On Yelp, you have the option to check in to a business you're visiting. For you, broadcasting who you're with and where you're at is fun for social purposes, but for business owners, you're basically giving them free publicity. Well, almost free publicity. Since there's incentive to get you to check in, some businesses reward customers with special deals, such as 20% off your first visit.

Microsoft Office files can be password-protected in order to prevent tampering and ensure data integrity. But password-protected documents from earlier versions of Office are susceptible to having their hashes extracted with a simple program called office2john. Those extracted hashes can then be cracked using John the Ripper and Hashcat.

The Moto G7 Power is a phone that screams battery life. From its display resolution to the massive battery, it was designed for those who hate to recharge each night. But unlike other battery-focused smartphones, it comes at a price almost anyone can afford.

Almost every phone comes with biometric security of some sort these days, but the same can't be said of Windows computers. While fingerprint scanners are becoming increasingly common with laptops and desktops, they're nowhere near ubiquitous. Thankfully, your phone's scanner can be used as a sort-of remote authentication point for your PC.

The week of the annual Consumer Electronics Show is supposed to be filled with good news for the augmented reality industry as AR headset and smartglasses makers show off their new wares.

Many popular IoT devices have terrible security. For instance, a hacker who's on the same Wi-Fi network as a Sonos speaker can assume direct control over the device's behavior. If an IoT device doesn't secure the messages used to control it over a network, it's easy for somebody to write a few Python scripts to make it do whatever they want.

The last time we heard from Meta, the makers of the Meta 2 augmented reality headset, things looked pretty bleak. Now, as several new facts have come to light, we have confirmation regarding the beleaguered company's fate: Meta is done.

One of the ultimate goals in hacking is the ability to obtain shells in order to run system commands and own a target or network. SQL injection is typically only associated with databases and their data, but it can actually be used as a vector to gain a command shell. As a lesson, we'll be exploiting a simple SQL injection flaw to execute commands and ultimately get a reverse shell on the server.

Stumbling upon a specifically tailored advertisement on your iPhone can be a bit disconcerting. But that's what happens when you let advertisers track your data. Some of you may appreciate more relevant ads in apps, but the rest of you might consider it a straight-up privacy invasion.

If you store important, sensitive information on your iPhone in Notes, you'll want to be more careful. When Notes syncs across your iPad and Mac via iCloud — devices that family members or coworkers may share — you run the risk of having your notes read, edited, and deleted by other people. Such a catastrophe is easily avoided.

The ability to execute system commands via a vulnerable web application makes command injection a fruitful attack vector for any hacker. But while this type of vulnerability is highly prized, it can often take quite a bit of time to probe through an entire application to find these flaws. Luckily, there is a useful tool called Commix that can automate this process for us.

Influencers of augmented reality demonstrate expertise in their fields and outline a strong vision for the future that they evangelize to others. They help define the direction of the industry and identify others who foster and create innovation in the field.

If you've been getting that "Please update from the iOS 12 beta" alert continuously in iOS 12 public beta 9, Apple just issued a fix for it Friday, Aug. 31, with iOS 12 public beta 10 — just in time for Labor Day weekend. This marks the second update this week as dev beta 11 and public beta 9 were released on Monday. It's also just one day after Apple announced its Sept. 12 event.

It's always a good idea to know how an attack works at the very basic level. Manual techniques for exploitation often find holes that even the most sophisticated tool cannot. Sometimes, though, using one of these tools can make things so much easier, especially if one has a solid foundation of how it works. One such tool can help us perform a cross-site request forgery with minimal difficulty.

In a surprise twist, Apple released iOS 12 public beta 8 to software testers on Thursday, Aug. 23, right alongside iOS 12 dev beta 10. The release comes as a bit of a shock, as the company released iOS 12 public beta 7 just three days earlier. The official build of iOS 12 now feels closer every day.

We're nearly there — Apple released the seventh iOS 12 beta to developers Monday, August 13. While not totally unexpected, beta testers understand the struggle of predicting the next update, as Apple has switched haphazardly between two-week, one-week, and irregular release schedules for both the developer and public betas.

You can never replace the skills and expertise of a professional graphic designer, but Canva comes pretty damn close. It's ridiculously easy to use the drag-and-drop design tool for both professionals and people like me who don't have the need (or knowledge required) to use more advanced graphic design software.

One of the most critical bugs to come out in the last five years was Shellshock, a vulnerability which allows attackers to execute arbitrary code via the Unix Bash shell remotely. This vulnerability has been around for a while now, but due to the ubiquity of Unix machines connected to the web, Shellshock is still a very real threat, especially for unpatched systems.

Command injection is a technique used by hackers to execute system commands on a server, usually via a web application or some kind of GUI. This can happen when an application provides some sort of functionality to the user involving the use of system commands. When the input is not properly sanitized, commands not originally intended to be run are allowed to be executed.

It always helps to be prepared for the worst. This applies to our phones now more than ever, as we depend on them to be our record keepers for text messages from friends, family, and coworkers. If you ever lose or severely damage your phone, having a backup of your precious texts gives you the peace of mind of knowing that you can always get them back.

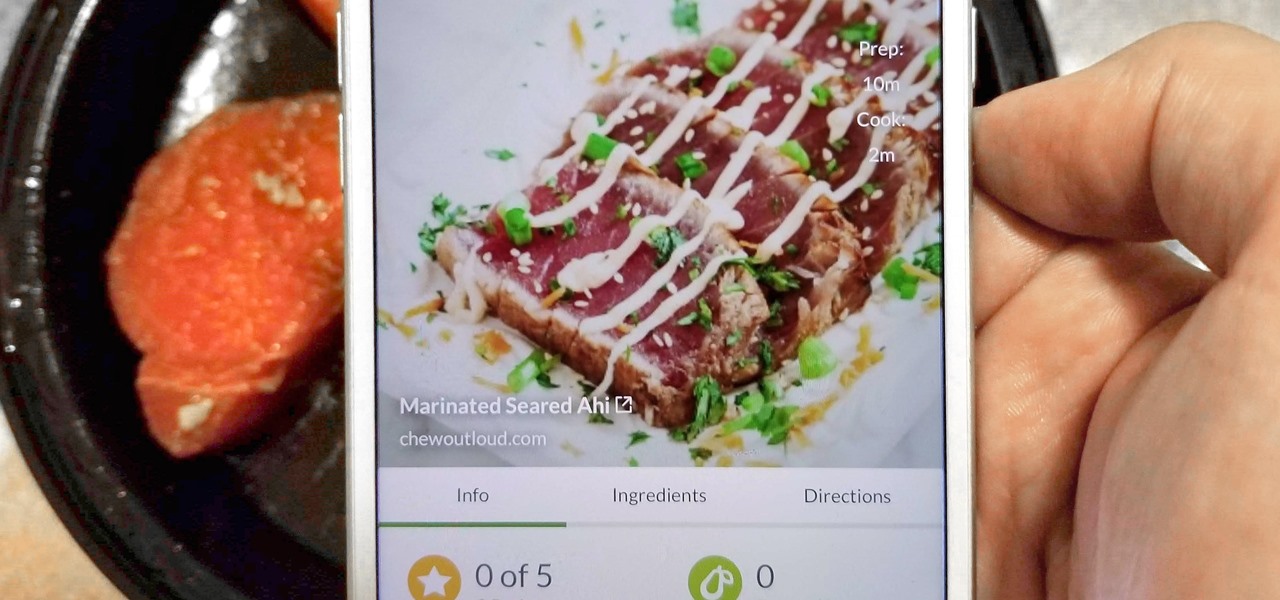
With Tasty dominating Facebook videos and online cooking flourishing, it can be cumbersome to keep track of all your recipes. Someone might send you something, and storing it in an app like Pocket is like jamming all your school papers in one folder — it just isn't practical. Fortunately, there's a better way to catalog your recipes so you can always have them on hand.

Database technology has vastly improved the way we handle vast amounts of data, and almost every modern application utilizes it in one way or another. But the widespread use of databases naturally invites a slew of vulnerabilities and attacks to occur. SQL injection has been around for awhile, and as such, there are many defense methods in place to safeguard against these types of attacks.

Once a hacker has created a PowerShell payload to evade antivirus software and set up msfconsole on their attack system, they can then move onto disguising their executable to make it appear as a regular text file. This is how they will get a Windows 10 users to actually open the payload without knowing they are doing so.

Apple removed the Wish List feature from the App Store when iOS 11 was released, which was a huge disappointment, to say the least. While the Wish List still remains in the iTunes Store, it seems gone for good for apps, but that doesn't mean you can't still keep a wish list of interesting apps and games to buy later — using software already on your iPhone.

One of the primary factors that separates an augmented reality device from a standard heads-up display such as Google Glass is dimensional depth perception. This can be created by either RGB cameras, infrared depth cameras, or both, depending on the level of accuracy you're aiming for.

Analysis of photographs and social connections can be a huge component of social engineering. Understanding who a person is, as well as who they know, can establish links within a company. This information could be used by hackers to execute elaborate social engineering attacks.

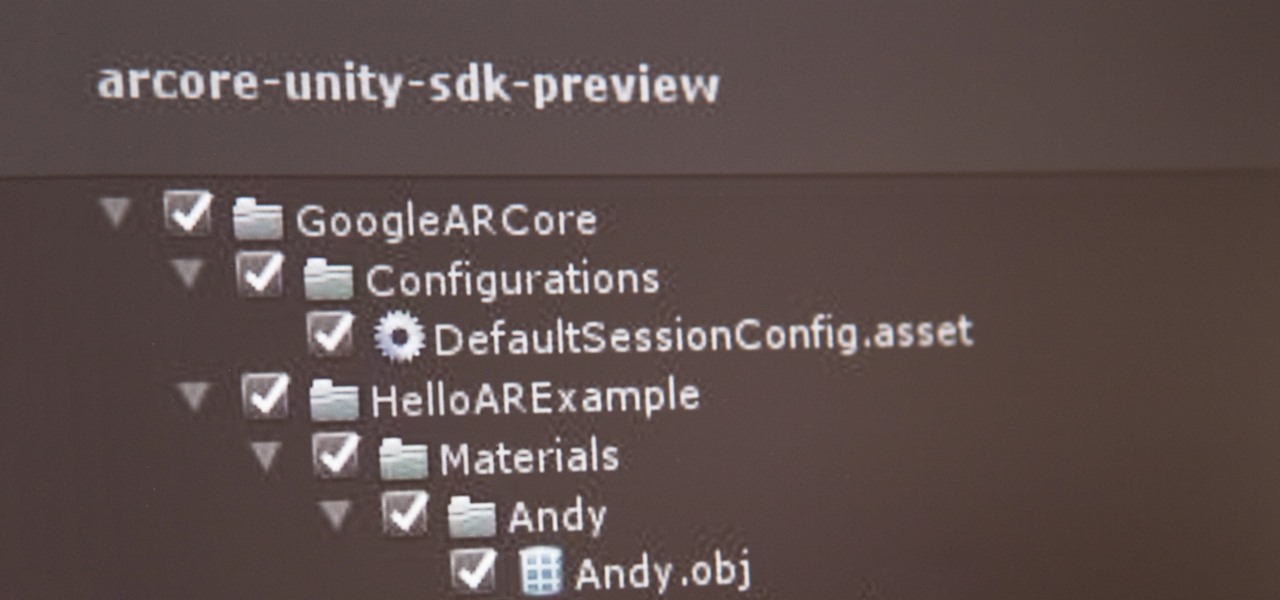
If you've contemplated what's possible with augmented reality on mobile devices, and your interest has been piqued enough to start building your own Android-based AR app, then this is a great place to to acquire the basic beginner skills to complete it. Once we get everything installed, we'll create a simple project that allows us to detect surfaces and place custom objects on those surfaces.

If bezel-less was the goal of OEMs in 2017, 2018 seems to be the year of the notch. Thanks in no small part to Apple's iPhone X, more and more smartphone manufacturers are designing their displays with this polarizing cutout. While many are frustrated with the trend, it's worth taking the time to consider what each phone gains with the unique design.

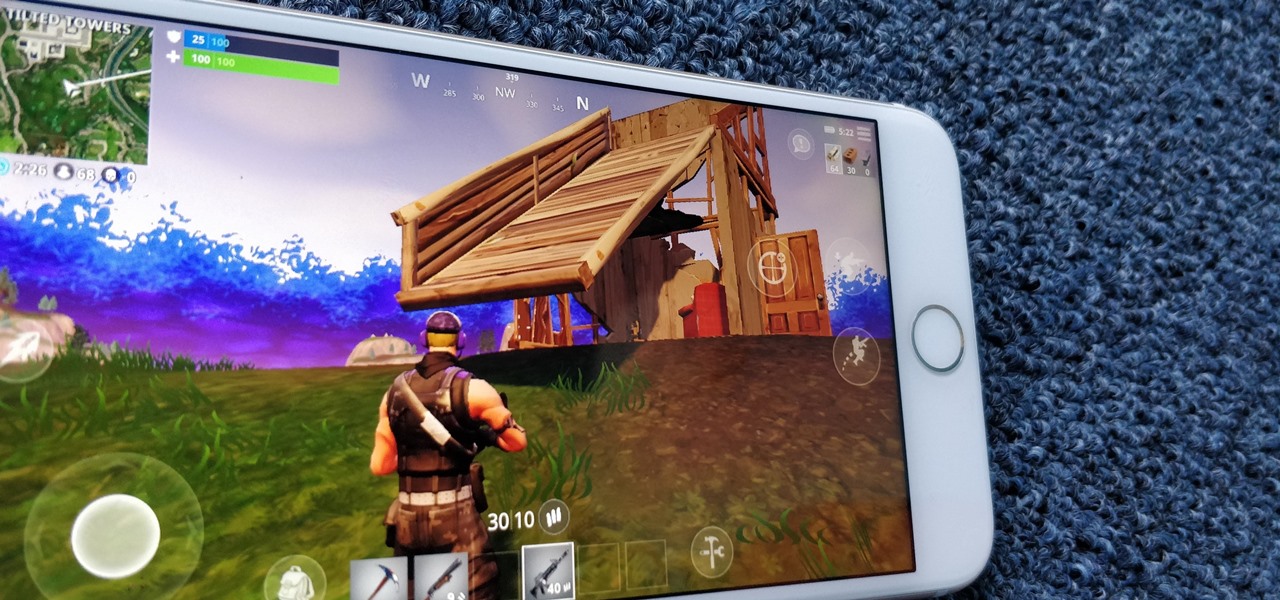
One of the more unique aspects of Fortnite Battle Royale is the ability to create structures. Using in-game materials, players can create walls and ramps for cover and to extend mobility. But creating isn't limited to just the basic generic structures. To really maximize their benefits, great players edit their creations to fit their needs.

When your iPhone is being sluggish, one thing you can do to get performance back up to snuff is clear the device's random access memory. It's not a publicized feature from Apple, but it's there nonetheless. And while it's easy enough to utilize on iPhones with Home buttons, the iPhone X is a little trickier.

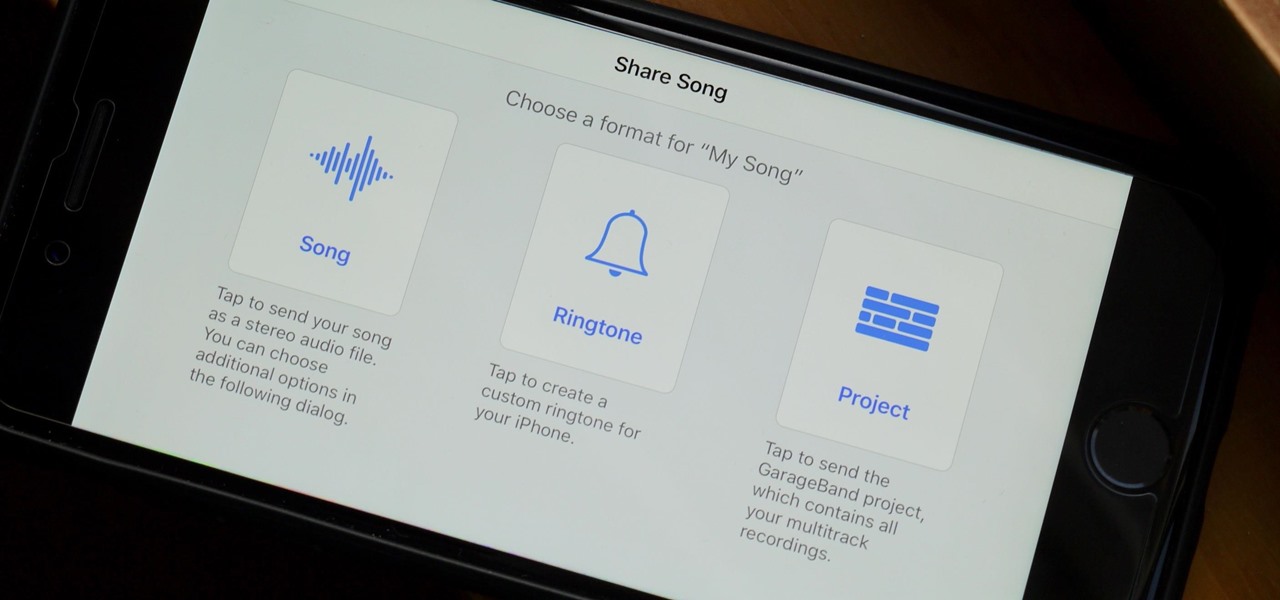
When you make an awesome song or beat that you're proud of in GarageBand for iOS, one way to show it off is to turn it into a ringtone or alert tone for your iPhone. That way, anytime you get a phone call or a notification, your musical creation will sound off, and everyone around you will hear it in all its glory. Plus, it's way cheaper to make your tones than to buy them off of iTunes.

Snapchat is in the midst of a massive redesign — one that not everyone loves. Still, it's clear that this is a decision fueled by money, and Snap Inc. believes this redesign will help attract more advertisers. Even so, Snapchat has a few more tricks up their sleeves to make a little extra dough. And while the average user couldn't care less about ads, they very easily could care about custom Filters and Lenses.

Coinhive, a JavaScript cryptocurrency miner, was reportedly discovered on the BlackBerry Mobile website. It was placed there by hackers who exploited a vulnerability in the site's e-commerce software that allowed them to anonymously mine cryptocurrency every time the website was viewed. There's no doubt Coinhive, an innovative mining method, is being abused and exploited by hackers in the wild.

The nemesis of music streamers is data caps, cell phone or otherwise. Restricting monthly data and forcing users to decide between quantity and quality of music has had audiophiles tearing their hair out since streaming toppled the iPod. While the problem regarding music quality seems difficult to tackle, it's far from impossible.

Whether you're white hat, black hat, or some shade in-between, navigating through a network is a core part of hacking. To do that, we need to be able to explore a network to discover the addresses of gateways, interfaces, and other attached devices. When ifconfig just isn't enough, you can steer your way around a network with a convenient tool called Ship, the script for everything IP.

Introduced along with the iPhone X, Animoji are animated characters, mostly animals, that are rendered from the user's facial expressions using the device's TrueDepth camera system to track the user's facial movements.

So after setting everything up, creating the system, working with focus and gaze, creating our bounding box and UI elements, unlocking the menu movement, as well as jumping through hoops refactoring a few parts of the system itself, we have finally made it to the point in our series on dynamic user interfaces for HoloLens where we get some real interaction.

With the V30, LG has really delivered an amazing smartphone that hits all the major features consumers want. Amazing camera, beautiful edge-to-edge display, great battery life, water resistance, and smooth performance — there isn't much not to like about the LG V30. Unfortunately, it does suffer from heavy bloatware thanks to the carriers. The good thing is, unlike in the past, you are not stuck with it.

The Pixel 2 is a solid upgrade when compared to the 2016 model, but we've reached a point where the latest generation of a smartphone is never leaps and bounds better than the last. It's hard to justify dropping nearly a grand on a phone when it doesn't improve your situation much — especially when a few software tweaks will give you most of the upgrade for free.

Code execution in Microsoft Word is easier than ever, thanks to recent research done by Etienne Stalmans and Saif El-Sherei. Executing code in MS Word can be complicated, in some cases requiring the use of Macros or memory corruption. Fortunately, Microsoft has a built in a feature that we can abuse to have the same effect. The best part, it does so without raising any User Account Control security warnings. Let's look at how it's done.