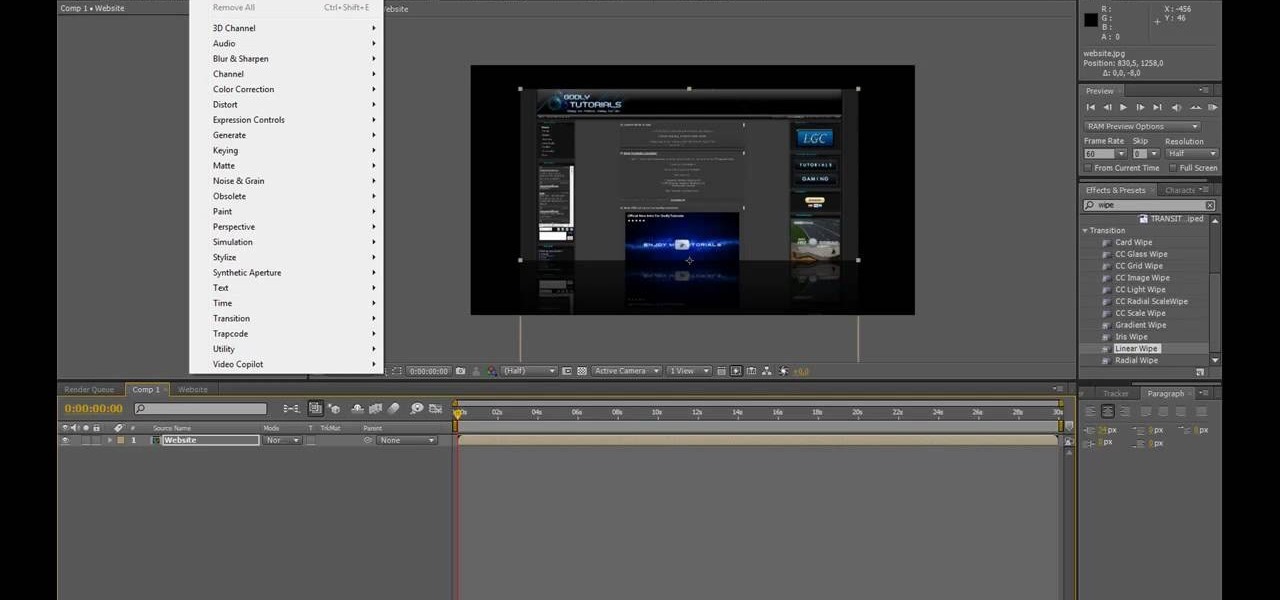
How To: Create a web advertisement video in After Effects CS4
Open After Effects. Create a new composition by selecting "Composition" and "New" from main menu. Use default NTSC DV preset. Keep 30-sec default duration unless you need more time for the video scene to edit. Import several video clips by selecting "File," then "Import" from menu. Navigate to video files you want. Import at least 3 different video files using Import File dialog box. Double click on 1st video file you want to add to your timeline. The file will now open in a video monitor win...

How To: Deal with gestational diabetes
Approximately 4 percent of women are diagnosed with gestational diabetes during pregnancy. Here's how to manage it.

How To: Immobilize an ankle
Learn how to immobilize an ankle. The ankle is a complex joint, so when an injury occurs, and you can't get help right away, the first thing to do is keep it from moving – you'll prevent any more damage to the surrounding nerves and tissue.

How To: Buy and win eBay auctions
Help yourself win that must-have item with these tips. You Will Need: a computer with internet access, money, & patience. Create an account. Browse the categories to familiarize yourself with the site, especially if you don’t have a specific item in mind. If you know what you want, start searching by using broad terms and synonyms to yield the most results. Add quotes around your search terms or qualifiers, such as a specific color or size, to narrow the field. You can also post on the “Want ...

How To: Teach vocabulary words to children
Here, you'll see how to properly teach children some vocabulary words by use of a scaffolding method. You'll learn about modeling, prompting, monitoring understanding, coaching and much more.
How To: There Are Hidden Wi-Fi Networks All Around You — These Attacks Will Find Them
There are hidden Wi-Fi networks all around you — networks that will never show up in the list of available unlocked and password-protected hotspots that your phone or computer can see — but are they more secure than regular networks that broadcast their name to any nearby device?
How to Hack with Arduino: Tracking Which Networks a Mac Has Connected To & When
A macOS computer can reveal a lot of information about the owner, including which Wi-Fi network they have permission to access. With an Arduino-based attack, we'll use a five-dollar setup to inject a rogue Wi-Fi network and steal the list of trusted Wi-Fi networks, allowing us to see where the computer has been.

News: Apple Watch vs. Fitbit — What's the Best Bang for Your Buck?
In the case of Apple Watch v. Fitbit, the winner comes down to the judge at hand. Apple currently offers two smartwatches — the Series 5 and the Series 3 — while Fitbit offers three models — the Fitbit Versa 2, Fitbit Ionic, and Fitbit Versa Lite. Whatever your assumptions about these devices are, throw them out the window, as each has something unique to bring to the table.

How To: Intercept Security Camera Footage Using the New Hak5 Plunder Bug
In a previous guide, I demonstrated how to extract images from a security camera over Wi-Fi using Wireshark, provided you know the password. If you don't know the password, you can always get physical with the Hak5 Plunder Bug. Using this small LAN tap, we can intercept traffic like images from a Wi-Fi or IP security camera if we can get physical access to the Ethernet cable carrying the data.

How to Hack Wi-Fi: Cracking WPA2 Passwords Using the New PMKID Hashcat Attack
Cracking the password for WPA2 networks has been roughly the same for many years, but a newer attack requires less interaction and info than previous techniques and has the added advantage of being able to target access points with no one connected. The latest attack against the PMKID uses Hashcat to crack WPA passwords and allows hackers to find networks with weak passwords more easily.

News: Inside Magic Leap's Cinematic Partnership with Andy Serkis & The Imaginarium's Experimental Motion Capture Experience
By now, you've probably already seen Andy Serkis and his performance capture demo for Magic Leap. And sure, marrying motion capture acting and augmented reality sounds compelling, but how does it really work as an experience?

News: Biggest Bee Study Yet Shows Devastating Effects of Neonicotinoids Across the Globe
By connecting the dots between theory and real-life effect, two new studies offer more proof that neonicotinoid insecticides are causing extensive damage to honeybee colonies.

How To: Log Wi-Fi Probe Requests from Smartphones & Laptops with Probemon
It's no secret that devices leak data, but sometimes they do so in ways you may not expect. Your phone, laptop, printer, and IOT devices leak Wi-Fi information that can (and is) used to track you.

News: The Definitive Guide to the Levels of Automation for Driverless Cars
Not only has there been difficulty finding consensus on a name for driverless, autonomous, self-driving, or automated vehicles, there is also the issue of what we actually mean when we say a vehicle is self-driving, automated, and so on.
How To: Turn Your Android Phone into the Ultimate Fitness Tracker
It seems like everyone is getting in shape these days (or at least trying to improve their fitness), and as a result, there's an endless supply of fitness trackers and smartwatches hitting the market. This is all very wonderful, unless of course, you're broke and can barely afford a decent pair of running shoes.

How To: Tell if Your Android Has Been Hacked (& What You Can Do About It)
Smartphones are almost always connected to the internet, so it stands to reason that they can be hacked remotely. Or perhaps a jealous boyfriend or girlfriend got hold of your device physically, in which case they could've potentially installed a keystroke logger, a virus, or any other type of tracking app to spy on you.

How To: 10 Reasons Why You'll Want to Use Screen Savers Again on Your Mac
Yes, screen savers are fun to look at for a few seconds, but those animations actually used to serve a purpose beyond simple entertainment.

