
How To: Solve a 5x5 Rubik's Cube Professor
Watch this four-part how to video on solving the 5x5 Rubik's Cube Professor. What, you didn't know they made them that big? Well, they do, and it's called the Professor. The 5x5 monolith.


Watch this four-part how to video on solving the 5x5 Rubik's Cube Professor. What, you didn't know they made them that big? Well, they do, and it's called the Professor. The 5x5 monolith.

Welcome back, my neophyte hackers! Digital forensics is one of the fields often overlooked by aspiring hackers. In a rush to exploit every and any system they can, they often ignore learning digital forensics—the field that may lead to them being traced.

It seems nowadays there's no limit to what type of companies are looking to invest in augmented reality. Given both the positive outlook on the future of AR, and its reported benefits for efficiency in employees, this makes sense. Safran, an international corporation with three main sectors—aerospace, defense, and security—is one such company taking the plunge into incorporating AR in their business.

Researchers have been studying the blood meals of flies to understand the flow of infectious pathogens in wild animals.

Hola my fellow hackers! I promised you the tutorials on setting up RAT's and Botnets, but before jumping into those, i want you to know about the precautionary measures and detection of RATs which might be on the system without your prior knowledge. Of course the Anti-virus do most of the job but there are some RATs which slips past the Anti-viruses (This is where Hacker's skill come into play).

Welcome back, my greenhorn hackers! Digital forensics and hacking are complementary disciplines. The better you are at digital forensics, the better hacker you are, and the better hacker you are, the better you are digital forensics. Unfortunately, few people in either profession cross these discipline lines.

My college days are long behind me, and while I don't necessary miss them, I am jealous of all the countless resources available to students these days. Apps like PhotoMath are something I wish I had access to in my student days, making assignments less strenuous and easier to complete.

With the Wigle WiFi app running on an Android phone, a hacker can discover and map any nearby network, including those created by printers and other insecure devices. The default tools to analyze the resulting data can fall short of what a hacker needs, but by importing wardriving data into Jupyter Notebook, we can map all Wi-Fi devices we encounter and slice through the data with ease.

A rainbow table can be thought of like a dictionary, except instead of words and their definitions, it holds combinations of characters on one side and their hashed form on the other. What is a hash and why would you want to know what random combinations of characters are hashed into?
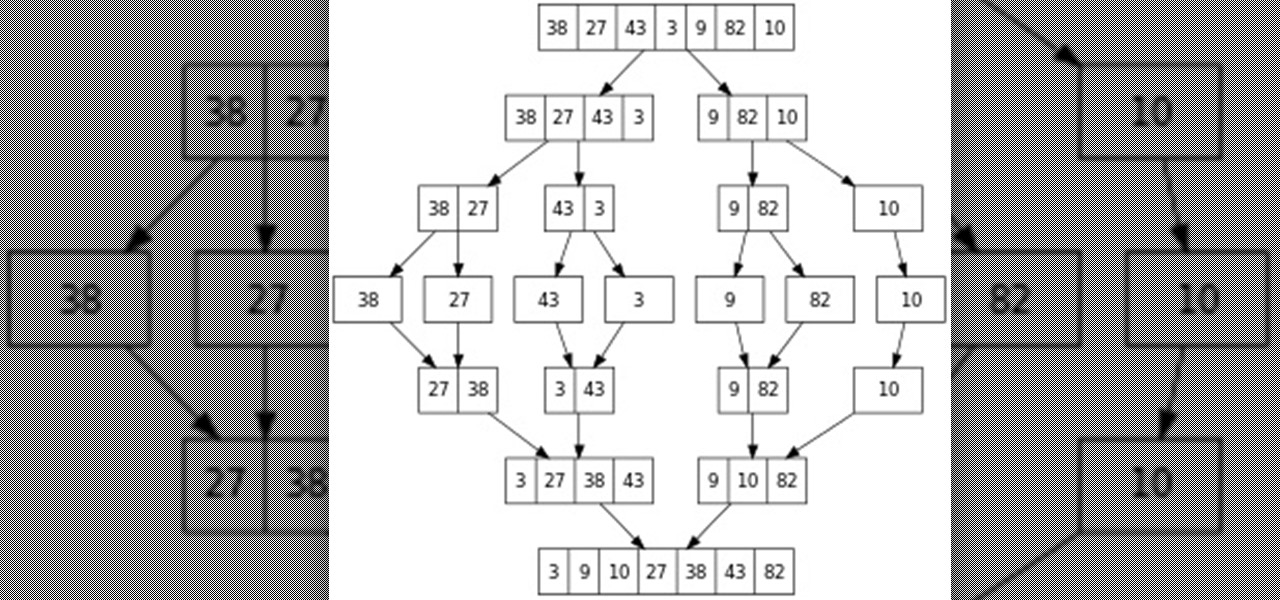
Hello everyone! This is part 7.0 of my Sorting series. I know, I said last time that there would be a 6.1, but not just yet!

Cryptography is the science of keeping secrets, or more specifically, the science of disguising them. As a point of fact, cryptography has progressed quite a bit farther and now encompasses file and message integrity, sender authentication, and pseudo-random number generators.

This video is a collection of useful tips and tricks for solving the OLL (Orientation of the Last Layer) and the PLL (Permutation of the Last Layer) of the mighty Rubik's Cube.

See ten algorithms that if repeated enough times, will bring your Rubik's Cube back to the solve position.
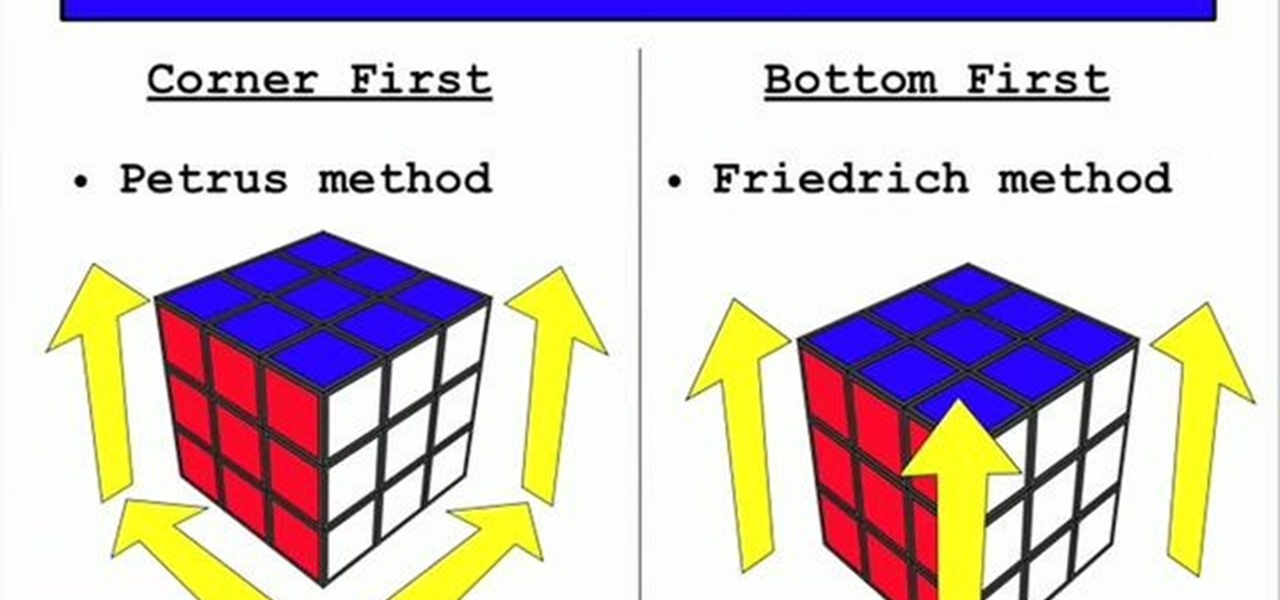
Learn how to solve a Rubik's cube in ninety seconds in this video. You'll learn that there are couple of common methods used to solve the cube. The Petrus method which starts with the corner and the Friedrich method which starts at the bottom and moves up. The presenter shows how he uses several methods and algorithms to create seven steps to a solved cube. The first step is to make a cross on the bottom layer. The second step is to correctly place the bottom corner pieces. The third step is ...
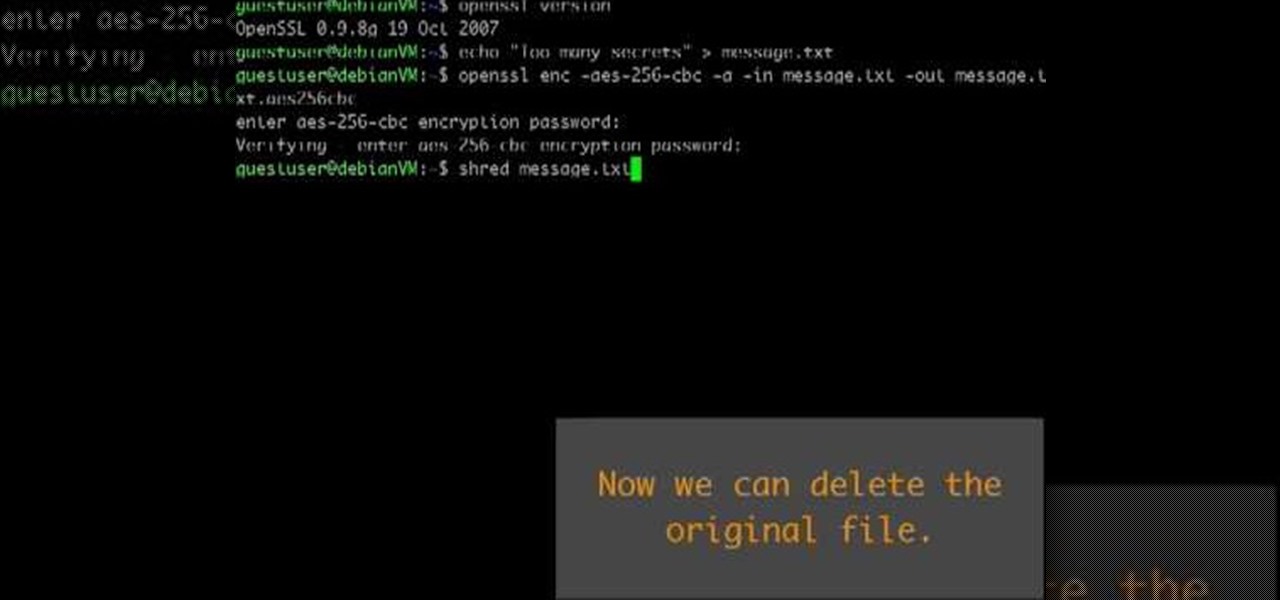
This video shows how to encrypt files with OpenSSL in Debian Linux. First we check if open SSL is installed on the system. If not, install it using packet manager. Next create the file going to be encrypted. Now encrypt the file. In this case AES algorithm in ypher block chaining mode is used. AES is US-government standard and can be considered secure. Now we are prompted for a password. In order for the encryption to be secure, we need to choose a strong password. Now we can delete the origi...

Solving puzzles can be hard, especially when it comes to Rubik's Cube. Erno Rubik's puzzles are extremely difficult, three-dimensional mechanical cubes, unless you're determined and can handle a few mathematical algorithms, then they're easy, or at least not impossible.

The Megaminx is a dodecahedron-shaped puzzle similar to the Rubik's Cube. It has a total of 50 movable pieces to rearrange, compared to the 20 of the Rubik's cube.

Want to solve the Rubik's Cube? Well, watch this how to video to know all about solving the troublesome Rubik's Cube. This three-part tutorial will go through seven steps to mastering the Cube. You'll need to lubricate the Cube first, with silicon spray, so it's lubed up nicely, for maximum speed. Then, start the steps.

Any internet user will need to download files eventually, and most simply have faith that what they are downloading is trustworthy. This doesn't give much clarity into the contents of the file, but if the file's author published the original checksum, comparing it to the SHA-256 hash of the downloaded file can ensure nothing was tampered with.

This video tutorial is for educational purposes only. See how to pick a normal lock with a tension allen wrench and a small screwdriver.
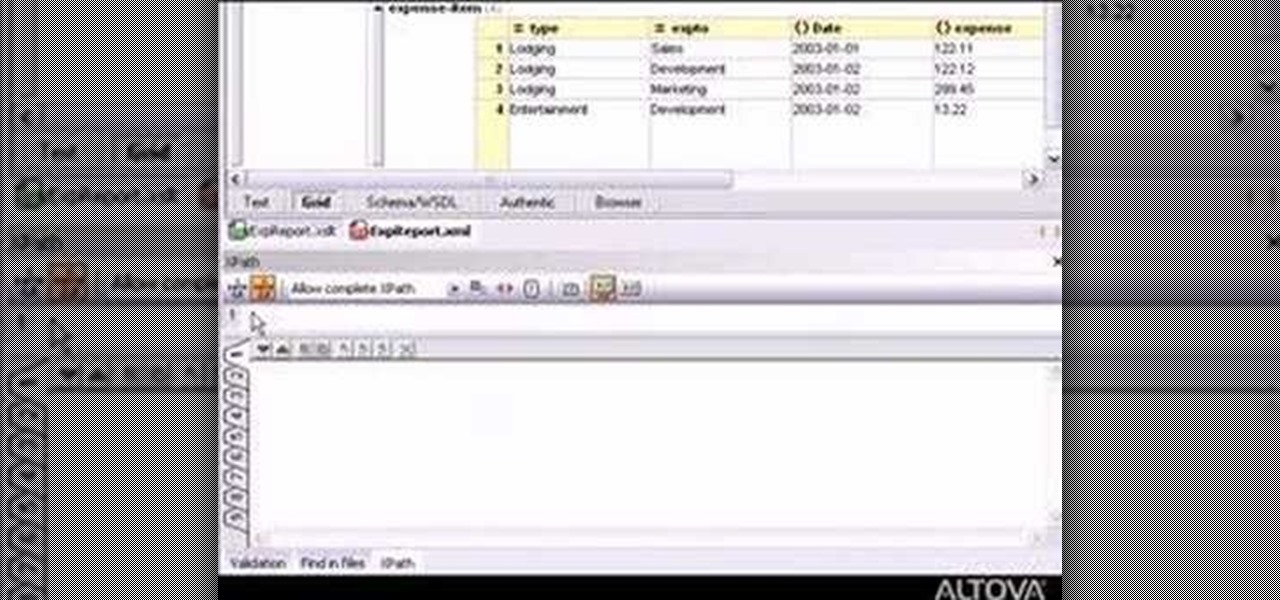
Desire to be an XML editor/programmer? This video will help you. You'll learn how to edit, analyze, and debug XPath expressions with XMLSpy.
Although early attempts at consumer smartglasses have employed trackpads and handheld or wearable controllers for user input, its the gesture control interfaces of the HoloLens 2 and the Magic Leap One that represent the future of smartglasses input.

Move over, cosmetics companies. The athletic footwear industry wants to be able to give their customers the opportunity to try on products in augmented reality as well.

When computers have vision but people don't, why not have the former help the latter? That's the gist behind the Cognitive Augmented Reality Assistant (CARA), a new HoloLens app developed by the California Institute of Technology.

While we've seen Snapchat apply sky segmentation to AR content, the makers of the Blue Sky Paint app have applied similar capabilities to create and share airborne art.

For younger children, a day at the playground is not complete without some sandbox time. Long a favorite of children and parents, sandboxes could also be sheltering dangerous pathogens.

In Bhopal, India, a place nestled in between the royally pink city of Jaipur and the dry (i.e., alcohol forbidden) state of Gujarat, is a team of developers determined to make a fully driverless car suitable to the complexities of Indian traffic. An algorithm elaborate enough has yet to be made by any other company, but is the fundamental key to handling the intuitive habits of Indian drivers, the often intense and gridlocked traffic, and the country's vast expanse of jarring roads.

Welcome back, my greenhorn hackers! The Holy Grail of any hacker is to develop a zero-day exploit—an exploit that has never been seen by antivirus (AV) and other software developers, as well as intrusion detection system (IDS) developers. In that way, you can exploit systems with your newly discovered vulnerability with impunity!

Welcome back, my greenhorn hackers! My preference for Linux as a hacking platform is well documented, and I have even created a series of tutorials to train new hackers. Without being proficient in Linux, you can't really call yourself a hacker.

Photo mosaics have interested me since I was a kid. I could never understand how someone took the time and effort to make one large masterpiece out of hundreds of smaller images. Maybe I'm too daft to grasp the concept, but it seems extremely difficult. I certainly don't have the necessary skills to make my own work of art, but luckily my Nexus 7 does.

Most of us have some sort of malware scanner or antivirus program on our computers, but what about our smartphones? A lot of people don't realize that computers aren't the only devices that are susceptible to malicious software and apps—they can follow you on your smartphone or tablet, too.

If you've wanted to solve the Rubik's Cube, there's no better tutorial than this. In this video, you'll learn how to solve the Rubik's Cube with the Fridrich Method.
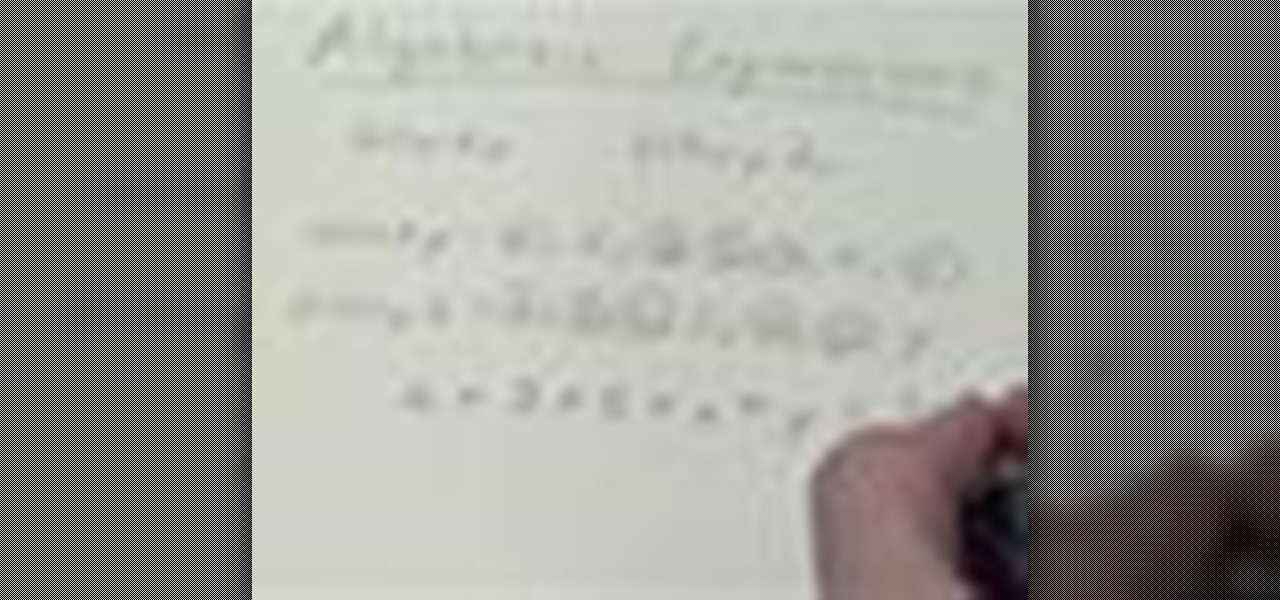
If you've ever been asked to find the GCF, or Greatest Common Factor, of a series of numbers or algebraic expressions, check out this video to learn how.

Need a new way to impress your friends and family? Watch this video tutorial to learn how to solve the Rubik's Cube blindfolded. To solve the Rubiks Cube blindly, use the Pochmann Method. You really need to practice this method to get it down, because there are many things to keep in mind.

We're living in a world that runs on Big Data. As the driving force behind everything from self-driving cars and Google algorithms to the latest medical technology and financial platforms, massive sets of increasingly complex data lie at the heart of today's most exciting and important innovations.

In today's data-driven world, being well-versed in Big Data and analytics can help land an exciting and high-paying career. Whether you're interested in working for a major tech company or pursuing freelance work in development, you need to have a thorough understanding of the latest and greatest platforms in analytics if you want to succeed.
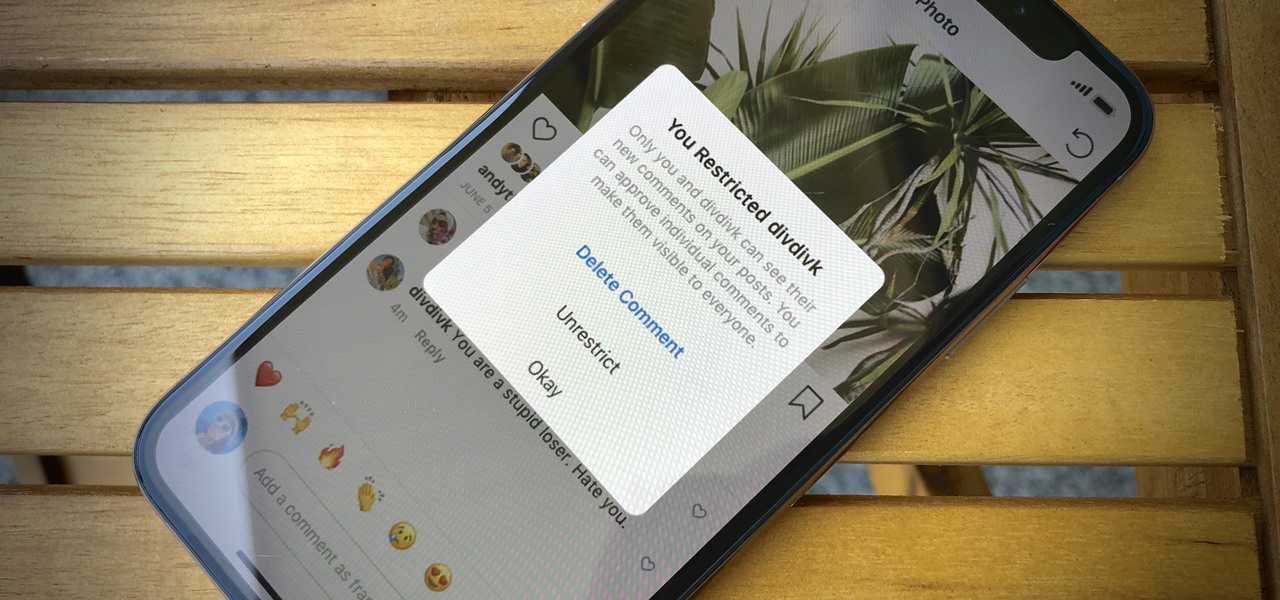
In general, the internet can be a cruel place, and Instagram is no exception. Most of the time, the platform is a fantastic way to share and view unique and creative content, to reach an audience of both fans and friends. People can step out of line and harass or bully others on posts to the detriment of the entire community. However, this type of commenting won't be sustainable for much longer.

Portrait mode works with any dual-lens iPhone, as well as the single-lens iPhone XR, and lets you take impressive portraits with blurry, bokeh-filled backgrounds. Portrait selfies, on the other hand, are only available devices with Face ID. But that's only for Apple's Camera app itself — third-party apps like Messenger have "portrait" selfies for any iPhone — as well as any Android phone model.

Your email inbox is a treasure trove of personal data. The people you contact, your writing style, which messages you flag as spam — all of this information and more can be used to paint a clear picture of you. Google knows this as well as anybody, so they use this data to constantly improve your experience in Gmail.
While augmented reality headset makers are faced with tackling numerous challenges before the category is truly ready for prime time, a start-up comprised of former Microsoft engineers may have nailed fast and precise tracking of hand gestures and full-body locomotion.