Offensive pictures, depressing tweets, political statuses, and just plain old dumb comments are only a few of the reasons why people unfriend or unfollow others on social media sites. Sometimes it's just social spring cleaning, other times there's no reason at all.

We use smartphones for just about everything, and while that may be beneficial to us in our day-to-day lives, it can also be used against us in the court of law.

Written language began with one of the most pedestrian tasks imaginable: accounting. The basis of poetry, epic mythologies, and novels initially involved marking down trades between livestock owners and grain suppliers. We rightfully think that literature is essential to the human spirit. But when contemplating how societies operate, spreadsheets are king.

If there's anything we've learned during 2020, it's that working and learning from home is going to shift the way we do business. With Microsoft announcing that its staff will be allowed to permanently work from home, expect more businesses to follow suit.

The amount of information we see on a daily basis is overwhelming. Then there's all the data we never even see. If your career depends on making sense of all of this information, you need to understand the programs that do the heavy lifting.

Since its release in 1991, Python has become one of the world's most popular general-purpose programming languages. From data mining and web programming to cybersecurity and game design, Python can be used for virtually everything online.

No longer strictly relegated to the realm of science fiction shows and novels, artificial intelligence can be found behind important technologies that are driving innovation throughout the world. From space exploration and self-driving cars to data science and marketing algorithms, AI is the driving force behind many technologies that are moving humanity forward.

More information is available to us now than ever before. We simply cannot make sense of so much data on our own. Thankfully, we have programs to do the heavy lifting for us.

For all the benefits 5G brings to cellular data, it isn't without weaknesses, the biggest being privacy. Yes, the latest standard comes with breakneck downloads speeds up to 4.3 Gbps, but at what cost? Like with all things on the internet, 5G devices open opportunities for both good and bad actors.

File permissions can get tricky on Linux and can be a valuable avenue of attack during privilege escalation if things aren't configured correctly. SUID binaries can often be an easy path to root, but sifting through all of the defaults can be a massive waste of time. Luckily, there's a simple script that can sort things out for us.

When filtered through the prism of the top stories of the year, the business of augmented reality 2019 was defined as much by epic failures of AR startups as it was by the promising developments that propelled the industry forward into 2020.

After facing reports of financial troubles over the past month, Magic Leap came out swinging this week with a big push for the enterprise segment of AR, including a repackaged Magic Leap 1, a suite of enterprise apps, and updates to Lumin OS and its supporting development ecosystem. Oh, and its AR headset managed to win a starring role in the marketing juggernaut for the forthcoming Star Wars movie.

Google is an incredibly useful database of indexed websites, but querying Google doesn't search for what you type literally. The algorithms behind Google's searches can lead to a lot of irrelevant results. Still, with the right operators, we can be more exact while searching for information that's time-sensitive or difficult to find.

In our comparison of the best gaming phones in 2019, the winner actually surprised us. A phone that most people don't know about from a brand you probably haven't heard of ended up as the clear winner. But how? Well, it ticked so many flagship boxes despite its midrange price tag.

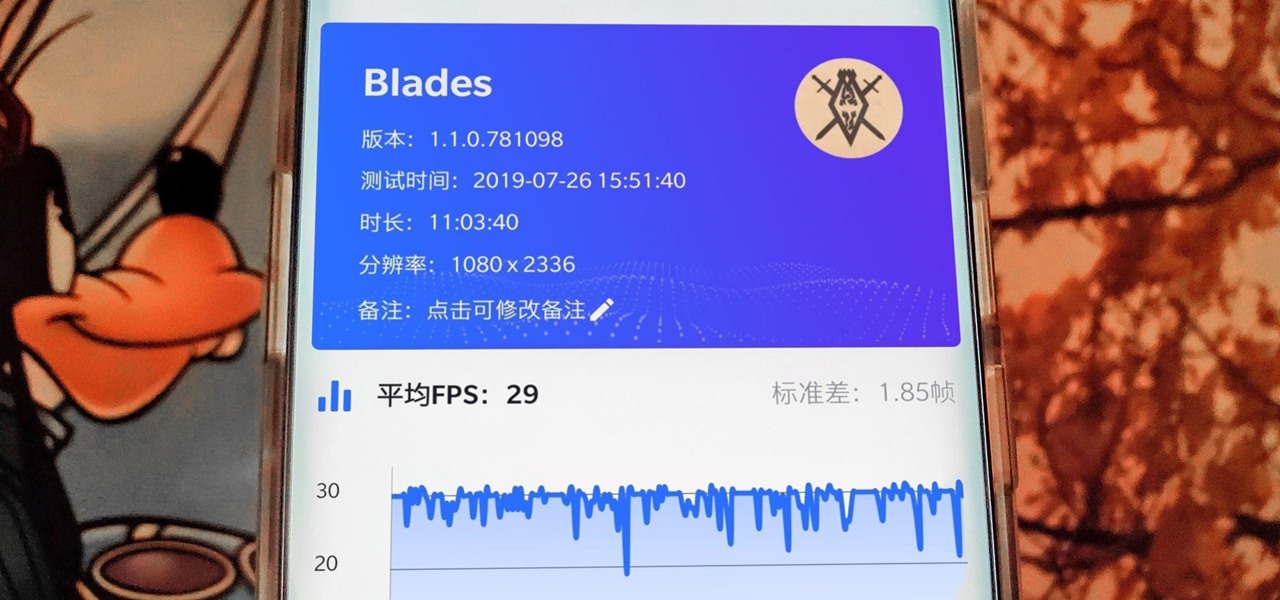
When you're gaming on your Android phone, does it sometimes feel "slow" and you can't figure out why? That means a drop in performance, which is when the frame rate dips, causing some noticeable stutters and lag. There's not really a way to know what's wrong unless you made the game yourself. But on the bright side, you can check any game's FPS with a simple tool.

When researching a person using open source intelligence, the goal is to find clues that tie information about a target into a bigger picture. Screen names are perfect for this because they are unique and link data together, as people often reuse them in accounts across the internet. With Sherlock, we can instantly hunt down social media accounts created with a unique screen name on many online platforms simultaneously.

Gathering information on an online target can be a time-consuming activity, especially if you only need specific pieces of information about a target with a lot of subdomains. We can use a web crawler designed for OSINT called Photon to do the heavy lifting, sifting through URLs on our behalf to retrieve information of value to a hacker.

This week, Next Reality released the fifth and final set of profiles on the NR30 leaders in augmented reality, with this chapter focusing on the influencers in the industry.

Continuing our NR30 series this week, we focused on the leaders of the software development industry that make augmented reality experiences possible. In other news, two of the current leaders in making AR headsets, Microsoft and Magic Leap, are pursuing multiple verticals with their products, as both now appear to be interested in making AR headsets for the military.

With Gboard, Google created a keyboard with more functionality than just inputting words. The app includes features such as GIF search and live text translation, but it gets even better when you let it learn more about you. With this data, Gboard grows from a good keyboard to one that can complete your sentences.

When traversing the web, you'll regularly come across websites that require you to create an account. With the majority of these accounts, protection is limited to a simple password. Despite this, many people are still using weak passwords such "123456." For these reasons, you really need a password manager, and our research has shown that LastPass is still your best bet.

You may have seen news reports over the last two days detailing a major security flaw in virtually all smartphones. The devices that are at risk are not limited to either iPhone or Android — all of us are affected. If you want to make sure your smartphone and its data stay secure, there are a few steps you can take.

Regarding foodborne pathogens, eating fish is not as hazardous as it was a few years ago — but if fins are on the menu, it's good to have a heads-up about what's good and what's bad these days.

While some researchers look for drugs to treat HIV, other scientists delve deep into the virus itself for answers on how it causes infections.

Killing more than 29,000 people each year, infection with Clostridium difficile (C. diff or CDI) is the most common healthcare-associated infection in the US. In a disturbing development, new research reveals recurring cases of the infection are soaring.

There is an Indian story called the Legend of Paal Paysam, and while it doesn't seem like it at first, it has a lot to say about what motivated Paul Travers in the augmented reality space.

Tell the truth. The bat picture creeps you out. You are not alone. But in reality, bats truly are some of our best friends. They gobble thousands of disease-spreading bugs a night. But they also carry viruses that can be deadly to humans. So, bats — friend or foe?

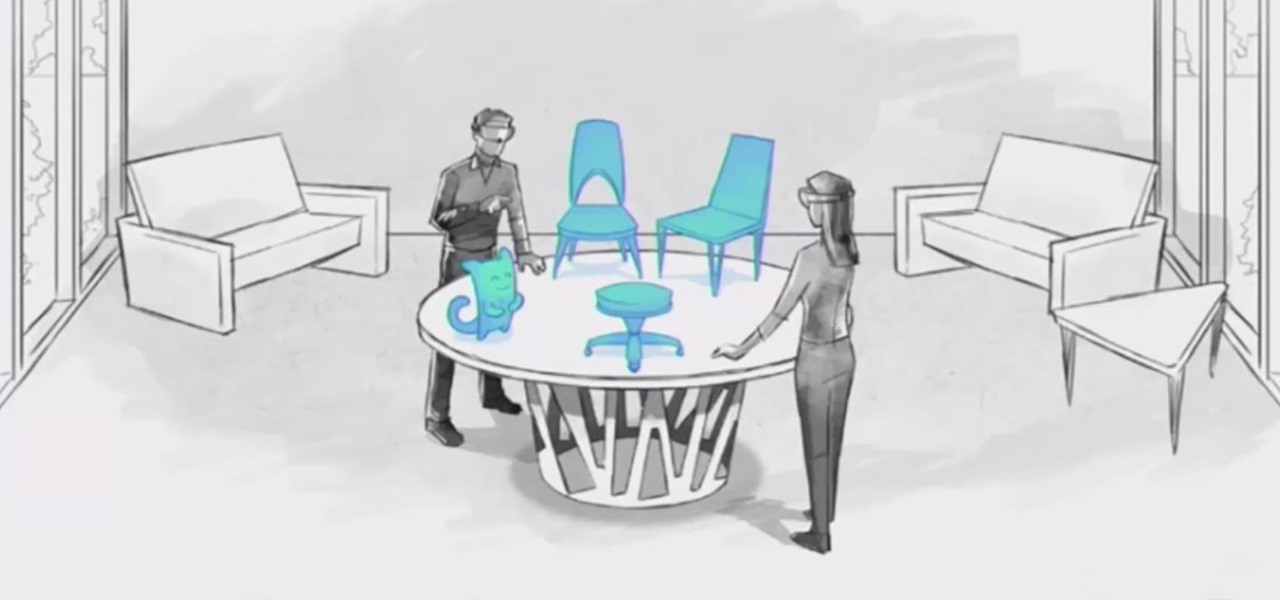
Those of us who are actively developing for the HoloLens, and for the other augmented and mixed reality devices and platforms that currently exist, are constantly looking for the next bit of news or press conference about the space. Our one hope is to find any information about the road ahead, to know that the hours we spend slaving away above our keyboards, with the weight of a head-mounted display on our neck, will lead to something as amazing as we picture it.

When it comes to global warming, most of us think of carbon dioxide emissions. While carbon dioxide is the most important greenhouse gas, carbon dioxide emissions have stayed constant for the last three years. On the other hand, methane, the second most important gas, has been steadily rising since 2007.

With new diet and health claims coming at you everyday, it's sometimes hard to know what to believe. Well, here's a bright spot: A pair of studies confirm that whole grains are healthy for you, and for the diversity of microbes living in your gut.

Six people have died from fungal infections in Pittsburgh hospitals since 2014—that fact is indisputable. The rest of the situation is much vaguer. A lawsuit has been filed against the hospitals on behalf of some of the deceased patients, alleging that moldy hospital linens are to blame. While the lawyers argue over who's at fault, let's look at how this could have happened.

A recent study underscores a connection between climate change and infectious disease, raising concerns about our quickly warming planet.

The food TV chefs prepare make our mouths water. From one scrumptious creation to another, they fly through preparation without frustration or error. They make us think we can do the same with similar ease and delectable, picture-perfect results. Some of us have noticed, though, that these TV chefs don't always adhere to the same safe food handling guidelines we've been taught to follow.

To much of the United States, Zika seems like a tropical disease that causes horrible problems in other countries but is nothing to be worried about stateside. It may make you rethink your beach vacation abroad, but not much more than that. However, if you live in Florida or Texas, the possibility of getting a Zika infection where you live is real — and local outbreaks are more and more a possibility.

When a dead body is discovered, finding out when the person died is just as important as finding out how the person died. Determining the time of death has always involved lots of complicated scientific detective work and less-than-reliable methods. However, a study by Nathan H. Lents, a molecular biologist at the John Jay College of Criminal Justice in New York, is the first of its kind to show how microbes colonize a body's ears and nose after death.

Welcome back, my novice hackers! In this series, we have been exploring how a forensic investigator can find evidence of illegal or illicit activity. Among other things, we have examined the registry and prefetch files for artifacts and have done some rudimentary forensic analysis. For those of you who are seeking career as a forensic investigator or security engineer, this can be invaluable training. For hackers, it might be life-saving.

Welcome back, my budding hackers! As I have mentioned many times throughout this series, knowing a bit of digital forensics might keep you out of a lot of trouble. In addition, digital forensics is a burgeoning and high paying career. Some knowledge and certifications in this field will likely help you land a Security Engineer position or put you on the Incident Response Team at your employer.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Welcome back, my greenhorn hackers! As hackers, we often take for granted that nearly all of our hacking tools and operating system are free and open source. I think it's important to examine a bit of background on how we arrived at this intriguing juncture in the history of computer software. After all, we pay for nearly all of our other software (Microsoft, Adobe, etc.) and nearly everything else we use in life, so how is it that Linux and all our hacking tools are free?

Welcome back, my novice hackers! This next subject might seem a bit obscure, but I promise you, this lesson will benefit you significantly either as a hacker or system admin. This tutorial will cover what is usually referred to as a regular expression, or regex for short.