Samsung is rolling out the Android 6.0 Marshmallow update for Galaxy S6 and S6 edge today, February 15th, and with it come some good improvements to how S6 edge users can utilize the handset's curved screen.

Many users across the web have reported issues with receiving notifications from the Gmail and Hangouts apps on Android. The problem is most prevalent with users running Marshmallow, and the gist is that notifications from these apps are extremely delayed or don't come through at all.

Welcome back to another episode of Java Tutorials, In today's tutorial, we'll be learning about what methods are, proper syntax when writing Methods, and why they are beneficial in a program's code.
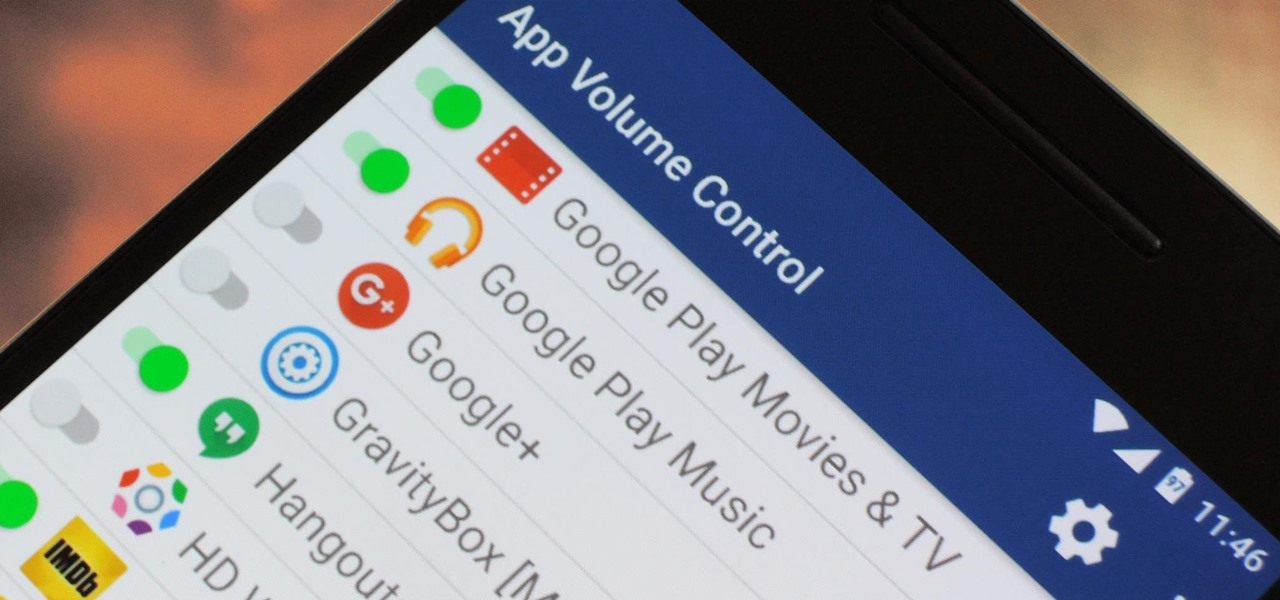
You can do practically anything with a modern smartphone or tablet, so it stands to reason that the apps you have installed may serve vastly different purposes. Picture a game and a video player sitting right next to each other in your app drawer—odds are, you want the sound turned up while you're watching videos, but would prefer that the game was muted or a little lower. As a result, we're constantly tweaking volume levels to get the best experience.

I mentioned in 2015 I wanted to start a 'DoXing' series, and since I havent seen this on Null Byte, I am now going to introduce this to the community.

Cast iron pans are a timeless treasure—they're an essential kitchen tool that will stand the test of time, and no home kitchen is complete without one. However, they do have a reputation for being difficult to care for... with arguments both for and against regular seasoning. In 2010, a blogger named Sheryl Canter claimed that she found the best way to season a cast iron pan that would keep the cast iron from rusting... or requiring re-seasoning! And after a few hands-on test by Cook's Illust...

Simmering or poaching food is a total pain sometimes. The problems are numerous: a layer exposed to air often dries out and creates a gross skin that can ruin the texture of the sauce, the poaching liquid evaporates too quickly and causes the poached protein to burn, and so on.

School internet filters serve a valid purpose—they keep students from wandering off into the deep corners of the web while still allowing at least some internet access. But a lot of these restrictions are completely ridiculous, to the point where some school districts block access to the educational material in National Geographic or forbid searching terms like "China," "Iran," or "Russia"—because, you know, breasts and commies.

Greetings null-bytians. Firstly, I would like to apologize for the no images thing. I guess I can't upload them.

Samy Kamkar, the security researcher known for the MySpace Worm and his combination lock cracking skills (using an online calculator), is back—and this time, he's after your credit cards!

I love making everything from scratch, but some things are just easier to buy. So there are times when you have to find a creative way to split the difference. For me, the easiest dish to buy without compromising on flavor is cornbread mix.

Cake decorating is one of those activities that used to leave my hands sticky and my spirits dampened. No matter what I seemed to do, the final result always ended up looking like a preschool art project.

When you're young, utensils tend to be optional—and eating with your hands is optimal. One of the best examples of finger food for kids that has pervaded today's nostalgia-driven culture is tater tots.

In this article, we will explore the basics of radare2, a powerful package that comes with Kali. We are going to write a simple program, and then disassemble it, to see what is really doing in the processor.

There are few things more satisfying than fulfilling a craving with instant gratification. Companies like Pillsbury and have made this possible with the introduction of their famous Ready to Bake Cookies line: just rip open the package, break off the cookies along the creased lines, place on a cookie sheet, and bake.

Welcome back, curious hackers! In today's tutorial, we will be diving deep into the manipulation of Google Operators, commonly referred to as "Google Dorks" in order to access Surveillance Cameras and other control panels.

Many home chefs are deterred from whisk-intensive recipes such as mayonnaise because they seem to require more than two hands—which is obviously the maximum number we possess. One hand is required to stabilize the bowl, another must be whisking constantly... and a third hand is needed to pour a steady stream of oil.

Welcome learners, lets us proceed further with the information we already have. In this post we will explore more about finding hacked accounts online. We will look into how to find juicy info in pastes which are deleted on Pastebin.

If there's a better way to impress your friends than with cocktails, I don't know what it is. Some nice glasses, quality spirits, and a recipe that doesn't involve pre-made margarita mix, and you'll automatically look suave. However, the most overlooked cocktail accoutrement (and the coolest, in both senses) is the ice.

If you've switched ROMs before or flashed quick mods on your Android device, you've probably used TWRP or another custom recovery to install them. But another great purpose for flashing through a recovery is to install your own custom .zip file filled with everything a fresh ROM needs—namely, all your apps.

Avocado is great in guacamole or as slices on a sandwich, but there's so much more you can do with this wonderful fruit (call it a vegetable, that's fine—but it's technically a fruit). While I could eat guac every single day, these are some of my favorite recipes to spice up avocados a bit, from making a guilty snack to a condiment and even dessert!

In this tutorial I will be explaining the purpose of unique encryption/decryption scripts ( I will be referring to these at "UEDS" for this tutorial). Then, I will show you how to make one. Finally I will talk about the downsides to the method I use. I will also provide links explaining the concepts and algorithms used in encryption to anyone who wants to see what is going on under the hood.

When I was a little kid, I was obsessed with shells. And while most of my shell collection came from combing the beach for treasure, some of it came from a different source: dinner. Whenever my parents had fresh clams or mussels, I would take the leftover shells, soak them overnight in soapy water, and add them to my collection.

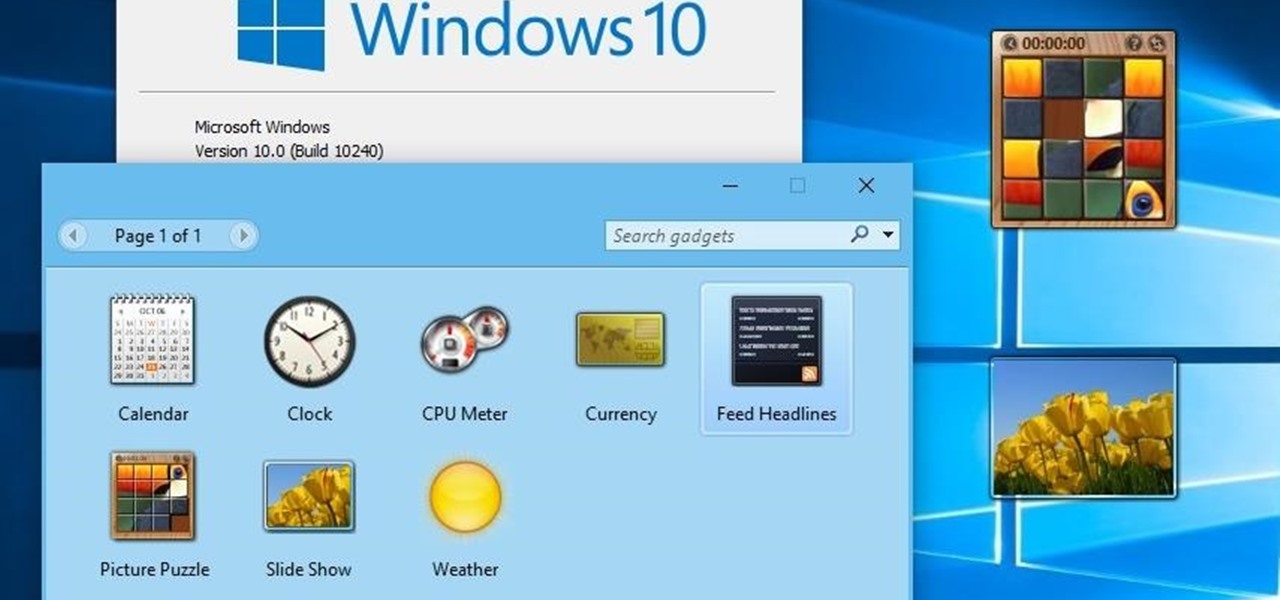
The concept of desktop gadgets has been around for quite some time, and Microsoft officially introduced them in Windows Vista to much fanfare. Desktop gadgets offered the ability to view various information at a glance, play mini-games, and more. Unfortunately, Microsoft decided to kill this beloved feature after Windows 7, citing security reasons.

There is no greater food to master than steak. If you can make a steak that's only marginally better than your neighborhood Applebee's, you'll still have friends waiting outside your door for steak night. And if you can make steak as good as that expensive gourmet steakhouse you went to for your birthday? Well, your popularity is about to increase dramatically.

If your PC setup includes a mouse and keyboard, you'll be happy to know that most of the touchscreen-first features of Windows 8 have gone by the wayside in Windows 10. Where it once required awkward gestures to access key features, Windows now recognizes when you're using a traditional desktop or laptop, then responds by making sure that all features can be easily discovered with clickable buttons and menu entries.

Most primary cocktail ingredients just sound delicious. Lime and tonic water? Yes, please. Bitters and simple syrup? Sign me up. Egg whites and... wait... egg whites? In a cocktail?

The next time you're out camping, whether it's outdoors in the wilderness or right outside in your own backyard, try this hack out for an effortless campfire all night long. While there is definitely some prep work involved, it's well worth it if you don't need a huge bonfire, and more so if you plan on cooking meals over the flames.

If you read my last tutorial on using SEToolkit, you probably know that SEToolkit is an effective way to make malicious actions look legitimate. But, that was only the beginning... the truth is, Metasploit and SEToolkit belong together, and help each other very well.

Disclaimer: All information in this tutorial is for entertainment and educational purposes ONLY. You pesky teenagers.

There are several reasons that you might want to restore the factory firmware on your device—maybe you need to send your phone back for warranty purposes, or perhaps you're getting ready to accept an over-the-air update and need to unroot first. In some cases, reverting to the stock firmware can even resurrect a soft-bricked phone.

Hi everyone! Last time we explained what roles Ebp and Esp registers have. We first introduced function's stack frame building, return address and calling conventions, but left some of the concepts floating without a full stop.

Google Play Music is an awesome app—even if you don't subscribe to their $9.99/month All Access service, you can still use it to store and stream up to 50,000 of your own songs for free. Add to that the fact that it's a pre-installed app on most Android devices, and there aren't many reasons not to be using Play Music.

Hi everyone! After messing around a little bit with IDA and Hopper disassemblers and briefly introducing you to memory, registers and Assembly, we are going to understand what happens when a process is running, which variables join the play and especially what happens when a function is called and why is this procedure-logic so interesting and useful along with the concept of stack.

Smartphone users often wish for a privacy, where no one is able to poke his/her nose in their personal stuff. Unfortunately, none of the smartphones have been able to guard their privacy in this fashion. Smartphones usually come up with none or almost negligible built-in security to serve your purpose.

Greasy fast food. Snacks. Candy. Empty stomachs. What do these all have in common? They're all things that people commonly have for lunch during the week, because it beats the hassle of having to plan, make, and pack lunches before their workday.

There are lots of great reasons for going out to a fantastic coffee shop for a cuppa. Coffee shops have a lovely ambiance, are a perfect place to meet with friends or do some work, and are a great excuse to get out of the house. Seeking out a perfect cup of coffee, however, shouldn't be one of the reasons that you hit up your local café.

Welcome back, my novice hackers! As we saw in my first tutorial on Facebook hacking, it is not a simple task. However, with the right skills and tools, as well as persistence and ingenuity, nothing is beyond our capabilities.

Don't leave your tongs out by the grill, as they are one of the most useful and versatile cooking tools to have in your kitchen. In my house, they come in a very close second to chopsticks, which I cook with everyday. Like chopsticks, they make it easy to delicately flip and turn food with precision. But unlike chopsticks, there's no learning curve, so anyone can use tongs for easier, simpler cooking.