Many people deal with motion sickness on a daily basis, and if you're reading this, chances are you're one of them. Kinetosis can make your stomach roll, your entire body sweat, and make you feel fatigued and dizzy at even the slightest movement, whether it's related to carsickness, seasickness, or airsickness. And let's not forget the worst part—vomiting.

So, we all probably know that when you run a trojan made by Metasploit, nothing will appear to happen. This is a sign for me to immediately check my Task Manager, but for an unsuspecting victim, it will just seem like a broken file. It is likely that they will delete this "broken file" once they see that it "doesn't work." In order to prevent this, we need to disguise the trojan.

With each day that dawns, there is a new, major hack that makes the news headlines. If you are paying attention, there are usually numerous hacks each day and far more that never make the news or are kept private by the victims. Every so often, a hack is so important that I feel compelled to comment on it here to help us learn something about the nature of hacking and IT security. This is one of those cases. Last week, the U.S. Office of Personnel Management (OPM) revealed that they had been ...

Sriracha has quickly become one of the country's most universally loved condiments. The addictive and affordable chili sauce seemingly goes on anything, and with anything, and never seems to get old. To wit: when I studied abroad, all of our food was boring, pre-packaged Sysco shipments; for three months, I smothered every breakfast, lunch, and dinner with Sriracha. And after all of that, I still eat it almost religiously.

Coconut oil must be sent from the gods themselves, because this stuff is made of miracles. If you ever wondered why your mother always has it around, it's because she's smart enough to know the countless uses for it.

Cheese might be one of the most satisfying snacks around, whether you prefer a slice of snappy Irish cheddar or a creamy, rich portion of Brie. It's been called "dairy crack" by a respected physician and for good reason: eating cheese produces casomorphins, which effect the human body like opiates. It also contains trace amounts of actual morphine.

There are certain foods and beverages that can actually brighten your smile or improve your dental health when you chew or sip them. Once you understand their chemical properties or textures, you can look to items you already have in your cupboards or refrigerator to help keep your teeth looking and feeling their best.

Believe it or not, you can put your money to use very efficiently in a new way: your credit or debit card can serve as a blade in desperate situations. (It might even be handier than dental floss as a brilliant substitution for specialized kitchen tools.) While I wouldn't take bets on it slicing a New York strip steak, there are definitely many other foods it will easily slice through. What Is It Made Of?

A few years ago I went hog-wild trying to achieve a zero-waste lifestyle. I didn't succeed, but the experiment taught me that we throw away things we could—and should—be using more.

Minor mishaps occur all the time in the kitchen, whether you cut your finger while dicing an onion, scorched your hand in a grease fire, or burned the roof of your mouth because you were to eager to taste-test your killer pasta sauce.

The Xposed Framework offers many great customization options for your Galaxy S5. S Health, with its ability to read your heart rate through a built-in monitor, is one of the main selling points of the GS5. Trouble is, the two don't seem to play nice together.

It's a small but very real frustration: you want a chilled drink, but you open the freezer only to see nothing but empty ice trays. Fortunately, there's a simple way to make ice cubes quickly—use hot water. Yup, you read that correctly. Hot water freezes more rapidly than cold.

When it's most important for me to browse the web incognito, I always seem to forget to enable private browsing. If that sounds like you, it's time you stop making that mistake for good. Manually deleting the cache and browser history is a thing of the past, and as it turns out, so is manually switching to incognito mode.

Google has finally announced the newest flavor of its mobile OS, Android L (Lollipop?), and I couldn't be more excited. While we won't see its official release until the fall, there are still some features we can get our hands on right now.

Back in August, Google introduced Android Device Manager. This new service allowed you to locate, lock, or wipe a lost or stolen Android device from either a companion app or a web interface. Effectively, this is the "kill switch" that legislators are clamoring for.

Having a dust- and water-resistant phone is truly useful, but it comes with a price. In order to achieve this functionality, Samsung had to literally plug up any holes in the Galaxy S5, and this included the charging port.

Sony has been hard at work refining its Xperia line of flagship phones. With a 6-month release cycle, they've managed to slim bezels, increase viewing angles, and boost processing power in the 1.5-year span between the original Xperia Z and the Z2.

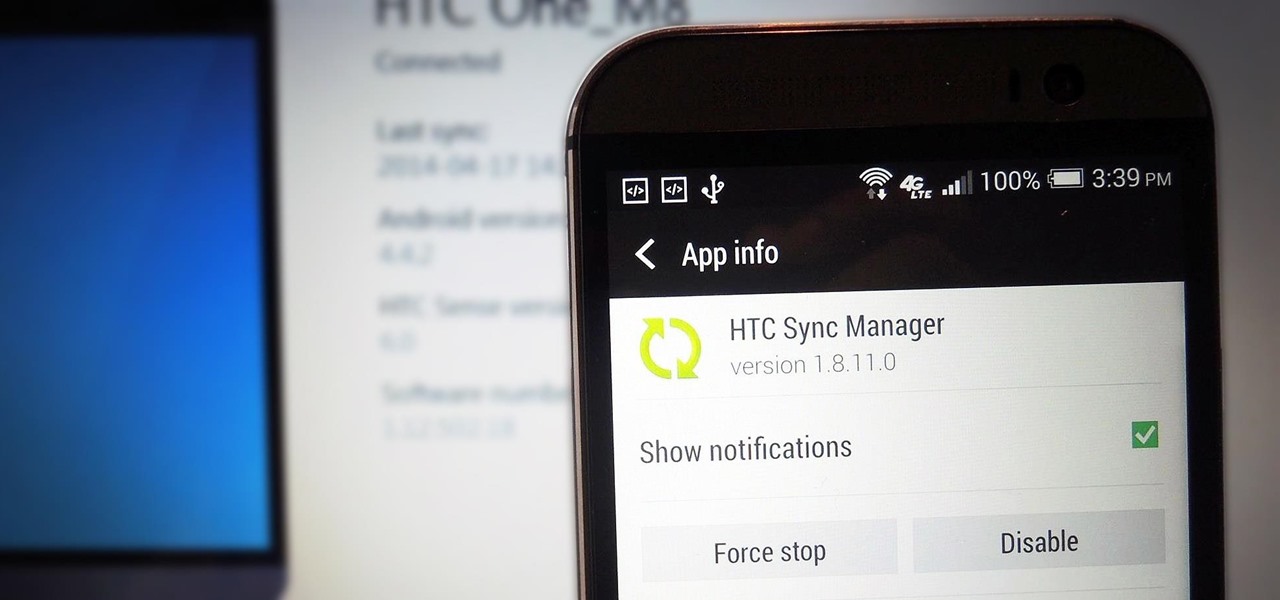
If you've just upgraded to an HTC One M8, chances are you've got some media files you want transferred over from your computer or previous phone. Even after you've done that, there will be times when you want to transfer content back to your computer for safe keeping.

Welcome back, my hacker novitiates! Recently, I demonstrated a hack where you could redirect traffic intended for one site, such as bankofamerica.com, to your fake website. Of course, to really make this work, you would need to make a replica of the site you were spoofing, or better yet, you could simply simply make a copy of the original site and host it on your own server!

Nokia's recent foray into the world of Android brought a plethora of goodies along with it. The Finnish smartphone manufacturer offers a slightly different take on our favorite mobile operating system, with customizations ranging from ringtones to its very own app store.

Currently, all Nexus tablets running Jelly Bean or higher can enjoy multiple user accounts. With tablets often migrating between various people in the same household, there’s no reason for Dad’s finances to mingle with little Tammy’s candy crushing. Multiple users, each with separate profiles, just makes sense on an Android tablet.

Welcome back, my rookie hackers! A short while back, I began a new series on database hacking, and now it's time to continue and extend your education in that field. As you know, the database contains all of the most valuable info for the hacker, including personally identifiable information, credit card numbers, intellectual property, etc. So, it's the ultimate goal of cybercrime and the APT hacker.

One of the biggest problems in data security is authentication of data and its source. How can Alice be certain that the executable in her inbox is from the venerable Bob, and not from the not-so-venerable Oscar? Clearly Alice wants to know because if this file is actually sent to her by Oscar, the file might not be a game, but a trojan that can do anything on her computer such as sift through her email and passwords, upload her honeymoon pictures, or even turn on microphones and webcams. Thi...

When it comes to the user interface, you're pretty much limited to the stock one that comes on your Samsung Galaxy Gear smartwatch—a carousel of large black and white icons representing the features and applications on the watch.

With the Samsung Galaxy Gear smartwatch only several weeks old, the extent as to what you can do with it is limited since there are only about 70 apps in the Gear Store right now, and a lot of those need the full app installed on your Samsung Galaxy Note 3 in order to function properly.

The NSA's massive internet spying efforts will continue. In President Obama's latest press conference, he went public to (in so many words) say that the NSA's spying efforts will continue uninterrupted. This, coming just weeks after the Amash Amendment which would have defunded the program, was narrowly defeated in the House (you can check if your congressmen voted against it here).

Welcome back, my budding hackers! Previous to this tutorial, we've focused mostly on hacking the target system. If we're successful in owning the target system, we'll then want to make certain that the system administrator doesn't know we were there, and that he or she cannot track us.

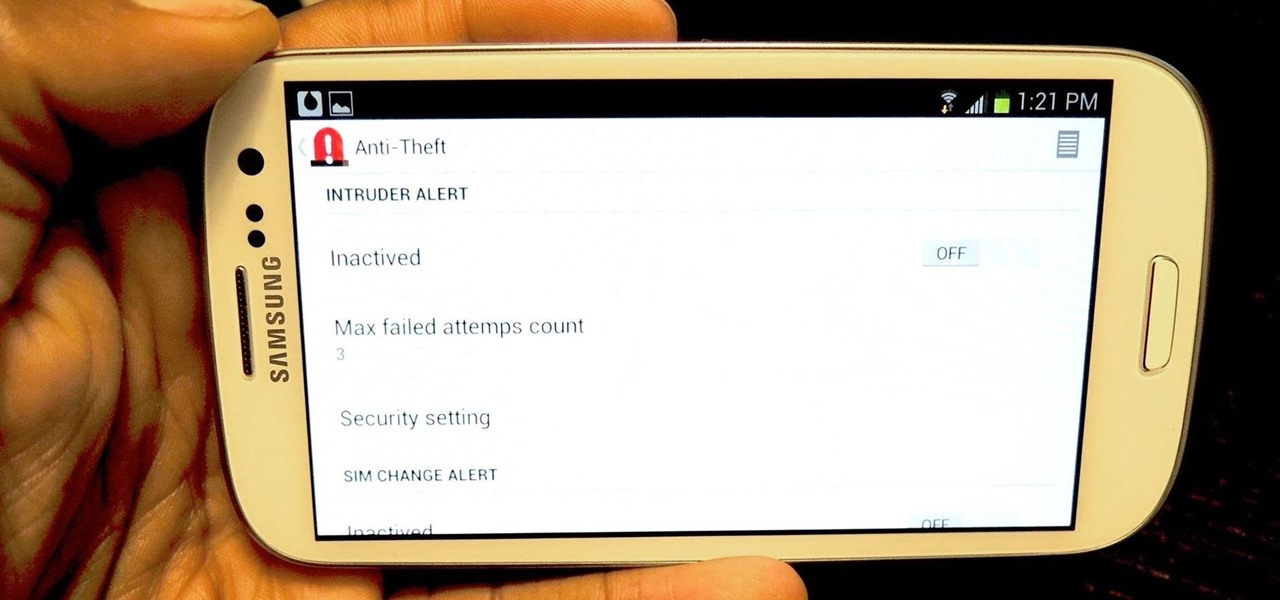
I love surprises. Surprise parties, surprise visits, surprise Patrick... But there are times when a surprise is the last thing you want, like reaching into your pocket to find that your Samsung Galaxy S3 is not where it should be.

The big fireworks day is almost here, but most of you are limited in what you can do when it comes to celebrating the Fourth of July with a bang. Unless you live in a dry area prone to wildfires, one type of fireworks you can probably still legally buy are sparklers.

This summer's going to be a hot one, so skip the water pistol this year and break out the big guns! In this project, I'll be showing you how to build a water balloon shotgun—a high-powered water balloon launcher that's capable of firing 17 water balloons at the same time!

Welcome back, my novice hackers! Most of my tutorials up until this point have addressed how to exploit a target assuming that we already know some basic information about their system. These include their IP address, operating system, open ports, services running, and so on.

For this project, I sacrificed some of my kids' clothes and a can of tuna to make some high-quality fire starter! Here's how to make a great batch of char cloth to add to your emergency survival kit.

People take their Black Friday shopping seriously. Some of them are even willing to fight over it. Every year the stories get crazier and crazier, and someone always gets hurt (or even killed).

Buid a facke house on some property (make it look real nice from the outside)Have fake pictures of the inside and make it a real cheap price so some guy buys it, When he' at the houe tell him an inspection is happening on the house so he can't go in at the moment (have some people look like there working on the house from a distance) at a certain point have someone radio in that there's a problem and everyone needs to get out and away from the house, when everyone is past the safe point blow ...

Move over NASA— SpaceX is taking over. Well, not really. But today, the privately funded spacecraft company broke all expectations when their Dragon capsule fell to a soft landing in the Pacific Ocean, completing an undoubtedly successful demo flight of nearly two full trips around Earth. It was the first re-entry of a commercial spacecraft ever, bringing commercial space transportation closer to reality.

Are you tired of counting your hair while waiting for your computer or laptop to respond? Then, these easy steps are perfectly fit for you, especially if you're a Windows 7 user.

Make sure your next apartment rental goes smoothly by properly checking the property before signing a contract. This way you will avoid unexpected disappointments or problems that you were not aware off. Moving is hard enough, give yourself all the advantage you can by going in prepared.

Tracy Richards specializes in the ingenue, and you will see all her tips here. Tracy shows you her pro makeup kit, how to use proper skin care under makeup, how to apply moisturizer, anti-shine, neutral set powder, and foundation. She also shows you her brushes and when to use different styles during the process.

On June 23, 2003, Linden labs created a free client program known as Second Life. This program allows users, or residents, to interact with each other in a virtual world by using avatars. Thanks to this program, residents are able to explore, socialize, and create and trade virtual property, and services with each other. Second Life has become one of the most popular programs used by various age ranges from 16 to 60, but how do you enter this world and get your own avatar?

This article will teach you how to make an error similar to this one (also by me). This error message though, is a yes or no question. Clicking yes and no will give different results. Like the previous error message, this is 100% harmless.