Well folks, the dream is coming to life. While we still may be a ways away from mind control, the team over at Thalmic Labs has created the Myo, and with it, the power of the Force comes to motion control, so long as you use it wisely.

Welcome back, my greenhorn hackers! My preference for Linux as a hacking platform is well documented, and I have even created a series of tutorials to train new hackers. Without being proficient in Linux, you can't really call yourself a hacker.
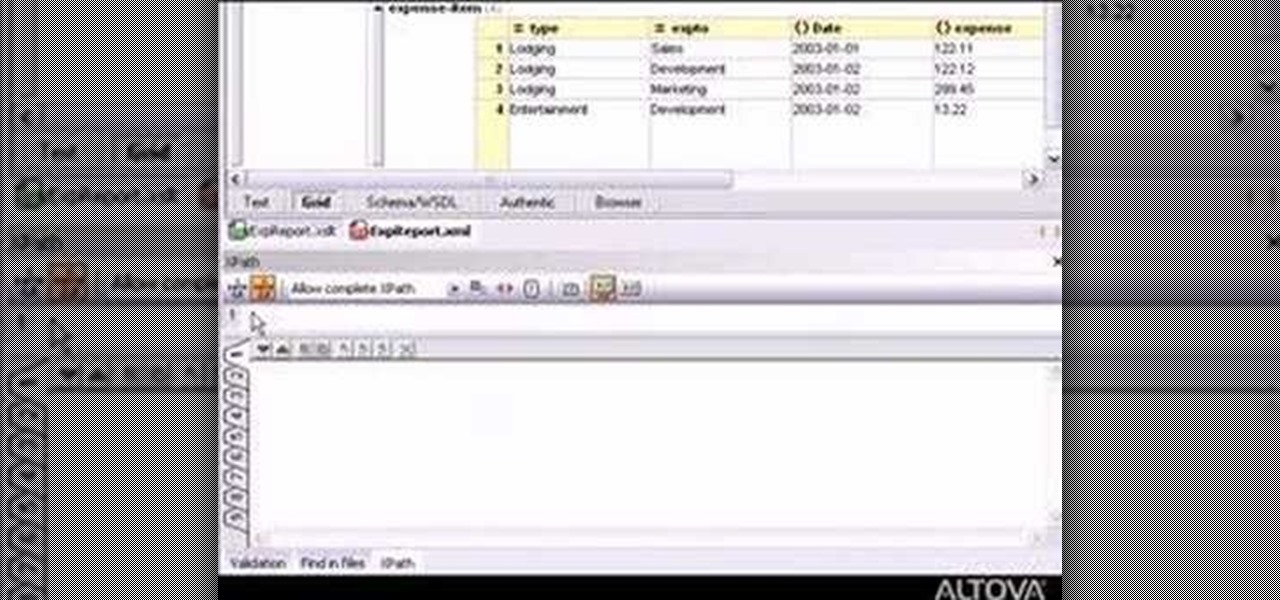
Desire to be an XML editor/programmer? This video will help you. You'll learn how to edit, analyze, and debug XPath expressions with XMLSpy.

A convincing domain name is critical to the success of any phishing attack. With a single Python script, it's possible to find hundreds of available phishing domains and even identify phishing websites deployed by other hackers for purposes such as stealing user credentials.

Your email inbox is a treasure trove of personal data. The people you contact, your writing style, which messages you flag as spam — all of this information and more can be used to paint a clear picture of you. Google knows this as well as anybody, so they use this data to constantly improve your experience in Gmail.

Welcome back, my hacker novitiates! If you have been following this new Snort series, you know that Snort is the world's most widely used intrusion detection/protection system. Now a part of the world's largest network equipment company, Cisco, it is likely to be found everywhere in one form or another. This makes a compelling argument for learning how to use it, as it will likely be a necessity in any security-related position.

Starting up a website can be daunting if you know nothing about web design or setup, but there are some tips to get the right people finding, looking, and returning to your site. A good landing page gives visitors exactly what they are looking for, and converts them from browsers to customers.

Whatever your reasons for doing it, if you are trying to hack passwords, it helps to have the right software for getting the job done. With the Cain and Abel program, you will be well on your way to hacking even the toughest personal passwords.

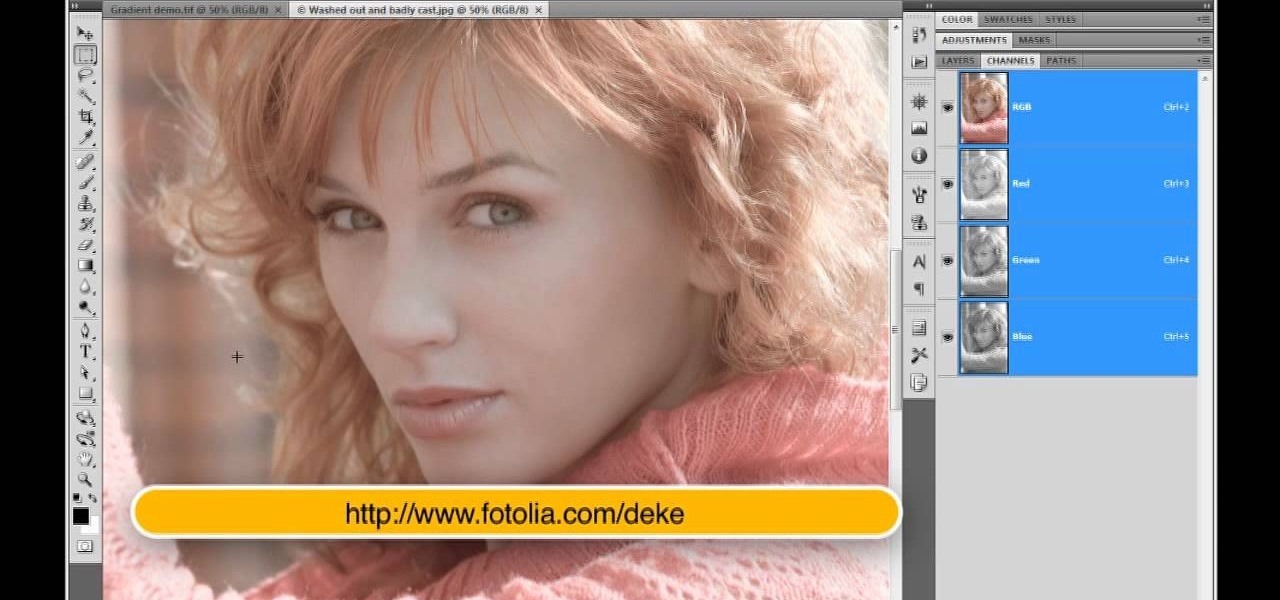
Deke McClelland explains what the Levels and Histogram commands can do in Photoshop in this video tutorial. Levels allows you to adjust the luminance levels allowing you to adjust the contrast and colors within each color channel of an image. Thus, Levels allows you to adjust the individual colors that can be found within a gradient. This command is very similar to the curves command but to a less powerful extent. It is also more efficient than the curves command. The Histogram is another col...

This is a step-by-step guide to cleaning out those old fires in your Windows XP computer. You want to start by clicking the "start" button and then clicking on "my computer". Once there, you are going to want to right click on the C-Drive to clean that one first and click on "properties". Once the box opens you want to click on "tools" on your tool bar and then click on the "defragment now" button. When the box opens click on the C-Drive and then click "Analyze" to

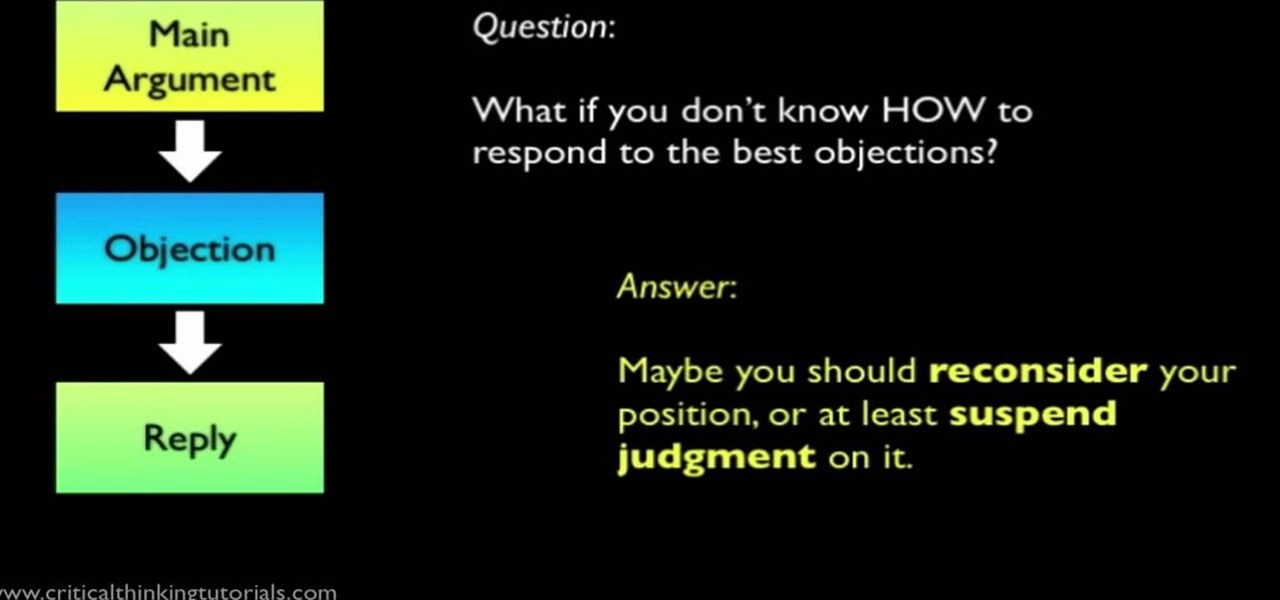
In this tutorial video, you will learn the basic structure for a good argumentative essay. The narrator in this tutorial, makes a very important distinction in the video; a good argument versus an average or mediocre argument. The narrator teaches you that a good argument will have, at minimum, a 5-part structure. The elements in the structure include an introduction, a body, and a conclusion. Within the body, a good argumentative essay would contain a main argument, an objection, and a reply...

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to build a mini multi-touch table and photo stitch.

Taking a group portrait can be a pain. Here’s how to make it go as smoothly as possible. Check out this Howcast video tutorial on how to take a group portrait.

Start with just a little bit of money and the multiply it into a vast fortune! All you need is the most current version of the free game hacking software, Cheat Engine! Then open your game in Firefox and follow the tutorial!

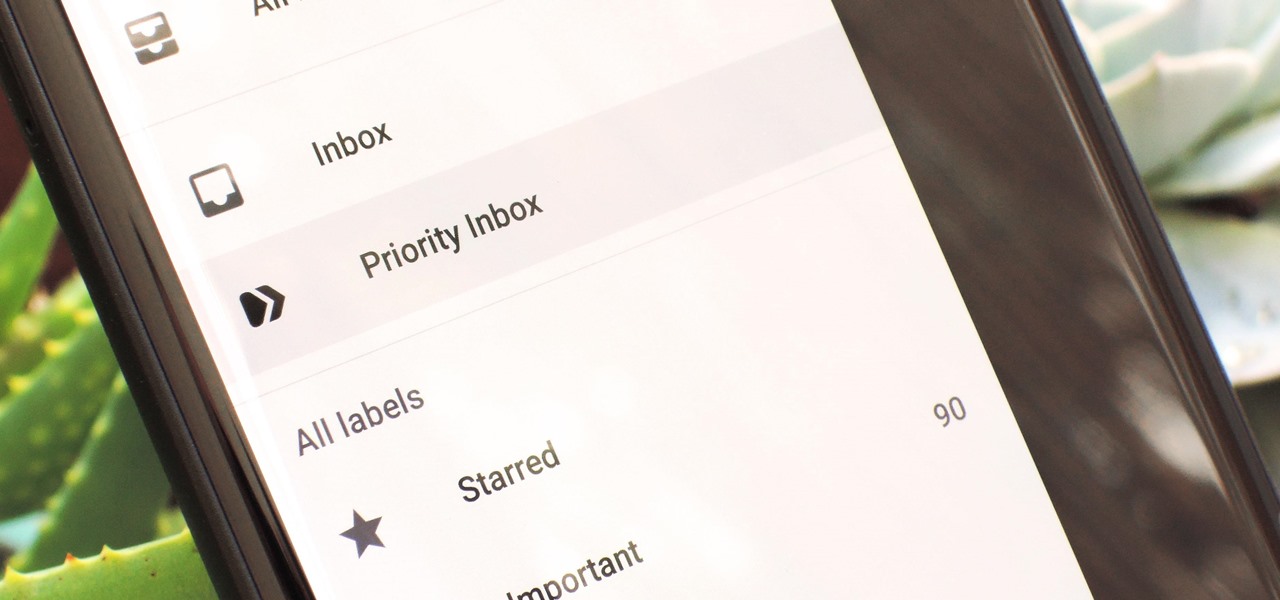
For many of us, getting to inbox zero is the highlight of our day. But if you used your email address to sign up for various sites and services, your inbox is probably cluttered with all sorts of spam, news letters, and unimportant emails. Thankfully, Gmail has a feature that can solve this by using machine learning.

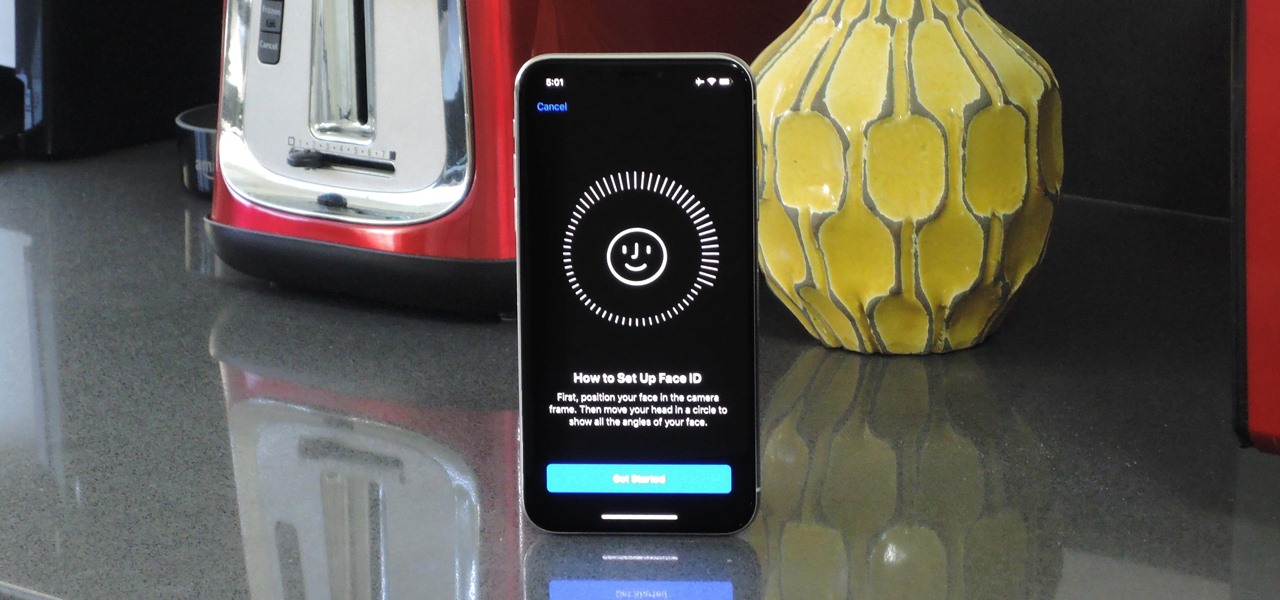
The cutting-edge iPhone X, XS, XS Max, and XR have one-upped their Android competitors when it comes to facial recognition. Apple packed these flagships with an array of front-facing sensors to complement its selfie camera, which allows the new device to more accurately analyze faces, which you need for Face ID, Touch ID's replacement.

Onshore, or on a boat, have you ever wondered what swims below in the dark water? Using standard equipment and a new process, marine scientists can now get a good look at what is swimming by—just by analyzing the water.

A couple weeks ago, GM's Cruise Automation released a remarkable self-driving video from the streets of San Fransisco that Driverless analyzed in detail. And now they've just released a new one giving more insight into their growing mastery of the complex roads in San Francisco, specifically, the Potrero Hill and Mission Dolores neighborhoods.

In this article, we will explore the basics of radare2, a powerful package that comes with Kali. We are going to write a simple program, and then disassemble it, to see what is really doing in the processor.

Hi everyone! Last time we explained what roles Ebp and Esp registers have. We first introduced function's stack frame building, return address and calling conventions, but left some of the concepts floating without a full stop.

With over a million apps and counting, it's not exactly easy to browse the iOS App Store to find fresh and interesting new apps for your iPad or iPhone. Even rummaging through the featured apps and games isn't easy.

If you are looking to improve your classical piano technique then this three part how to video is the place to start. You will learn how to practice and study Chopin's nocturne number 20 in C# minor. This detailed lesson goes over where to place the accents, analyzes the dynamics and legato playing technique. This piano tutorial teaches you the best way to practice it so you can Chopin's nocturne no.20 quickly and easily. This piece is not for beginner students, this lesson is directed to adv...

The life of a busy entrepreneur isn't easy. In addition to coming up with original business ideas and marketing strategies, you also need to be continually thinking about investors, overhead, the competition, and expanding your customer base — often with a limited budget.

The term "hacker" often has negative associations attached to it, yet the world is in dire need of professionals with hacking skills. White hat hackers are ethical computer hackers that use their hacking skills to pinpoint network vulnerabilities and patch them up before they can be exploited by the bad guys.

If you're reading this, you're likely a tech-savvy coding pro whose analytical talents are mostly applied to designing apps, cracking passwords, and infiltrating networks — all of which are admirable activities for both aspiring and seasoned white hat hackers. But there are other profitable ways that you can put these types of skills to use, namely in the world of investment and trading.

Before the internet, acquiring enough data to analyze was challenging. Now we have the opposite problem: a deluge of data makes trying to sort through it nearly impossible. That's where data science comes in.

The overarching and expanding field of data science and analysis has become virtually inseparable from areas such as programming and development.

For over three decades, Microsoft's landmark program, Excel, has helped businesses accomplish tasks and problem solve quickly and efficiently. Whether you're a budding entrepreneur or navigating a remote career, Excel can help you apply your business skills at a higher level.

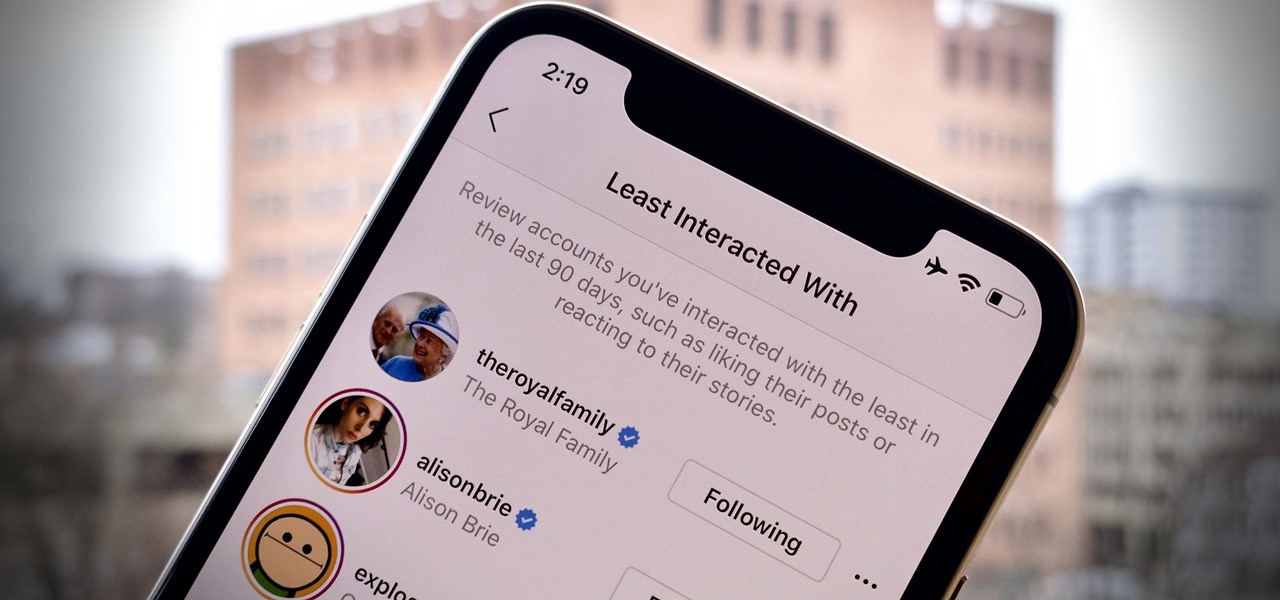
Is your Instagram feed a bit cluttered? Maybe you're seeing posts from people you don't even recognize. Perhaps the content isn't interesting. Whatever the case, it's common after years of having an account to follow too many users whose posts just aren't doing it anymore. Luckily, Instagram has an easy way for you to purge unwanted accounts from your following list.

Auditing websites and discovering vulnerabilities can be a challenge. With RapidScan and UserLAnd combined, anyone with an unrooted Android phone can start hacking websites with a few simple commands.

While augmented reality is a means for presenting news to their audiences to some media outlets, Bloomberg is interested in how the technology can improve the way journalists work.

According The Venture Reality Fund, the introductions of Facebook's camera platform and Apple's ARKit catalyzed increased activity among companies developing consumer applications.

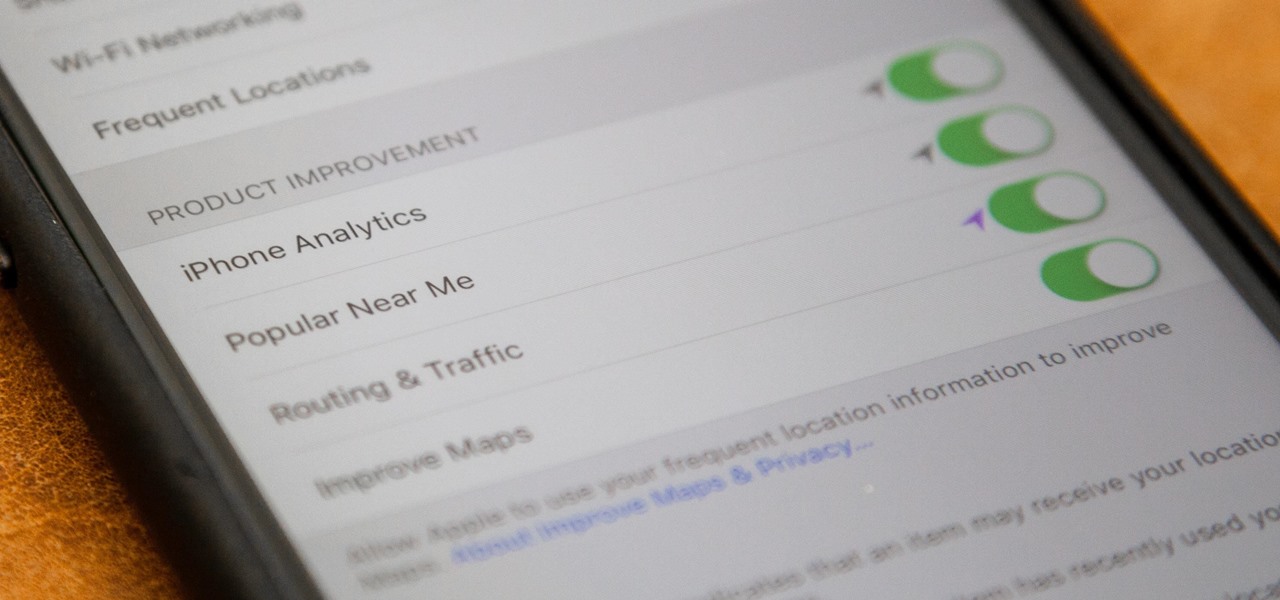
If you just installed the iOS 11 beta on your iPhone, you're automatically sending your location data to Apple — even if you don't want to. Luckily, there's an easy way to prevent Apple from seeing this data if you don't want them to.

Microsoft, even being Apple's fierce competitor, is no stranger to producing iOS apps—in fact, they've made 94 of them. But their latest iOS app may be their silliest yet: a goofy photo editor named Sprinkles.

Anyone who paid attention to the Lavabit shutdown had a feeling it was connected to Edward Snowden, the high-profile NSA whistleblower. Ever since the government's case against Lavabit went public in late-2013, people have put two and two together.

In a study attempting to observe virality in real time, two Microsoft engineers, Corom Thompson and Santosh Balasubramanian, used Microsoft's recently released Face detection API to create How-Old.net and track its usage in real time.

Animal lovers, especially dog owners, know that pets are a part of the family, but it's often incredibly frustrating to know if and when something just isn't right with our furry companions. If you're out and about most of the day, your dog will be so happy to see you when you come home that you may have no idea they were tired and listless all day long, which can be a sign of health problems for your pup. This is where FitBark comes in.

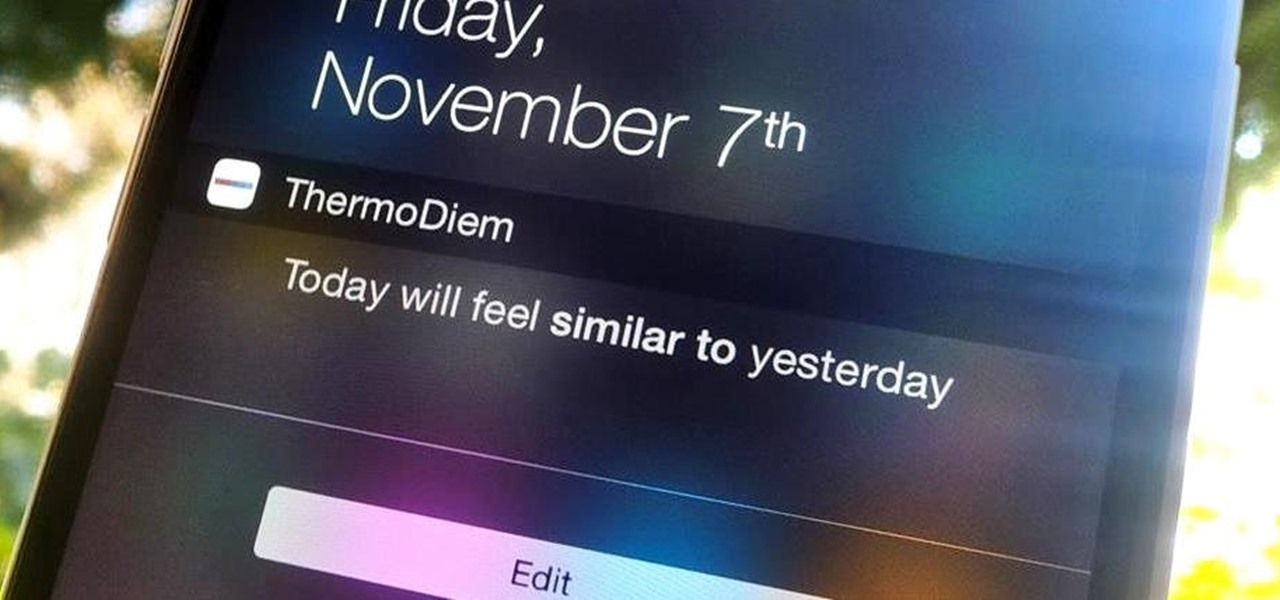
When I get weather information, I prefer to receive it in a straight-forward, minimalistic fashion. Living in California, I could care less about wind speeds, humidity, or any other calculations that I can't analyze in a second. I essentially use the information to help decide whether I'll be wearing shorts or pants on a given day, so give it to me bluntly.

Having your phone ring loudly in a quiet environment could be potentially embarrassing for you, but also quite annoying for everyone else that didn't forget to put their smartphone on silent. Whether it's in class, at work during a meeting, at the library, or a movie screening—you can bet that someone's phone is going to ring loudly, pissing some people off. You don't really want to be that douchebag that interrupts a movie or the middle of a lecture with their annoying ringtone just because ...

If you don't have a car, or just prefer to take public transit to work, you know that an unexpected change in the weather can quickly...er, dampen your day. If you're not expecting it, rain or snow can turn your trip into a long, hellish ordeal—especially if you bike.