
XSS Shell is a cross-site scripting backdoor into the victim's browser which enables an attacker to issue commands and receive responses. During a normal XSS attack an attacker only has one chance to control a victim's browser; however, the XSS Shell keeps the connection between the attacker and the victim open to allow the attacker to continuously manipulate the victim's browser. XSS Shell works by setting up an XSS Channel, an AJAX application embedded into the victim's browser, that can ob...

In a legal brief entered on Monday, Florida-based startup Magic Leap has filed suit against the founder of Nreal, a former employee of Magic Leap, claiming that the company's Nreal Light smartglasses were built using Magic Leap's intellectual property.

Accused of violating whistleblower and age discrimination laws by its security director, Magic Leap has taken an internal situation to the US District Court to clear its name of the allegations.

Abdominal thrusts—also known as the Heimlich maneuver—can be used to expel a foreign object lodged in a choking victim's windpipe. Watch this video tutorial to learn how to perform the Heimlich Maneuver (abdominal thrusts).

The wooden spoon prank is one of the great group pranks, especially if you have a big group of spectators that won't ruin it right away. What you do is get three wooden cooking spoons and an accomplice. Your accomplice will challenge your victim to a game where they take turn seeing who can hit each other's head the hardest with a wooden spoon held in the mouth. The victim goes first, landing a weak hit on your accomplices head. What the victim doesn't know is that you have a spoon too, and a...
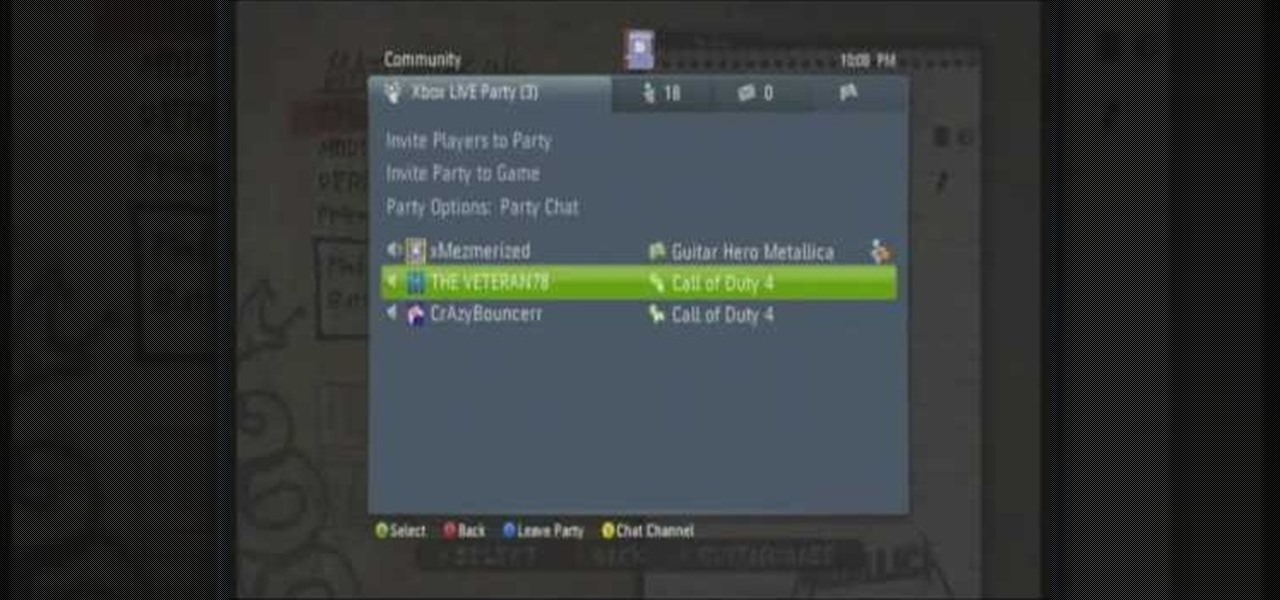
This is a hack tutorial, learn how to freeze someone else's Xbox 360. First, host a party and invite your "victim". Send them a voice message about 15 seconds long an wait till you see the victim listening to the message. Kick the victim from the party and reinvite them back to the party really fast, before they stop listening to the message. This freeze has about a 75% chance of working, depending on what your "victim's" actions.

This Is for the Script Kiddies: This tutorial is about a script written for the How to Conduct a Simple Man-in-the-Middle Attack written by the one and only OTW.

Give someone his or her own personal ticker tape parade with this easy prank. You Will Need

Nextraker has another great prank for you to pull at home— the pillow prank. You'll need the plastic bag from a loaf of bread and some shaving cream.

Brushing your teeth is pretty mundane. Why not enliven the experience for a friend or enemy by pranking them into thinking that their mouth is gushing blood? This video will teach you how to use food coloring and an oven to set up the Bloody Toothbrush Prank. All you do is cook the food coloring into it's powdered essence, apply the powder sneakily your victim's toothbrush, and wait until they brush.

Sometimes the simplest pranks are the best ones! They take no time at all, and they're so simple that no one would even expect to look for the obvious. Like this windshield prank. It involves chocolate syrup and a cup of milk.

Flying under the radar during Magic Leap's big week at the Game Developers Conference, the company settled a potentially ugly lawsuit with a former employee.

Do you ever thought that you can't control an Internet disconnected system? I saw a funny video in Chema Alonso's youtube channel (A well-known hacker of my country and creator of Fingerprinting Organizations with Collected Archives among other security tools), and decided to post something similar.

Welcome back, my hacker wannabees! Most of my recent posts have addressed using Metasploit’s Meterpreter and what we can do once we have embedded it on the victim’s system. This includes remotely installing a keylogger, enabling the webcam, enabling the microphone and recording, disabling the antivirus software, among many other things. The list is almost unlimited.

A sleeping prank victim is much easier to deal with than an awake one. They can't prevent the prank, and afterwards are usually too disoriented to respond violently with any effectiveness. This video will show you several pranks to play on sleeping victims, some of which you've probably seen before and a couple we're betting you haven't.

This prank is not for the faint of heart. It will hurt your victim a great deal, and likely make them want to visit the same fate upon you. But if you're really trying to find a prank that will make the day of your victim worse, and they like to work on cars, this prank is for you. All you do is wait till your victim is under a car working, then grab a hammer and...

If you have been a victim of identity theft, you are not alone. This happens to millions of people every year.

The Diet Coke and Mentos Explosion prank is one of those classic pranks that everyone should experience at some point. When combined the Diet Cola and Mentos become volatile, basting your victim in stickiness. Watch this video to learn how to make a Diet Coke and Mentos bomb, a simple, yet devious exploding prank. Next up: how to con your victim into cleaning up the mess. Use this as inspiration for one of your April Fools Day pranks!

Hey everyone, this guide will show the process of stealing your victims Facebook credentials. This is a followup to my previous post.

Welcome back everyone. As many of you know, reconnaissance is extremely important in any successful hack. Without proper reconnaissance, we won't know what we're about to get into, literally.

Welcome back, my amateur hackers! With Halloween right around the corner, I thought you could have a little fun with your newfound hacking skills using a hack that is guaranteed to freak out your boss, teacher, coworker, friend, etc.

At last, what you all finally waited for! Hi! Fire Crackers,

In my last hack blog on crashing your roommates Win7 system, we started looking at client- side attacks. As promised, we will be looking at some more client-side attacks.

This computer prank how-to video will show you how you can make a fake virus on someone's computer. The virus featured in this video will shut down your victim's computer and generally annoy them.

Play a spooky prank that preys on the most basic fear that one day haunted computers will rise up and destroy us all.

You've probably tried every alleged hangover cure--from cold showers to hot coffee--with little success. But a hangover remedy does exist! So watch this video and learn how to be a drunk without suffering hangovers ever again!

Welcome back, everyone. In the previous part of this rapid-fire miniseries, we built the attacker portion of the shell. In this article, we'll just be testing it to see if everything works correctly.

Welcome back, everyone. In the previous part of this rapid-fire miniseries, we built the victim portion of the shell. Today, we'll be building the attacker portion. This script will initialize interaction with the victim portion of the shell, send commands, and receive the output.

In this article I will show you how to obtain victim's credentials without cracking any hashes. There are a couple of ways to perform this task (for example dumping the SAM file and cracking the NTLM hashes), but here I will explain how to do it using PowerShell and a bit of social engineering. We are going to create a fake login popup.

You must have a certain attitude to appreciate practical jokes and pranks. Your friends (or targets) may not appreciate pranks as much as you, especially messy ones. The messy pranks are the ones that are less likely to provide a laugh from your victims, at least not right away. This ketchup prank is one of those.

Some of the funniest pranks are some of the easiest pranks, like this toothpaste prank. It's very simple, and if you follow the instructions, you'll be able to booby trap your roommate's toothpaste for a very fun time. It can be very gross if you deem necessary.

Welcome back my, tenderfoot hackers! Many people come to Null Byte looking to hack Facebook without the requisite skills to do so. Facebook is far from unhackable, but to do so, you will need some skills, and skill development is what Null Byte is all about.

Welcome back, my rookie hackers! Most often, the professional hacker is seeking protected information from the target system or network. This might be credit card numbers, personally identifiable information, or intellectual property (formulas, plans, blueprints, designs, etc.). Most of my Null Byte guides have been focused on getting into the system, but this only begs the question—"what do I do when I get there?"

Welcome back, my greenhorn hackers! Several of you have you have emailed me asking whether it's possible to install a keylogger on a victim’s computer using Metasploit. The answer is a resounding "YES"!

Welcome back my fellow hackers! In my last few articles, I've concentrated on what is called a listener, which is basically the same thing as backdoor and rootkit, only "listener" sounds much less malevolent than the other two terms.

Halloween is a time that embraces blood, gore, and using blood and gore to scare innocent civilians. So if you're in the pranking mood this Halloween, check out this video to learn how to do a funny ketchup splattering prank that'll leave fake blood all over your victim's clothes and on the floor.

Tass is here to show viewers a video walk through for the game Horror Plant, revealing both endings. The focus of this game is to set up victims for a meat eating plant to devour along the journey. Starting fires, setting up gruesome traps and fooling poor souls is the name of the game. The horror plant is also revealed to be something of a hero to other non-human comrades as it saves and even shares meals with them along the way. One ending shows how adding certain ingredients to another vic...

Wounds that involve underlying structures usually require immobilization. The purpose for immobilizing an injured victim is to provide support. This first aid how-to video demonstrates the proper technique for immobilizing someone who has serious wounds or injuries.

This video demonstrates how to reverse the rescue system so that you can lower a victim to safety.









































