There's a lot of misinformation about VPN services, and it stems from the fact that not all of them are created equal. Some focus on privacy, others on security, and a few VPNs are seemingly even purpose-built for the polar opposite: data collection. We made this guide to help clear the air on some of these issues while objectively ranking the best of the best.
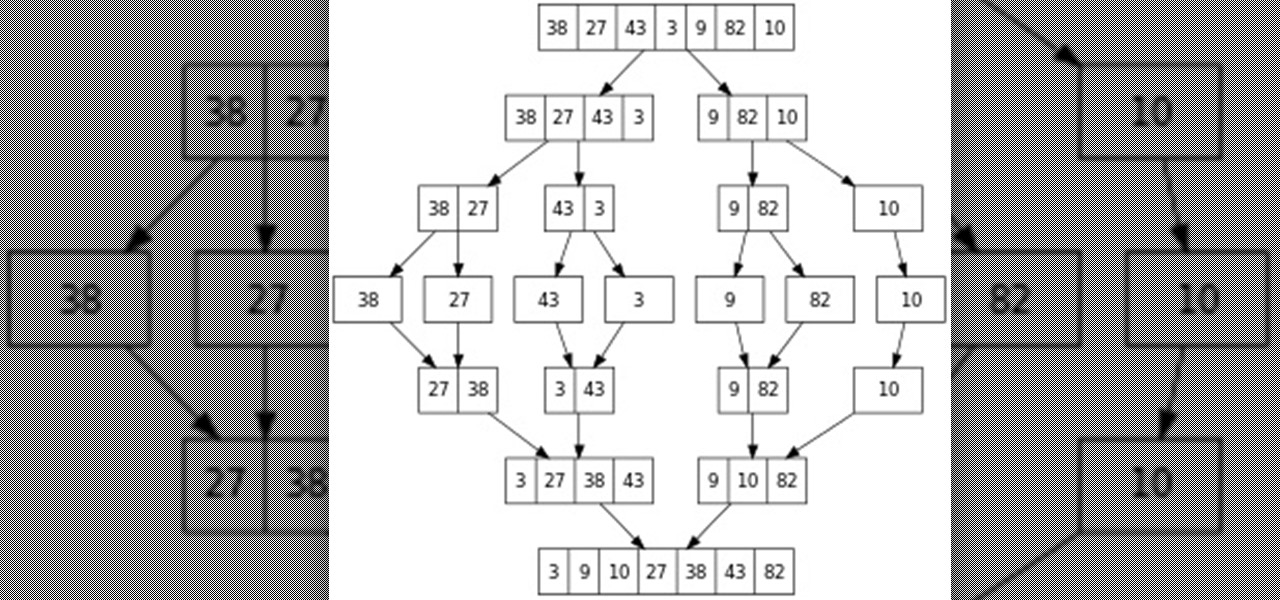
Hello everyone! This is part 7.0 of my Sorting series. I know, I said last time that there would be a 6.1, but not just yet!

Greetings fellow hackers. This tutorial is about creating "safe" passwords. This is different from strong passwords. Safe passwords is just creating a password that is not used by someone else or colleague, my definition. But how do you prevent something like this from happening? Of course you won't ask your friend if s|he is using the password you are about to create. Before I show you some of my tele-psychic powers like Professor Xavier, you might want to read this for advice on creating "s...

Shapr is a new networking app that aims to help professionals connect more efficiently, and draws much of its format from dating-focused social networking apps. Shapr could be especially useful for those who have recently moved into their industry or location, and for those seeking employers or employees. For example, the app already has 65,000 users just in New York City alone.

If you're a tech enthusiast, there's no way you're not watching HBO's Silicon Valley. So you surely know the Pied Piper crew's latest shenanigans involve an app that uses a phone's camera to find facts about food items — a sort of Shazaam for food, if you may.
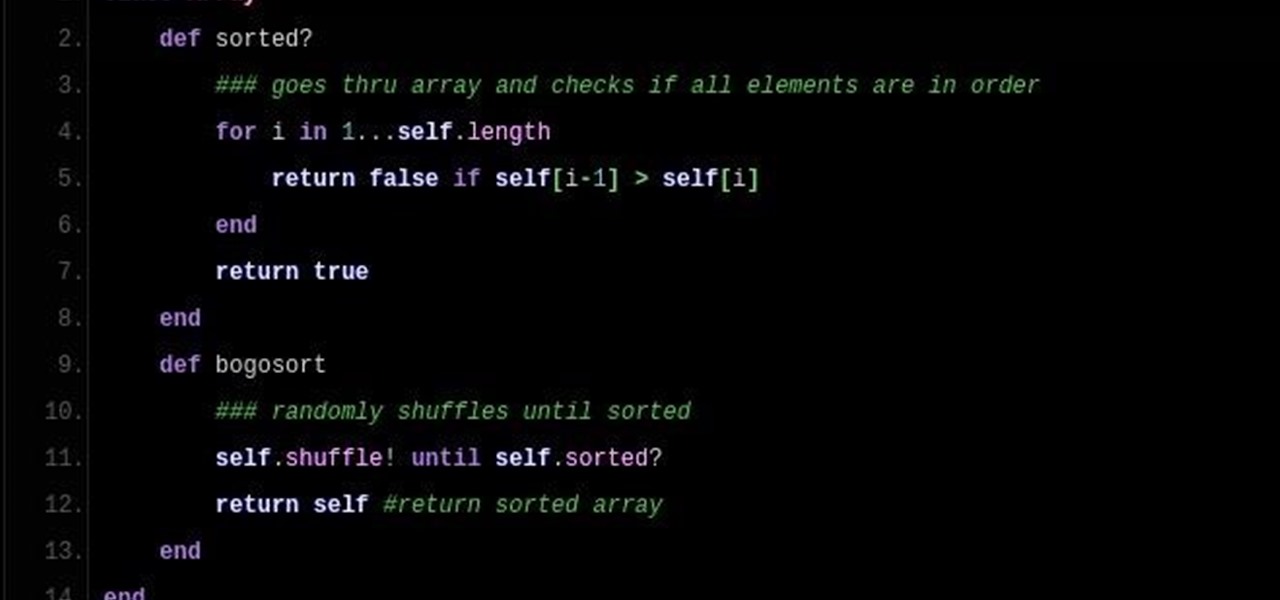
So DTM insisted I write up a little article on Bogo Sort. What Is Bogo Sort?

Welcome back, my nascent hackers! In the conclusion of the Mr. Robot television series, Elliot and fsociety successfully completed their mission of encrypting all of Evil Corp's data with AES-128 encryption and destroying the key.

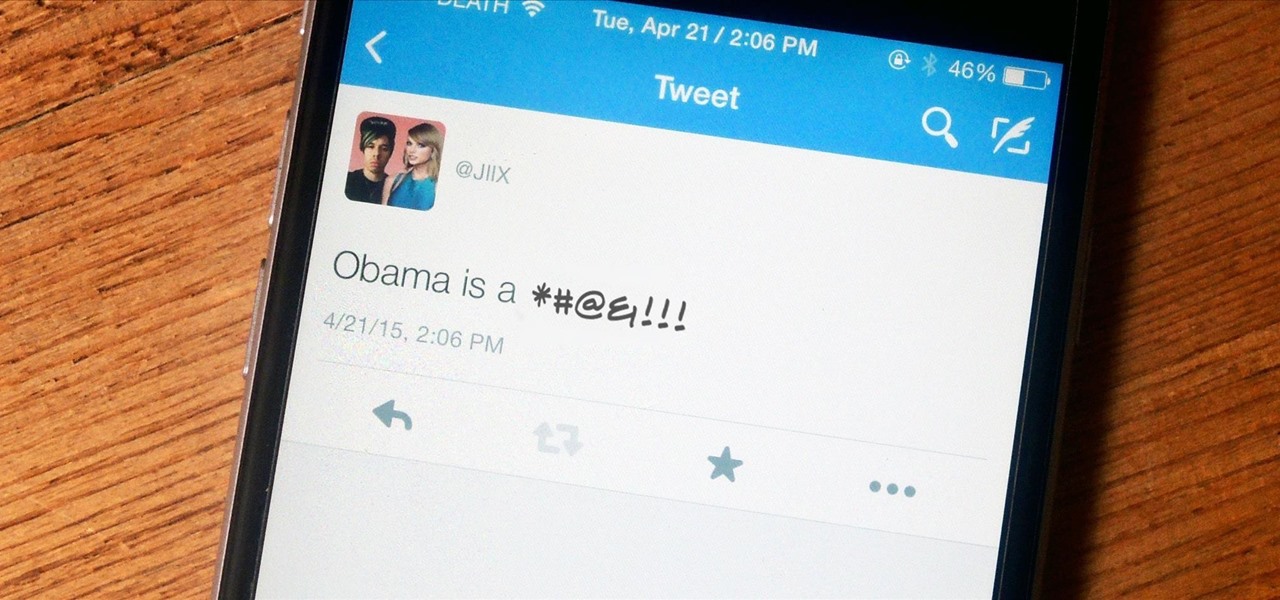
One tweet can get your fired from your job. At least, in the cases of Gilbert Gottfried, Rashard Mendenhall, Ozzie Guillen, and Mike Bacsik, who were all either fired or forced to resign from their jobs after posting regrettable tweets online.

The new Samsung Galaxy S4 may be the only phone to include temperature and humidity sensors, but your Galaxy Note 2 has a few weather-detecting features of its own.

Are you constantly traveling? Well, as a Hilton HHonors member, you can enjoy special treatment at all of their hotels and resorts. It's free to register, but the difficulty lies in climbing up their membership level. To reach Gold elite status, Hilton HHonors requires that you have a minimum of 20 stays, 40 nights, or 75,000 base points—all in one year. While this may very will be easily attainable for those with jobs that revolve around traveling, it's almost damn near impossible for the re...

When we are building programs that communicate over a network, how can we keep our data private? The last thing we want is some other lousy hacker sniffing our packets, so how do we stop them? The easy answer: encryption. However, this is a very wide-ranging answer. Today we're going to look specifically at how to encrypt data in Python with dynamically generated encryption keys using what is known as the Diffie-Hellman key exchange.

Although early attempts at consumer smartglasses have employed trackpads and handheld or wearable controllers for user input, its the gesture control interfaces of the HoloLens 2 and the Magic Leap One that represent the future of smartglasses input.

When computers have vision but people don't, why not have the former help the latter? That's the gist behind the Cognitive Augmented Reality Assistant (CARA), a new HoloLens app developed by the California Institute of Technology.

While we've seen Snapchat apply sky segmentation to AR content, the makers of the Blue Sky Paint app have applied similar capabilities to create and share airborne art.

In Bhopal, India, a place nestled in between the royally pink city of Jaipur and the dry (i.e., alcohol forbidden) state of Gujarat, is a team of developers determined to make a fully driverless car suitable to the complexities of Indian traffic. An algorithm elaborate enough has yet to be made by any other company, but is the fundamental key to handling the intuitive habits of Indian drivers, the often intense and gridlocked traffic, and the country's vast expanse of jarring roads.

Thanks to Snapchat, we're all familiar with face swapping and augmentation thanks to some clever, fun technology. But that's just the beginning, because this kind of augmented reality can do so much more.

Most of us have some sort of malware scanner or antivirus program on our computers, but what about our smartphones? A lot of people don't realize that computers aren't the only devices that are susceptible to malicious software and apps—they can follow you on your smartphone or tablet, too.

If you've ever been asked to find the GCF, or Greatest Common Factor, of a series of numbers or algebraic expressions, check out this video to learn how.

These two videos will get you on your way to using the Fridrich F2L Method to solve the Rubik's Cube. What is F2L? The first two layers, of course.

Now that the transfer tool for migrating your Google Play Music library to YouTube Music is rolling out, more fans of the former, which will meet its end in 2020, are giving its replacement a try.

Apple's ARKit has built a considerable lead in terms of features over Google's ARCore, but Google's latest update to ARCore adds a capability that makes the platform a bit more competitive with ARKit.

Love is the spice of life — it is also the microbes that couples share through sickness and in health, through the bathroom and in a hallway.

Greetings, fellow NBers! Welcome to my sixth iteration of my sorting series. Today, we'll be discussing a personal favorite: Quicksort, or Quick Sort.

With just a swipe and tap of a finger, we can access enormous libraries of information on our smartphones like never before. Whether we want more info about gluten sensitivity or just want to brush up on 18th century philosophers, there's an article somewhere in the vast ocean of the internet that can lend us a hand.

Hashes are commonly used to store sensitive information like credentials to avoid storing them in plaintext. With tools like Hashcat, it's possible to crack these hashes, but only if we know the algorithm used to generate the hash. Using a tool called hash-identifier, we can easily fingerprint any hashes to discover the right Hashcat mode to use to retrieve a password.

When I see the words "free trial," I know I'm probably going to have to whip out my credit card and enter in the number to "not get charged." Then I end up forgetting about the trial and want to kick myself in the ass when I see my statement at the end of the month.

Everybody knows not to store sensitive information in unencrypted files, right? PDFs and ZIP files can often contain a treasure trove of information, such as network diagrams, IP addresses, and login credentials. Sometimes, even certain files that are encrypted aren't safe from attackers. That's where Zydra comes in — a tool for cracking RAR files, ZIP files, PDF files, and Linux shadow files.

Celebrities and influencers learned how to leverage Instagram's platform to build their brands. While some effortlessly amassed a following, many had to do the legwork to reach a vast audience. Understanding their secrets will help you grow your own following.

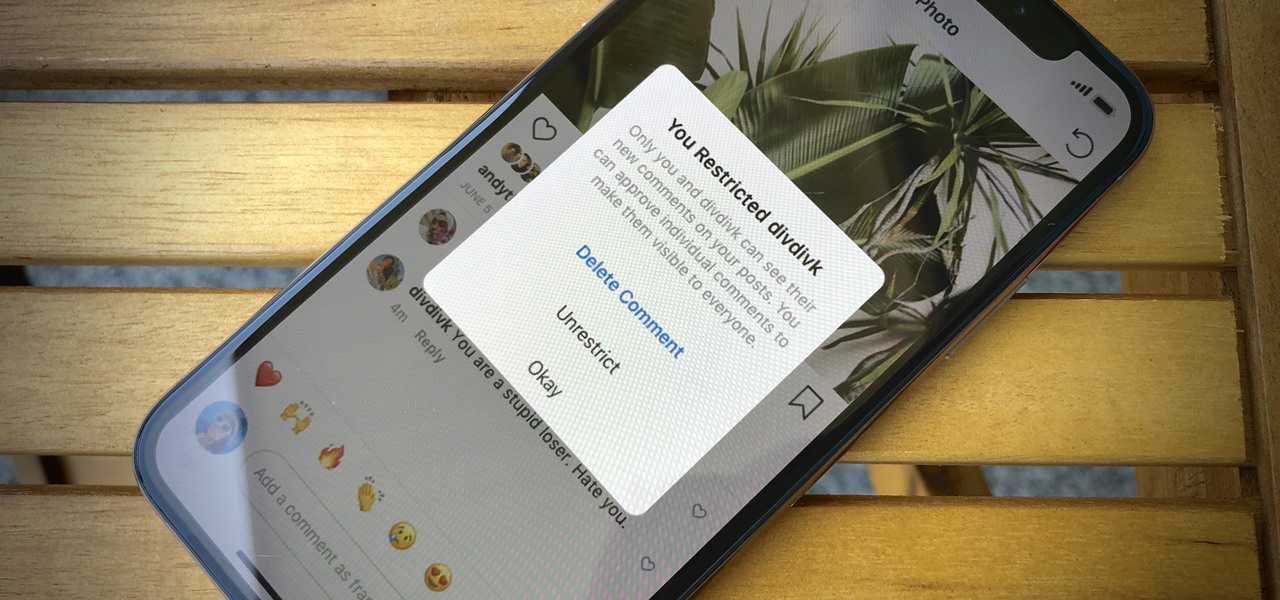
In general, the internet can be a cruel place, and Instagram is no exception. Most of the time, the platform is a fantastic way to share and view unique and creative content, to reach an audience of both fans and friends. People can step out of line and harass or bully others on posts to the detriment of the entire community. However, this type of commenting won't be sustainable for much longer.

As you're surely aware, your phone can be used against you. Thanks to our cameras and microphones, a clever hacker can obtain access to your device and invade your privacy. But spying isn't limited to just these two sensors — gyroscopes, proximity sensors, QR codes, and even ads can be used to paint a very clear picture about who you are and what you're currently doing.

While augmented reality headset makers are faced with tackling numerous challenges before the category is truly ready for prime time, a start-up comprised of former Microsoft engineers may have nailed fast and precise tracking of hand gestures and full-body locomotion.

Geotagging your location on Instagram is one of the most undervalued ways to generate traffic to your profile. The beauty about adding your location to your IG posts is that it allows you to be seen by other users than the ones that already follow you.

Facebook released a new app in November 2016 that aimed to compete directly with Snapchat, but it was only officially available in Brazil—and still is. The app, called "Flash," is so much like Snapchat that it's not even the slightest bit of a stretch to call it a clone.

According to sources, Google has been working on a travel app for some time, and now it has a name: Google Trips. Google Trips aims to be the all-in-one place to go for travel information about your trip. It hasn't been officially announced, but from the leaks that have come out so far, think of it like Yelp, TripAdvisor, and your itinerary in one.

If you haven't read the last article, feel free to stop by and give it a read, but abstaining from reading it will not, for the most part, be detrimental to your understanding.

Hello all. It's time for level 6 all, password encrypting. Step 1: Looking for ASCII Table

In recent years, Hollywood has taken a shine to hackers, with hackers appearing in almost every heist or mystery movie now. This can be both good and bad for our profession. As we know, whichever way Hollywood decides to depict our profession is how most people will perceive it.

While your iPhone may have a built-in time-lapse feature, it's nowhere near as smooth as Instagram's newish Hyperlapse app, and it doesn't give you any speed control like the latter does. If you haven't tested out Hyperlapse yet, check out the short promo video to see just how well its stabilization algorithm works.

If you've used Twitter on your smartphone sometime in the past two weeks, you've probably noticed that tweets from users you don't follow have been popping up on your timeline.