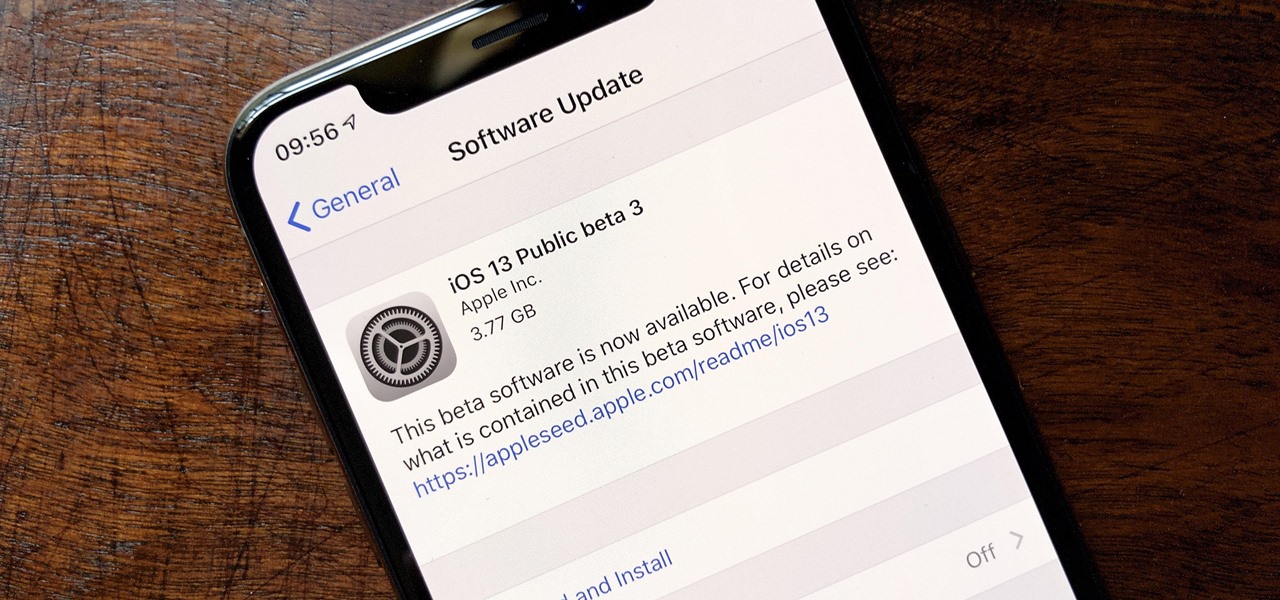
The wait wasn't so long this time. Apple released public beta 3 for iOS 13 on Thursday, July 18, just one day after the release of developer beta 4. For context, Apple took five days to seed public beta 2 after releasing dev beta 3, so it's a pleasant surprise that the latest public beta dropped so soon.
We're pumped for iOS 13 and all of the fresh features and changes that come with it. Developer beta 3 came with new features in the double digits, including AR eye contact in FaceTime and mouse cursor size customization. Developer beta 4, released today, has a few more additions and changes as well.

The third developer beta for iOS 13 has been out since July 3, and while devs have had fun exploring all the new features, those of us on the public beta have sat on the sidelines running the public version of dev beta 2. But we don't need to wait any longer, as Apple just released iOS 13 public beta 2 and all the goodies that come with it.

On July 3, Apple pushed out iOS 13 developer beta 3 for iPhone, and there's a lot found hidden within. A new FaceTime setting, more Arcade details, full-page scrolling screenshots everywhere, a noise cancellation option in the Control Center, and a new markup tool — and that's just a few of the new features.
There's no doubt iOS 13 has dominated the talk around the Apple community this month. Since the announcement and release of the first developer beta, we iPhone users have had a treasure trove of new features and changes to explore and discuss. Now the fun continues with iOS 13 dev beta 2. Who's ready to start up the conversation all over again?

The first developer beta for iOS 13 is available to install on iPhone models, but the process for doing so may be a bumpy ride. Apple has not included configuration profiles for the developer beta yet, and many developers are having issues installing iOS 13 even with macOS 10.15 Catalina installed. Plus, since this is the first beta, there are a lot of problems with old and new features to work the kinks out of.

Even though most phones don't have Oreo yet, Google has released Android 9.0 Pie. It's available on Google's own Pixel devices, and updates should soon be available to partnered devices from Essential, Nokia, Oppo, Sony, Vivo, and Xiaomi. We're already digging into it to highlight all of the features and changes.

If you use Apple's Mail app on your iPhone for iCloud and third-party email accounts, install the new iOS update ASAP if you haven't already. While there's not a colossal number of new features, the latest tools and improvements are powerful enough to make the update feel like Mail's biggest ever — and there are features we've been waiting for for years!

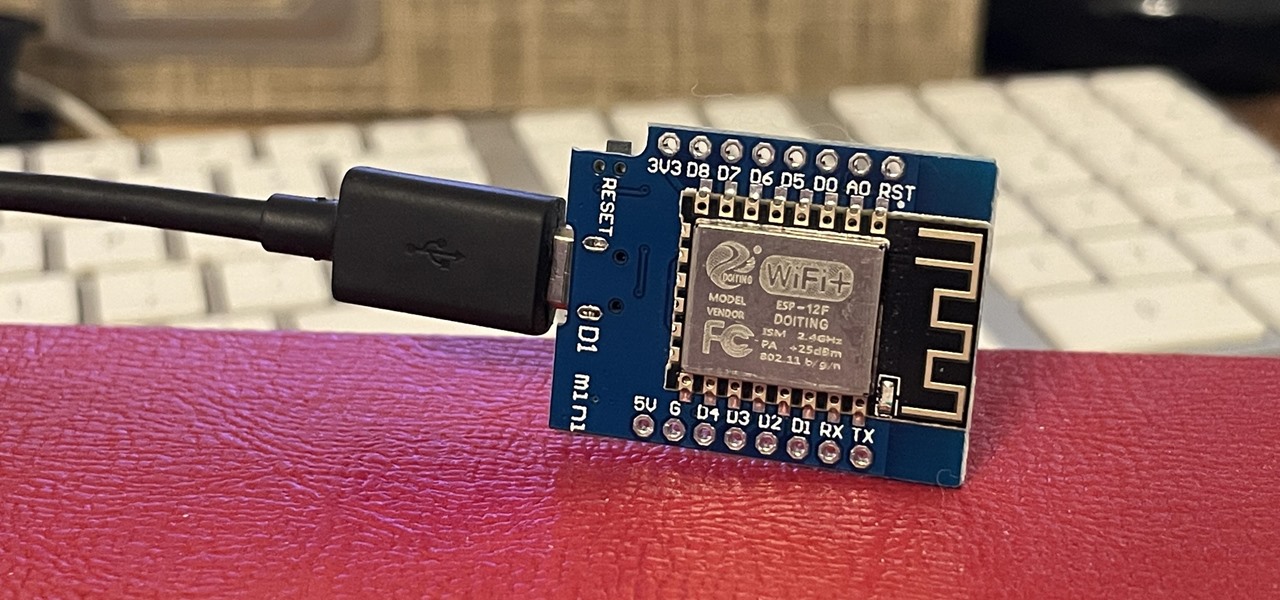
If you've wanted to get into Wi-Fi hacking, you might have noticed that it can be pretty challenging to find a safe and legal target to hack. But you can easily create your own test network using a single ESP8266-based microcontroller like the D1 Mini.

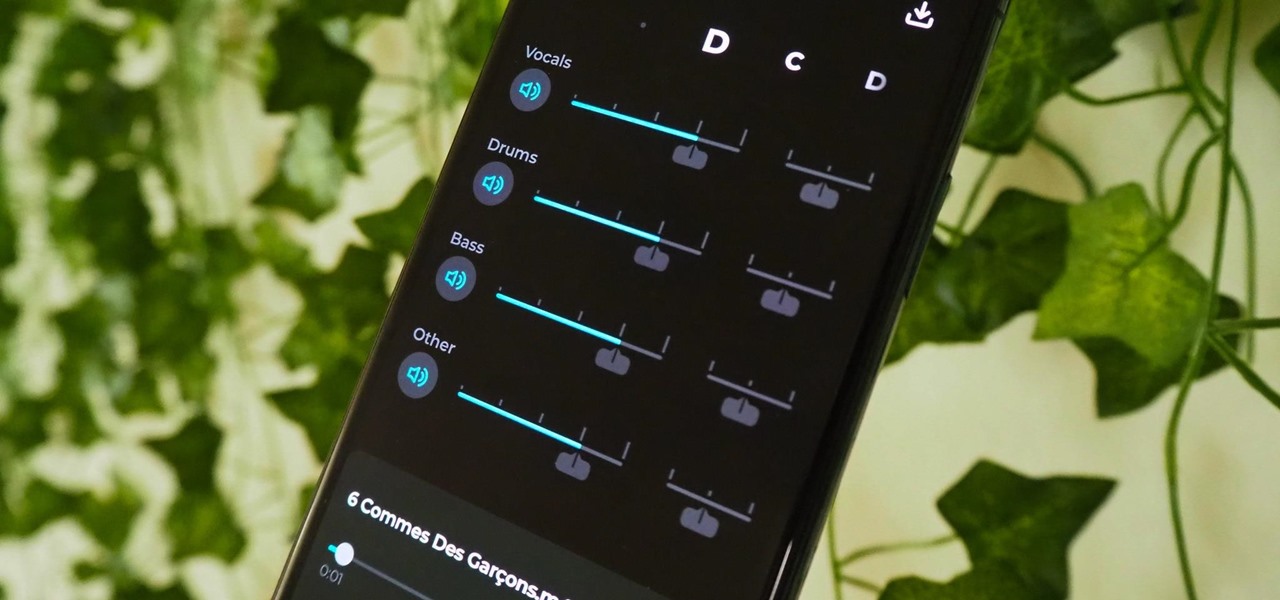
Adobe Audition, Audacity, and other audio editing software have tools to isolate vocals and instruments in regular songs so that you can get an instrumental track for karaoke, vocals for an a capella version, or solo drums, bass, keys, etc. that you can use to learn the song yourself. The software is mostly for desktop computers, and it doesn't always do a good job, but that's where Moises comes in.

Using a strong password is critical to the security of your online accounts. However, according to Dashlane, US users hold an average of 130 different accounts. Memorizing strong passwords for that many accounts is impractical. Fortunately, password managers solve the problem.

A dead man's switch is a fairly simple concept. If you don't perform a specific task before a set amount of time, it'll perform a specific action you set. They can be handy not just for hackers but for everyone who wants to protect themselves, someone else, or something tangible or intangible from harm. While there are more nefarious uses for a dead man's switch, white hats can put one to good use.

If we were to assign a theme for the 2019 edition of the Next Reality 30 (NR30), it might be something along the lines of, "What have you done for me lately?"

Trying to figure out which music streaming service to subscribe to can be a difficult task when the playing field is so crowded. Each has its benefits, as well as downsides, so finding the right one for your needs and wants can take a lot of overwhelming research. But we've done all the research for you to help you find the best music subscription your money can buy.

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.

Learn this algorithm to do the cube within a cube design with a Rubik's Cube:

If you've wanted to solve the Rubik's Cube, there's no better tutorial than this. In this video, you'll learn how to solve the Rubik's Cube with the Fridrich Method.

--in under ten moves! Listen closely newbies, or actually, watch closely newbies. This algorithm gets every color on every side.

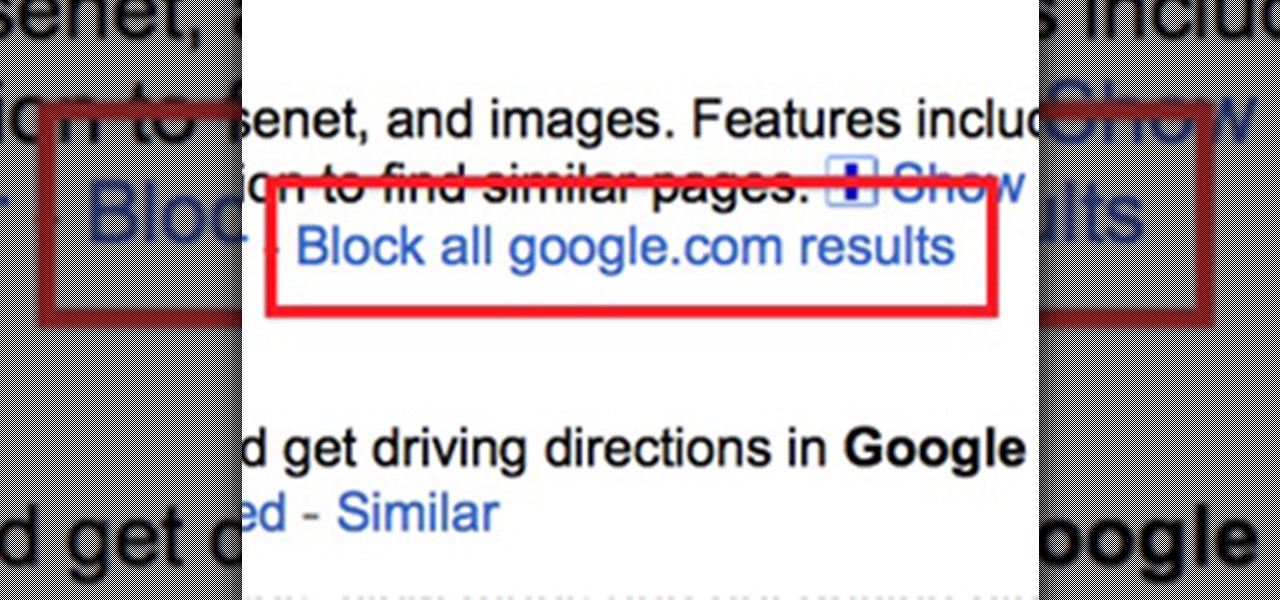
Google recently rewrote their search algorithm to make "low-quality sites" disappear from your front page results, putting the emphasis on better, more relevant answers with original content and in-depth information. And now Google has added a new feature to their search system that gives you some of the control of what you see in your results.

Another great Community Byte in the bag! This week was really cool, especially with programming going on twice a week. We transitioned to the new times very smoothly with no one left behind, from what I can tell.

This article is going to cover the basics of link building. Why do we want to build links? First of all, what is a link? A link is a hyperlink, actually. You click on it and it brings you to another webpage. I'm sure you've all clicked on links before. Well, what we want to do is we want to build links from other sites back to our own site. Why do we want to do this? Google’s problem, as I see it, and this is based on thousands of hours of research, reading articles and watching videos and li...

This medical presentation discusses the management of nausea and vomiting of pregnancy (NVP). Many women who have to cope with nausea and vomiting of pregnancy endure tremendous physical hardship. This suffering may have a profound impact on family, work, and social life. Therefore, it is important for health professionals to realize that pregnant women who complain about nausea or vomiting are coming for help. Follow along with this presentation as it looks into the various aspects of NVP an...

From ZDNet: "A group of students in China have created PhotoSketch, a project that does exactly what I just described: it takes a rough, hand-drawn sketch, scours the web for photos that match, and runs them through an algorithm, stitching it all together."

Today, we are going to combine what we learned from the Introduction to Cryptography article with our Java programming skills. If you are new to Java, check out Matthew's Learn Java: Part One for a quick beginner's lesson, or check out some of the Java tutorials directly on Oracle.

In this article, I'll show you how to create a simplistic AES python based text encryptor. You'll need python 2.7 and PyCrypto (found here). The code is fairly simple, a user enters an encryption key (which basically tells the program how to scramble the text, using an algorithm), then the text to be encrypted. The program takes the key and text and inputs it into the "cryptograph" or code-based algorithm from PyCrypto. PyCrypto can use 16, 24, or 36 character encryption keys, but for the sak...

If you've ever heard software piracy terminology being discussed, I'm sure the term KeyGens came up. KeyGens is short for key generator, which is a program that exploits algorithmic faults in software by generating software license keys that appear to be genuine. Normally used as a technique to protect the source code software and prevent piracy, a key generator exploits the key algorithm to effectively nullify the need for any software licenses. For example, we must try to find patterns in t...

More password cracking action from Null Byte! Today we aren't going to be cracking passwords per se, rather, we are going to learn the basics of generating rainbow tables and how to use them. First, let's go over how passwords are stored and recovered.

Here at WonderHowTo we love the rubik's cube. We also love cake decorating. So what better than a rubik's cube cake? It looks somewhat complicated, but it surely can't be as complicated as solving the cube itself!

You wouldn't think that something so simple as a "suggested users" list would create so much controversy, but Google+ seemed to have accidentally ignited a firestorm when they introduced a new feature over the weekend: the "Suggested People to Follow" list now appears when a new user joins Google+.

Dealing with insomnia? Just can't fall asleep at night? Well, there's a few things you can do to escape those restless nights. You can take a hot bath (unless you're a shower person), do some yoga (granted you can do the downward-facing dog), or try a little tapping (if you don't mind smacking yourself in the face). But let's face it—most people who have trouble sleeping use prescription medication or natural remedies like melatonin. If you don't want to be dependent on sleeping pills, then m...

The Android Megaminxer is mind-bogglingly elaborate, impressively combining multiple geeky mediums to solve an incredibly complex puzzle. ARM, the genius behind the stunt, uses LEGOs (a Mindstorms NXT kit to be exact) to build a robot responsible for the mechanics; they then employ an Android app as the brain, which solves a Rubik's Cube—oh wait, not a simple Rubik's (that would be too easy), but a Megaminx, which is a dodecahedron with 12 faces, each face containing 5 edges. Like the classic...

Imagine walking around and everyone looks awesome! Ok, maybe this beauty is only skin deep or shall we say AR deep. Coming soon to a pair of glasses near you, you will be able to put on glasses that actually make people look more muscular, have bigger boobs, look tan & blonde, etc... Now imagine that you can push a button or say a word and now all the people around you become brunette. Then another setting makes everyone slightly shorter than you. All of this in realtime!

MultiCuber achieves another world's first: the timed relay solve of 2x2x2, 3x3x3, 4x4x4 and 5x5x5 Rubik's cubes.

Learning the basics of SEO In this tutorial I will go over the basics of Search Engine Optimisation. The "white-hat-way" ("black-hat" SEO is tricking Google and other search engine providers, this will get you into trouble quick!).

Exploring a new city is tough if you're all by your lonesome. But if you have your iPhone on you, you're not alone at all... there's tons of great apps available for discovering the city around you. We've previously featured an app that helps you decide on what bar or club to attend, as well as one that shows you the hidden world unbeknown to most tourists (sometimes even the local population). When it comes to dining out, Yelp helps considerably, but it doesn't provide you with personalized ...

With Microsoft's release of the Kinect SDK, things seem to have slowed down a bit in the world of Kinect development. Have developers exhausted the uses of Kinect already? No way! Four researchers at Cornell University have created an AI-based system on the Kinect that can recognize what you're doing, and maybe even who is doing it.

Cryptography is a quintessential part of computer security in the modern world. Whenever you buy something on eBay or log into Facebook, that data is encrypted before it's sent to the server in order to prevent third parties from eavesdropping and stealing your sensitive information.

Following the first part in this series on advanced cracking techniques, we are going to go over how we can intelligently crack passwords using the old-fashioned bruteforce method. These unique cracking techniques aren't widely used, because most crackers are Script Kiddies who have no idea what the concepts are behind cracking passwords, thus, word won't get around too quickly.

If you've ever wondered how software pirates can take software and crack it time and time again, even with security in place, this small series is for you. Even with today's most advanced methods of defeating piracy in place, it is still relatively easy to crack almost any program in the world. This is mainly due to computer processes' ability to be completely manipulated by an assembly debugger. Using this, you can completely bypass the registration process by making it skip the application'...

Welcome to the fifth Community Byte for coding in Python and beating the challenges given to us from HackThisSite. These sessions are created to bring our community together, to learn from each other, and essentially grow together. Everyone is welcome, from novice programmers to aspiring hackers—even people that are nearly computer illiterate.