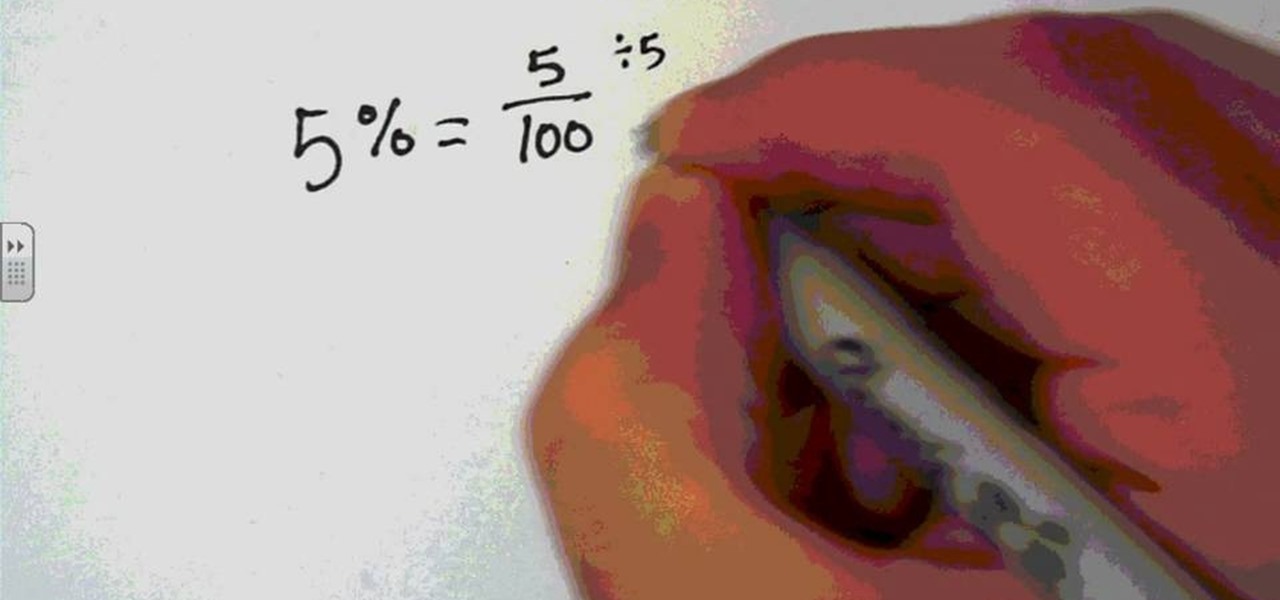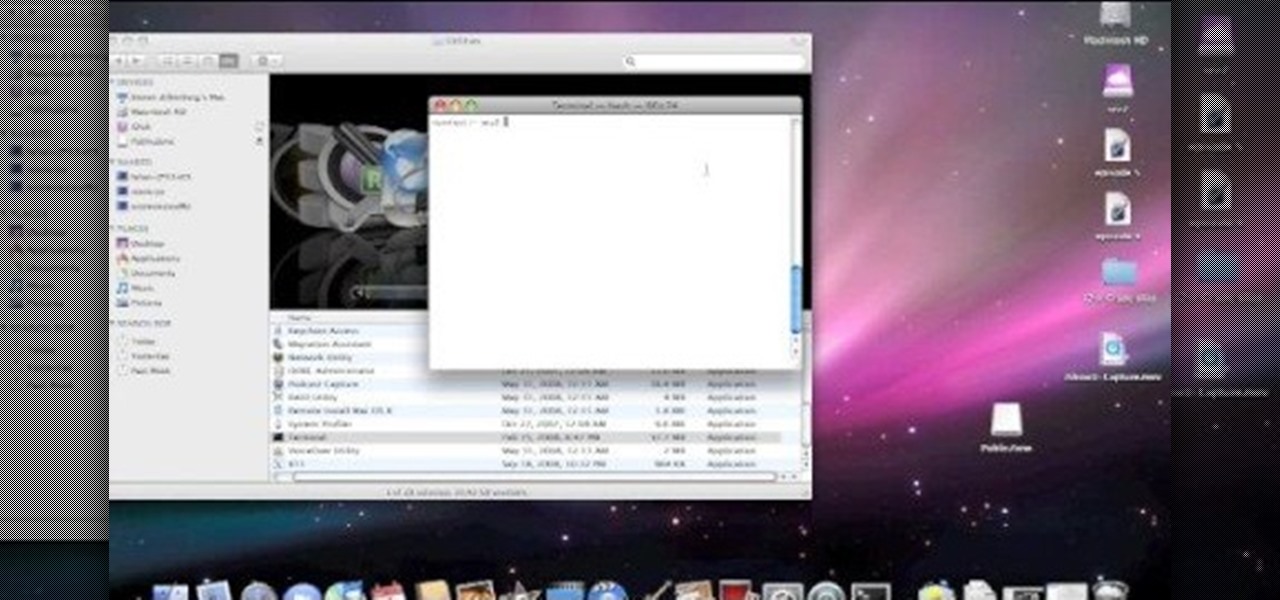
In this tutorial, we learn how to eject devices from the use of the terminal for Mac. First, go to the terminal of your computer where you will see a notepad sort of page. Next, type in "df" and then press return. You will now see a list displaying processes on your computer. On the bottom will be your public zoning device, which is your USB device. Next, type in "hdiutil eject -force (the code under "mounted on)- volumes-publiczone". This is not case sensitive, but don't forget or add in any...

Some of the best kids activities are done right in your own home, recycling everyday items. For instance, an egg carton. What could you possibly make out of an old egg carton? This video will show you exactly what you could do! See how to make egg carton flowers. These decorative flowers can proudly be displayed anywhere. All you and your kid will need are:
The most important part of art is making sure others see it and appreciate the message. In this tutorial, learn how to attract more viewers to your artwork, as displayed on the website, Deviant Art. This is a great way to get your vision out there and make your voice heard. You don't have to wait until you can get your pieces in a museum - get started gaining fans today.
In this how-to video, you will learn how to shut down your Blackberry device quickly and easily. If you have uninstalled or installed a new program, this may be useful for you. You will have to find the power off tool in the display of your Blackberry. You can place this option in the tools section. Once you highlight it and press the track ball, it will begin the process of turning the device off. This allows you to shutdown all processes on the device and completely turn off. This video sho...
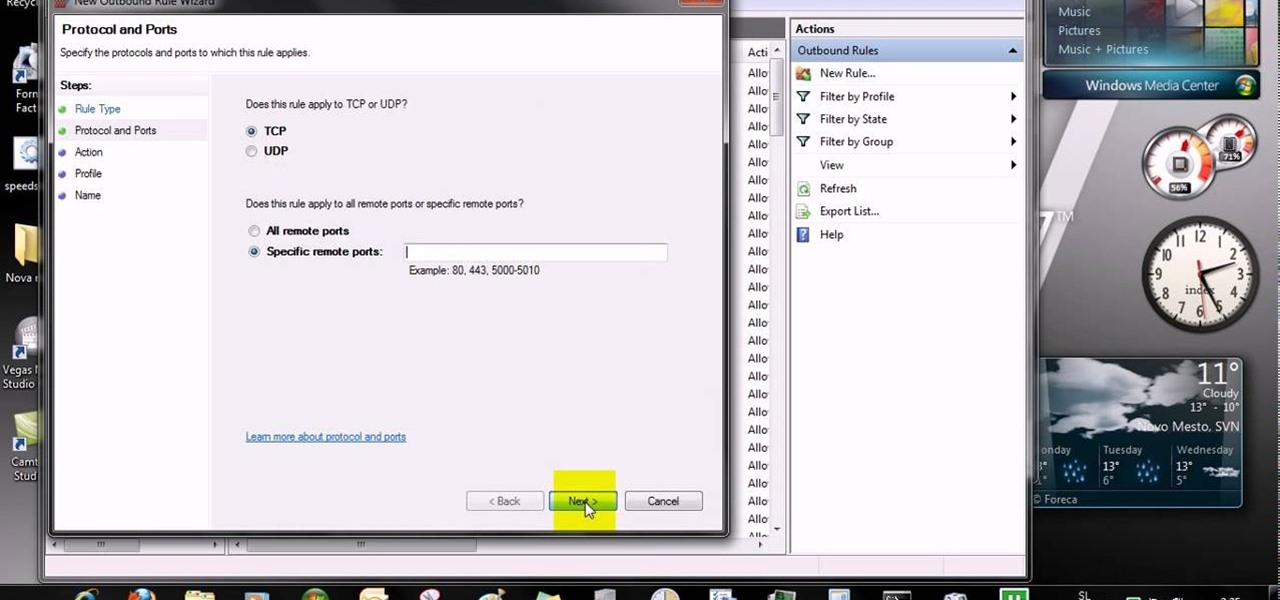
This video tells us the method to open ports in Windows 7. Click on myu icon and go to 'Preferences'. Copy the port number from the resulting window. Go to 'Start', 'Control Panel' and 'System and Security'. Go to 'Windows Firewall' and 'Advanced Settings'. Go to 'Inbound Rules' and 'New Rule'. Click on 'Port' and select 'TCP' and 'Specific Local Port'. Type the port number in the text box. Click 'Next' and 'Allow Connection'. Press 'Next' twice and put the name in the space provided for it. ...

In this Outdoor Recreation video tutorial you will learn how to mount a fish finder on your kayak. There are many ways of doing this. All the methods work. It’s just a matter of personal choice where you want to mount it. Some boats are designed for a through hole transducer and have a space for it to mount it in a hole. Take a piece of foam, trace out the transducer and cut out the foam. Now open the front hatch of the boat and glue down the foam on the flat surface of the boat. Once that ...

Percents are handy for displaying statistics or labeling objects such as sale items in a store, or ingredient labels. However, in a math equation, a percent is a bit difficult to use. Therefore, you will need to convert your percents into an easier type of number form.

First, get out a Swiss Army Knife and clean your hands. Then, take out the main blade. Next, on the right hand side of the IPod, stick the blade through between the gap to open the casing of the IPod. Then, turn the ipod upside down, so that the display side is facing the ground. Cautiously open the case, being careful not to damage the attachment in the top corner. Once the case is open, carefully detach the the hard drive from the bar "thing" connected to the top of the hard drive. Next, ta...

This video illustrates the method to Set up a Remote Desktop connection on a Windows PC. This process is composed of the following steps: Step 1Install "TeamViwer" software on the PC's which would be involved in this process.Step 2Create a connection between the computer you want to access remotely and the one which would be used to gain remote access. To create a connection , you need to connect them through Wi-Fi, LAN or through the internet.Step 3Open the TeamViewer software from the compu...

In this Electronics video tutorial you will learn how to update your iPhone and iPod Touch firmware 3.0. You will need iTunes 8.2 and the firmware from Deposit Files. Go to the website and download the firmware. This will take some time. Use Firefox browser for the download. Now make sure your device is clean, i.e., it is not jailbroken and connect it to the computer. Then open up iTunes on the device for this hold down ‘power’ and ‘home’ until the device switches off and then powers on. Once...

The following are the steps to be followed to boot Windows XP from a CD: 1. The first thing to do is switch on your computer. Before your computer starts loading windows, you need to hit the F12 key.

Do you have a PC and you keep trying to explain it to your friend, but he doesn't seem to understand what are you talking about?

After struggling for years with acne, this skincare system that is displayed got rid of the hostess's acne problem effectively. In the morning, she uses Sea Breeze Actives deep clean astringent which has 1% salicylic acid in it, making sure that you use one cotton ball for each individual part of your face. Afterwards, she uses a skin lotion that has salicylic acid in it. These products will prevent your face from getting too oily during the day. At night, she uses the Proactiv cleanser, whic...

FoodWishes will show you how to make an apple swan with this short little video. This project is simple and quick.

Susie Henderson, owner of Auntie's Beads, explains how to be successful in the bead industry. Learn how to make up business cards, get the business name out there, display the product, have the product ready, and how to present the product nicely. Watch this instructional video series and follow along to pick up these great business tips.

Microsoft believes its Mesh platform can help developers build immersive AR apps more easily. We spoke with a member of the Microsoft team to learn more about the platform.

Attackers may have actively exploited a new WebKit vulnerability on iOS and iPadOS, but Apple just released a patch to secure your iPhone and iPad from attacks.

Navigating a pandemic is new for everybody, which makes staying on top of your finances more important than ever. Fortunately, financial freedom is possible when you focus on budgeting and investing wisely.

As phones' screens get closer to seven inches, now is the perfect time to take advantage of Android's split-screen mode. This feature has available since Android 7.0 Nougat and allows you to divide the screen into two halves, with a different app on each side.

If you've ever wanted to track down the source of a Wi-Fi transmission, doing so can be relatively easy with the right equipment.

Choosing which programming language to learn next can be a truly daunting task. That's the case regardless of whether you're a Null Byter just beginning a career in development and cybersecurity or you're a seasoned ethical hacking and penetration tester with years of extensive coding experience under your belt. On that note, we recommend Python for anyone who hasn't mastered it yet.

If you haven't used a Samsung device in a few years, the Galaxy S20 series will be your first taste of One UI 2, the skin running on top of Android 10. Although One UI is on the heavier side, it has loads of exciting features that go beyond what's offered in stock Android.

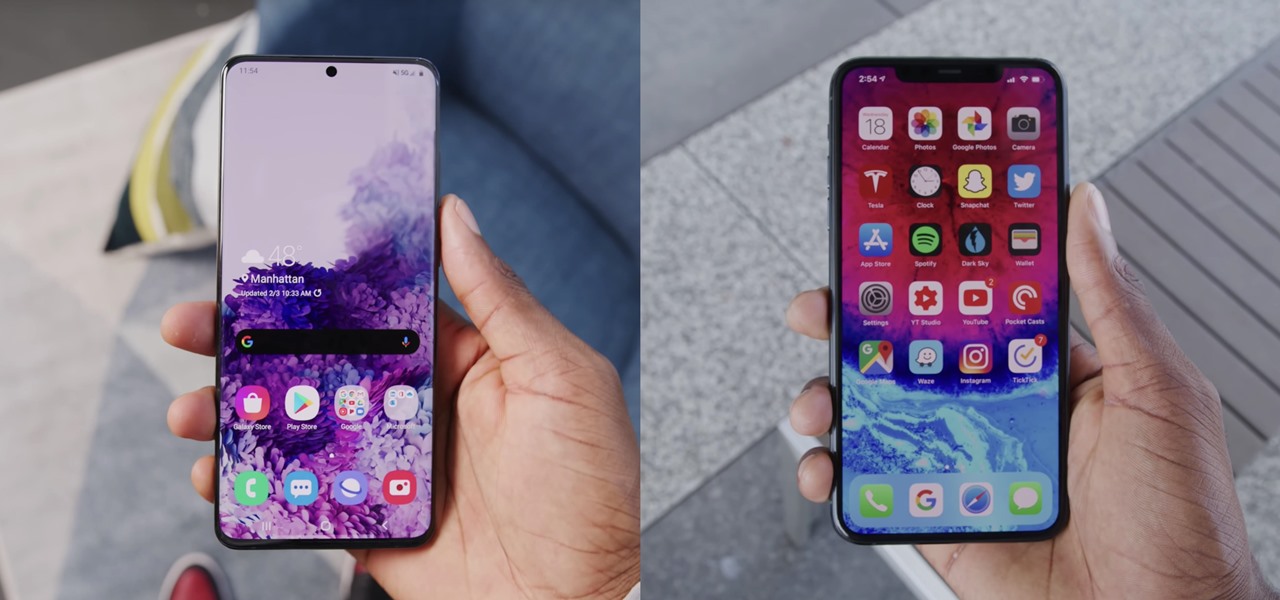
The time to wait for an absolutely killer phone from Samsung is over. They've released a giant of a phone known as the S20 Ultra, and at least on paper, it's a grand slam. But only a few months ago, Apple released its first "Pro" iPhone, and it was giant in its own right. So which is better?

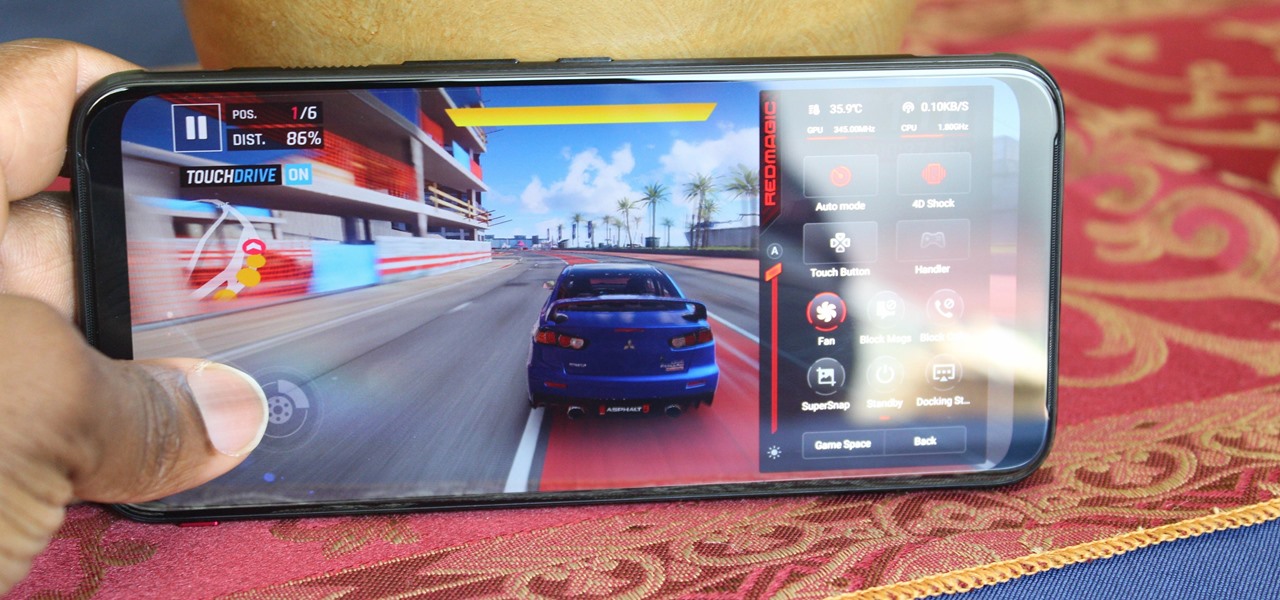
Mobile gaming has exploded in recent years, with experts predicting 2.4 billion global mobile players by the end of 2019. It already accounts for 47% of the worldwide gaming market, besting console and PC. No wonder we've seen the rise of gaming smartphones, a class of phones that specialize in mobile gaming.

The Music sticker is one of Instagram's best features. With it, you can add music directly to your story, incorporating a high-quality soundtrack to your favorite moments. On June 6, Instagram upped the ante on this feature, introducing live song lyrics that play throughout your story. Karaoke, anyone?

Motorola is a shell of its former self. In 2010, it had just released the Motorola Droid, a phone so popular it led to all Android phones being called "Droids" by non-techies. But there have been some rough years between then and now, and Motorola's latest "flagship" doesn't look like it will help get them off this path.

In recent weeks we've talked about the growing trend of smartglasses makers moving the brains of their devices to smartphones, and now a veteran of the space has joined that movement.

In case you thought the long and unfortunate story of ODG was over, hold on, there's one last chapter to tell.

Websites are often misconfigured in ways that allow an attacker to view directories that are not ordinarily meant to be seen. These directories can contain sensitive information such as private credentials or configuration files that can be used to devise an attack against the server. With a tool called Websploit, hackers can scan targets for these hidden directories without difficulty.

For 2019, Sony is trying to shake its failures of the past and start fresh. Following the unsuccessful Xperia XZ series, Sony is changing the name of their flagship to a single number: Xperia 1. With the name change comes a few upgrades, one of which is its new look. Secondly, its new display is unmatched in the mobile space.

The HoloLens has made enough of an impact on the healthcare industry for Microsoft technology partner Medivis to convince investors to pledge $2.3 million in funding for its surgical platform.

Every step in the evolution of computing brings an in-kind leap forward in user input technology. The personal computer had the mouse, touchscreens made smartphones mainstream consumer devices, and AR headsets like the HoloLens and the Magic Leap One have leveraged gesture recognition.

The week of the annual Consumer Electronics Show is supposed to be filled with good news for the augmented reality industry as AR headset and smartglasses makers show off their new wares.

With more and more phones using OLED displays, the need for dark mode is at the highest it's ever been. Since dark backgrounds reduce battery consumption on these displays, the Android community has been begging Google to include a system-wide dark mode. Instead, Google gave us dark mode for many of their apps, including the Phone app.

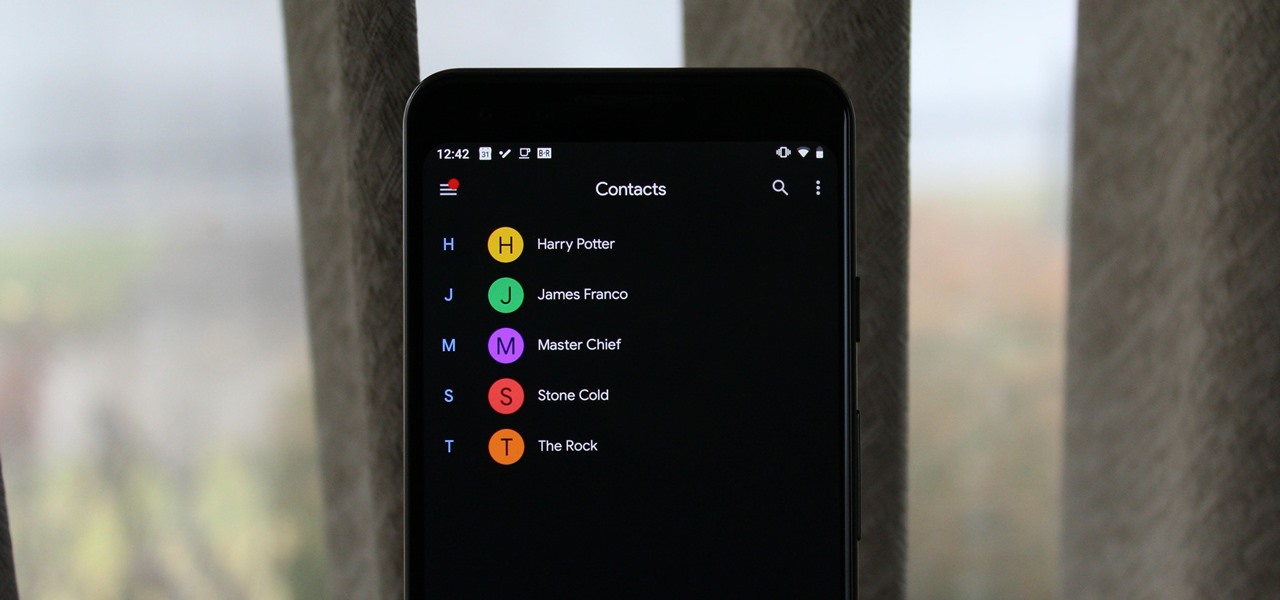
With the rise of OLED displays, Android users have been begging Google for a true system-wide dark mode for years. While a system-wide solution is still somewhat unlikely, Google has given in by providing a dark mode for certain apps, including Contacts.

Update February 25: The new Sony Xperia flagship has been announced, and it has a new name: The Sony Xperia 1. You can read all of the official specs and details at our full article on Sony's new model.

The dream of Google Glass lives on via North's stylish and normal-looking smartglasses that bring text messages and navigation prompts into the user's field of view and Amazon Alexa integration for voice-activated assistance.

Ever since the announcement of the Razer Phone, a wave of gaming smartphones started to hit the market. With ASUS being such a big name in gaming, it made sense for them to throw their hat in the ring. The result is the ROG Phone. And with this first try, ASUS has topped the rest, creating a gaming phone others should try to emulate.

In this jam-packed October, the Huawei Mate 20 Pro has flown under the radar in the US. Due to Huawei's lack of presence in the States, many are unfamiliar with the second largest OEM in the world. Huawei has continuously put out amazing mobile devices, and this year they released a phone that's nearly perfect on paper.

This week, Next Reality released the fifth and final set of profiles on the NR30 leaders in augmented reality, with this chapter focusing on the influencers in the industry.