It's no secret that there's a lot of surveillance going on these days. It's easier than ever to end up in a database, and even former government agents are speaking out about the atrocious amount of spying being done against our own citizens. They've targeted our laptops, cars, IP addresses, and now they're coming for our iPhones. AntiSec hackers managed to get their hands on a list of over 12 million Apple UDIDs (Universal Device IDs) from an FBI computer, and they published 1,000,001 of the...

While MacOS computers have been spared from some of the most famous malware attacks, there is no shortage of malicious programs written for them. To keep your computer safe from some of the most common types of malware, we'll check out two free tools. These tools can automatically detect ransomware encrypting your files and watch for unauthorized access to your microphone and camera.

Burning Man 2018 is underway, but Intel and the Smithsonian American Art Museum are giving those not in attendance the ability to view the art from the event through Snapchat.

With the macOS stager created and the attacker's system hosting the Empire listener, the malicious AppleScript can be designed and disguised to appear as a legitimate PDF using a few Unicode and icon manipulation tricks.

SSH is a powerful tool with more uses than simply logging into a server. This protocol, which stands for Secure Shell, provides X11 forwarding, port forwarding, secure file transfer, and more. Using SSH port forwarding on a compromised host with access to a restricted network can allow an attacker to access hosts within the restricted network or pivot into the network.

In a recently released video, it was revealed that Formula-E's partner Roborace has developed a driverless race car that can complete laps at full racing speed.

I.M. Healthy Original Creamy SoyNut Butter was recalled on March 4 after being linked to 16 Escherichia coli cases in nine states. Montessori of Alameda preschool in Portland is the latest victim in a multi-state E. coli outbreak caused by the nut-free butter.

Cancer is a complicated illness, but the more we understand it, the likelier we are to beat it. The 3D Visualisation Aesthetics Lab at the University of New South Wales took to virtual reality to help improve our odds by allowing scientists to walk through virtual representations of actual cancer cells.

Welcome back, everybody. In the previous article, we covered the ideas and concepts of well-known ports and trust exploitation in order to evade a firewall. Today, we'll be building the shell, the part that receives commands, executes them, and sends the output back to the attacker.

Welcome hackers. Hackacademic.RTB1 is vulnerable machine for training our skills.This machine can be download from free from here. There is many tutorial how to hack these machine but i did always be my self.

UPDATE: This post is outdated, the latest version with the correct links and updated instructions can be found at my blog, here - https://techkernel.org/2015/12/19/embed-metasploit-payload-in-apk-manually/

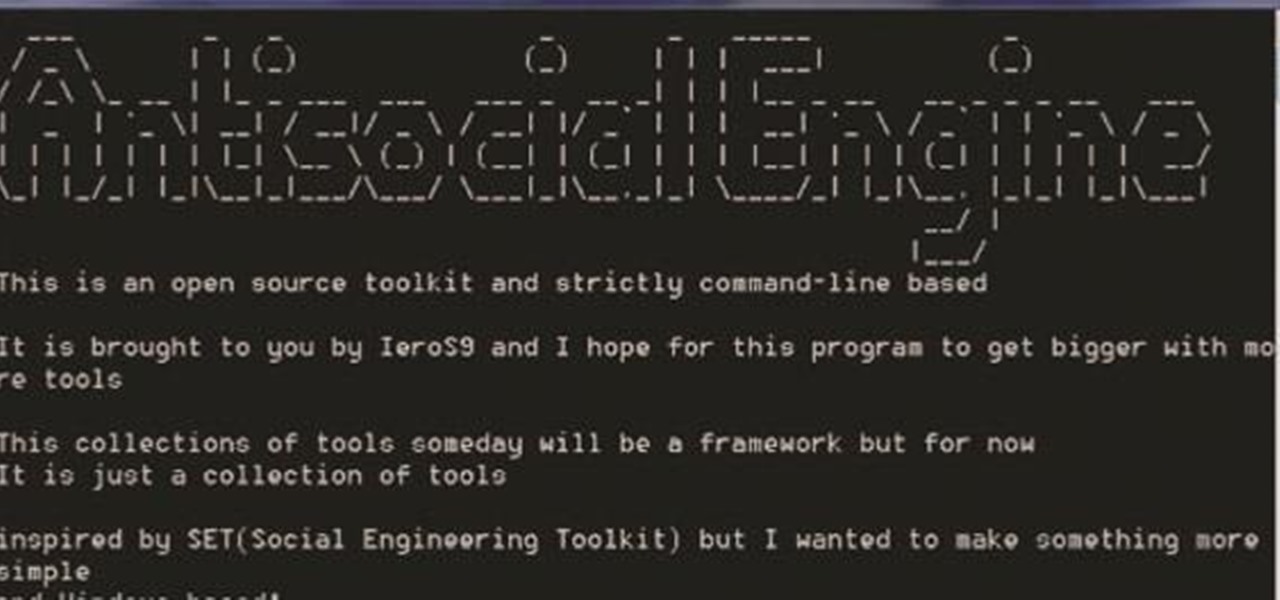
A.E Hi again this is my second post on nullbyte. The first one was on how to make a remote screenshot captor, now I will give you a presentation for a project of mine(I have named It Antisocial Engine) that It is not something extraordinary but will help many guys.

Hello, everyone! Many of you don't even know about my existence here on Null Byte, so I thought of contributing something rather interesting. Recently, someone asked how to make your own "Bad USB," and I promised to make a how-to on this topic. In addition, it would be nice to have something related on our WonderHowTo world. So here it is!

Hello Hackers! Welcome to my 2nd Post: This is a tutorial explaining how to hack android phones with Kali.

Welcome back my fellow hackers. Today I'm going to teach you how to preform an Idle Scan. You may be asking what is an Idle Scan. Its a very stealthy scan because you don't use your own ip you use a zombie (in computer terms).

The Maze Runner tells the story of an unpredictable maze designed to kill. If you're looking for a Halloween costume that's both dark and deadly, the film offers a great option.

Just days after news spread that Snapchat could be exploited by spammers, an anonymous group of hackers have released the private information of over 4 million users of the popular photo-sharing application.

If an athlete gets athlete's foot, what does an astronaut get? Mistletoe. Yup, that's about the only time I've ever really needed mistletoe for anything, but cheesy one-liners aside, mistletoe can be the greatest wingman (or wingwoman) ever, but only during the holiday season.

The best part about April Fool's Day is that everyone is fair game. Even big tech companies like Google and Twitter get in on the action every year. It encourages even the most uptight, unfunny party-poopers among us to have a little fun driving each other crazy with pranks — even at work.

As our society and population grows, more developments such as housing and restaurants are built. While this is beneficial for us, it's not so great for the environment and the animals that occupy it. Some of the victims of our prosperity have been the birds, forced from their natural habitats.

Lucid dreaming, in which you're aware that you're dreaming, can be profoundly beneficial to us. It gives us freedom to do things we couldn't possibly do in the real world. It can show us the true potential of our brain power. You can even use lucid dreaming to question the nature of our own reality. For whatever reason, people everywhere are interested in this mysterious phenomenon...especially in achieving it. Whether it be visiting another planet or flying around, the possibilities in lucid...

It seems like every other day there's a new security threat or data leak in the news. Whether it's your credit card PIN or your smartphone's apps leaking your email address, no one wants their personal information out there, especially passwords. And if you use the same email address and/or password for more than one site, the effects of someone getting hold of your credentials can be catastrophic.

Combination locks in Minecraft can be really simple or frustratingly difficult, but no matter how complicated they are, some of them fall victim to the same simple exploits.

Pyromania is definitely nothing new on WonderHowTo. From flamethrowers and hydrogen fireballs, to flame-making pistons and wine corks, to simply burning steel wool fireworks and DIY smoke mix, we've covered it all. But when pyromaniacal mad scientists feel the need to release some tension in the lab, gummy bears and cockroaches become the victims of euphoric oxidation by way of molten potassium chlorate. A recent video by famous YouTube chemist NurdRage shows one of mankind's most despised cr...

Saw is no longer just a movie, it's a video game, and you can play it on the Xbox 360, PlayStation 3, and Windows. With this video walkthrough series from Committed Gamers, you can BEAT IT (for the Xbox 360).

Even those with hearing impairments need to know basic first aid procedures, because everyone, including deaf people, can save a life one day. People may collapse unexpectedly for a number of reasons, and people who faint periodically, or those who suffer frequent seizures or from epilepsy need help from others, so it's important that everyone know the proper first aid procedure for saving a collapsed victim casualty.

Everyone should know how to perform basic first aid, especially for choking victims. This video will help deaf people and those with hearing impairment learn how to deal with choking, using sign language. Choking is serious life-threatening problem that need immediate attention. It could result in such problems as hypoxia or even death.

And then there was light…on your pen. Have a little fun and with a little ingenuity and a couple of matchsticks you can liven up any afternoon by pranking your friends with this magically burning pen.

Use the power of a condom to make one of the best pranks ever. With the help of a water bottle you can leave your victims wet. Watch this pranking how-to video to find out how. All you need is a condom, a water bottle, and a hot glue gun. Use this as inspiration for one of your April Fools Day pranks!

Accidents happen at work. When there is a minor wound victim, take charge and help support the injured person. This first aid how-to video shows you how to treat work related minor wounds. These first aid tips for work are sure to keep your employees healthy and happy.

Accidents happen at work. When a burn occurs the first priority is to stop the burning. This first aid how-to video shows you how to treat someone who has been burned at work. These first aid tips for work are sure to keep your employees healthy and happy.

Ever wanted to know how to disable an attacker? The trick to getting away from an assailant – even one who's bigger and stronger than you are – is to hit 'em where it hurts.

In the unlikely event you're ever in a plane crash, these tips will dramatically improve your odds of walking away from it alive.

The human body contains nine units of blood—but in matters of a traumatic cut or injury, it's always better to be safe than sorry. If you're unsure whether you're in an emergency situation, get to an emergency room and let them decide.

It's the coolest pool party game ever named after a 13th-century explorer. Marco Polo is a perfect way to cool down and have fun.

In my first installment in this series on professional hacking tools, we downloaded and installed Metasploit, the exploitation framework. Now, we will begin to explore the Metasploit Framework and initiate a tried and true hack.

Ransomware is software that encrypts a victim's entire hard drive, blocking access to their files unless they pay a ransom to the attacker to get the decryption key. In this tutorial, you'll learn how easy it is to use the USB Rubber Ducky, which is disguised as an ordinary flash drive, to deploy ransomware on a victim's computer within seconds. With an attack that only takes a moment, you'll need to know how to defend yourself.

In one of my previous articles, I discussed ShinoBot, a remote administration tool that makes itself obvious. The goal is to see if the user could detect a remote administration tool or RAT on their system. In this article, I'll be demonstrating the use of Pupy, an actual RAT, on a target Ubuntu 16.04 server.

In my previous article, we learned how to generate a vulnerable virtual machine using SecGen to safely and legally practice hacking. In this tutorial, we will put it all together, and learn how to actually hack our practice VM. This will provide some insight into the methodology behind an actual attack and demonstrate the proper way to practice on a VM.

Take a close look at the image above. These bugs spread a deadly parasite that infects thousands of people each year. They also live in the US, and it's important to know where they are and whether you need to worry that they're carrying a dangerous infection.