The buttonhole stitch is used in many types of hand embroidery - general surface embroidery, crazy quilting, whitework and cutwork, Mountmellick embroidery, needle lace, filet work - you name it, buttonhole stitch fits in somehow. It's a super versatile stitch, and once you have the basic stitch down, it's just a matter of applying it in a variety of ways. Watch this video from Needle 'n Thread to see how it's done.

Here's how to access some hidden websites at the Internet Cafe in Grand Theft Auto 4 1) Go To Internet Cafe In GTA IV

Saj bread, also called Markouk, is a type of flat bread common in the middle eastern countries. It is baked on a domed or convex metal griddle, known as Saj. Similar to the procedures for making other flat breads, the dough of Saj bread is flattened and kept very thin prior to cooking, resulting in a very slender depth to this bread.

This Scooby's Workshop video shows proper form of the incline dumbbell fly exercise for pecs. Fly type exercises have done far more for my pec development than the pushing type exercises. In doing flys, make sure that your arms do NOT go behind the plane of your body as this puts too much stress on the shoulder joint. If you don't have a incline bench, you can make one as I have done here by tying a 2x8 securely to a coffee table. This exercise is best done with a spotter for safety, if you m...

Learn how to wear different types of hijab in different styles in this two part series. The hijab details have been explained in terms of the hijab material and hijab durability.

This is a great video that breaks down the different types of microphones available and how you can use them to get different results or resolve different problems. If you use the right microphone, your videos will come out that much better.

Does your video look flat? By using Three Point Lighting, you will be able to give your flat video more dimension. In this tutorial, Israel Hyman demonstrates the effects of the key light, the fill light, and the back light. This is a long standing lighting technique that you definitely should know if you plan on shooting any type of video.

Coach Tom Martin discusses different techniques for shooting and the various types of shots used in the game. Among these are the wrist shot, snap shot, and the slap shot. A recap is given at the end of the video. Throughout the video, tips appear in the form of pop ups.

Tennis Pro Brad Gilbert discusses and shows techniques for hitting an overhand smash. The types of overheads discussed are the basic, scissor-kick, backhand, and bounce. They are summarized at the end of the video. Additional information is given in sidebars and popups during the video so it's easy to understand.

This video demonstrates how to work the medial deltoid muscles on an ordinary gym machine, the lateral raise. This video walks you through setting up the machine to your body type and doing the excercizes correctly on the machine.

How to fix those loose and jiggly cupboard doors on your kitchen or bathroom cabinets. For this repair, you're going to need a flat head or phillips head screwdriver. Now, the type of screwdriver you're going to need is really dependent on the type of screw you have holding your cabinet door to your cabinet. We're going to use a phillips head screwdriver because, as you can see here, the top of our screw head is shaped like that of a crosshair. If it were shaped like one long groove in a stra...

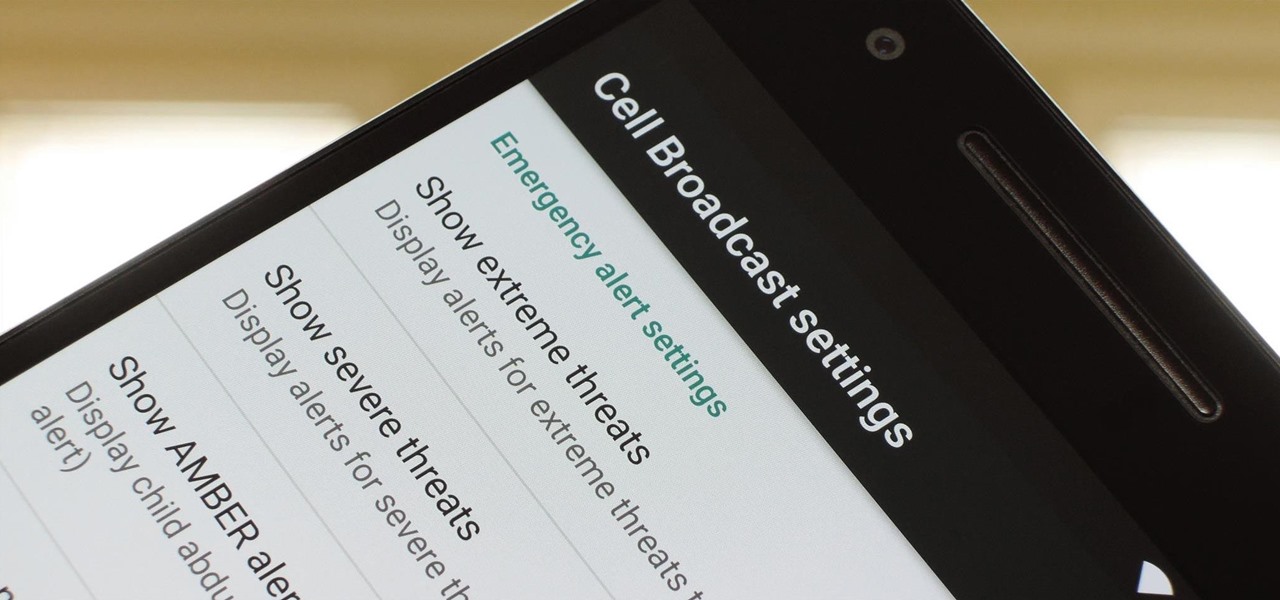
To bring things up to code with a new FCC standard, Android recently added an "Emergency broadcasts" feature that will make your smartphone notify you whenever a potential safety threat or Amber Alert is posted in your area. Even if you have your phone set to silent, these emergency alerts will cause your device to emit a loud, piercing sound when a potential threat is nearby.

Waking up your Apple Watch to see "your heart has shown signs of an irregular rhythm suggestive of atrial fibrillation" might come as a shock. While your watch can send you warnings if it detects a fast or low heart rate, those messages are pretty vague, while the abnormal arrhythmia alert can downright scary. So what should you do if you receive one of these AFib notifications?

Sure, emojis are all the rage, but there's not an emoji for every emotion or feeling just yet. That's where emoticons come into play, emoji's older typographical sibling. Unfortunately, emoticons can be hard to type out, easy to forget, and ASCII art, in general, can be pretty time-consuming to create from scratch — but there's an easy way to forgo all these issues — make keyboard shortcuts.

Configuring onion services for the first time can be tricky. A surprising number of system administrators make seemingly trivial mistakes that ultimately lead to catastrophic cases of de-anonymizing supposedly anonymous sites on the dark web. OnionScan is a tool designed to identify common misconfigurations in onion services and aid us in understanding how to fix them.

While hackers adore the command line, working with the GUI (graphical user interface) of an operating system has some advantages. This is especially true when it comes to post-exploitation. When we can control the mouse and keyboard of a remote computer, we can truly say we have complete control over the device. Today, I'm going to introduce to you the PyAutoGUI module, which does just that, and just how much fun you can have with it!

PowerShell Empire is a post-exploitation framework for computers and servers running Microsoft Windows, Windows Server operating systems, or both. In these tutorials, we will be exploring everything from how to install Powershell Empire to how to snoop around a target's computer without the antivirus software knowing about it. If we are lucky, we might even be able to obtain domain administrator credentials and own the whole network.

Unless you're a WhatsApp pro user, you may be surprised to know that there are text formatting options that you can apply to your messages. Markdown characters can help you emphasize certain words or phrases by making them italicized or bold, and it'll even let you cross out words and change the font. It's one of those nice touches that isn't available in most other messaging apps.

Flu vaccines can help prevent us from getting or suffering the most severe effects of the flu. But, each vaccine only protects us from three different strains of the flu. If we don't have a vaccine against all types of flu, it leaves us open for an epidemic with a flu virus we didn't expect.

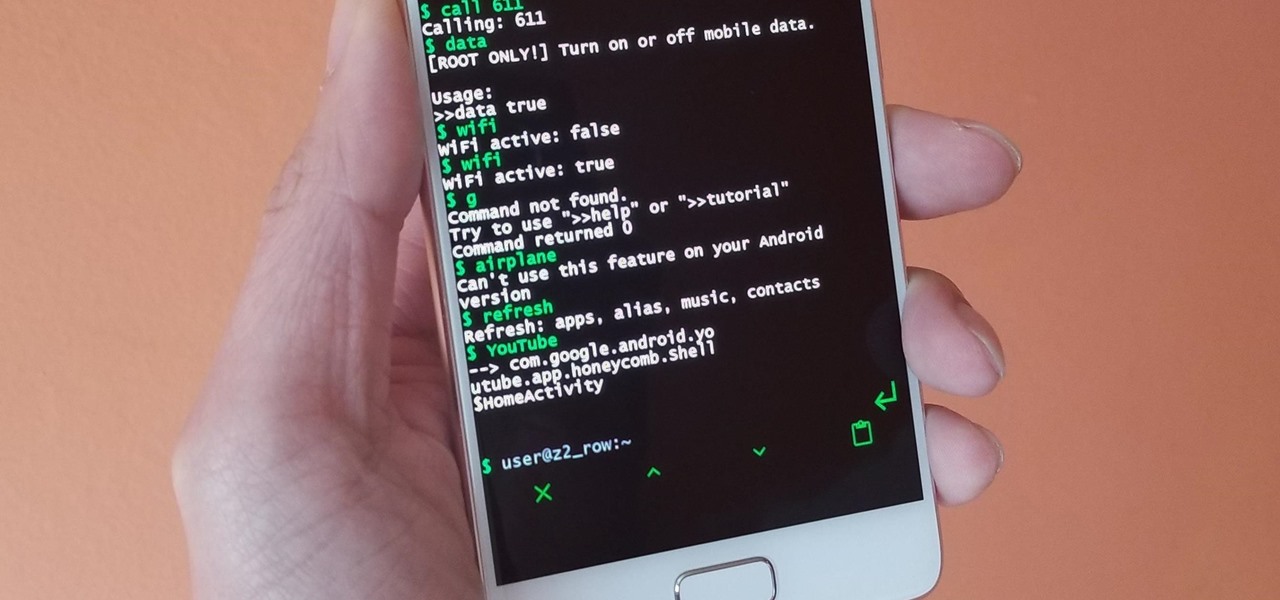
Running commands on Linux seems so complicated for the layman that it may as well be a foreign language. But for the die-hard terminal users, or for those who are just curious about the Linux experience, there's a new Android launcher that gives your home screen a command line makeover.

Connecting your devices with a cable is the fastest and most reliable way to transfer files between them. Now that most Android devices have either USB Type-C or a Micro-USB port that supports USB OTG, phones are capable of importing media files directly from a camera using a simple (and cheap) adapter.

Our quest to find novel compounds in nature that we can use against human diseases —a process called bioprospecting — has led a research team to a small frog found in India. From the skin slime of the colorful Hydrophylax bahuvistara, researchers reported finding a peptide — a small piece of protein — that can destroy many strains of human flu and can even protect mice against the flu.

Designing for mixed reality, especially for the HoloLens, can present unique challenges. Dong Yoon Park, a Principal UX Designer at Microsoft with a passion for typography, recently gave a talk to the Windows Holographic Users Group Redmond (WinHUGR) about the pitfalls he ran into trying to convert what started out as a 2D iOS app 5 years ago to the newer 3D Holographic frontier with Unity.

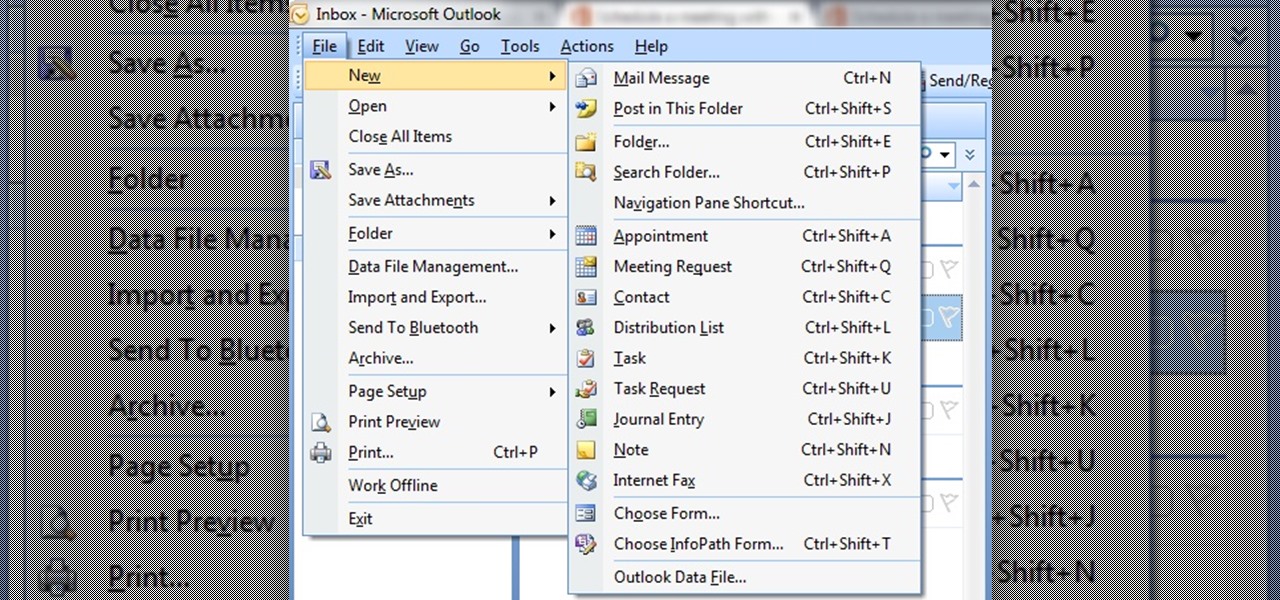
In this tutorial First, we will discuss what a meeting is, How can we schedule it in Outlook. A meeting can be defined as a mass of two or more people have a common motive. All the people present in a meeting can share their ideas and exchange information, to carry out the actions to achieve their goal. This tutorial helps those people who are looking for the steps to Schedule a Meeting in MS Outlook.

So, you want to perform an exploit on a victim, but you're not on the same network as their machine. In this tutorial, I'll be showing you how to set up a meterpreter reverse_tcp attack to work over the internet.

Welcome back to another episode of Java Tutorials, In today's tutorial, we'll be learning about what methods are, proper syntax when writing Methods, and why they are beneficial in a program's code.

Yes, I understand some people may consider this a repost. However, I have been searching for this answer for 3 weeks and after reading numerous reddit post, Kali Forums post and Null byte post I finally have gotten it to work for me. I would like to compile and share this information with you guys.

Welcome back, my neophyte hackers! Metasploit is such a powerful tool that I can only scratch the surface of its capabilities here. As it has developed over the years, it is now possible to use Metasploit for nearly everything from recon to post exploitation to covering your tracks. Given its versatility, every aspiring hacker should have at least a tentative grasp of Metasploit.

Make no bones about it—having an "undo" option is a freaking godsend. Whether you accidentally deleted an entire essay, screwed up the shading on a Photoshop job, or sent an email that wasn't quite ready, having the option to undo a click or button-press can definitely be a lifesaver.
Hello, Hackers/Viewers! My name is nullf0x, and I have 4 years of experience as a hacker. You might see everyday that one of your friends or acquaintances get a new virus in their computer. You might think, How cool would it be if I made a virus? or How cool would I be if i could remove viruses from others computers for money or free?

Today I am going to teach the various ways that you can use social engineering to hack a system. For those of you that have followed my past tutorials, you know that social engineering can unlock a world of possibilities. This is because no matter how many firewalls, no matter how many patches there are on a server, the password is kept in the minds of people...and people, are not as smart as computers.

Third-party keyboards have been available for iPhone ever since iOS 8, but which ones are worth checking out? There have been many options over the years, and if you want keyboard features like swipe-typing and themes, you're going to have to put Apple's stock QuickType keyboard on the backburner and try out these top hits.

As soon as third-party keyboard compatibility was announced for iOS 8, Apple loyalists and the newly curious both looked to the popular Android third-party keyboard developer, SwiftKey, to see if they'd be offering their services to iOS.

Every Windows system includes command prompt; and while a lot of people on Null Byte and WonderHowTo in general know how to use it, some people don't know anything about it, even how to access it.

THis video shows you what types of videos you can make, why you should make videos and exactly whant you need to get started.

This video will show you how to use MCedit to create flat land in your Minecraft world. Are you the type for wide open spaces? Land lots of land under starry skies above? Watch this video to learn how to make flatland in Minecraft with MCedit.

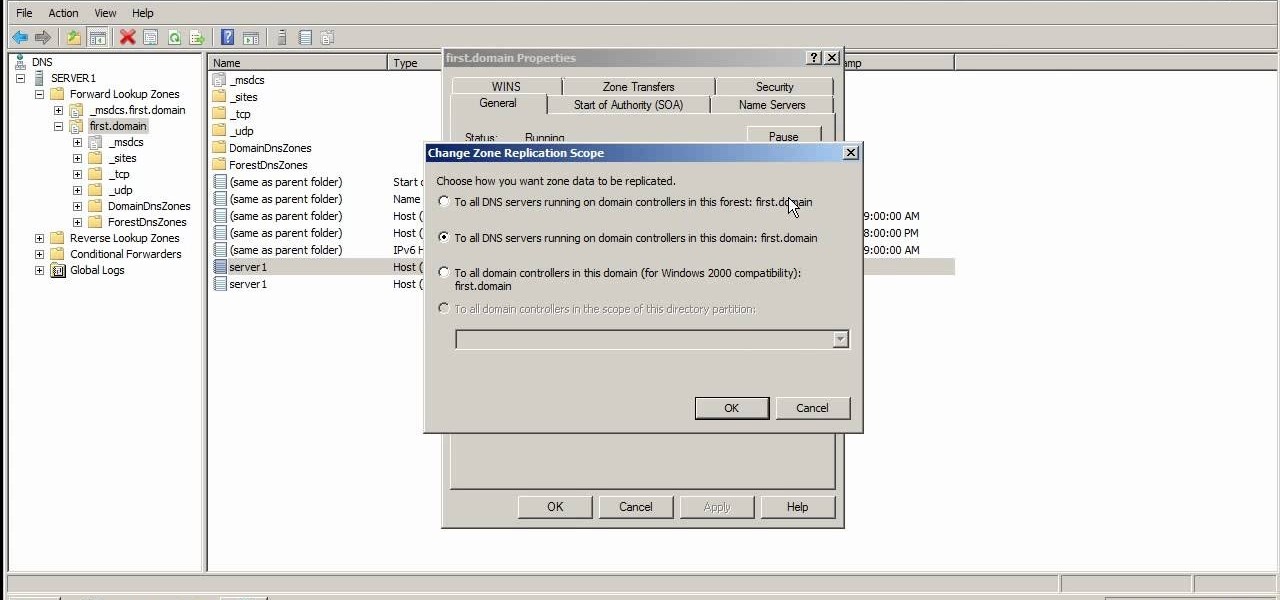
This video explains the different kinds of zones you will come across in Microsoft Windows Server 2008 DNS. The video has practical step by step instructions to managing these zones, as well as understanding their different functions and uses, and covers replication.

Fairy cakes are basically lovely little cupcakes adorned with pretty icing and "fairy dust" - AKA sprinkles - for a nice ethereal effect.

You may be just recovering from a hectic - and binge-filled - holiday season, but prom season is just around the corner. Make sure you look like the belle of the ball by creating this simple and romantic hairstyle.

This tutorial shows you how to determine what kind of skirt you have - straight or tapered . Then, depending on the type of skirt you have, you're shown how to alter the hem or shorten the length of your skirt.