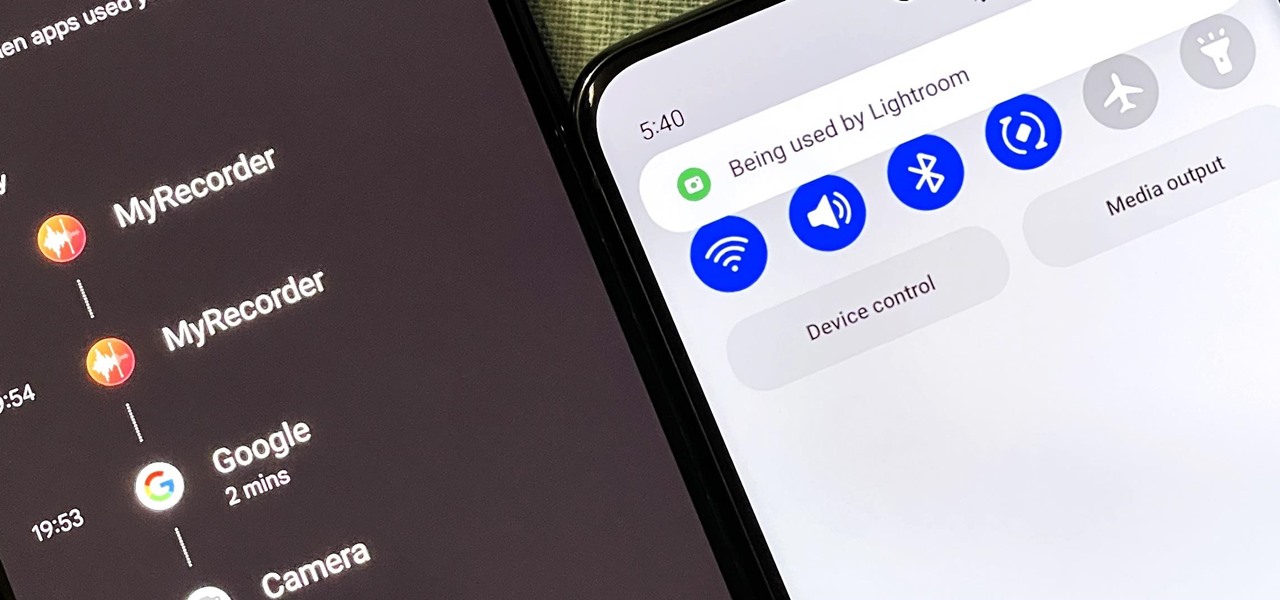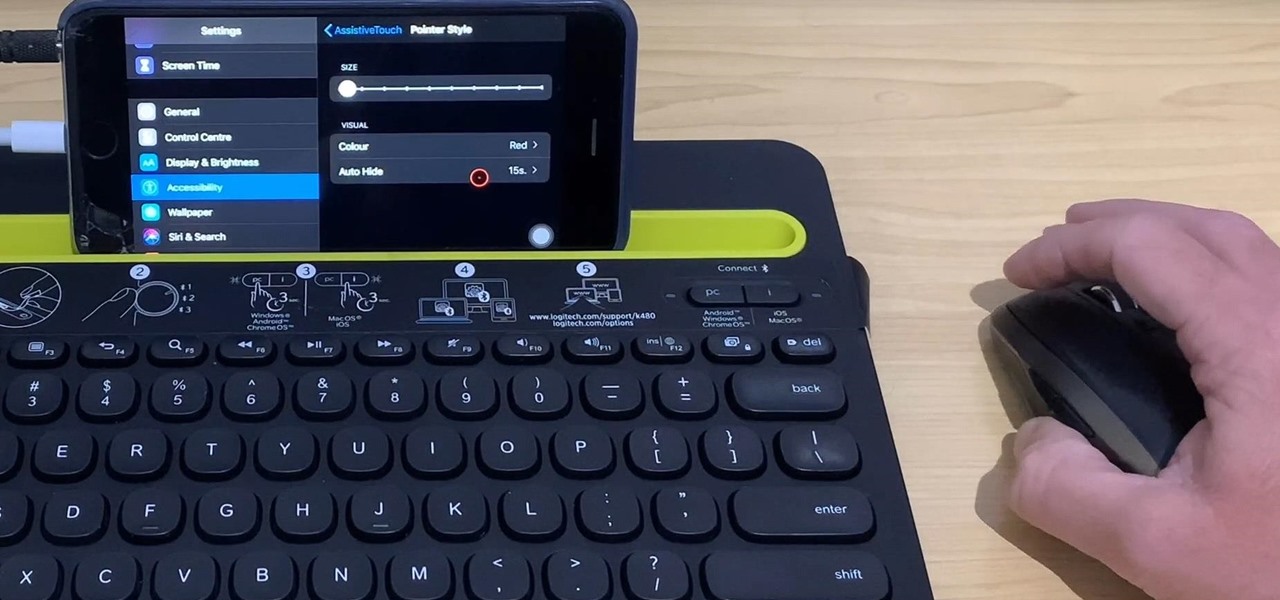
If you exceed your monthly mobile data limit, your cell phone bill can skyrocket pretty quickly. This is why a lot of people vigilantly monitor internet usage and even uninstall apps that use too much background data.

In Minecraft 1.9 New Command Blocks can be used to make elevators. You types different commands to achieve controlling the elevator for movement you like. This tutorial tells in Minecraft 1.9 how to use command blocks to make elevator. Lets just have a look at it!
The Nexus 6 came with a hidden kernel module that allowed for double-tap-to-wake functionality, essentially letting you turn your screen on just by tapping it. A simple root app allowed us to activate this feature, which meant we were always two quick taps away from waking our device.

Google's music offerings have been on a roll lately. First they announced a new music video streaming service called YouTube Music Key, offering ad-free playback with background listening. Then they stated that the new offering would be rolled in with their Google Play Music service, with members allowed to exclusively test the Music Key beta, which just went live. And if all that wasn't enough, they're also offering free music to boot!

Matthew Inman, who runs the popular web comic The Oatmeal, decided to test his new hand-held "Tesla Cannon" (which is essentially a small-scale Tesla coil) on one of his friends. His friend, Matt Harding, held a giant light bulb and allowed himself to be shot with the Tesla Cannon.

Check out this tutorial jet ski video that provides several safety tips on riding your personal water craft with caution. Personal Water Craft (PWC), also called Jet Skis and Wave Runners, are the fastest growing watercraft on the waterways. Along with their popularity has come increasing numbers of injuries and deaths. Commander Tom Martin of the U.S. Coast guard says riders need to follow the rules of the road, as well as wear life jackets and have other safety equipment on board. John Birk...

Check out this cool video where you will learn how to create the liquid rope coil effect. Honey is dribbled off the end of a chopstick into a pot below. As the falling stream stikes the pool of honey below, it turns itself into tight circular coils which rapidly begin to pile one on top of the other. A growing column of liquid coils of rope begin to emerge from above the surface of the honey in the pot in an effect referred to as the liquid rope-coil effect.

Is your smartphone eavesdropping on you? It's a question that will never go away because it's easy to envision hackers or malicious apps taking over your device to spy on conversations, snap photos, or even record video. But fewer people will be asking it, thanks to Android 12, which has a new privacy feature that visually warns you of possible invasive surveillance.

Apple released the third beta of iOS 12 for developers on Tuesday, July 3. The update comes exactly two weeks after the release of the second developer beta, which introduced a variety of fixes as well as new issues, and just one week after the release of the public beta. Public beta testers received this iOS 12 update on Thursday, July 5, labeled as public beta 2.

New releases of iOS are always pretty exciting. I remember the anticipation buildup of iOS 7 before it was announced at WWDC 2013, as it was expected to be a complete game changer compared to previous versions—and it was.

In case you didn't know, Android has an awesome hidden settings menu called "Developer options" that contains a lot of advanced and unique features. If you've ever come across this menu before, chances are you just dipped in for a minute so that you could enable USB debugging and use ADB features.

Below are the official rules and guidelines for submitting content to WonderHowTo. Please look over them before publishing any articles. Ignoring the rules could result in deletion of your article or being flagged as a spammer. Most of these rules apply to comments as well.

With each update, Chromebooks are slowly becoming the Android tablet we always wanted. They already run your favorite Android apps and recently added a multitasking feature introduced to Android smartphones a few years ago: picture-in-picture mode.

Did Google CEO Sundar Pichai kill Google Glass for non-enterprise users? That's the obvious first question following news that non-enterprise Glass users will no longer have access to Google's core apps after February 2020.

While Magic Leap World gets its share of fun apps for playing with Porgs, watching TV, and exploring the ocean's depths, developers are making a strong business case for the Magic Leap One as well.

The latest film addition in the American-produced Millennium series, The Girl in the Spider's Web, was just released on Blu-ray a few days ago. As you could expect, the movie has many hacking scenes throughout, just like the previous English and Swedish language movies centered around hacker Lisbeth Salander. Of course, with the quick pace of some scenes, the hacks can be hard to follow.

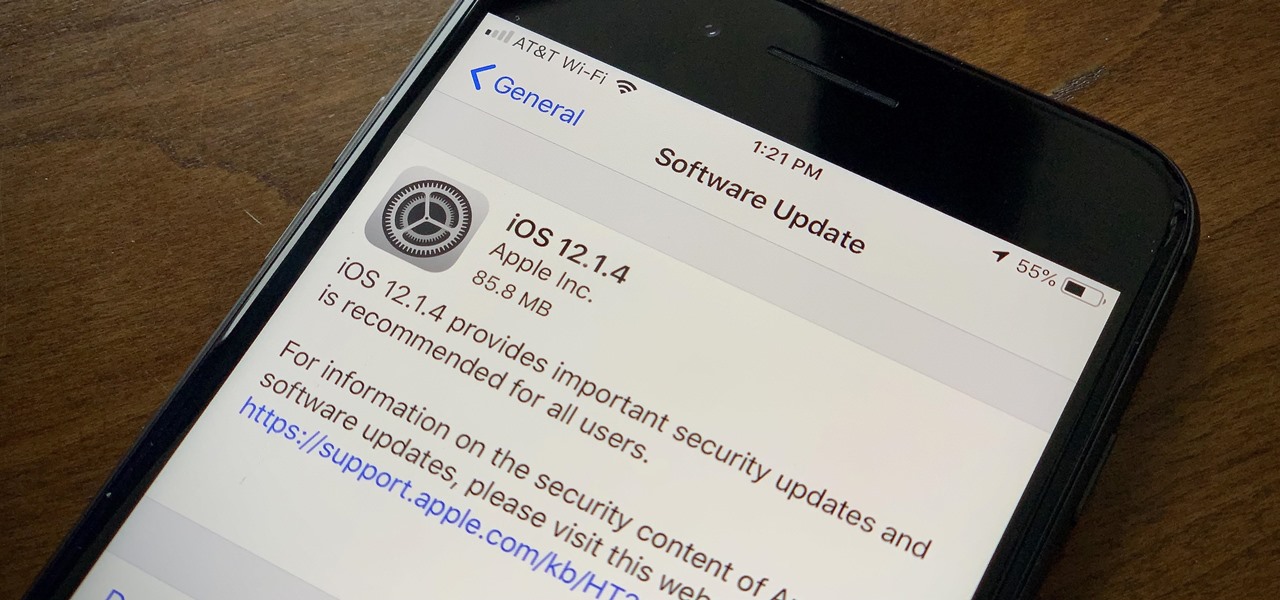
Apple found itself in serious trouble last week when a teenager discovered a critical FaceTime bug that threatened the security of nearly every iPhone user. The bug enabled a user using Group FaceTime to access either the microphone or the camera of a recipient before they answered the call. According to Apple, the issues have been fixed in an iOS 12.1.4 update released Thursday, Feb. 7.

Roughly four years ago, Adobe decided to abandon development of the mobile version of their popular Flash Player browser plugin. Their excuse at the time was that this move would enable them to focus more on HTML5 development for mobile devices and allow them to put more effort into maintaining the fluidity and security of their desktop Flash plugin.

For all of the flak that Windows 8 received from desktop users, it certainly had some interesting and unique features. For instance, the "Charms" bar allowed you to easily access several key menus by simply hovering your mouse pointer in the top- or bottom-right corner of the screen.

Losing your phone is a much bigger ordeal today than it was just 10 years ago. Our smartphones carry with them lots of sensitive data that, in the wrong hands, is capable of being used for identity theft and fraud.

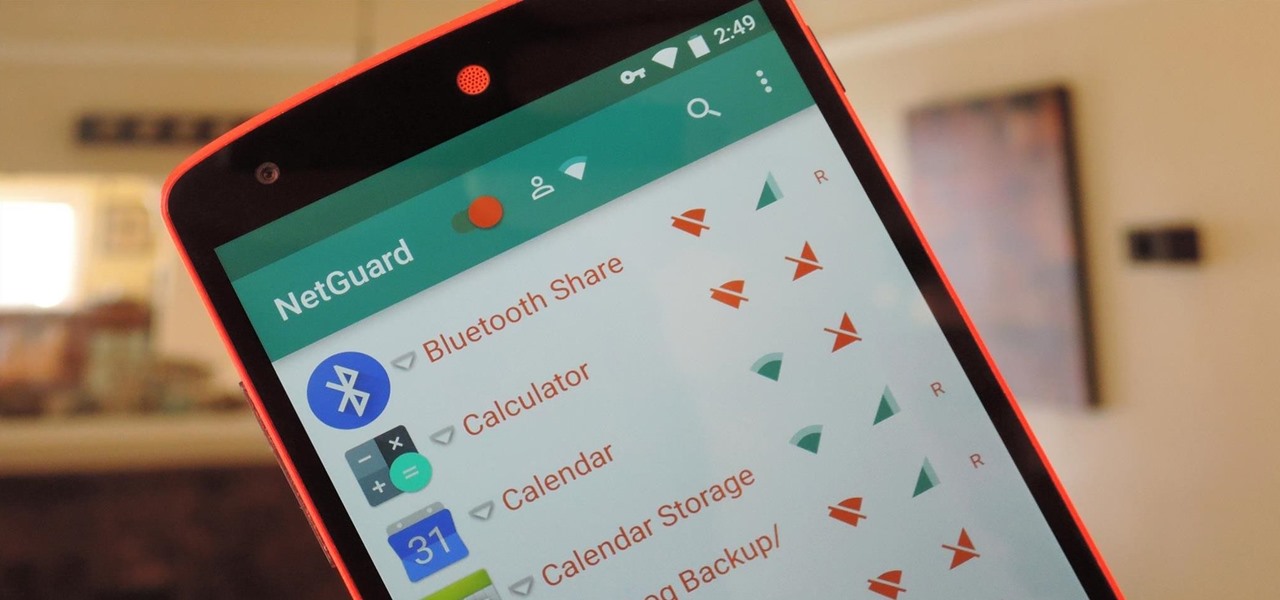
If you've been using Google's hidden App Ops to lock down and prevent some of your Android applications from exposing your privacy, then think twice before updating to the new Android 4.4.2 software.

If there's one way to get a visceral response from someone, it's bringing up the DMV. Regardless of the reason, whether it's the long lines, disgruntled employees, or just general inefficiency, I have yet to meet a single person who doesn't mind the trip. Just look at all those happy faces.

20 Questions is a great game to play when you have some time to kill. Check out this video and learn the basic rules of the game. 20 Questions is perfect whether you are in the car, a waiting room or anywhere else and feeling a bit bored.

Quitting smoking is incredibly difficult. It's hard enough to break the habit, but the withdrawals are even worse. In this tutorial, learn how to make the transition a little more bearable.

Right on the heels of the iOS 11.4.1 beta 3 release, Apple pushed out iOS 12 beta 2 to registered developers on Tuesday, June 19. Public beta testers received the same version, labeled as iOS 12 public beta 1, six days later on Monday, June 25. Last year, the iOS 11 public beta opened up just five days after the release of iOS 11 developer beta 2, so iOS 12 is pretty much right on track in that regard.

Ringtones and text tones can be annoying, so my iPhone is almost always set to vibrate on silent mode. Unfortunately, that causes me to miss phone calls and text messages when the device isn't in my hands or pockets. While I hate missing alerts, I'm still reluctant to switch to ring mode — and that's where another iOS and iPadOS feature helps out.

Starting with Android 9 and 10, Google made privacy and security the main priorities for Android updates. Both versions brought numerous changes to help erase the notion that Android isn't safe, but Android 11 might even have them beat.

The "Zoombombing" trend is still strong on the Zoom video meetings service, despite security measures Zoom put in place to stop it. That's why it's up to you, as either a host or co-host, to be proactive about preventing Zoombomber harassment, as well as stopping it whenever it slips through the cracks.

Web applications are a prime target for hackers, but sometimes it's not just the web apps themselves that are vulnerable. Web management interfaces should be scrutinized just as hard as the apps they manage, especially when they contain some sort of upload functionality. By exploiting a vulnerability in Apache Tomcat, a hacker can upload a backdoor and get a shell.

One of the things that sets a seasoned hacker apart from the script kiddies is the ability to effectively sneak past antivirus defenses when executing an attack. One way to do this is to use custom shellcode in an exploit. Not everyone is an expert at writing shellcode, but luckily there's an easy way to do this that is both quick and effective.

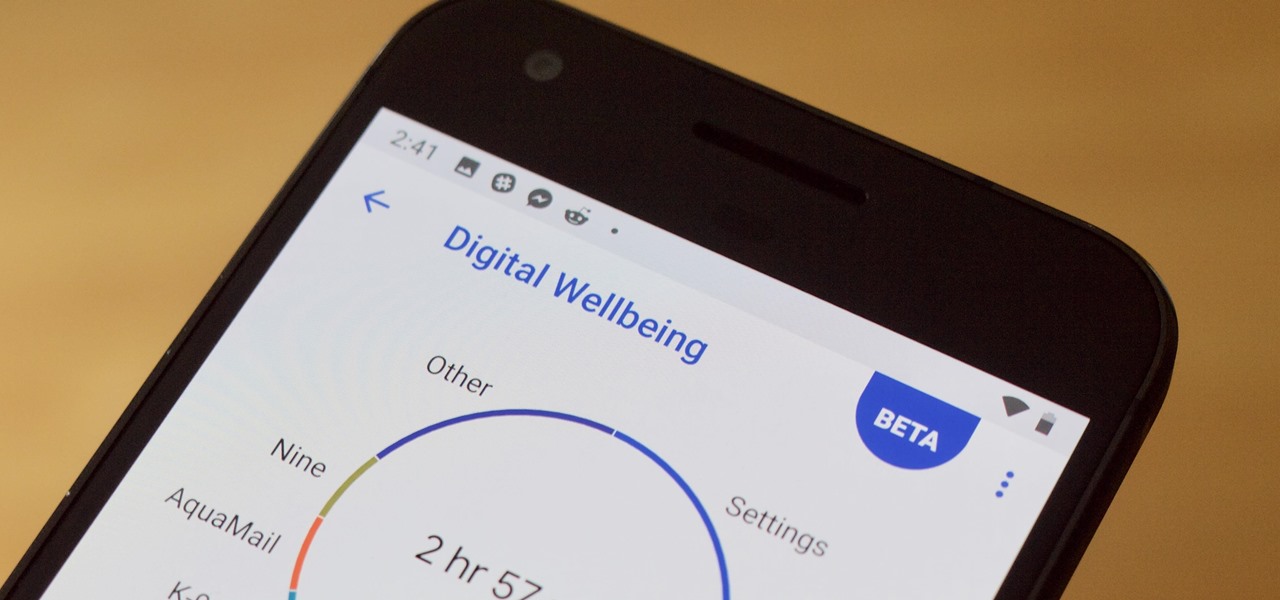
Is your smartphone taking over your life? Do you need help putting your Pixel down at night? Well, update to Android Pie! Android 9.0 comes with Digital Wellbeing, a new tool to both help you understand your smartphone habits and perhaps step away from the apps, games, and notifications every now and then.

Cancer cells do a pretty good job of flying under the radar of our immune system. They don't raise the alarm bells signaling they are a foreign invader the way viruses do. That might be something scientists can change, though.

Disengagement report numbers for self-driving car testing in 2016 on public roads in California were just released, and the biggest point we can make about them is that Waymo is very far ahead of their competitors in almost every metric.

Back in the '80s, I was just a kid with a LEGO hobby. I remember building castles and floating boats, spaceships and monster trucks, even a working LEGO train powered by battery, lights and all.

In a previous post, I wrote about how controversy changed SCRABBLE, about how the SCRABBLE Dictionary evolved thanks to Judith Grad and her crusade to rid the world of derogatory and racist words. She won, at least in some manner, but the fact still remains, racist or not—words are words, and they're here to stay.

You know that you have the Gmail app on your iPhone. After all, you get Gmail notifications, you see it in the app switcher, it's in the Settings app, and there's an "Open" button in the App Store instead of "Get" or a download icon. But you cannot find the app on your Home Screen. If this situation sounds like something you're dealing with on iOS 14 or iOS 15, there's an easy answer.

File permissions can get tricky on Linux and can be a valuable avenue of attack during privilege escalation if things aren't configured correctly. SUID binaries can often be an easy path to root, but sifting through all of the defaults can be a massive waste of time. Luckily, there's a simple script that can sort things out for us.

With stay-at-home orders for most of us in the US because of the new coronavirus, many of you are likely struggling to be productive and efficient when working from home. Unless you've worked from home before, it can be challenging to separate work from personal life throughout the "workday." But your iPhone can help make the transition easier and more successful.

Huawei has been in a losing battle with the US government for around ten years, with the last year being the spike of Huawei's problems. Because of US pushback against some Chinese-based smartphone manufacturers due to security concerns, Huawei is hoping to limit its dependency on US-based companies, and recent rumors of Huawei's very own mobile operating system may be the first step.

Command injection is a technique used by hackers to execute system commands on a server, usually via a web application or some kind of GUI. This can happen when an application provides some sort of functionality to the user involving the use of system commands. When the input is not properly sanitized, commands not originally intended to be run are allowed to be executed.