In just a few weeks, on May 29, the annual AWE (Augmented World Expo) conference will take place once again in Silicon Valley (Santa Clara, California, to be exact).

While keeping your iPhone out of the bedroom might help to avoid unnecessary distractions before bedtime, it could be better served right by your side to help diagnose sleeping issues you may be experiencing each night.

Around this time in 2016, the predictions for the next year had reached something of a consensus: 2017 would be the year of augmented reality. But a funny thing happened on the way to the future — nothing much, really. At least not for the first half of the year.

Step 1: What Exploit Development Is and Why Should I Be Interested on About This Topic
Welcome back Hackers\Newbies!

Hackers are always seeking zero-day exploits that can successfully bypass Windows 10's security features. There has been extensive research into creating undetectable malware and entire GitHub projects dedicated to automating the creation of undetectable payloads such as WinPayloads, Veil v3, and TheFatRat.

Web applications are becoming more and more popular, replacing traditional desktop programs at an accelerated rate. With all these new apps out on the web comes various security implications associated with being connected to the internet where anyone can poke and prod at them. One of the simplest, yet the most prevalent types of security flaws found in modern web apps are SQL injections.

No more carrying around heavy laptops and thousands of Linux Live CDs and USBs to always be ready for pentesting on the fly!

Although the Clock app in iOS has undergone some design changes over the years, you still can't set more than one timer on your iPhone. Oddly enough, Apple's own HomePod speaker added this feature, mimicking the timer on Amazon's popular Echo smart speakers. Fortunately, through Apple's Shortcuts app, there's a clever hack to set multiple timers — without using a third-party timer app.

It can be very frustrating: You open your Messages app, send an iMessage, and then see that dreaded red exclamation point or horrible green SMS bubble. At this point, you may be curious whether it's just your iPhone or whether iMessage is broken for everyone, but how do you find out?

With the holidays right around the corner, it's easy to miss a big software update on your iPhone, and by that, I mean iOS 15.2, which was pushed out Monday, Dec. 13. There's a surprising amount of new features and changes in the updated firmware, and there are a few big ones you need to know about.

Apple's iOS 13 has been available for beta testing since June, and the stable release pushed out to everyone on Thursday, Sept. 19. To help you make the most out of iOS 13 for iPhone, we've rounded up everything you'll want to know, whether a colossal feature, small settings change, interface update, or hidden improvement.

You've protected your Ubuntu system from physical attacks, annoyed network hackers, and sandboxed potentially malicious applications. Great! Now, the next logical steps to locking down your OS include thoroughly auditing Ubuntu for weak points, using antivirus software that respects your privacy, and monitoring system logs like a boss.

In these videos, you can see how 3 minute chess blitz games are for the greats, because if you're a beginner, you spend too much time analyzing the moves, when they should come almost as second nature. See some common follies in rushed games, and see some good defenses, here and there.

Revealed! The secret to learning a language quickly. It's a little known technique diplomats and royalty have used for centuries. I lucked up on it by analyzing how I could quickly boost my language and workforce marketability. You get it here by design.

Having a website people can easily navigate is common sense. It can save taxpayer dollars & help your agency achieve its mission. Here's how to dramatically improve your website by focusing on your customers' needs & adopting some basic usability techniques.
Dimensional analysis is the process of analyzing units to decide which conversion factors to use. You can use this in real life if you want to figure your gas mileage. Here is a link to a website to help you Dimensional Analysis definitions | Quizlet.

We've all heard of the power that red wine holds. It can help lower risks of heart disease, boost your brain power, and can even recharge your car battery. But last year, a group of Japanese physicists made headlines when they announced that they could induce superconductivity by soaking metals in red wine. But why red wine?

I love books almost as much for their book covers as I do their actual books. A well-designed book cover matches the intent and spirit of the story, and can often enhance the experience of reading it.

Another great Community Byte in the bag! This week was really cool, especially with programming going on twice a week. We transitioned to the new times very smoothly with no one left behind, from what I can tell.

Here at Null Byte, we've spoken a lot about securing and anonymizing traffic. This is a big deal. With all of today's business taking place electronically via computers, we need to be secure when on-the-go. A lot of businesses don't even train their employees to secure their computers to protect from various threats. Here are a few things that should always happen when doing business on computers:

There are over 250,000 apps in the Android Market, ranging from free productivity programs to a ridiculous $200 for a vuvuzela horn effect. But chances are you don't have the vuvuzela app on your Android smartphones right now, but you are likely to have one of the ten most popular apps in the Android Market.

What Is Dimensional Analysis? Dimensional analysis is used to convert units. It's the process of analyzing units to decide which conversion factor to use. It's used by multiplying units by conversion factors, rates equal to 1.

Since the launch of Edit on a Dime several weeks ago, I’ve been putting a variety of automatic video editing apps though their paces. One of the first tested was Magisto, a web-based app that’s directly accessed through YouTube, which I enjoyed, but found some obvious problems with. Since then, I’ve been in contact with Oren Boiman, CEO and founder of Magisto, who was kind enough to address my concerns.

You're walking down the street, minding your own business. Then you see it—a large, bright fireball in the near distance. A tremendous heat wave speeds towards you at one thousand miles an hour, and before you can think, before you can even blink, the extremely heated wind pushes right through you. Your skin melts, your eyes liquefy—your face disappears into the wind. Before you know it, your pancreas collide with what’s left of the person next to you, your duodenum is dissolving faster than ...
Microsoft SharePoint is a business management system introduced by MICROSOFT. It has many build in functions to work in web based environment easily. Microsoft SharePoint 2010 is released on April 17, 2010. It is introduced with the promise of better performance than its predecessor version for both developers and IT professionals. It is entitled as “Business Collaboration Platform for the Enterprise and The Web”.

When your computer first connects to a nework, it sends out a request on the network to lease an IP from the router. The router then leases your computer an unused IP address, which is used as a unique routing address for sending traffic that is meant for you, to you. As everything tends to, this method has its flaws.

Sounds like a false promise à la infomercial or typical spammy web headline—how can a 4.8 ounce gadget aid in weight loss? But, in truth, "who" better to act as a dedicated personal trainer and nutritionalist than the iPhone? The smartphone is completely and utterly tethered to the daily life of the average middle to upper class American. It's reliable and exact. All it needs is a charged battery, the right app, and of course, as with every diet and fitness regime, a user with unwavering self...

Wireless networks. Nowadays, everyone uses 'em, but most don't secure 'em. On average, I can drive up and down any block in my city and find at least one or two open or semi-open networks on any given day. With some changed MAC addresses for good measure, an attacker can use your network as a spring board for who knows what. When the police come a few days after, they are coming to your door—and not to talk about how nice your lawn is. Don't be that guy.
Sergio Peralta Advisor: Jessica Davis

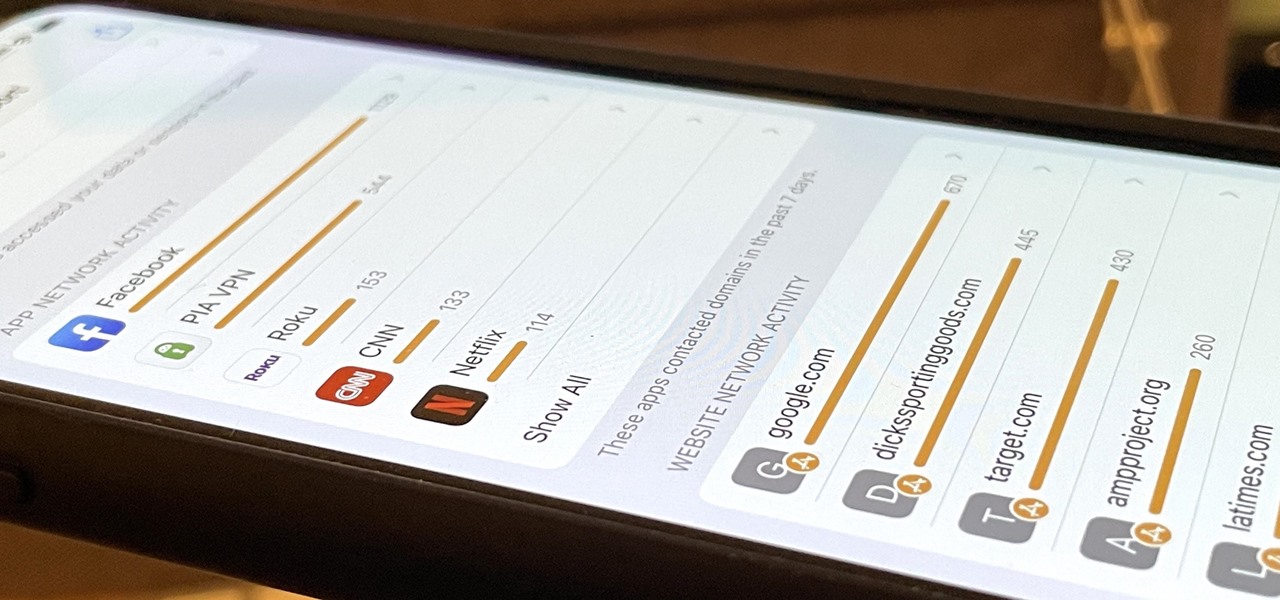
Anonymity is something that doesn't exist today. Everything you do in the world is tracked, from the purchases you make to surfing the internet—even taking pictures on your iPhone. Everything you have ever said and done on the internet is still there—somewhere. This is called caching. For example, when a site is down, you can view its cached page on Google.