Many new players wonder how one actually gets a rating in SCRABBLE. Now, we're talking about an official rating, not one you would get on SCRABBLE Beta or with the ISC WordBiz player — I mean an "Official SCRABBLE Rating". A rating that allows you to play in the National SCRABBLE Championship (NSC), which is held once every year (sometimes two).

Hello, nubile young Photoshop explorers! As we all know, besides design, Photoshop is best used for revenge, as will be demonstrated below. This is my ex-girlfriend, Cassandra. She dumped me because I had "poor bone structure." I'll bone her structure! Well, not anymore, I guess.

Ah, turducken. The fondest of all portmanteau words and the tastiest of all Thanksgiving day meals. Turducken is a turkey stuffed with a duck stuffed with a chicken—three glorious poultry meats molded into one marvelous, boneless hunk of flesh that any sane carnivore wouldn't dare resist. It's slapped together with pork sausage stuffing, sometimes even three different kinds, and caked with Cajun seasonings.

Giveaway Tuesdays has officially ended! But don't sweat it, WonderHowTo has another World that's taken its place. Every Tuesday, Phone Snap! invites you to show off your cell phone photography skills.

To make things a little more fun here on Scrabble World, I've decided to start a weekly feature for word freaks to ponder about it... a challenge. No, I'm not 'challenging' any of your words... I'm challenging your brains. See if you can figure some of these Scrabble puzzles out. You can print this page or hand write the questions out to play at home (or wherever).

It's no secret. Professional video editors everywhere are irate at the newest edition to Apple's popular non-linear video editing software, Final Cut Pro X. As of right now, Final Cut Pro X has 503 five-star ratings in the Mac App Store. Not bad. But it also has 671 one-star ratings and 414 users who aren't sure what they think. It's such a bad update that it even earned itself a skit on Conan.

Giveaway Tuesdays has officially ended! But don't sweat it, WonderHowTo has another World that's taken its place. Every Tuesday, Phone Snap! invites you to show off your cell phone photography skills.

Darrin Judkins - BMG Models NYC, Women's Board Booking Agent

Are you bankrupt or all tied up for money? Do you want a very easy way to make money in RuneScape? If so, you are reading the right article! If you're a non-member, then read this.

This is my list of programs that I must have on my PC, but I think you can also use them, so here is the list:

TOP MOVIES 2011 The Artist (2011)

A woman from space that who has been dead hundreds of years has been resurrected on the internet and you're the IT assigned to fight the viruses attacking her. Child of Eden is a mesmerizing musical game, with fluid animations, great game play, and lots of replay ability.

New Year's Eve. It will be one hell of a chaotic night. Trust me. The overcrowded streets. Long lines for the urinal. Maxing out your credit card on that shot of Cuervo. You'll be lucky to make it out alive.

Remember KODACHROME? That color reversal film from Kodak? The film that was the inspiration for Paul Simon? The only brand of film to have a state park named after it?

Before you start snapping away and submitting your photos, please take some time to read the official rules below!

Last week, I demonstrated how to go a little deeper into your Google+ profiles, photos, and introduced cross-posting. This week, I'm highlighting a bunch of different unofficial resources that have sprung up that will help improve your Google+ experience, and give you the latest updates on Google+ Photos.

Giveaway Tuesdays has officially ended! But don't sweat it, WonderHowTo has another World that's taken its place. Every Tuesday, Phone Snap! invites you to show off your cell phone photography skills.

I just found out that I might be expected to tip all the vendors... on top of the exorbitant fee they charge! Sigh... Here is a great tipping cheat sheet courtesy of theknot.com.

Big brother is watching when you're playing around on another system—and big brother is that system. Everything from operating systems to intrusion detection systems to database services are maintaining logs. Sometimes, these are error logs that can show attackers trying various SQL injection vectors over and over. This is especially so if they are using an automated framework like sqlmap that can spam a ton of requests in a short time. More often than not, the access logs are what most amate...

Over the past couple of weeks, there have been a series of high-profile hacks and leaks. From the rooting of CombinedSystems, to a secret FBI conference call leak, all the way to the distributed denial-of-service (DDoS) attacks on U.S. government sites—with a lot in-between. As governments move to close their long fingers around the free speech that exposes their secrets, this shadowy collective of loose-knit, but like-minded individuals are hell bent on preventing them. Or are they?

Posted with permission via HereComeTheYanks.com 1776...a group of colonies walked away from the British, effectively starting a war that ended in the defeat of the mighty Brits.

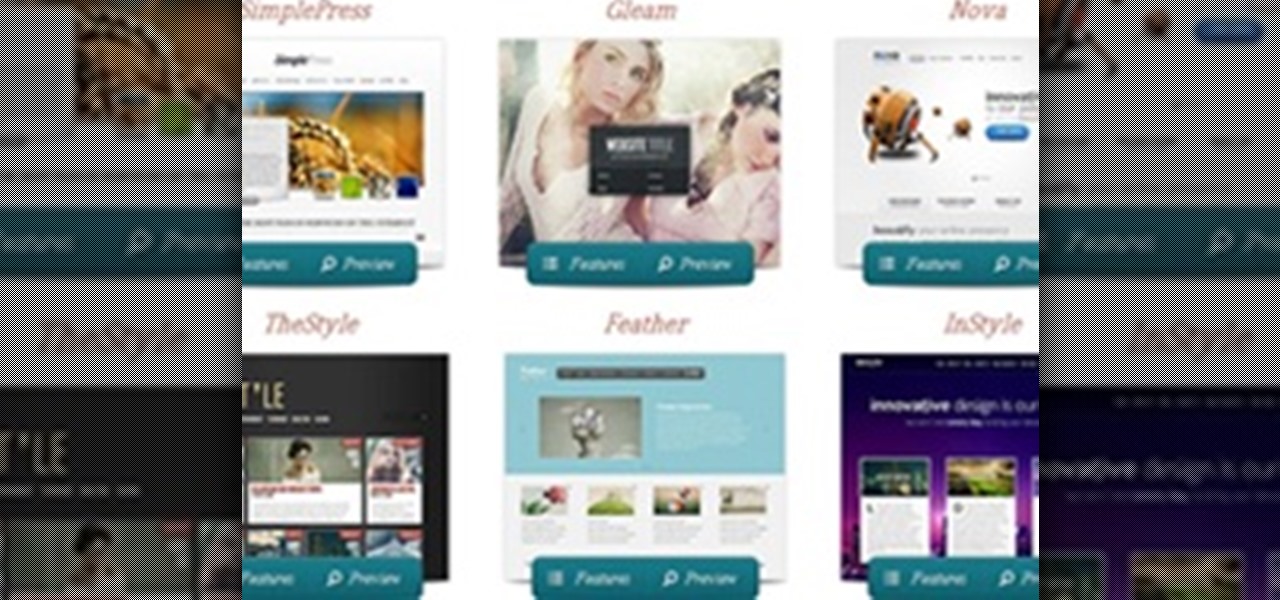
To create an elegant WordPress blog or website from scratch without being noticed that you're a complete beginner, you need that drive and pairs of eyes and ears. It may seem difficult at first but it can truly be fun and exciting.