Caller ID is great to have, but there are certain situations where you don't want the person you're calling to have your number. People who sometimes use their personal phones for work may not want clients knowing where to reach them outside of work, and anytime you're dealing with Craigslist, it's better to be safe than sorry.

This week, Silk Road was shut down for good when the FBI seized the anonymous online marketplace after Ross Ulbricht, aka Dread Pirate Roberts, was arrested. This comes just two weeks after another illegal marketplace called Atlantis shutdown. However, there are plenty of other black markets hiding within the Deep Web, freely and anonymously accessible using the Tor browser.
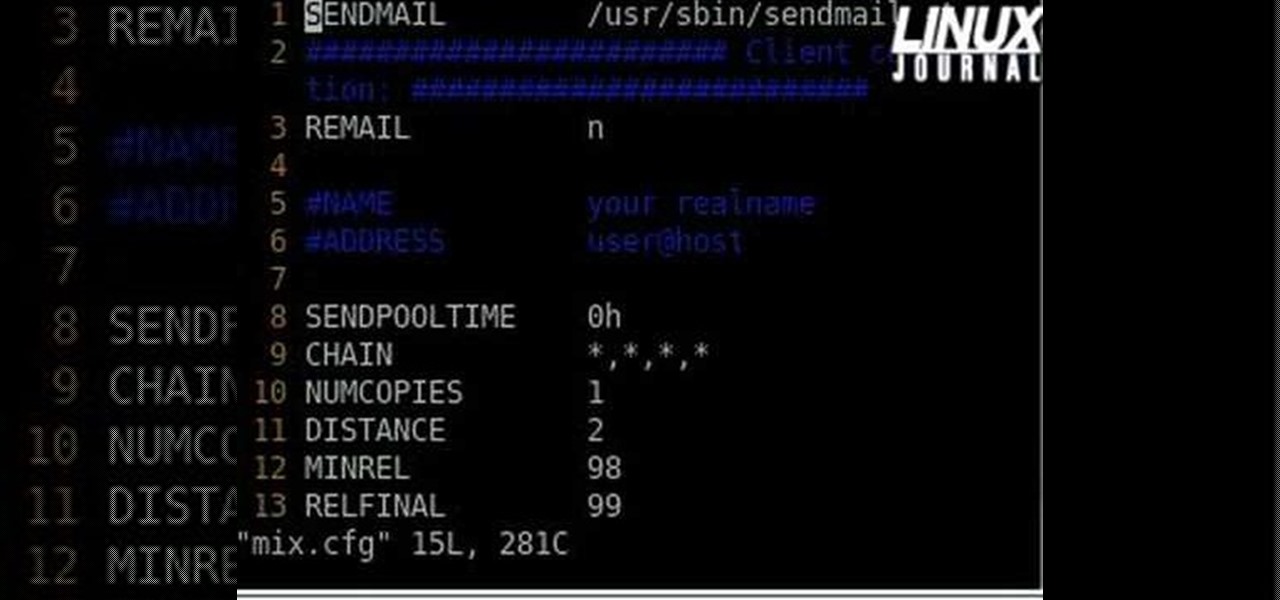
Email is one of the least private and least secure forms of communication, although few people realize this. MixMaster is one way to allow secure, anonymous communication even over the very public medium of email. This tutorial will get you started with MixMaster quickly and easily.
PirateBox is a great way to communicate with others nearby when cellular and Wi-Fi networks aren't available. With it, you can anonymously share any kind of media or document and even talk to one another by voice — without being online. However, it needs a Raspberry Pi, which is more expensive than ESP32 boards, and if you only need a text-based chat, there's a much simpler option.

Just days after news spread that Snapchat could be exploited by spammers, an anonymous group of hackers have released the private information of over 4 million users of the popular photo-sharing application.

We all know them, and many of us despize them. And some might support them, regardless many have different opinions.

A long time ago, we recommended the Hover Zoom extension for Chrome as an easy way to blow up small image thumbnails without actually have to "click" on the images themselves. Over the past year, there have been reports that Hover Zoom now collects and sells your browsing data to third-party advertisers without your consent.

There's actually more to the dialer screen on your OnePlus than meets the eye. Besides its obvious purpose of calling people, there's a vast array of secret codes that you can input to troubleshoot your device, in addition to revealing important information, making anonymous phone calls, and so much more.

With Gboard, Google created a keyboard with more functionality than just inputting words. The app includes features such as GIF search and live text translation, but it gets even better when you let it learn more about you. With this data, Gboard grows from a good keyboard to one that can complete your sentences.

In recent weeks, some people have been shunned from the Null Byte community because they expressed "black hat" aspirations. This is because Null Byte is the "white hat" hacker training/playground. Although most of us think we know what that means, it does beg the question; "Who and what is a white hat hacker?"

Welcome back, my tenderfoot hackers! Well, the first season of Mr. Robot just ended and Elliot and fsociety successfully took down Evil Corp! They have effectively destroyed over 70% of the world's consumer and student debt! Free at last! Free at last! Of course, global financial markets crashed as well, but that's another story.

Tor is an excellent obfuscation network for web traffic, and while instant messaging over the network is very useful, it can be relatively difficult to configure. In this guide, we'll look at two synchronous communications platforms (instant messengers) which can be routed over the Tor network, Ricochet and XMPP.

Hacking from a host machine without any form of proxying is reckless for a hacker, and in a penetration test, could lead to an important IP address becoming quickly blacklisted by the target. By routing all traffic over Tor and reducing the threat of malicious entrance and exit nodes with a VPN, we can configure Kali to become thoroughly private and anonymous.

In the first part of this series, we took a factual and technical look at the history of the Internet. I explained how all of these wires and servers got here in the first place. Obviously, a firm did not just create and build the Internet around 1995! Now that we know how the Internet came to be, we can get into the really fun stuff—what the Internet looks like now! Well, that's not quite the network design I was talking about, but it does show what the Internet looked like back in 2007 befo...

School internet filters serve a valid purpose—they keep students from wandering off into the deep corners of the web while still allowing at least some internet access. But a lot of these restrictions are completely ridiculous, to the point where some school districts block access to the educational material in National Geographic or forbid searching terms like "China," "Iran," or "Russia"—because, you know, breasts and commies.

This is my first tutorial on this website. So, if you think anything to be wrong, just place it in the comments.

Apple's latest updates to its operating systems add another security feature to its Find My service, so you have an even better chance at locating your lost iPhone, iPad, or Mac should it ever happen. As long as you have the option enabled, you can leverage other Apple users' devices to find yours on the map.

WonderHowTo is a how-to website made up of niche communities called Worlds, with topics ranging from Minecraft to science experiments to Scrabble and everything in-between. Check in every Wednesday evening for a roundup of user-run activities and how-to projects from the communities. But don't wait—start submitting your own projects to the most appropriate World now!

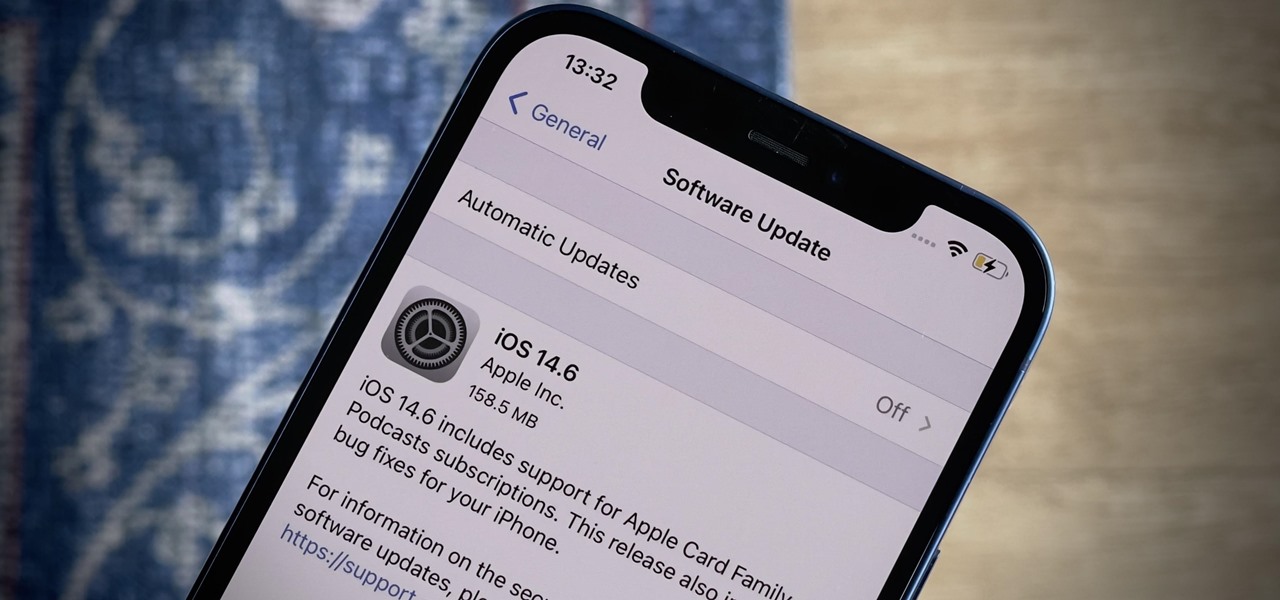
Apple released the latest version of its iPhone OS, iOS 14.6, today, Monday, May 24. This latest update (build number 18F72) introduces new features like unlocking your iPhone with Voice Control after a restart, Apple Card Family support for up to five people, and subscription support for shows in Podcasts.

As fun as Twitter is, it can also quickly turn scary. Anonymous, aggressive, and troll accounts can attack you for your tweets and stalk your every move. While you could make your profile private and block users, there are lesser-known privacy and security features that you can switch to improve your safety online.

When it comes to digital security, one of the best ways to protect yourself is to use two-factor authentication. Most apps these days support it, including Facebook, a site where the more privacy you can muster, the better. However, of the two 2FA options available for Facebook, only one should be used as the other will share your phone number with the world, a huge privacy concern.

Throwaway phones aren't just for seedy criminals and spies—they can be useful for many everyday situations.
As a hacker or an aspiring one, You need to be careful and anonymous if your doing anything illegal. But you slipped up. Now someone is tracking you! Well luckily you read this post ahead of time and have a backup plan!

You might have missed it, but the virtual keypad you use to enter phone numbers in your smartphone's dialer and contacts app isn't all numbers. Take a closer look, and you'll notice a few mysterious buttons you've likely been tuning out unconsciously. But it's time to stop ignoring them because each has a particular purpose that could come in handy one day.

Outside of iPhone releases, software updates are arguably the most exciting aspects of iOS life. It's like Christmas morning when your iPhone installs an update, as you dive through your device to find all the new features and changes Apple thought to include. With iOS 14.4, there are at least 10 such new additions just waiting for you to explore.

The term "hacker" often has negative associations attached to it, yet the world is in dire need of professionals with hacking skills. White hat hackers are ethical computer hackers that use their hacking skills to pinpoint network vulnerabilities and patch them up before they can be exploited by the bad guys.

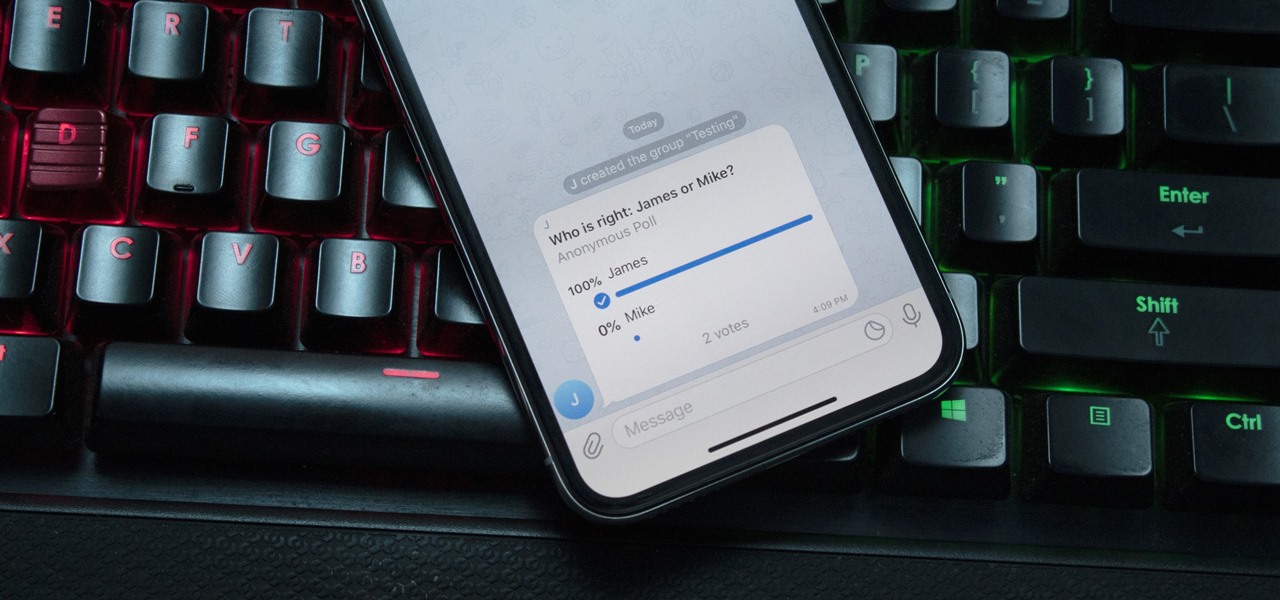
With group chats, arguments tend to devolve from a dispute between two people to a giant debate amongst all members. But before things get out of control, Telegram has a feature that can help.

Hackers often find fascinating files in the most ordinary of places, one of those being FTP servers. Sometimes, luck will prevail, and anonymous logins will be enabled, meaning anyone can just log in. But more often than not, a valid username and password will be required. But there are several methods to brute-force FTP credentials and gain server access.

Facebook is where a lot of people get their news. The problem, though? Your Facebook feed gets jumbled with random post times, which isn't useful for keeping up with new stories in real-time.

We've all seen the login pages that allow you to log in to third-party accounts using your credentials from Facebook, Google, or Twitter. It saves you the trouble of creating another account and remembering more passwords — but it can also become a privacy and security issue, which is why Apple created the "Sign in with Apple" feature for iOS 13.

While the betting lines on iPhones with depth-sensing, rear-facing cameras in 2019 have already been established, a new report adds some certainty to the notion that the iPhone will get new AR superpowers later this year.

There's a lot more to your iPhone's dialer screen than just entering phone numbers and hitting the green call button. It's not very obvious, but there are secret codes that you can enter on the dialer to find out information about your device, help troubleshoot issues, and mask outgoing calls, to name just a few things.

Intel Corp.'s augmented reality division could ship consumer-focused smartglasses before the end of the year, according to reports.

The developers at Immersion VR are clearly fans of both Apple's ARKit and Rick & Morty, as the company has shared its second demo in as many weeks of the augmented reality platform that is influenced by the animated sci-fi series.

iCloud can occasionally be the worst part of being an Apple user. It's useful for backing up your information, however, sometimes the problems that stem from Apple's cloud service are so tremendously frustrating they almost seem intentional. Well, buckle in, because it's possible there may be a widespread login issue.

Apple is working on autonomous systems for vehicles, which could then be implemented with the help of car manufacturers.

If you just installed the iOS 11 beta on your iPhone, you're automatically sending your location data to Apple — even if you don't want to. Luckily, there's an easy way to prevent Apple from seeing this data if you don't want them to.

When it comes to social media, Google has had it a bit rough. But its next big app in this category is apparently steps away from completion, with a platform that allows small groups of users to edit and organize photos in unison.

Opera's web browser for Android, Opera Mini, now comes with integrated ad-blocking technology for a less cluttered browsing experience. More importantly, it decreases the amount of data being loaded, which Opera claims increases webpage loading times by 40 percent. This is in addition to the 90 percent data reduction from Opera Mini's compression technology.

It's looking more and more likely that rumors stating that the iPhone 7 will not include a 3.5 mm headphone jack are true. Chinese websites Wei Feng and Anzhuo.cn reported that anonymous sources on the supply chain confirmed that the controversial design choice is a reality.