As smartphones become more accessible, billions of people have come to depend on their features for daily life. One of the most important aspects these days is the camera. OEMs have been working for years to improve camera quality, and they seem to have finally figured it out — the best way to achieve DSLR-quality photos wasn't just with better sensors, but with better intelligence.

Influenced by the growth of augmented and virtual reality technology as well as 3D computer vision, Ericcson Ventures invested in Matterport, whose hardware and software help companies create AR/VR experiences.

Hello again, folks! I'm back with another (final) guide on runtime crypters which is an extension on my previous runtime crypter guide. If you have not read it yet, I highly recommend that you do since the fundamental theory of the PE format. Again, this will be a Windows-specific guide, so I'll repeat this: If you're a hater and cringe at the slightest sound of Microsoft's grotesque baby, feel free to close this tab, delete your history, exit your browser, pour some oil onto your machine and...

Welcome back, my neophyte hackers! Digital forensics is one of the fields often overlooked by aspiring hackers. In a rush to exploit every and any system they can, they often ignore learning digital forensics—the field that may lead to them being traced.

On June 5th, robotics firm Aldebaran and SoftBank Corp., the Japanese giant that owns Sprint (and possibly T-Mobile), unveiled an emotion-sensing robot named Pepper.

This week in Market Reality, we see two companies capitalizing on technologies that contribute to augmented reality platforms. In addition, industry mainstays Vuzix and DAQRI have business news of their own to report.

In this video from the ID Theft Center, learn exactly what identity theft is and how to prevent it from happening to you. Identity theft can happen to anyone - young, old, living, dead - thieves do not discriminate. This helpful video will tell you exactly what to look out for and how to avoid scams. Your host will explain how identity thieves operate and how to cut them off at the pass.

Now more than ever, people everywhere are suffering from bad credit. Credit is important. You need it to take out loans, buy a house, rent an apartment, get a car, almost anything! Check out this two part video, presented by Daniel Medina from United Credit Education Services, and listen along as he offers you tips on how to improve your credit - even in a recession. This helpful and informative video can start you on the right track to financial stability, no matter what the circumstances.

It seems nowadays there's no limit to what type of companies are looking to invest in augmented reality. Given both the positive outlook on the future of AR, and its reported benefits for efficiency in employees, this makes sense. Safran, an international corporation with three main sectors—aerospace, defense, and security—is one such company taking the plunge into incorporating AR in their business.

Researchers have been studying the blood meals of flies to understand the flow of infectious pathogens in wild animals.

Hola my fellow hackers! I promised you the tutorials on setting up RAT's and Botnets, but before jumping into those, i want you to know about the precautionary measures and detection of RATs which might be on the system without your prior knowledge. Of course the Anti-virus do most of the job but there are some RATs which slips past the Anti-viruses (This is where Hacker's skill come into play).

Welcome back, my greenhorn hackers! Digital forensics and hacking are complementary disciplines. The better you are at digital forensics, the better hacker you are, and the better hacker you are, the better you are digital forensics. Unfortunately, few people in either profession cross these discipline lines.

My college days are long behind me, and while I don't necessary miss them, I am jealous of all the countless resources available to students these days. Apps like PhotoMath are something I wish I had access to in my student days, making assignments less strenuous and easier to complete.

With the Wigle WiFi app running on an Android phone, a hacker can discover and map any nearby network, including those created by printers and other insecure devices. The default tools to analyze the resulting data can fall short of what a hacker needs, but by importing wardriving data into Jupyter Notebook, we can map all Wi-Fi devices we encounter and slice through the data with ease.

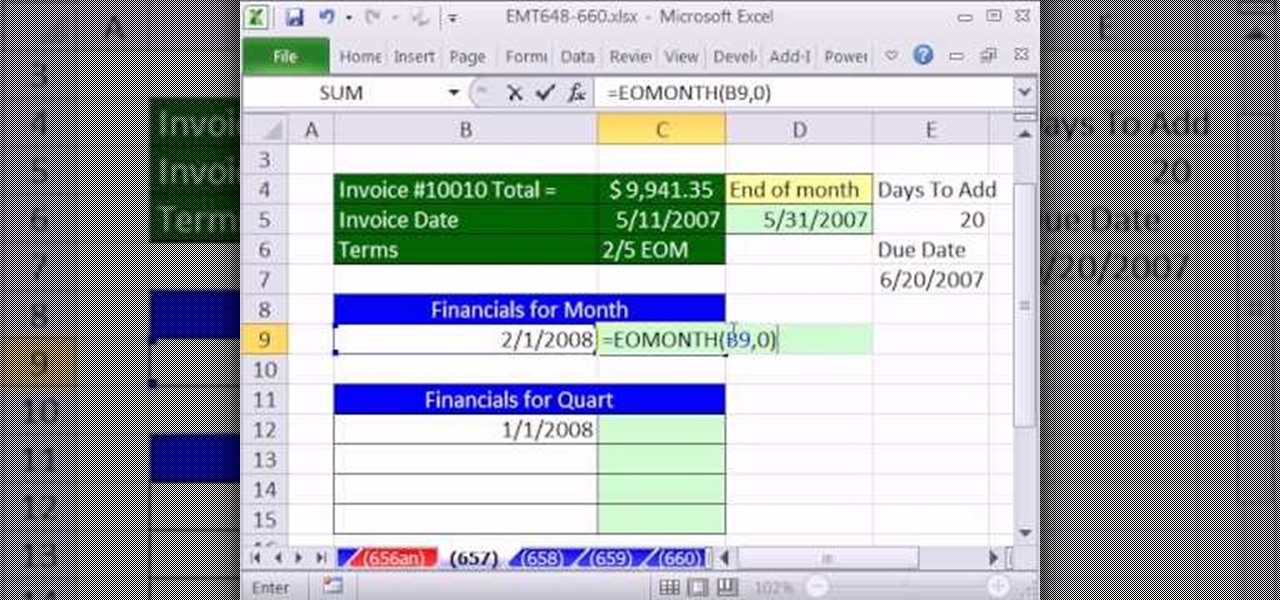
New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 657th installment in their series of digital spreadsheet magic tricks, you'll learn see howto calculate Invoice Due Dates & Financial Statement Dates using the EOMONTH function including end of the month and beginning and ending dates for each quarter.

If you're playing word association with the terms "augmented reality" and "automobiles," your first thoughts probably center on navigation displays in cars or virtual models of exotic vehicles.

Investors aren't keen to throw money at a new technology sector without at least some hope of a significant return on their investment in the future. That's why a recent run of activity within the augmented reality business space has stoked some new optimism among the financial community.

Faraday Future's all-electric super sports car concept attracted a lot of attention at CES earlier this year, but now it is struggling to replace key driverless engineers and program directors who left the company amid its recent financial troubles.

Parents rejoice, Apple Pay is making it much simpler for your kid to use Greenlight, the MasterCard for kids app.

Welcome to the maiden voyage of our new Market Reality column. Each Friday, NextReality will give you a roundup of news briefs from the financial end of the augmented and mixed reality industry. We'll cover funding news, market analysis, and more.

Last week, the U.S. Justice Department issued criminal indictments against seven Iranian hackers. These hackers, working for private companies in Iran, are accused of orchestrating DDoS attacks against U.S. financial institutions from 2011-2013 as well as intruding into the control panel of a small dam in Rye, New York. It is thought that these attacks were a response to the U.S. tightening financial restrictions on Iran during those years and the NSA-based Stuxnet attack on their uranium enr...

This video tutorial is for educational purposes only. See how to pick a normal lock with a tension allen wrench and a small screwdriver.

Tired of walking everywhere? Does your only ride have two wheels and a bell? Check out this video and learn tips and tricks for convincing your parental units to buy you a car. Pretty soon you will be cruising through town and the envy of all your friends.

This video questions whether or not the writer should stay with her boyfriend who is living with his last girlfriend. The advice given is it's dangerous. If you truly love this guy then you want a personal relationship with him. It’s going to be hard with him living with his last girlfriend. He may be truthful about not wanting to be with her. On the other side of the coin it would be so easy for him to accidentally slip up. Since the ex-girlfriend and he have been down that road before it wo...

With divorce rates set to hit a record high this year, 'betterdatethannever' explains how to avoid arguing with your partner. Most people experiencing marital difficulties blame financial reasons for their fights. The easiest way to avoid conflict with your partner is to make sure you communicate and share your problems. Holding things deep inside makes them get worse and worse till they explode into one huge argument. Allow your partner to speak their mind and express things they do not like...

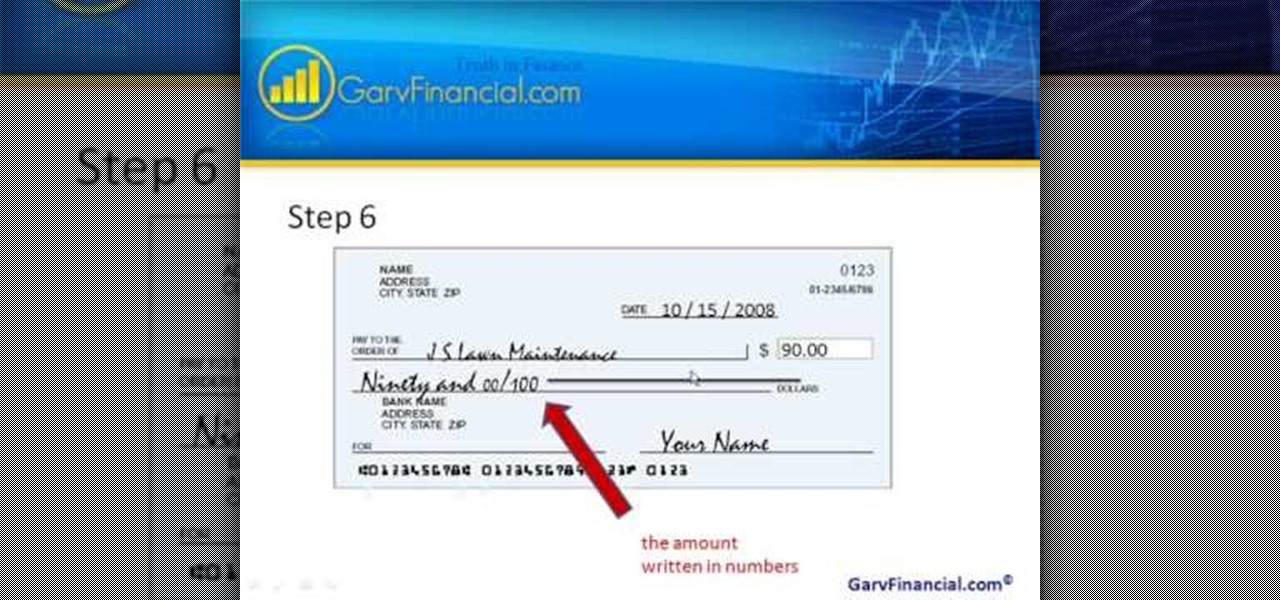
Here are step-by-step instructions on how to write a check. 1. Date the check, and ensure it is dated for the day you intend the recipient to cash it.

An invisible number controls your financial destiny. So until the revolution, you might as well learn how to raise your credit score.

Tax season is always stressful, especially for entrepreneurs and small business owners. Rather than wait until March to get your finances in order every year, learning how to keep track of your expenses is a valuable skill that saves you and your business time, money, and plenty of anxiety.

We all know how volatile the stock market is, especially during times of crisis. That does not mean that the market is impossible to gauge, however. Day traders are trained to read charts in order to recognize market trends and price patterns, giving them the insight they need to make their trades as profitable as possible.

This week's news that Magic Leap's patents had entered collateral limbo, now in the hands of JPMorgan Chase, threw a dark cloud over the company.

In the realm of internet security, it's becoming clear that augmented reality is not immune to the increasing wave data breaches plaguing users.

Investors continue to bet on augmented reality, both for short-term returns and long-term plays. This week, Niantic reportedly picked up another round of funding from Samsung and others, based on the success of PokémonGO and the prospects for future revenue. Likewise, investors see value in WaveOptics, whose waveguide displays could make consumer smaller AR smartglasses possible within the next year.

For younger children, a day at the playground is not complete without some sandbox time. Long a favorite of children and parents, sandboxes could also be sheltering dangerous pathogens.

Welcome back, my greenhorn hackers! The Holy Grail of any hacker is to develop a zero-day exploit—an exploit that has never been seen by antivirus (AV) and other software developers, as well as intrusion detection system (IDS) developers. In that way, you can exploit systems with your newly discovered vulnerability with impunity!

Welcome back, my greenhorn hackers! My preference for Linux as a hacking platform is well documented, and I have even created a series of tutorials to train new hackers. Without being proficient in Linux, you can't really call yourself a hacker.

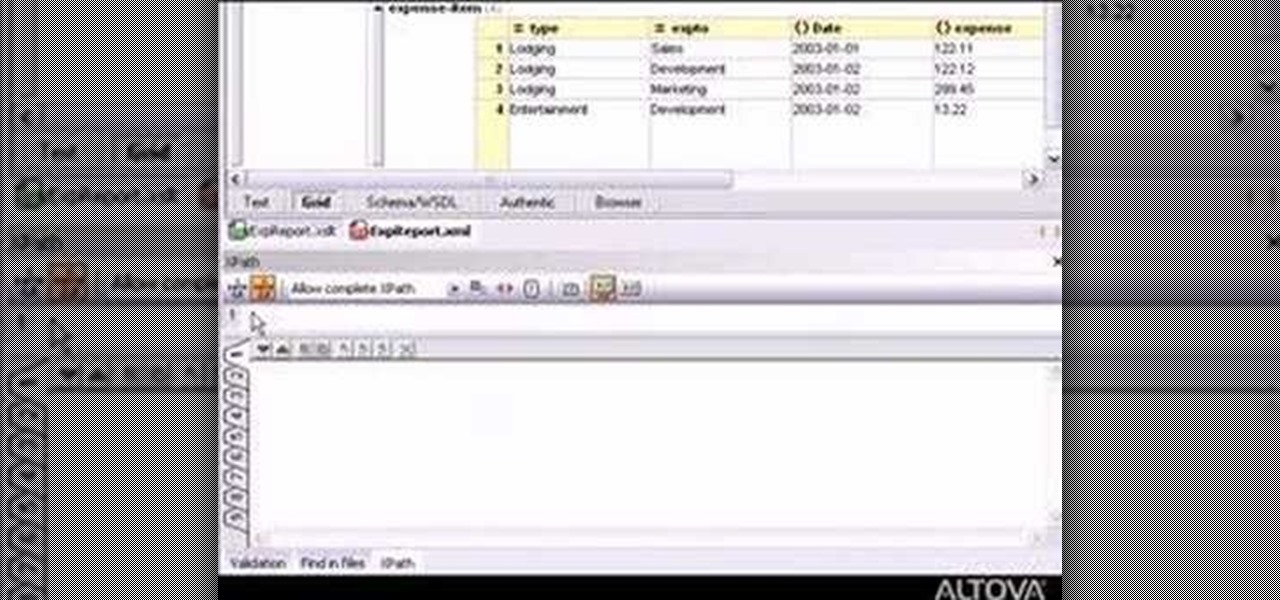
Desire to be an XML editor/programmer? This video will help you. You'll learn how to edit, analyze, and debug XPath expressions with XMLSpy.

Starting up a website can be daunting if you know nothing about web design or setup, but there are some tips to get the right people finding, looking, and returning to your site. A good landing page gives visitors exactly what they are looking for, and converts them from browsers to customers.

Whatever your reasons for doing it, if you are trying to hack passwords, it helps to have the right software for getting the job done. With the Cain and Abel program, you will be well on your way to hacking even the toughest personal passwords.

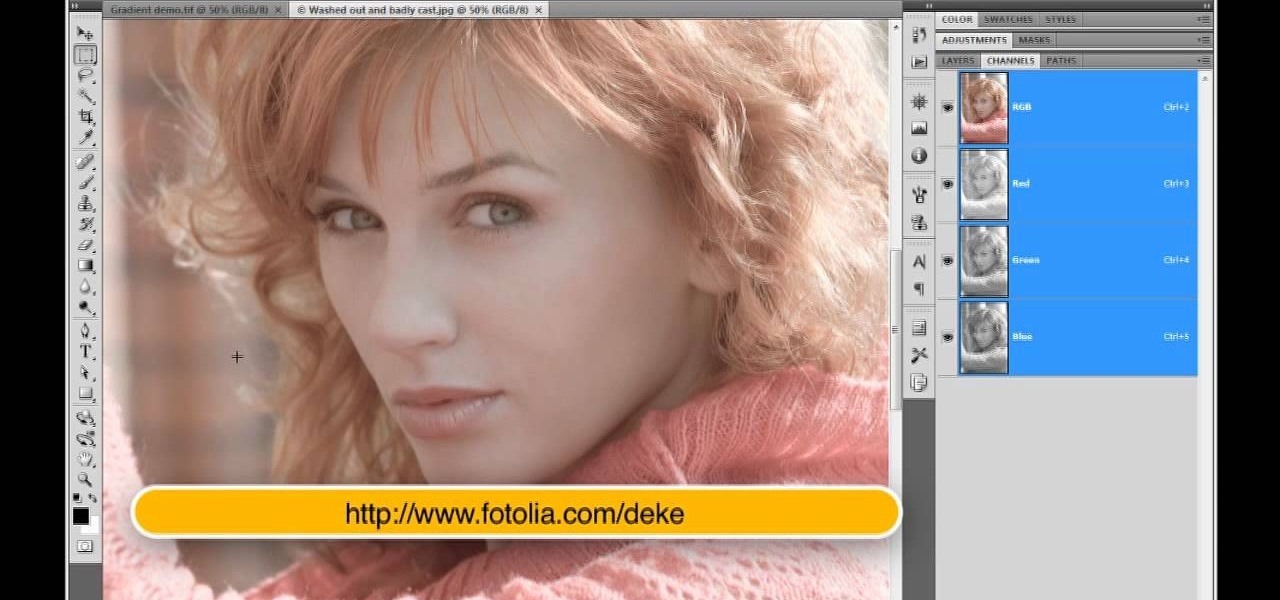
Deke McClelland explains what the Levels and Histogram commands can do in Photoshop in this video tutorial. Levels allows you to adjust the luminance levels allowing you to adjust the contrast and colors within each color channel of an image. Thus, Levels allows you to adjust the individual colors that can be found within a gradient. This command is very similar to the curves command but to a less powerful extent. It is also more efficient than the curves command. The Histogram is another col...