
News: US Military Shows Off Modified HoloLens 2 Augmented Reality System
New images reveal that Microsoft is already well underway in fulfilling its $480 million contract to provide augmented reality headsets to the US Army.


New images reveal that Microsoft is already well underway in fulfilling its $480 million contract to provide augmented reality headsets to the US Army.

Fast-casual burger restaurant Bareburger expects to soon replace all of its paper menus with 3D models of its burgers and other items rendered in augmented reality, but for now, the company is preparing some rather interesting limited AR interactions.

It's a given that if you're driving, you or someone you know has Waze as a go-to on their smartphone. The Google-owned crowdsourced navigation app is one of the best for avoiding traffic, roadblocks, and even cops.

What's up guys! It's time to discuss strings in more detail. Review
Hello! My name is An0nex. I am an ethical hacker who wants to share the art of hacking with all of you guys!

The months of constant snowfall and freezing temperatures seems endless once the excitement of the first snowfall fades, and you become weary of traversing black ice and other slippery streets.
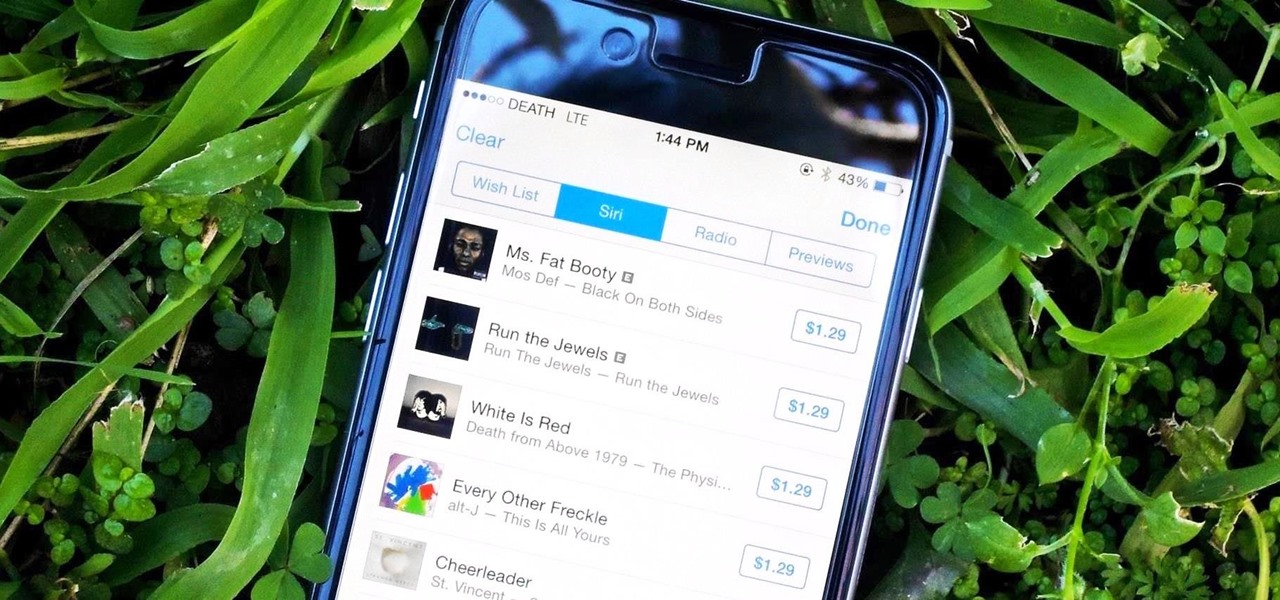
When you hear a song you like but can't quite catch enough of its lyrics, it can be nearly impossible to search for it online. That's where Shazam comes in. For the past decade, they've been making music easier for us to identify by analyzing a track's acoustic footprint, requiring only a few seconds of audio for accurate identification.
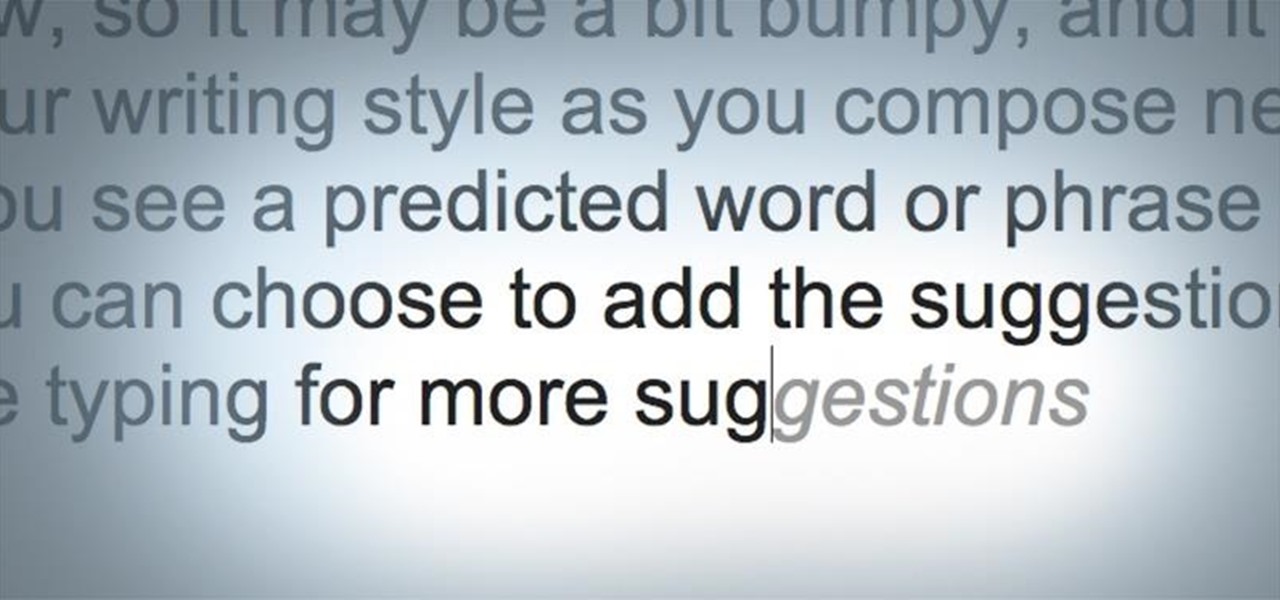
Android has had predictive text for a while now, both with stock and third-party keyboards such as Fleksy, SwiftKey, TouchPal, et al. Apple is even getting on board, with stock predictive text and third-party keyboards for iOS 8, slated for public release later this year.

Whether it's bad timing, or some trying-to-be-funny photobomber, it sucks having a photo ruined by someone or something getting in the way. While you can always retake the photo, it's simply impossible to capture the moment you intended, no matter how much restaging you do. But with an HTC One, there's no need to retake anything, as we have access to built-in features that will remove those photo intruders.

Let's just say it's been a pretty bad year for spies and government agencies and an even worse one for the privacy of U.S. citizens. Edward Snowden blew the lid off the NSA's spy program, and the FBI was recently discovered to have the ability to access your webcam any time they want—without triggering the "camera on" light. Yeah, that means those Justin Bieber lip sync videos you recorded weren't just for your private collection.

How much privacy are you getting as an AT&T customer? With the recent leaks confirming the National Security Agency's surveillance on AT&T users, and the ongoing trial of Jewel v. NSA, it seems not much at all.

Considering how easy and convenient Photoshop has become, even for the average computer user, it's nearly impossible to tell whether a photo is authentic, or if it's had some "improvements."
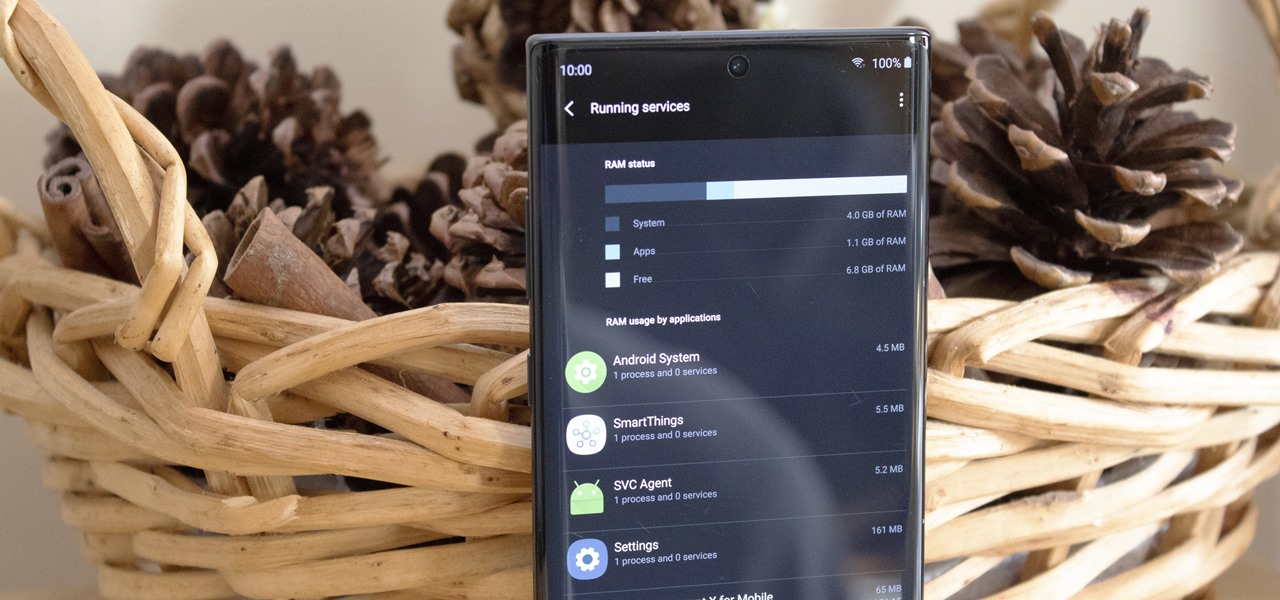
There are phones nowadays with 12 gigs of RAM, but they'll cost you well over a grand. The majority of Android devices have much less memory — I'd wager most have less than 4 GB. And with the system taking up around 2 GB, that leaves user-installed apps little room to breathe.
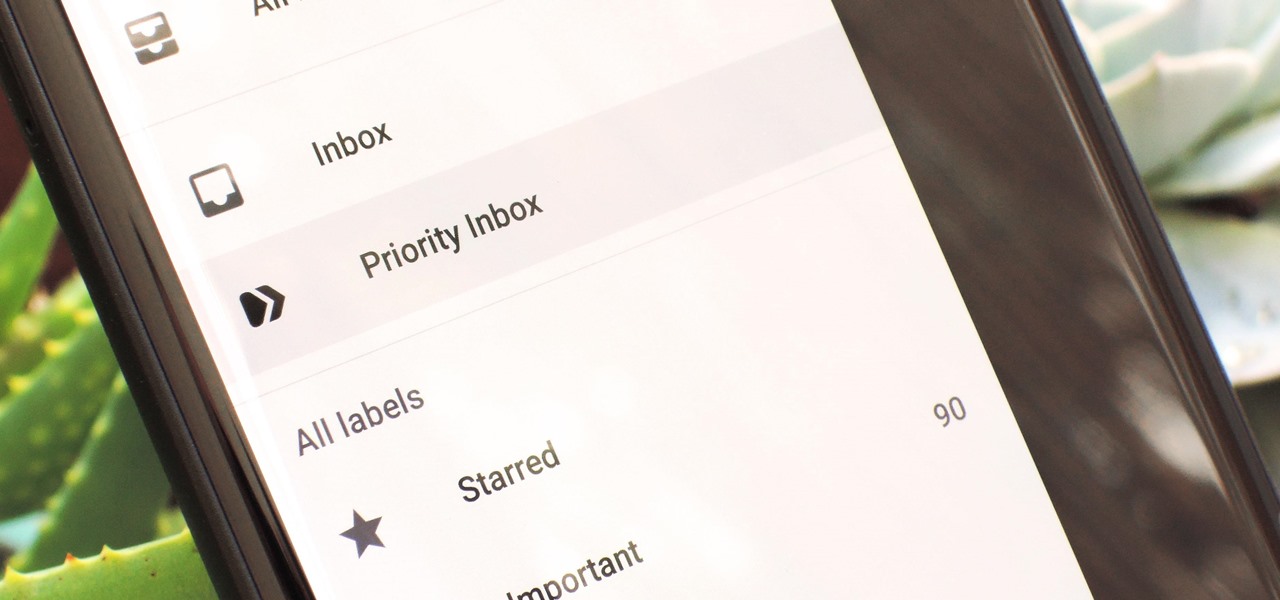
For many of us, getting to inbox zero is the highlight of our day. But if you used your email address to sign up for various sites and services, your inbox is probably cluttered with all sorts of spam, news letters, and unimportant emails. Thankfully, Gmail has a feature that can solve this by using machine learning.
In the first part of this series, we looked at the surface detection that is provided by the ARKit. We looked at how it worked and covered some of the tools that could help us determine what is not working; when it doesn't. Now let's take this to the next step.

Onshore, or on a boat, have you ever wondered what swims below in the dark water? Using standard equipment and a new process, marine scientists can now get a good look at what is swimming by—just by analyzing the water.

Uh oh. With millions of devices already sold, Apple's latest blunder is bound to upset the owners of some of their brand new iPhone 7 Plus phones.

In the last tutorial, we learned how to make functions and how they work on the high level. This time, we will take a peek under the hood again, stare deep into its soul and see its ugliness face to face to see how it works in the lower level.

Hi everyone! Last time we finished analyzing the assembly representation of our vulnerable piece of code (have I ever told you it is vulnerable?). This time we are going to introduce some fundaments about exploitation by demonstrating how to crash a program's execution. If that sounds lame, next time we will see how this crash can in fact be useful to control the program's execution, achieving remote code execution!

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Welcome back, my budding hackers! With this article, I am initiating a new series that so many of you have been asking for: Hacking Web Applications.

The season for outdoor activities and indoor heavy cleaning has arrived, and with that comes all the aches and pains of enjoying it. If you find yourself with sore muscles and no easy way to fix it, then a portable massager you can use whenever you're in pain is something that could put the spring back in your step.

Data analytics is crucial to the operations of any modern business these days. This trend is going to continue: in three years, 71% of global enterprises predict a rapid increase in data analytics.

Hacking web applications can sometimes be challenging due to the sheer amount of moving parts they possess. At the core of these apps are HTTP requests and parameters, but these things are often concealed from the user, due to security reasons, convenience, or both. However, a tool called Arjun can be used to discover hidden HTTP parameters in web apps.
It seems like all tech companies want to know where we are. Even Apple and Google have been caught abusing their location access on iOS and Android. Luckily, there are apps that can trick your phone into thinking it's somewhere it's not.

A virus easily spread among trout and salmon could make it harder to keep your favorite fish on the menu.

The Deepwater Horizon oil spill that began on April 20, 2010, was the largest maritime oil spill in history. Killing 11 people and discharging 4.1 million barrels of oil and natural gas into the Gulf of Mexico, the event was an unparalleled personal, environmental, and business disaster. It was also the first major oil spill to take place in the deep ocean.

The next-generation Audi A8 to launch in July is expected to be the world's first Level 3-capable production car to go on sale in retail channels.

Even as health authorities describe the symptoms of Zika infection in the general population as mild, a new surveillance study finds serious side effects are more common, and serious, than previously thought.

A robust appetite for imported foods is leading to increased disease outbreak in the US. Despite the locovore and slow food movements, America's demand for foreign foods is picking up. According to a study published in the journal of Emerging Infectious Diseases, demand for imported fresh fruits, vegetables, and seafoods has jumped in recent years.

Marijuana is legal to use for medical purposes in 28 states and the District of Columbia, but the quick development of this new industry could have left some regulation issues in the lurch.

Disengagement report numbers for self-driving car testing in 2016 on public roads in California were just released, and the biggest point we can make about them is that Waymo is very far ahead of their competitors in almost every metric.

Despite the availability of a vaccine against it, almost 50% of men aged 18-59 in the US are infected with the human papillomavirus (HPV). Why?
Starting in October, many Nexus 6P users have been experiencing a bug that causes their phone to completely shut down, even though there was 20% or more battery life remaining. At first, it was thought to be a direct result of the recent Android Nougat update, but a combination of factors indicate that this isn't necessarily the case—or, at least, it's not the only problem.

In Pokémon GO, having an in-depth understanding of your Pokémon's stats and abilities is crucially important to becoming a better player. Not all Pokémon are created equal; as such, it's critical that you look at each of your Pokémon—even duplicates—with a keen eye.

Welcome back, my rookie hackers! The Golden Fleece of hackers is to develop a zero-day exploit, an exploit that has not been seen by antivirus (AV) software or and intrusion detection system (IDS). A zero-day exploit is capable of skating right past these defenses as they do not contain a signature or another way of detecting them.

Welcome back, my budding hackers! One of the most basic skills the forensic investigator must master is the acquisition of data in a forensically sound manner. If data is not captured in a forensically sound manner, it may not be admissible in court. In my Kali Forensics series, I showed you how to acquire a forensically sound, bit-by-bit image of a storage device such as a hard drive or flash drive, but now let's dive into live memory.

The Google Now on Tap feature puts the power of Google Search inside each and every application on your Marshmallow-powered device, allowing you to retrieve contextual results based on the content on your screen.

Macs are generally highly power efficient due to, in part, the optimized sleeping schedule with OS X. Yet in certain scenarios, you might not want your Mac to go to sleep: downloading a huge file, reading a book, reviewing a spreadsheet, analyzing some content on the screen... the list goes on. To resolve this, you can go to System Preferences and mess with the settings, but this can be an annoying process if you need to do it often.

Welcome back, my aspiring hackers! In this series, we continue to examine digital forensics, both to develop your skills as a forensic investigator and to avoid the pitfalls of being tracked by a forensic investigator.