
Snapchat may trail Facebook and Instagram in terms of daily active users, but a new partnership with Samsung may get those innovative AR Lenses onto the mobile devices of a lot more users.
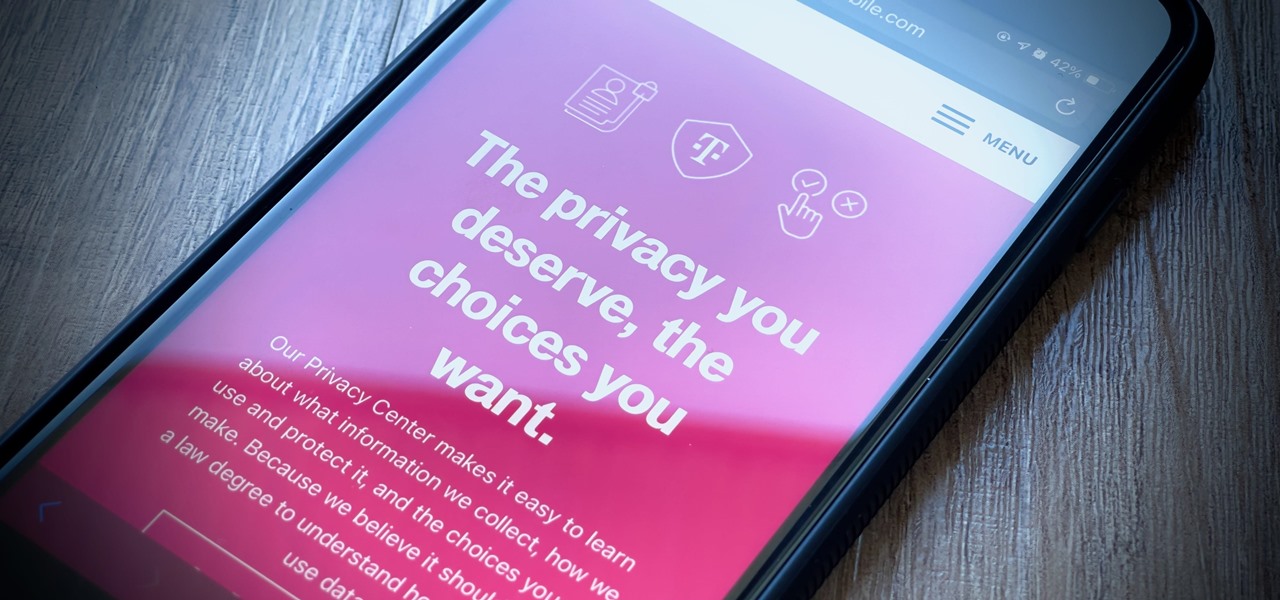
It's getting harder and harder to escape ad tracking by the day. For the latest example, look no further than T-Mobile. The No. 2 carrier updated its privacy policy on Feb. 23, 2021, indicating that it would start sharing customer data with advertisers under the guise of more relevant ads starting April 26. If that's not something you'd like to participate in, there's a way to opt-out.

The year is still off to a roaring start, with augmented reality at the center of nearly everything, from enterprise solutions, to entertainment, to safety.

Among the various components of the emerging augmented reality space, the most lucrative is the advertising market. The prospect of turning every object, every location, ever signpost in the real world into a discount code or virtual transaction interface is why AR will ultimately be more profitable than VR.

When life hands you lemons, make lemonade. At Magic Leap, the lemons are the COVID-19 pandemic, and the lemonade is a new solution for virtual meetings born out of social distancing.
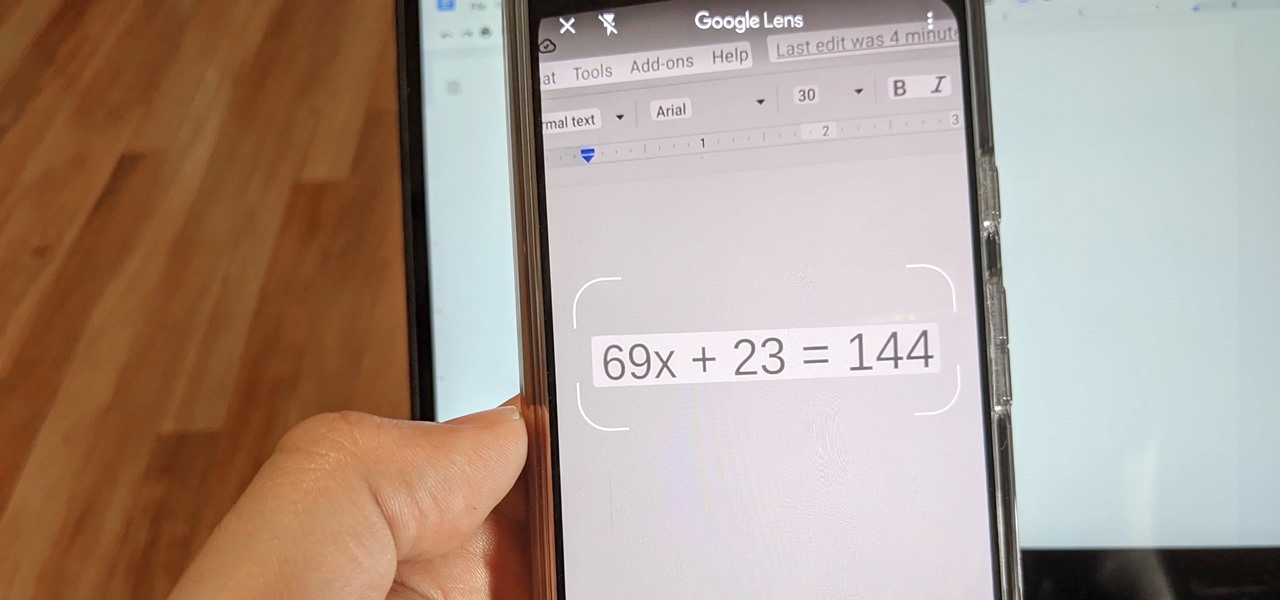
Since launching Google Lens as a a Pixel-exclusive feature in 2017, Google has not only expanded the availability of the tool to Android and iOS, but also built upon its functionality. Now, in addition to translator, tip calculator, personal shopper, and tour guide, Google has added math tutor to the job description for Google Lens.

For a hacker, there are a lot of advantages to creating a fake network. One advantage forces nearby devices to use their real MAC address if you happen upon a network that's stored in their preferred network list.

So you want to know what that person who is always on their phone is up to? If you're on the same Wi-Fi network, it's as simple as opening Wireshark and configuring a few settings. We'll use the tool to decrypt WPA2 network traffic so we can spy on which applications a phone is running in real time.

It's safe to say that we can call the annual ranking of AR investments a holiday tradition at Next Reality.

Windows 10 passwords stored as NTLM hashes can be dumped and exfiltrated to an attacker's system in seconds. The hashes can be very easily brute-forced and cracked to reveal the passwords in plaintext using a combination of tools, including Mimikatz, ProcDump, John the Ripper, and Hashcat.

Apple might not have been the first to add a night camera mode to its suite of smartphones, but it's pretty impressive nonetheless. With "Night" mode, your iPhone can shoot photos with incredible detail in some horrendously dark lighting conditions. But when you open up your new iPhone to try it out, you might be wondering how you turn it on.

You may have recently seen a plethora of Instagram users, including celebrities and politicians, sharing a screenshot declaring that the platform will implement a new "rule" where it would own and could use your photos and videos however it wishes. The screenshots are part of an internet hoax, one that's been around in one way or another since 2012, but what can Instagram actually do with your media?

Microsoft.com is one of the most extensive domains on the internet with thousands of registered subdomains. Windows 10 will ping these subdomains hundreds of times an hour, making it challenging to firewall and monitor all of the requests made by the operating system. An attacker can use these subdomains to serve payloads to evade network firewalls.

Automating port scanners, directory crawlers, and reconnaissance tools can be complicated for beginners just getting started with Kali Linux. Sparta solves this problem with an easy-to-use graphical interface designed to simplify a penetration tester's tasks.

Websites and web applications power the internet as we know it, representing a juicy target for any hacker or red team. TIDoS is a framework of modules brought together for their usefulness in hacking web apps, organized into a common sense workflow. With an impressive array of active and passive OSINT modules, TIDoS has the right instrument for any web app audit.

Directory traversal, or path traversal, is an HTTP attack which allows attackers to access restricted directories by using the ../ characters to backtrack into files or directories outside the root folder. If a web app is vulnerable to this, an attacker can potentially access restricted files that contain info about all registered users on the system, their permissions, and encrypted passwords.

The year 2018 was a rough one for Snap, the company behind the Snapchat app and the Spectacles wearable camera device. From executive departures to reports of slowed user growth, the company that once spurned Facebook's multibillion-dollar advances is now facing a moment of truth as it stares down its uncertain future.

Whether it's for health reasons or just to look better, many of us want to get in shape. It's a long process that starts with nutrition, and dieting is never easy. Fortunately, there are some great food-tracking apps that will make it a lot easier to become a healthier version of yourself.

While keeping your iPhone out of the bedroom might help to avoid unnecessary distractions before bedtime, it could be better served right by your side to help diagnose sleeping issues you may be experiencing each night.

The idea of a perfect phone is a myth. There are lots of pros when it comes to OnePlus devices, but there are also a few things that could be better. And even if there were a phone without flaw, there are still things that you might want to customize for personal preference. That's why we set out to find the very best tweaks for OnePlus phones, and to make it easier for you to apply them.

Encrypting payloads and encoding stagers are more effective against macOS than one might think. It's very easy to evade VirusTotal and macOS antivirus software using a few simple tricks.

Ever since the announcement of the Razer Phone, a wave of gaming smartphones started to hit the market. With ASUS being such a big name in gaming, it made sense for them to throw their hat in the ring. The result is the ROG Phone. And with this first try, ASUS has topped the rest, creating a gaming phone others should try to emulate.

Reconnaissance is the phase of an attack where a red team or hacker designs a strategy based on the information they can learn about the target, as well as what the available attack surface looks like. These scans can take time to discover relationships, but Raccoon OSINT scanner coordinates multiple automated scans to produce invasively detailed reports on a target with a single command.

The war on dehydration is a commercially burgeoning marketplace. An increasingly sophisticated consumer population hoping to conquer everything from 26-mile marathons to vodka shots is deconstructing every functional remedy in the fight to quell the effects of severe dehydration.

They're finally here — Samsung has officially revealed the Galaxy S9 and S9+, which run Android Oreo out of the box. Since we've spent plenty of time with the Oreo beta for the Galaxy S8, we already know about some of the best new software features coming to the Galaxy S9. Like previous updates, Samsung has enhanced its software with a fresh look and brand new functionality.

Dating websites allow you to see a person in a very intimate context, framing their successes and accomplishments in life to an important audience. The information contained in these profiles often can't be found elsewhere, offering a unique look into the personal life of the user.

For almost a decade, projector phones have tried to entice consumers with their convenience as media machines. While these devices are alluring, they've never really taken off with mainstream success. The latest effort, Moviphone, sounds tempting if you watch a lot of films and TV on your smartphone, but is it good enough to be your daily driver?

Open-source data scraping is an essential reconnaissance tool for government agencies and hackers alike, with big data turning our digital fingerprints into giant neon signs. The problem is no longer whether the right data exists, it's filtering it down to the exact answer you want. TheHarvester is a Python email scraper which does just that by searching open-source data for target email addresses.

Throughout this NR50 series, we have talked about the incredible growth the augmented and mixed reality space has seen in the last year. More devices, software, developers, and use-cases seem to arrive daily. For this growth to have occurred, it took the work of many people, from many different backgrounds and skill sets — and Next Reality wants to recognize them for all that they have done and are doing.

If you live with pets, you know where their tongue has been, yet you let them kiss and lick you all they want without even thinking twice about it. I've heard people say that a dog's mouth is very clean, and that their saliva, delivered by licking, can help heal wounds, but is that really true?

Welcome finally, to a tutorial on buffer overflows! At last we have reached an exciting part of this series where I will dedicate the entire article on explaining and exploiting the notorious vulnerability. Grab some popcorn, sit back and enjoy the show.

It's been a while when the major web browsers first introduced HTTP Strict Transport Security, which made it more difficult to carry Man In The Middle (MITM) attacks (except IE, as always, which will support HSTS since Windows 10, surprised?).

Apple's newest mobile operating system, iOS 8, is out for the general public, and we've got a rundown on the best new features you can use on your iPad, iPhone, and iPod touch. While there's not a huge visual change as there was from iOS 6 to iOS 7, there's still plenty of cool new features in iOS 8 to be excited about.

Many of my aspiring hackers have written to me asking the same thing. "What skills do I need to be a good hacker?"

It can be hard finding fellow singles in the suburbs but it can be done! Keep your eyes peeled and make sure you are out and about meeting new people in public settings. Don’t forget about your online or in print options.

Dyeing your hair is a great way to change your look. But if you don't do it right, the results can be pretty ghastly. If you seek a new do without the harsh chemicals, these steps will give you the locks you’ve been looking for.

A CNC router machine is probably the most useful tool a hobbyist can own, but the price for a CNC machine on the market is way more than the average hobbyist is willing to spend. You can build your own CNC with very basic tools, little knowledge of machinery, mechanics, or electronics, but be warned, these machines are inherently dangerous, so wear the proper protection and use common sense. At the very least, read the instructions and precautions on every tool you use.

Human life has been wiped out. Extinct for 20 years. Destroyed by a nuclear holocaust. But there are a few survivors on Earth, and they're forced to live in the underground metro systems in the big cities. But it gets worse. There's mutant beasts, communists, Nazi factions, and even psychic powered Dark Ones that endanger your lives every second. This is Metro 2033, and this walkthrough series from Mahalo will show you the entire gameplay on the Xbox 360. Can life really be like this in the M...

And then there was light…on your pen. Have a little fun and with a little ingenuity and a couple of matchsticks you can liven up any afternoon by pranking your friends with this magically burning pen.

You can learn to deal with the thing we all dread, a computer crash. Hopefully you diligently back up work but even if that's not case, stay calm. There is still hope and even if you're not a wiz at computers there are people out there who can help.








































