When you want to install a new tool or game on your iPhone, you go straight to the App Store to do so — but it's not the only place you can get apps from. Some developers use back alleys to get their apps to you, while others can trick you into installing them without giving it much thought. This can lead to malicious software running on your iPhone, software you'll want to get rid of asap.

Auditing websites and discovering vulnerabilities can be a challenge. With RapidScan and UserLAnd combined, anyone with an unrooted Android phone can start hacking websites with a few simple commands.

The Raspberry Pi Zero W and Pi 3 Model B+ include integrated Wi-Fi, Bluetooth Low Energy, and more than enough power to run Kali Linux. They sound like perfect all-in-one penetration testing devices, but the lack of support for monitor mode and packet injection usually meant buying a supported Wi-Fi adapter. Now, it's possible to use monitor mode on the built-in Wi-Fi chip with Nexmon.
Expressing yourself during chats is much easier these days thanks to the steady rise of emoji. Now, products like emoji Minis for Gboard are taking the craft to an interesting yet familiar new level. With emoji Minis, you can automatically create stickers based off your own face. From there, you can further customize the stickers by adding key features such as glasses, earrings, and facial hair.

Apple officially released iOS 12 to everyone on Sept. 17, and while the new iPhone XR, XS, and XS Max will come with the software by default, you have a choice on whether or not to update your current iPhone model from iOS 11. There are a lot of tempting features to want to update right away, but there are also some compelling reasons to wait it out and install at a later time.

Something that always brings a tear to my eye is uninspired Instagram stories. When you have a bunch of like-minded friends, you end up with like-minded stories. While it may seem difficult to stand out, stickers were designed so that you can differentiate yourself from other users — and knowing everything there is to know about Instagram stickers will make you a sticker master.

Developed by Open Whisper Systems, Signal is a free, open-source encrypted communications app for both mobile and desktop devices that allows users to make voice calls, send instant messages, and even make video calls securely. However, a vulnerability was recently discovered for the desktop version that can be turned into a USB Rubber Ducky payload to steal signal messages with a single click.

Single sign-on (SSO) lets users login across different sites without having to manage multiple accounts. I'm sure most of us appreciate the convenience of seeing "Sign in with …" buttons that let us login with a single username. Hackers, however, see a possible avenue for exploitation, and you'll soon learn how an attacker can exploit a SAML vulnerability to assume another user's identity.

Hashes containing login passwords are transmitted between Windows computers on local Wi-Fi networks. By intercepting and decrypting these hashes using Responder and John the Ripper, respectively, we can learn a target's login credentials which can be later used to gain physical access to their computer.

While the security behind WEP networks was broken in 2005, modern tools have made cracking them incredibly simple. In densely populated areas, WEP networks can be found in surprising and important places to this day, and they can be cracked in a matter of minutes. We'll show you how a hacker would do so and explain why they should be careful to avoid hacking into a honeypot.

Between the Cambridge Analytica scandal and the revelation that Facebook logs your calls and text history on Android, many are considering joining the #DeleteFacebook movement. But it can be difficult to leave the site, because so much of its content is only available to active users. If you want to keep in the loop without sacrificing your privacy, you'll want to follow the steps below.

After a hacker has configured Metasploit on a remote private server, created a resource script for automation, and created a simple payload, he or she can begin the process of remotely controlling someone's Windows 10 computer with just a few moments of physical access — even if the computer is off.

As we aim for a wireless world, technology's reliance on cloud computing services is becoming more apparent every day. As 5G begins rolling out later this year and network communications become even faster and more reliable, so grows our dependency on the services offered in the cloud.

Using just a small sticky note, we can trigger a chain of events that ultimately results in complete access to someone's entire digital and personal life.

As a developer, before you can make augmented-reality robots that move around in the real world, controlled by a user's finger, you first need to learn how to harness the basics of designing AR software for a touchscreen interface.

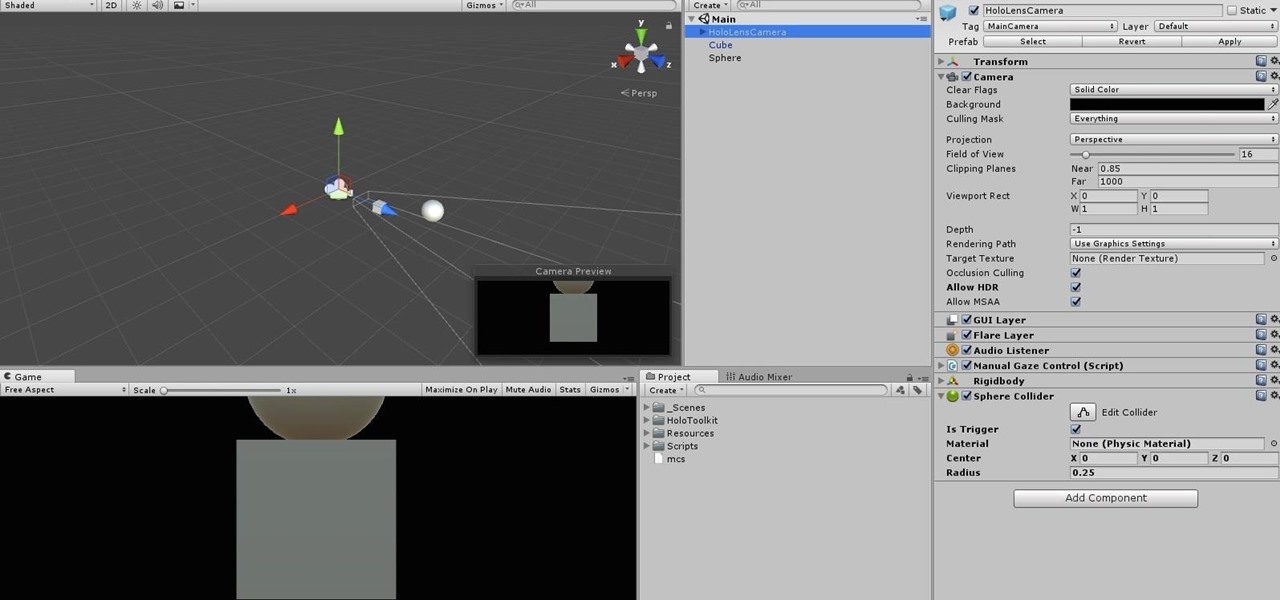
An incorrectly scaled object in your HoloLens app can make or break your project, so it's important to get scaling in Unity down, such as working with uniform and non-uniform factors, before moving onto to other aspects of your app.

| Updated February 11, 2019 with new phones. When will my phone get Android Oreo? That's a question still being asked by many, even this late in 2018. Most OEMs have answered this question in one way or another, either releasing a stable OTA or confirming their device won't be receiving the update. We consolidated all these responses, and here's where we stand.

Apple has been in hot water ever since the news that the company slows down iPhones with older batteries. The iPhone maker is now in damage control, offering customers a large, $50 discount on battery replacements. The question for you, though, is does your iPhone need a battery replacement in the first place?

The augmented reality industry made great strides in 2017, but its apex is not even in sight. In terms of software, augmented reality is approaching meaningful mainstream awareness, thanks mostly to Apple and ARKit. Meanwhile, on the hardware side, AR is very much in its infancy, with headsets mostly limited to enterprise customers or developer kits and the majority of smartphones lacking the sensors necessary to achieve much more than parlor tricks.

File inclusion can allow an attacker to view files on a remote host they shouldn't be able to see, and it can even allow the attacker to run code on a target.

Connecting to your headless Raspberry Pi on the go typically requires a network connection or carrying around bulky peripheral hardware like a screen and keyboard. With the help of an old-school connecting standard, though, you can log into your Pi from any computer using a simple cable. If you don't have a power source, you can also power your Linux distro over the cable at the same time.

With Virtual Network Computing, you don't need to carry a spare keyboard, mouse, or monitor to use your headless computer's full graphical user interface (GUI). Instead, you can connect remotely to it through any available computer or smartphone.

SSH is a powerful tool with more uses than simply logging into a server. This protocol, which stands for Secure Shell, provides X11 forwarding, port forwarding, secure file transfer, and more. Using SSH port forwarding on a compromised host with access to a restricted network can allow an attacker to access hosts within the restricted network or pivot into the network.

There are more than 2 billion Android devices active each month, any of which can be hacked with the use of a remote administration tool, more commonly known as a RAT. AhMyth, one of these powerful tools, can help outsiders monitor a device's location, see SMS messages, take camera snapshots, and even record with the microphone without the user knowing.

"I'm Rey." That's what a lot of people will be saying again this Halloween, as Rey costumes are sure to be another favorite of trick-or-treaters and cosplayers. Yes, on Oct. 31 we all have a chance to be the scavenger of Jakku who just so happens to be the "new hope" for a Jedi renaissance.

Ransomware is software that encrypts a victim's entire hard drive, blocking access to their files unless they pay a ransom to the attacker to get the decryption key. In this tutorial, you'll learn how easy it is to use the USB Rubber Ducky, which is disguised as an ordinary flash drive, to deploy ransomware on a victim's computer within seconds. With an attack that only takes a moment, you'll need to know how to defend yourself.

In the previous section of this series on dynamic user interfaces for HoloLens, we learned about delegates and events. At the same time we used those delegates and events to not only attach our menu system to the users gaze, but also to enable and disable the menu based on certain conditions. Now let's take that knowledge and build on it to make our menu system a bit more comfortable.

After numerous scandals like the Equifax data breach and the 2016 US election, cybersecurity has become a significant issue for Americans. Unfortunately, anytime we use our devices, we're open to a cyber attack — especially when we browse the web. However, there are ways that we can make it harder for hackers and data miners.

Tor is an excellent obfuscation network for web traffic, and while instant messaging over the network is very useful, it can be relatively difficult to configure. In this guide, we'll look at two synchronous communications platforms (instant messengers) which can be routed over the Tor network, Ricochet and XMPP.

Bluetooth Low Energy (BLE) is the de facto wireless protocol choice by many wearables developers, and much of the emerging internet of things (IoT) market. Thanks to it's near ubiquity in modern smartphones, tablets, and computers, BLE represents a large and frequently insecure attack surface. This surface can now be mapped with the use of Blue Hydra.

Aircraft equipped with ADS-B are constantly shouting their location into the radio void, along with other useful unauthenticated and unencrypted data. In this guide, we will make an ADS-B receiver using a Raspberry Pi with a software-defined radio (SDR) dongle, which we can use to track aircraft anywhere in real time.

In my previous article, we learned how to generate a vulnerable virtual machine using SecGen to safely and legally practice hacking. In this tutorial, we will put it all together, and learn how to actually hack our practice VM. This will provide some insight into the methodology behind an actual attack and demonstrate the proper way to practice on a VM.

Andrew Mucci, a New Jersey-based vlogger who is also Social Media Coordinator at Sennheiser, likes to use Instagram not only as a platform for the brand but also as a place to experiment with content on his own account.

Imagine for a moment that a VPN is like putting on a disguise for your computer. This disguise works to change your IP address, secure your traffic with encryption, and mask your location to bypass regional restrictions. This makes it a helpful tool for both whistleblowers and journalists. VPNs are also built into the well-known Tor Browser.

Signal Private Messenger is famous for its end-to-end encryption, but you can't even use the messaging app without having a real phone number attached to it. Luckily, there is a way around this limitation, so you can use Signal even if you don't have a valid SIM card in your smartphone.

Nvidia's decades-long development of graphics processor units (GPU) for PCs has given it a major leg up in the driverless space.

Full disclosure: I really like Apple's stock ringtones on the iPhone. After all, there are over 50 to choose from if you include the classic ones. With all that choice, why would you ever need more? Personally, I get bored easily, and I'd like my music to play when people call. Apple doesn't let us pick a song from our music libraries, but there is still a way to use our favorite tunes as tones.

If you use the Google Assistant on your Android device, you can easily send a text message to any one of your contacts. But even though that same Assistant is powering the Google Home, you can't use the smart speaker to accomplish the same task — at least, not without some tinkering.

The world of investment and finance can be labyrinthine in its very nature — and even more complicated in regards to augmented and mixed reality. While these new emergent technologies are teeming with explosive levels of unrealized potential, there's still a big layer of uncertainty in terms of return — but these investors aren't afraid to take the leap.

When making a convincing mixed reality experience, audio consideration is a must. Great audio can transport the HoloLens wearer to another place or time, help navigate 3D interfaces, or blur the lines of what is real and what is a hologram. Using a location-based trigger (hotspot), we will dial up a fun example of how well spatial sound works with the HoloLens.