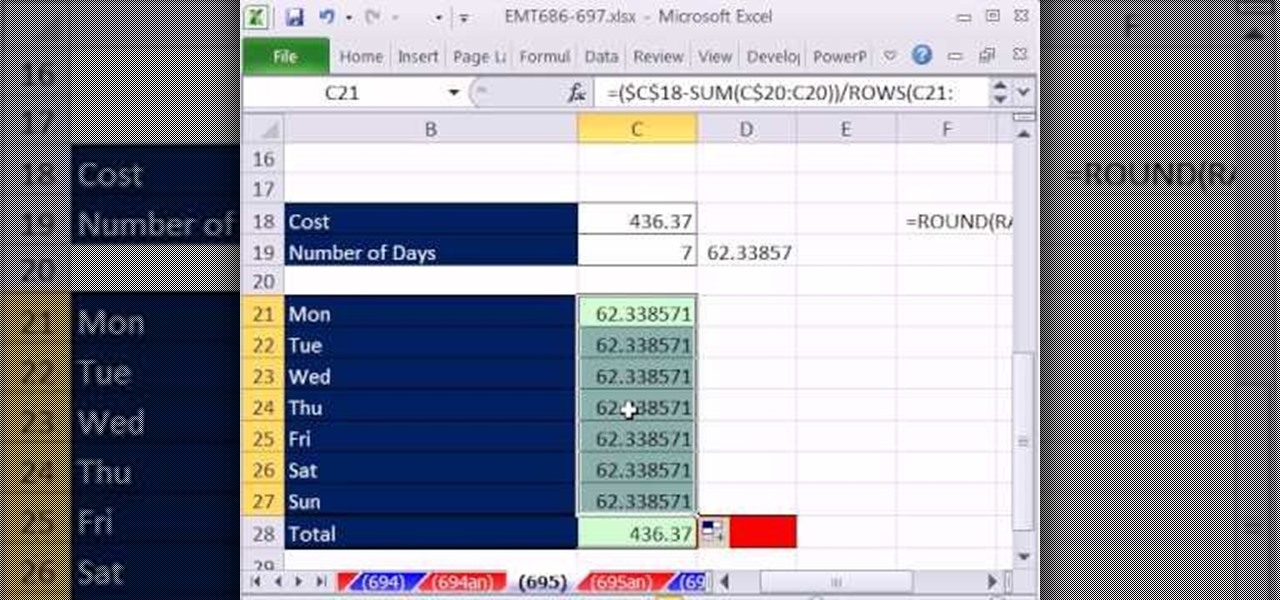
New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 697th installment in their series of digital spreadsheet magic tricks, you'll learn how to allocate $950 across 7 days including the extra penny with a single formula.

Wondering how you can allocate more RAM to Minecraft? Watch this video to learn how to dedicate more of your computer's RAM to Minecraft. This video contains the code to enter into your computer to change the allocation of RAM for Minecraft.

This video tutorial demonstrates tips for how to organize your home office when you are visually impaired. Here a rehabilitation specialist is helping a visually impaired person. The person who is visually impaired should know what is visually important to him/her. Mostly these people obviously need to know where every thing is because they don’t have their eyes to depend anymore. Here visually impaired person is 66 year old Deanne Jackson. She has wet macular degeneration. In order to set up...
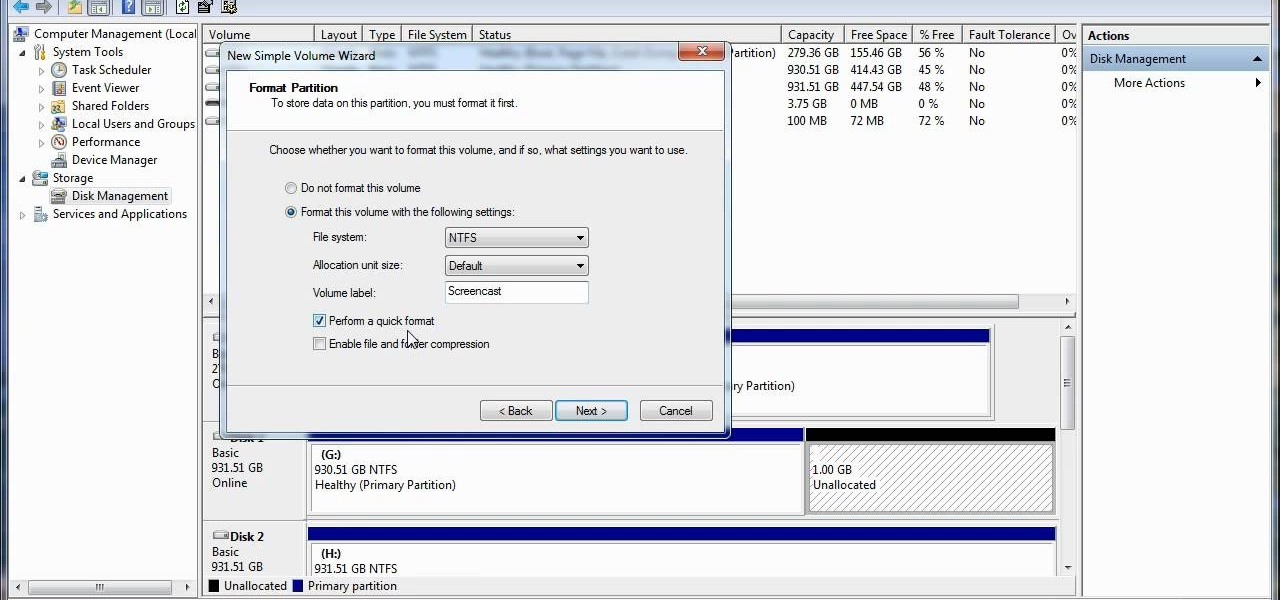
In this video, we learn how to re-partition your hard drive in Windows. In the event you have a hard drive that you want to allocate differently, this will do it. First, go to the start menu and then right click over "my computer". When the new window opens, go to storage, disk management, and then you will see the disks on your computer. Choose the drive you want to partition by right clicking on it and then write in how much you want to shrink the disk. Click shrink and then it will load. N...

Check out this origami how-to video if you want to origami a shuriken. With help from a tutorial, you can allocate some helpful supplements for your origami education. A shuriken is a fun Japanese star-like thing to origami.

There's no doubt Kali has established itself as the most popular penetration distribution available. However, just because it's the fan favorite of beginners and security researchers doesn't make it right for everyone. Manjaro Linux is a beginner-friendly Arch-based distribution which can be easily weaponized with the Black Arch expansion, creating a friendlier first-time Arch experience.

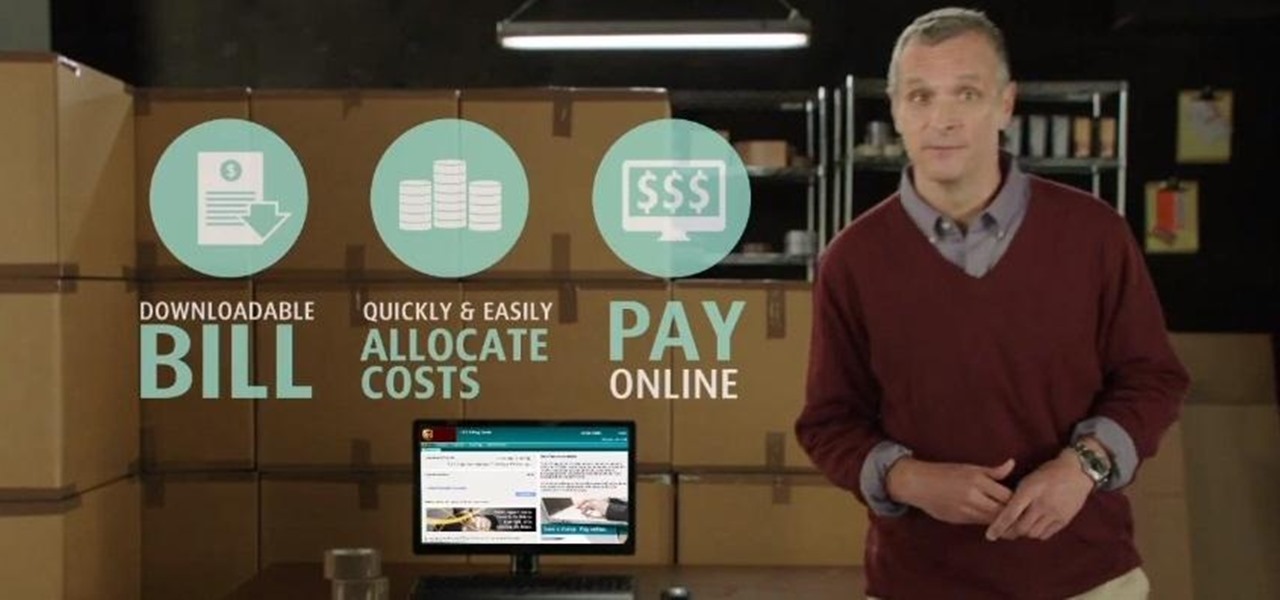
UPS understands how important small business cash flow management is to increase profitability. UPS Billing Center allows companies to download their bills, allocate costs and pay online, so they can bill customers faster and get paid faster.

This video will teach you how to increase your PC's virtual memory. Or in other terms, the Random Access Memory space to be used when doing something with your computer. 1. Press CTRL+ALT+DEL. Go to Performance tab. 2. Check the Commit Charge which is also the amount of virtual memory used. 3. Right-click the My Computer shortcut on your desktop. 4. Go to Advanced tab. 5. On the Performance box, click Settings button. 6. Click the Advanced tab. 7. At Virtual Memory box, click Change button. 8...

Hacking from a host machine without any form of proxying is reckless for a hacker, and in a penetration test, could lead to an important IP address becoming quickly blacklisted by the target. By routing all traffic over Tor and reducing the threat of malicious entrance and exit nodes with a VPN, we can configure Kali to become thoroughly private and anonymous.

One of the main goals of Google Wifi (and Nest Wifi after it) is to make managing your internet connections as simple as possible. A great example of this is how easy it is to prioritize one device and allot it more bandwidth when your network is bogged down with other traffic.

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.

Russians are well known for their knack at documenting exciting and horribly beautiful events on the go, from insane car accidents to attempted insurance fraud and even a superbolide meteor streaking across the sky.

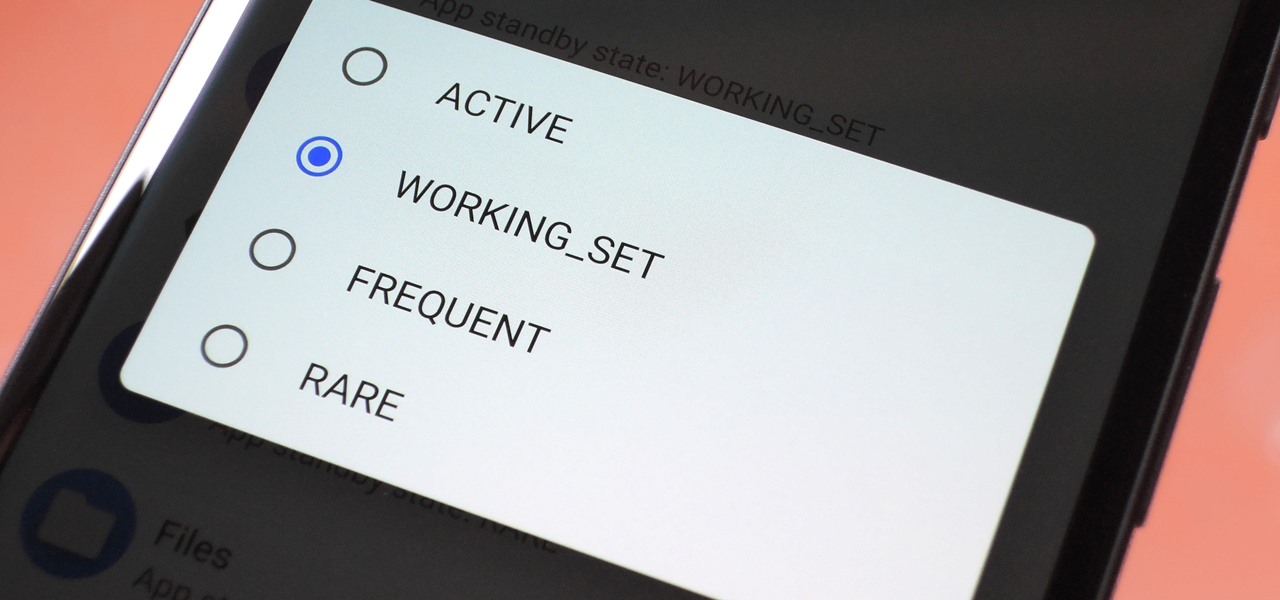
Battery drain is a major pain point for Android users, though that promises to change thanks to Android Pie's new Adaptive Battery feature. But Google hasn't said much about the inner workings of this feature, only publicly stating that it uses AI to boost battery life. So we dug in to find out what's really going on under the hood.

While the iPhone XS and XS Max come equipped with 4 GB of random access memory, and the iPhone XR with 3 GB of RAM, Apple's latest flagships are still susceptible to occasional slowdowns in performance in iOS 12. This can be fixed by clearing RAM, but the process is now a little trickier compared to iPhones with Home buttons.

Hey guys, in this tutorial, we are going to learn about the heap segment and how to use it for storing data in our programs. We will also go into the details of its use in conjunction with the char pointer and struct data types.

INTRODUCTION Hello dear null_byters here we go again with our third part of this serie.

In the previous article in this short series, we learned how to find our neighbor's name using publicly accessible information and how to monitor device activity on their home network. With this information at our disposal, it's time to get into installing and configuring the necessary tools to begin our attack on John Smith's computer.

Being able to write your own hacking tools is what separates the script kiddies from the legendary hackers. While this can take many forms, one of the most coveted skills in hacking is the ability to dig through the binary files of a program and identify vulnerabilities at the lowest level. This is referred to as binary exploitation, and today we're going to check out a tool known as Protostar.

With a cheap computer, smaller than the Raspberry Pi, an attacker can create a remote hacking device. The device can be attached to a target router without anyone's knowledge and enable the hacker to perform a variety of network-based attacks from anywhere in the world.

Dual booting Ubuntu 10.10 Maverick Meerkat and Windows 7 is fairly easy. If you don't believe me, just read on!

Warnings Be careful giving Memory to Java, I recommend leaving at least 2gb to your computer for the operating system and any background processes. This can result in Ram getting overloaded and PC crashes

At some point, we all go from organized to disorganized. Let's assume you are a business executive working in a busy corporate building. Chances are you are going to get a heavy workload and it will impact how clean your workspace is. However, this article is about keeping your desktop clean and clutter free, along with the use of software to find documents you have misplaced.

Since the beginning of last year, every six months or so the fine folks at Wolfire Games have gathered indie developers together to release a combo gaming pack called Humble Indie Bundle. Not only are the included games good, but the way one buys them is what makes Humble Indie Bundle one of the coolest products in games. Even better, Humble Indie Bundle #3 just came out last Tuesday and is available here for two weeks only.

Ever wanted to display text in Minecraft? It's actually not overly difficult. In this tutorial, I will endeavor to guide you through the process between storing and displaying text from memory. To do this, we will examine two different methods of displaying and storing text in memory.