Finished Act 1 (3 total) of Red Dead Redemption and it was disappointing. The act is divided into five important people who you have to do missions for in order to progress the story. Around five missions per person on average. Only Bonnie and the Marshall's story missions felt tied to the storyline. Dickens, Seth, and Irish's missions felt like they added nothing but padding to the game. Add that nothing that you do in the game affects the world around and it's like you never existed in the ...

Artist Austin Houldsworth of the UK has come up with a device that drastically speeds up the process of fossilisation. Entitled Two Million & 1AD, Houldsworth is capable of creating a fossil in a few months (which otherwise might require thousands of years). Houldsworth is currently experimenting with objects such as a pineapple and phesant, but ultimately hopes to fossilize a human. Houldsworth proposes:

Levon Helm... The longtime drummer for The Band , Levon Helm wore many musical hats throughout his long career, including multi-instrumentalist, songwriter, singer, impressario, studio owner, studio engineer and producer. He grew up working on a farm in Arkansas; his first instrument was guitar, which he began playing at ag eight, but after seeing the F.S. Walcott Rabbits Foot Minstrels, he decided to ...

Apple no longer has an exclusive province to LiDAR for the purposes of augmented reality. This week, headset maker Varjo unveiled its new VR-3 and XR-3 headsets, the latter of which includes LiDAR sensors and stereo RGB cameras to enable depth sensing and inside-out tracking of real-world environments for "pass-through" mixed reality experiences.

We've all seen the login pages that allow you to log in to third-party accounts using your credentials from Facebook, Google, or Twitter. It saves you the trouble of creating another account and remembering more passwords — but it can also become a privacy and security issue, which is why Apple created the "Sign in with Apple" feature for iOS 13.

You may have recently seen a plethora of Instagram users, including celebrities and politicians, sharing a screenshot declaring that the platform will implement a new "rule" where it would own and could use your photos and videos however it wishes. The screenshots are part of an internet hoax, one that's been around in one way or another since 2012, but what can Instagram actually do with your media?

Microsoft.com is one of the most extensive domains on the internet with thousands of registered subdomains. Windows 10 will ping these subdomains hundreds of times an hour, making it challenging to firewall and monitor all of the requests made by the operating system. An attacker can use these subdomains to serve payloads to evade network firewalls.

As you're surely aware, your phone can be used against you. Thanks to our cameras and microphones, a clever hacker can obtain access to your device and invade your privacy. But spying isn't limited to just these two sensors — gyroscopes, proximity sensors, QR codes, and even ads can be used to paint a very clear picture about who you are and what you're currently doing.

It finally happened! In a world of "go big or go home," Magic Leap has finally done something other than tease us with vague promises and rendered video concepts. Although, other than actually showing us what the developer's kit will look like, it seems little more than a slightly different kind of a tease. To demystify this new product, we here at Next Reality decided to put together what we know about the hardware.

PowerShell Empire is an amazing framework that is widely used by penetration testers for exploiting Microsoft Windows hosts. In our previous guide, we discussed why and when it's important to use, as well as some general info on listeners, stagers, agents, and modules. Now, we will actually explore setting up listeners and generating a stager.

Due to the overnight success of smartphones, millions of people are connecting with others. Currently, over 15 million text messages are sent every minute worldwide. Most of this communication is happening in the open where any hacker can intercept and share in the discussion unbeknownst to the participants. However, we don't need to communicate insecurely.

In 2013, Offensive Security released Kali Linux, a rebuild of BackTrack Linux derived from Debian. Since then, Kali has gone on to become somewhat of a standard for penetration testing. It comes preconfigured with a collection of tools accessible by a menu system, tied together with the Gnome desktop environment. However, Kali Linux isn't the only penetration-testing distribution available.

Welcome back, everybody. In the previous article, we covered the ideas and concepts of well-known ports and trust exploitation in order to evade a firewall. Today, we'll be building the shell, the part that receives commands, executes them, and sends the output back to the attacker.

Even those of us most comfortable in the kitchen can be daunted by the idea of cooking for a whole houseful of people. Whether you have a large, well-equipped kitchen or a small one with just the essentials, it can prove to be quite a task to prepare food for a dozen or so people. It takes a certain type of recipe that allows for mass production, in respects to both technique and ingredients. And what I've provided below includes several recipes that you might normally make for just a family ...

Dinner is meant to be enjoyed after a long day away from home—it shouldn't cause stress or fuss. But for many, that's exactly what a home-cooked meal represents, especially on a work night. The prep work, the steps involved in following the recipe, the numerous amount of bowls, pots, and pans you use, and... worst of all, a sink full of dishes to clean.

Welcome back, my rookie hackers! As hackers, we are often faced with the hurdle of cryptography and encryption. In some cases, we use it to hide our actions and messages. Many applications and protocols use encryption to maintain confidentiality and integrity of data. To be able to crack passwords and encrypted protocols such as SSL and wireless, you need to at least be familiar with the concepts and terminology of cryptography and encryption.

There's a lot that goes into making a nice crystal radio set, so this is going to have to be broken down into two parts. The first part is the actual making of a functional radio, and the second part is making the whole arrangement look nice. In this part, I'm actually going to tell you more than just how to make a crystal radio, but I'm also going to explain how and why they work. Crystal radios are pretty Steampunk in and of themselves, since they were first developed in the late 19th centu...

From A Hamburger Today: your guide to regional hamburger and cheeseburger styles. What red-blooded American doesn't love hamburgers? Think you're an enthusiast? Think again. There's more to the burger than the Big Mac (though the Big Mac is included in this guide, of course).

Deadly natural disasters can happen at any moment— earthquakes, hurricanes, tsunamis, floods, fires and especially tornadoes. That's why you have to be prepared.

Get lots of fake blood, put it in little packets that can be broken easily. Strap someone up with rollerblades and knee pads helmet etc. Put the fake blood pouches on your body, tape them ore something, then go to a area where there's stairs and lots of people and attempt to jump them or roll down them. You fall on purpose and make sure you pop all the fake blood packs (have some in your mouth and helmet). act like your in serious pain and get up all dazed and confused. Quickly stumble or bla...

Who would have thought that dryer sheets can be a quick remedy for super-staticky flyaway hair? But it's true. It's all about the positive charges in the sheets and their ability to neutralize electron buildup. And that's not the only surprising quick fix for hair problems that you can easily find in your home.

This is a refreshing spring update on your classic hamburger slider. Instead of using a ground beef patty, I am using shrimp tempura. This recipe calls for fresh truffles, but fresh truffles are hard to come by so feel free to use truffle oil (it is much more affordable and what I usually like to use). The flavor will be just as good.

One of the hardest parts of entering the IT and computer science field — other than the difficult material and intense competition — is the time and financial cost of learning everything you'll need. Learning to code isn't just learning one language; you have to learn a variety of languages used for different purposes, and then you have to get experience using them.

No matter the field you work in, tech dominates every industry in 2020, and that means that you can always increase your earning potential by adding valuable coding skills to your arsenal. Coding can lead to dream software development career paths, lucrative freelance work, and it can be an impressive boost to your résumé. Now, you can learn these valuable skills at home with The Complete One Hour Coder Bundle, an offer at an unmissable 97% off its usual price, at just $34.99 (usually $1,200).

Password cracking is a specialty of some hackers, and it's often thought that raw computing power trumps everything else. That is true in some cases, but sometimes it's more about the wordlist. Making a custom, targeted wordlist can cut down cracking time considerably, and Wordlister can help with that.

Congratulations, you've made it deep into the middle of flu season! If you're reading this, you're either a very smart preemptive sick day prepper, or already in the throes of fighting off a cold or flu situation.

Not that long ago, touchscreen-friendly gloves were an outlier accessory, something you had to track down at a specialty brick-and-mortar store or solely online. But as the smartphone has become an integral part of our lives, so, too, has the need for fashion accessories that cater to our desire to be always connected. So now, touchscreen gloves are everywhere.

Magic Leap's legal battle against Nreal has taken an intriguing turn this week, as Magic Leap set a date to discuss the matter with Nreal. But a new partnership struck by Nreal adds another wrinkle to the duel between the two AR wearable makers.

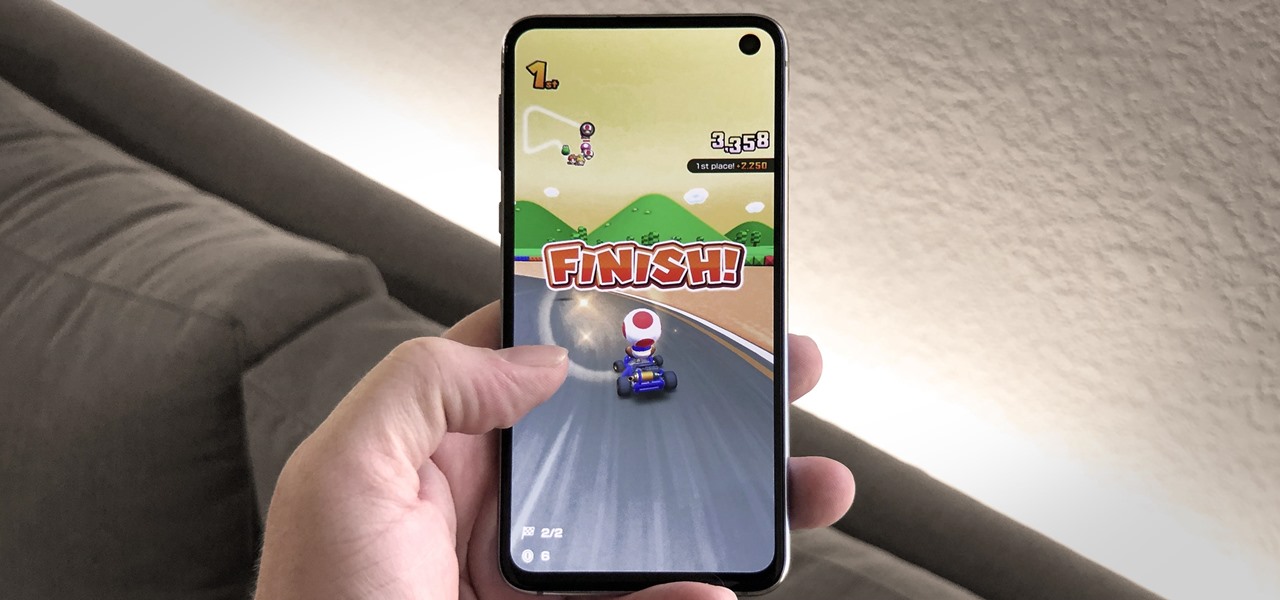
So you can't seem to win in Mario Kart Tour? Whether it's your first game in the Mario Kart series or not, Mario Kart Tour can be challenging, especially when you don't know the tracks. Instead of struggling your way through the cups, try out these five tips to get a leg up.

Apple might not be ready to unveil its rumored-yet-unconfirmed smartglasses. But the iPhone's current depth-sensing hardware is proving to be useful for both smartglasses makers and mobile AR apps.

Gboard is often considered the best keyboard for iPhone or Android. Google made sure to jam-pack it full of features, and you should expect nothing but the best when it comes to Google's own first-party software. But with so many capabilities, a few things might slip through the cracks.

Apple's latest updates to its operating systems add another security feature to its Find My service, so you have an even better chance at locating your lost iPhone, iPad, or Mac should it ever happen. As long as you have the option enabled, you can leverage other Apple users' devices to find yours on the map.

OnePlus has purposefully made their devices easy to root so that you can spend less time waiting and more time doing. These phones are a solid choice for anyone looking to dive into the rooting and modding scene. Using the same principles that Google has with the Pixel line, you can always be sure your OnePlus 7 Pro will get first-class treatment from launch day and beyond.

The OnePlus 7 Pro is truly the best phone that the company has ever created to date — it's even one of the hottest phones around regardless of OEM. It offers an awesome display with minimal bezels, a smooth 90-hertz refresh rate, a pop-up selfie camera, and the best triple camera system in a OnePlus phone so far. It can truly compete with other flagship phones while keeping the cost down.

In about 27% of all car crashes, someone was using their cell phone. You may think texting is the big problem here, but many fail to realize that even the smallest smartphone interaction could spell disaster. Thankfully, Google Maps has rolled out an overdue feature that'll help ensure a safer drive.

As great as passcode and biometric security features like Face ID are for preventing unwanted access, they aren't needed 100% of the time. When you're at home with a locked door between you and anyone you wouldn't trust with your phone, they really only serve to slow you down. Android has long had a solution for this, but a new Cydia tweak has now brought a similar solution to iPhones.

Imagine this: you have your finger poised to take the perfect picture — a once in a lifetime opportunity, like a solar eclipse — and you are suddenly caught off guard by a buzz, then "ding!" You look down at your phone to find your perfect pic ruined by distortion from the vibration, all because of an ill-timed notification. It's enough to make you crazy, especially when you find out it could have been prevented.

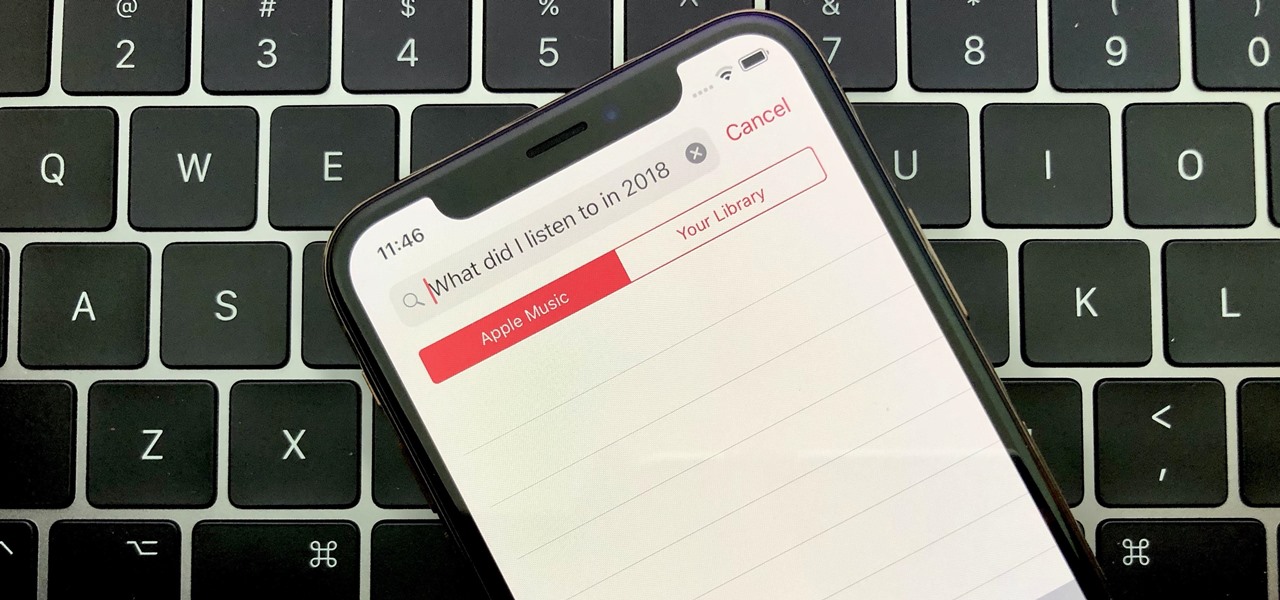
Around the end of each year, Spotify offers a year-in-review service so its users can see what they listened to the past year and share their listening histories in fun infographics. Apple Music does not have such a feature, unfortunately, but there is a way to curb that FOMO feeling this holiday season by downloading your listening history not just for 2018, but for the entire lifespan of your account.

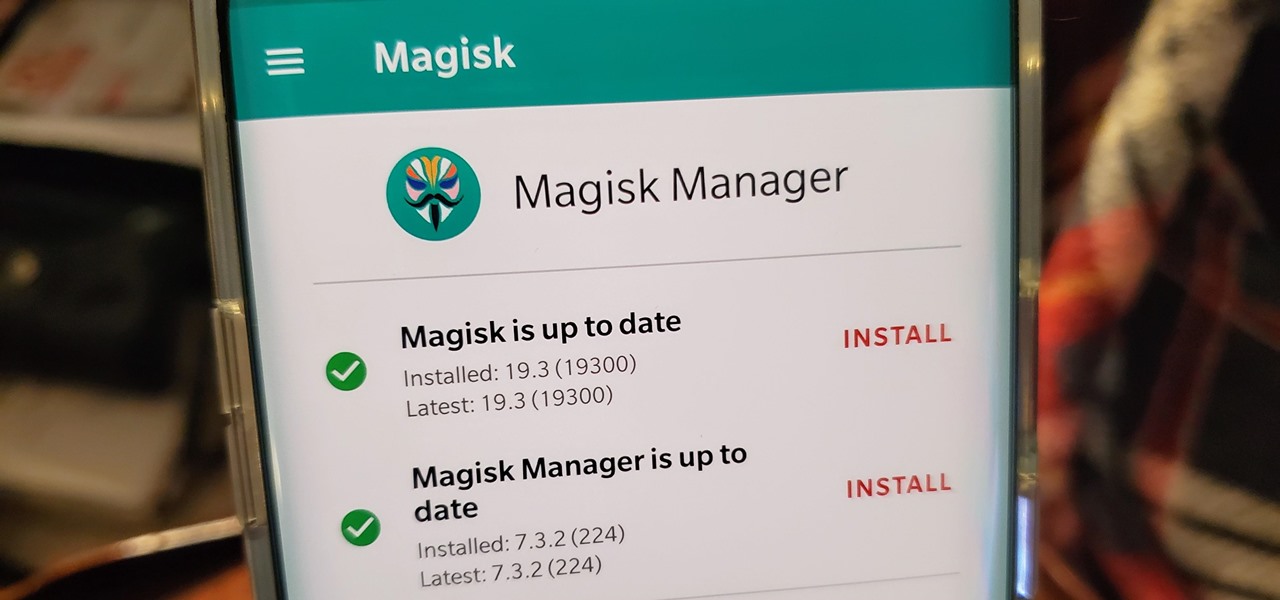
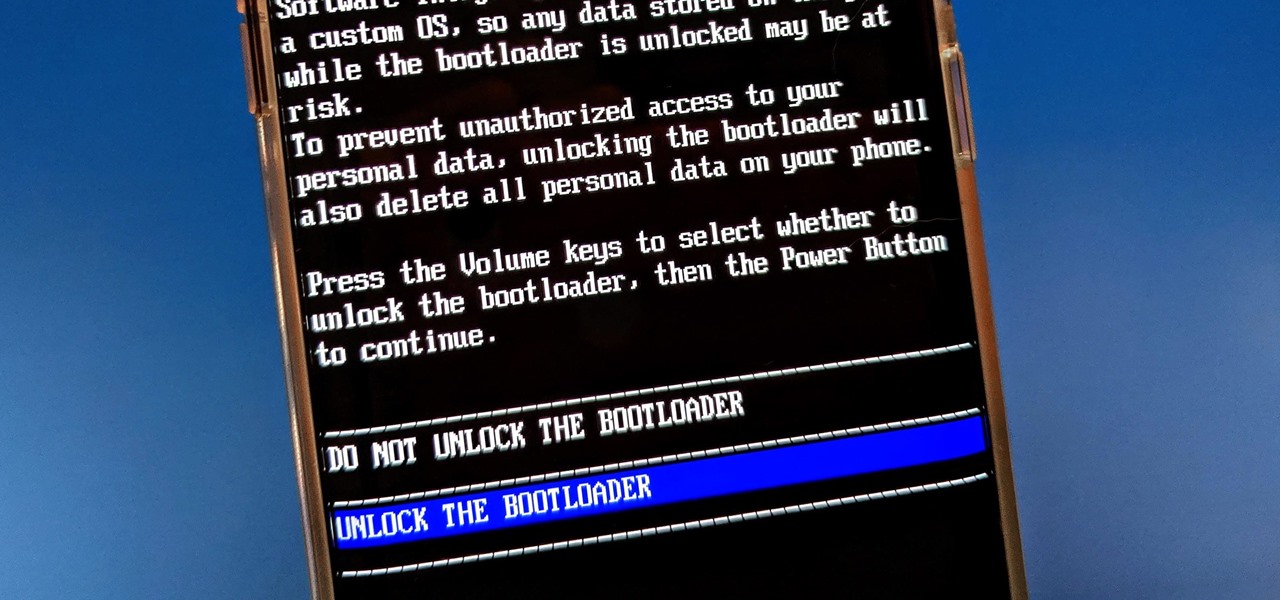
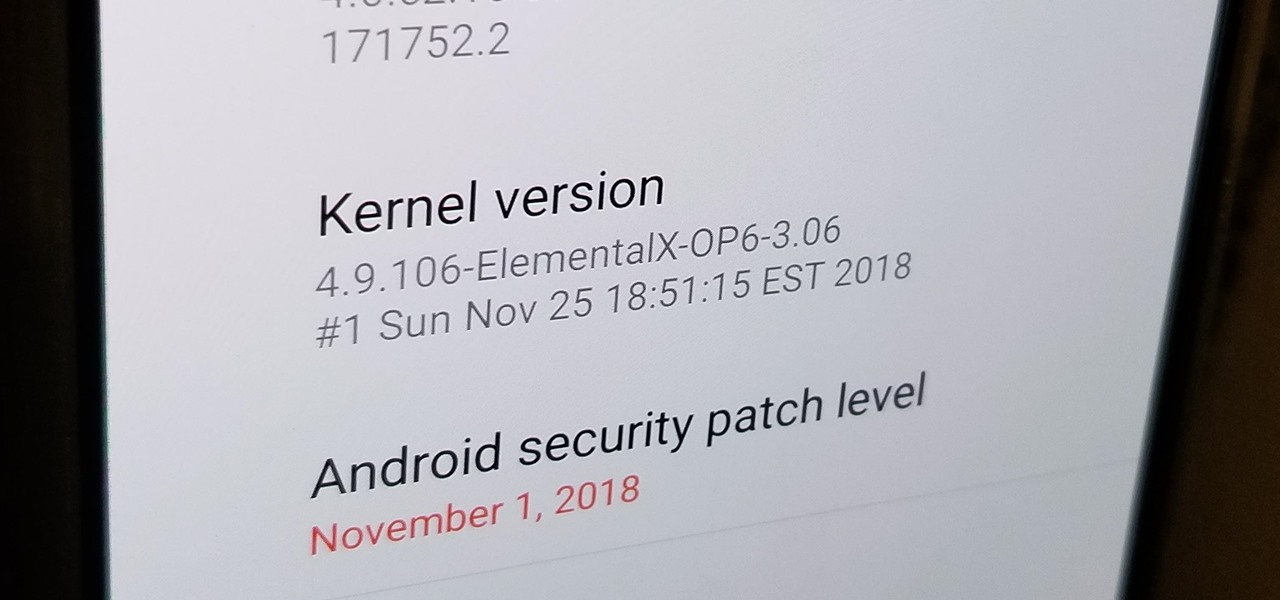
After you unlock the bootloader, install TWRP custom recovery, and flash Magisk to gain root access, what might be the next step of your modding adventure? A custom kernel, of course! Flashing a custom kernel onto your device gives you a whole new level of tweaks and customizations, and it allows you to have full control over how your system performs.

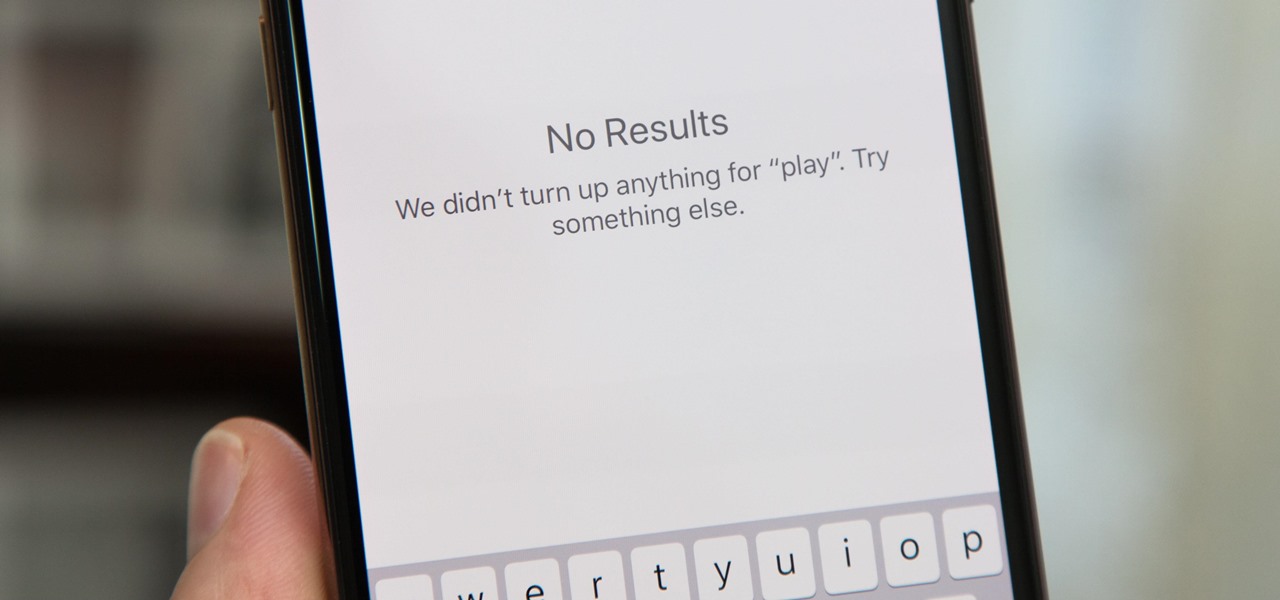
There's something seriously wrong with Apple's new Shortcuts app, and it's severely limiting the number of shortcuts users can install on their iPhones.