While a viable version of consumer-grade smartglasses has yet to find mainstream success, two more contenders emerged this week, as Vuzix confirmed that a leak of a fashion-forward design is legitmate and Vivo introduced tethered smartglasses designed to pair with its new 5G smartphone.
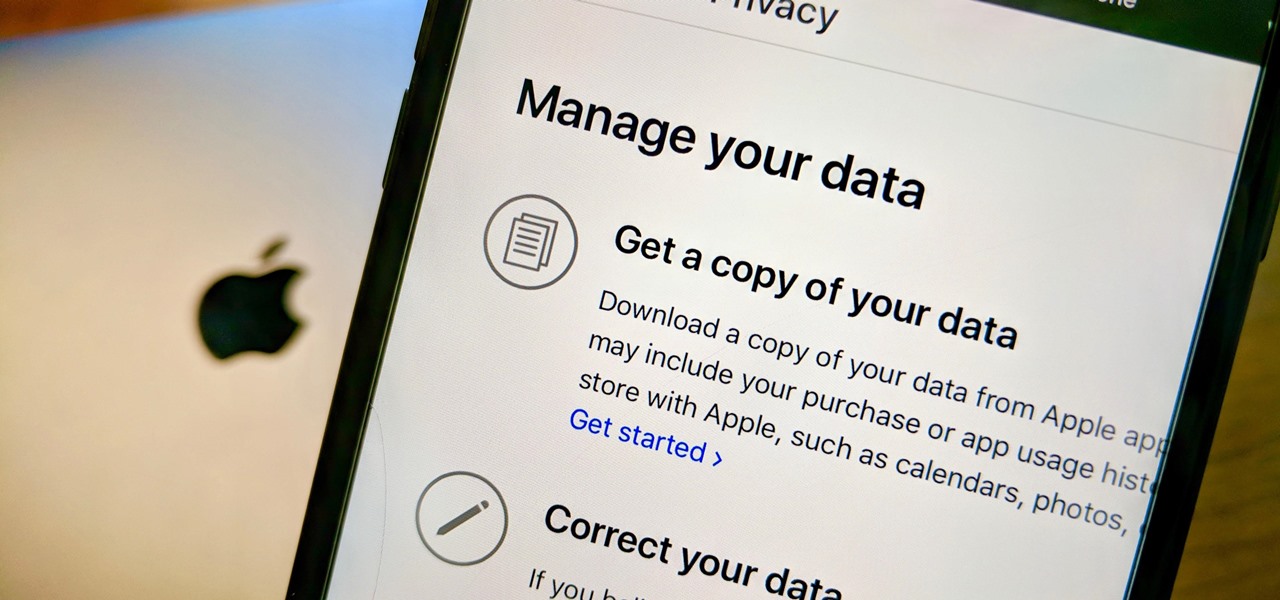
Personal data is a hot topic right now, and for good reason. Never before has the public been so on edge about how companies use their information. Services like Facebook and Google now allow you to download all of the data each has on file. Soon, you'll be able to see exactly the same for Apple as well.

OnePlus has now officially upgraded both the 5 and 5T to Android 8.1 Oreo. As implied by the version number, this isn't a huge update from Android 8.0 Oreo. However, OnePlus has included a few of their own features as well.

Messaging apps can be a double-edged sword. Not only do they let you interact with other people, but they also let you go back and reminisce on past exchanges. However, that same archive can be used against you in certain situations. Luckily, Signal can be manipulated to remove any record of past messages.

As of 2016, there are approximately 1.85 billion Android smartphones worldwide. This growing popularity has led to an increasing number hacks and cyber attacks against the OS. Unfortunately, Android users need more protection than what is offered by Google. The good thing is that there are a number of options available.

Cruise Automation, the driverless car startup General Motors (GM) bought for $1 billion in 2016, is readying a formidable fleet of robo-taxis for rollout in cities throughout the US. But when it comes to details about how the company plans to realize these lofty goals, it's been fairly tight-lipped.

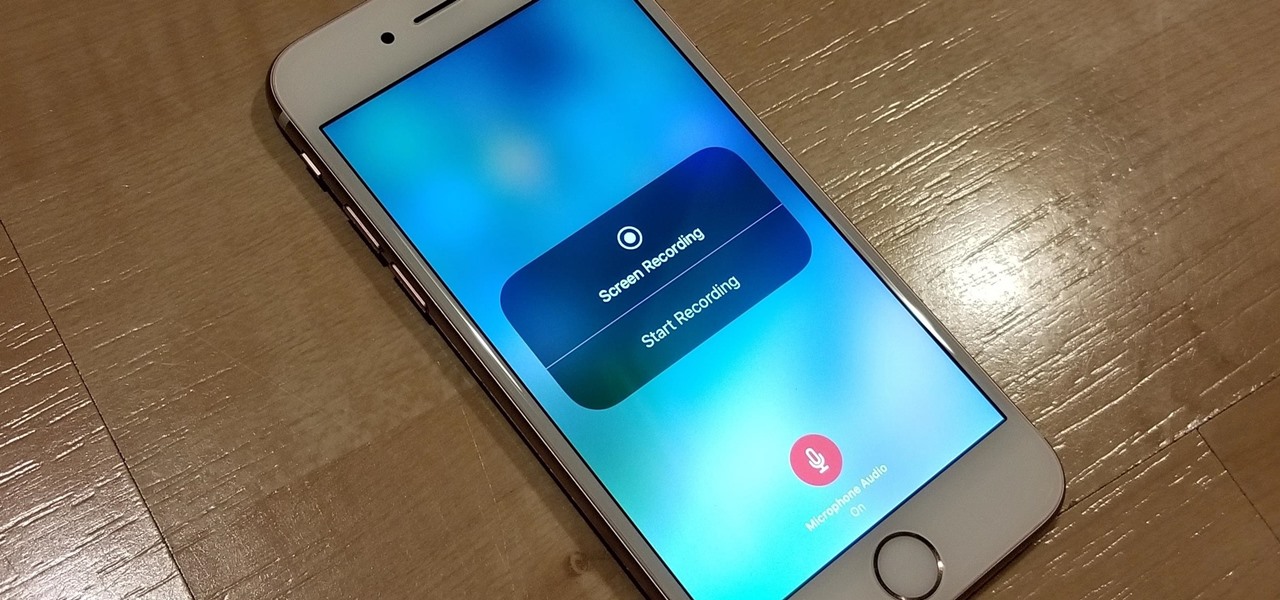
The only official way to record your iPhone's screen before iOS 11 was to hook it up to a Mac and use QuickTime Player to do the recording for you. If you wanted to record your iPhone's screen without an external device, there were unofficial apps you could use, like AirShou, but they required complicated installations. Now, in iOS 11, iOS 12, and iOS 13, Apple has an official, native screen recording tool.

New statements from Apple make it clear that they do not believe a hacker, or group of hackers, breached any of their systems. This comes after a recent report from Motherboard that a hacker gang called the "Turkish Crime Family" is threatening to remotely wipe up to 559 million iPhones by April 7.

A robust appetite for imported foods is leading to increased disease outbreak in the US. Despite the locovore and slow food movements, America's demand for foreign foods is picking up. According to a study published in the journal of Emerging Infectious Diseases, demand for imported fresh fruits, vegetables, and seafoods has jumped in recent years.

Marijuana is legal to use for medical purposes in 28 states and the District of Columbia, but the quick development of this new industry could have left some regulation issues in the lurch.

Last week it was announced that Waymo, the former Google Self-Driving Car project, had graduated from Alphabet's X innovation center. This graduation had been in the cards for many months with senior members of the project team and X hinting that it would be soon.

As Android's official app provider, the Google Play Store is packed with thousands of useful programs. But Google's terms of service is extremely restrictive, which means that countless apps simply don't qualify to be hosted on the Google Play Store.

Chestnuts are roasting on an open fire, which can only mean one thing: Christmas is nearly here. It's the time of year we're supposed to spend with family and friends, but usually we spend it stressing out over what to buy everyone on our list without going over budget, or shopping for decorations or holiday-friendly food items.

You want to become anonymous, and dont want your IP to be logged on websites? Well read along here. Continuing This Series:

As many of you know, processor's clock frequency improvement got stuck in about 2003, causing the origin of multicore CPU (and other technologies). In this article I'll introduce you on how to run code simultaneously in various processors (I suppose that all of you have a multicore CPU). When you write code without any parallel directive, it only executes in one CPU at the same time (see it below). OpenMP make simple to work with various cores (if not with all of them) , without so much heada...

Welcome back, my nascent hackers! Although my favorite TV show, Mr. Robot, had completed its first season already, I have not completed demonstrating the hacks that Elliot used in the show. (By the way, I can't wait for season 2!)
Mostly all hackers like to have a laugh. We like to have fun! We like to troll. And maybe, even cause some havoc once in a while. But, while we do this, we must always stay in the line of the law.

Welcome back, my fledgling hackers! In this series, I am trying to develop your knowledge of digital forensics, which is valuable whether you're choosing a career in it or just want to know how your hacker activity can be traced. Few professional digital forensic investigators have a hacking background, but the best ones do.

Unruly customers. Crazy exes. Horrible bosses. When you need proof of insanity or just want it for your records, recording a phone call is a must. Problem is, it's not the easiest thing to do on an iPhone — but it's completely possible.

Big box stores love to sell gift cards, and as consumers, we snap them up almost as quickly as they can be printed. This industry has become rather profitable, though, because portions of the gift card balances often go unused.

Welcome back, my tenderfoot hackers! A short while ago, I started a new series called "How to Spy on Anyone." The idea behind this series is that computer hacking is increasingly being used in espionage and cyber warfare, as well as by private detectives and law enforcement to solve cases. I am trying to demonstrate, in this series, ways that hacking is being used in these professions. For those of you who are training for those careers, I dedicate this series.

We are living in a golden age of craft beers. Originally invented by the ancient Egyptians, every culture now has its own tastes regarding beer. The process of making beer is so multi-faceted, it's a miracle that any gets made at all.

It's nice to have a drink on an airplane, whether you're taking a flight somewhere fun or for work. However, what's not so nice is the high prices and relatively bad quality of the liquor that's available.

Fish is delicious, and as the Harvard School of Public Health points out, incredibly good for you. There are many studies that show regularly consuming a couple of servings of fish per week can help prevent heart disease and may well reduce your chances of stroke, depression, and getting Alzheimer's. After all, there's a reason why fish is called "brain food."

There are spontaneous times in everyday life that just scream to be recorded on video. The crazy guy yelling obscenities on the bus. Your favorite actor at the supermarket check-out register. Maybe even your kids just being super adorable.

Like Costco's price codes or the tags on your bread, the numerical codes printed on those sticky little fruit and vegetable labels can reveal a lot of information to us consumers. Once you understand the codes, you can look at that little label (also known as PLU, or "price look up" label) and know whether the produce you're about to buy or eat was treated with pesticides, genetically modified, both, or neither. Before we go any further with deciphering the codes on these labels, let's take a...

It took many months of cries from all around the internet—and a particularly large groan from an ex-Lifehacker editor-in-chief—but Apple has not only acknowledged the existence of its iMessage problem, it's promising a fix.

Welcome back, my fledgling hackers! It's been awhile since we did a Metasploit tutorial, and several of you have pleaded with me for more. I couldn't be happier to oblige, as it's my favorite tool. For the next several weeks, I'll intersperse some new guides that'll help expand your Metasploit skills and keep you abreast of new developments in Metasploit, so look for them in the near future.

Russians are well known for their knack at documenting exciting and horribly beautiful events on the go, from insane car accidents to attempted insurance fraud and even a superbolide meteor streaking across the sky.

Welcome back, my budding hackers! Previous to this tutorial, we've focused mostly on hacking the target system. If we're successful in owning the target system, we'll then want to make certain that the system administrator doesn't know we were there, and that he or she cannot track us.

Sometimes, doing the right thing is way more difficult than it should be, like trying to return a lost smartphone. Despite having the best intentions, it's often hard to track down the rightful owner, especially if the device is armed with a passcode. On the other hand, there are plenty of people who see an unattended iPhone or Samsung Galaxy S3 as a chance for profit. In 2011 alone, the number of lost and stolen cell phones in America was worth over 30 billion dollars. That's right, billion....

Welcome back, my nascent Hackers! In my last blog, we looked at a passive way to gather information necessary for a hack. The advantage of using passive recon is that it's totally undetectable, meaning that the target never knows you're scouting them and you leave no tracks. The disadvantage, of course, is that it's limited to only some websites and not entirely reliable.

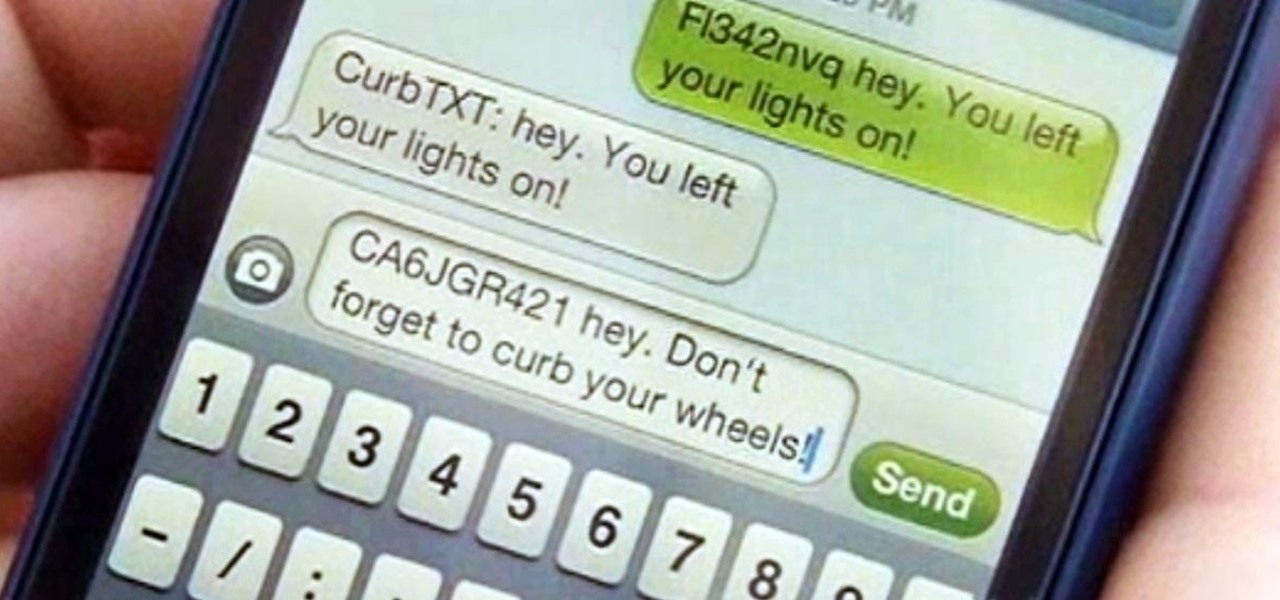
Parking. Ugh. Parking is about as fun as running through a swarm of bees while being chased by a pack of wolves from The Grey.

As practically the entire Steampunk world knows by now, IBM has predicted that Steampunk will be the big new trend from 2013 to 2015. They based this prediction on their computers, which sift through broad swathes of the internet in order to see patterns that may help commercial industries. According to them, Steampunk has been on the rise for the last few years, and they predict that it will explode into peak popularity within the next two years. But what does that mean and how will it impac...

Want to find out if your neighbors are talking about you? You could always hack their webcam or turn your iPhone into a secret spy camera, but unless you have a key to their house, that could be tricky to do without getting caught.

I'm not admitting to anything, but let's be honest, most of us download content on the Web from time to time. With copyright holders laying down the law more and more often, it can't hurt to do so with caution. And even if you aren't downloading copyrighted material, you still don't want companies snooping in on your online activities. So just how do you protect yourself when torrenting? Avoid "Open Communities"

Your closet is an area that holds important things such as keys, glasses, clothes and shoes. However, for some reason, it's always messy. Why is this? I know my closet is messy because I don’t have a lot of time to sit down and organize every little thing in there. I have never really even given much thought into organizing it.

A game warden's job is to enforce the hunting, fishing and trapping laws in the United States. Learn how to become a game warden with tips from an experienced game warden in this free hunting video series.

Google Voice has a hidden feature that lets you record any phone call you're participating in, and unlike other apps, it doesn't cost a dime.

Becoming a successful web developer is more than knowing coding languages. Learning to craft functional, intuitive designs is as much coding as knowing how the user will interact with what you've built. The Complete Become a UI/UX Designer Bundle can take you from introduction to mastery in designing the best user experience, and right now, it's only $34.99.