Post-exploitation information gathering can be a long and drawn-out process, but it is an essential step when trying to pivot or establish advanced persistence. Every hacker should know how to enumerate a target manually, but sometimes it is worth it to automate the process. Metasploit contains post modules that can quickly gather valuable information about a target, saving both time and effort.

Web application firewalls are one of the strongest defenses a web app has, but they can be vulnerable if the firewall version used is known to an attacker. Understanding which firewall a target is using can be the first step to a hacker discovering how to get past it — and what defenses are in place on a target. And the tools Wafw00f and Nmap make fingerprinting firewalls easy.

TWRP won't be ready for the Pixel 4 and 4 XL until months after release. But since you can already root with Magisk and tinker with the OS, you might find yourself in a situation where your phone won't boot, yet you don't have a custom recovery installed to fix it. Luckily, there's still a way around this.

Google is an incredibly useful database of indexed websites, but querying Google doesn't search for what you type literally. The algorithms behind Google's searches can lead to a lot of irrelevant results. Still, with the right operators, we can be more exact while searching for information that's time-sensitive or difficult to find.

Reconnaissance is one of the most important and often the most time consuming, part of planning an attack against a target.

While you might suspect your MacOS computer has been infected with malware, it can be difficult to know for sure. One way to spot malicious programs is to look for suspicious behavior — like programs listening in on our keyboard input or launching themselves every time we boot. Thanks to free MacOS tools called ReiKey and KnockKnock, we can detect suspicious programs to discover keyloggers and other persistent malware lurking on our system.

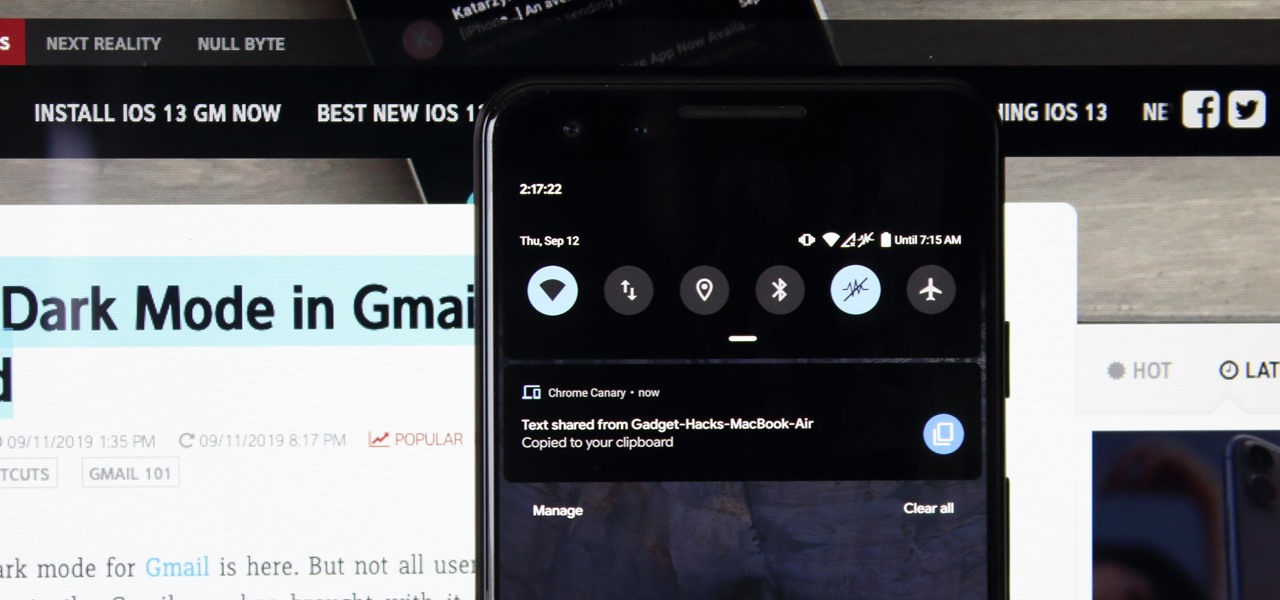
Recently, Android Police highlighted one of the downfalls of Android 10's new privacy protection: the fact that it broke the ability for apps like Pushbullet to sync your clipboard across devices. While third-party apps can potentially find a way around this, there's no guarantee. But have no fear, Google is here to the rescue.

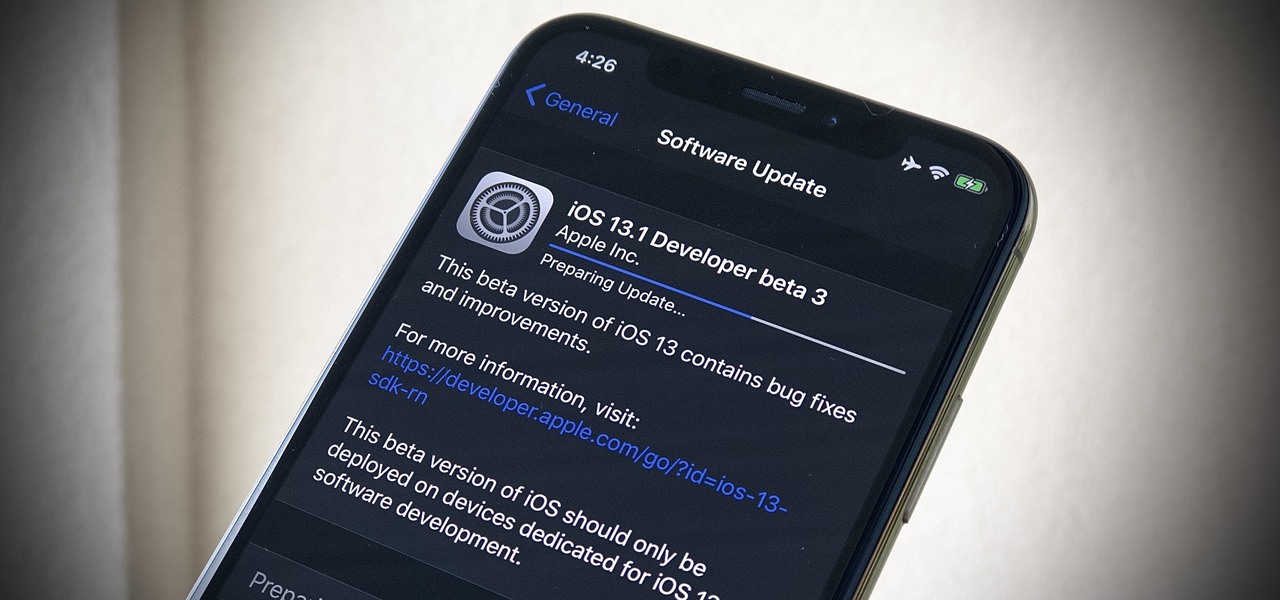
Yesterday showed us our first look at the iPhone 11, iPhone 11 Pro, and iPhone 11 Pro Max. But it wasn't all about hardware. Apple also released the iOS 13 Golden Master, making iOS 13.1 the main focus for us beta testers. Now, Apple just seeded the third public beta, following yesterday's release of 13.1 dev beta 3.

It's a big day for Apple. First, the company announced its new suite of phones: iPhone 11, iPhone 11 Pro, and iPhone 11 Pro Max. Then, we get the iOS 13 Golden Master, the beta version of iOS 13 that will eventually release to the general public on Sept. 19. Now, it seems the company has dropped the third developer beta for iOS 13.1, set to release to all compatible iPhones on Sept. 30.

Apple has pulled quite the headscratcher in anticipation of its big iPhone unveiling next week. Its latest iPhone update, iOS 13.0, is just on the horizon, going through eight beta versions so far. And yet, before that software's official release, the company has started beta testing iOS 13.1, with no explanation why. And the second public beta for iOS 13.1 is now out, so let's see what's new.

When Apple takes the stage next week, we have no idea what version of iOS it will release. For months it seemed like a given that we would, of course, see iOS 13 seeded to our iPhones. Now, we aren't sure if Apple will tout iOS 13 or iOS 13.1, since the latter is now the focus of its beta testing. In fact, 13.1's second developer beta is now available to download and install.

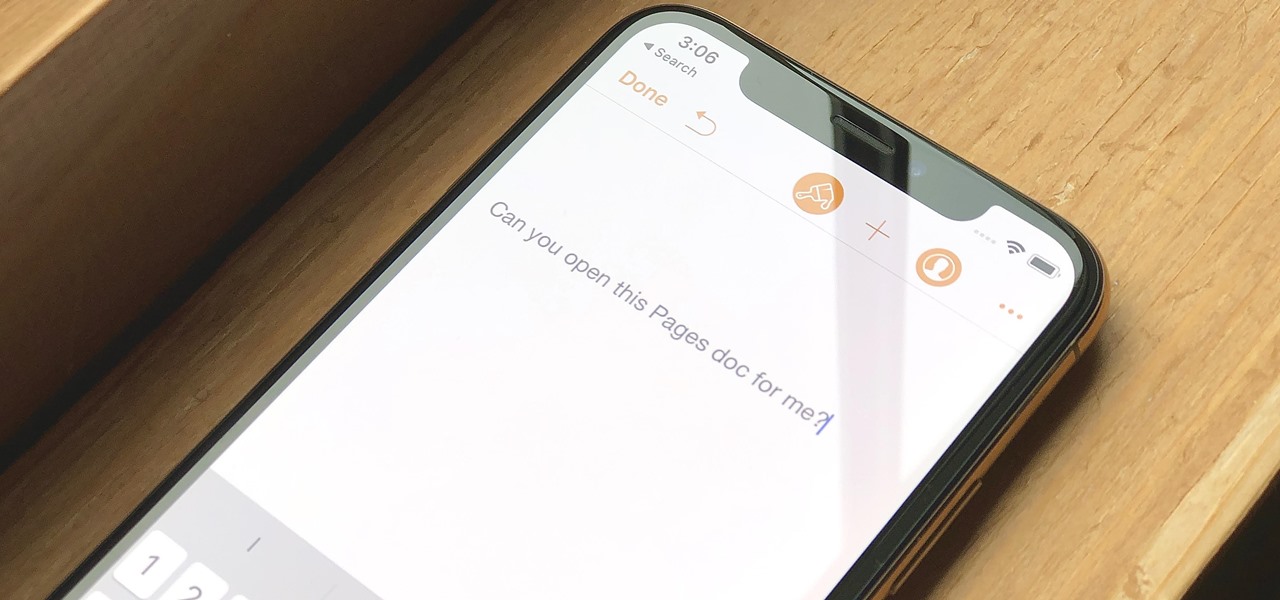
Let's say you have an important report to submit, but you want to check it over for any last-minute edits or changes. Times running out, and you simply can't find this Pages document anywhere. Wouldn't it be great if you could just ask your iPhone to open the report for you, so you could stop wasting time searching and finish the paper? Well, thankfully, Siri can help you out with that.

Beta testing certainly has its perks. While you do need to deal with bugs, you're introduced to new features before the general community. And if we're talking iPhones, there are over 200 new features in iOS 13 beta. If you're already on board with iOS 13 public beta 6 for iPhone, you can get an upgrade on that firmware as Apple just released public beta 7 today.

OnePlus is known for making a quality products with their line of smartphones, but as with most, they have their own specific customizations that you can't get anywhere else. Font types, boot animations, sounds, and proprietary apps — they are all unique to each different skin of Android. The good news, though? There's an effortless way you can grab some of that OxygenOS goodness right now.

Who's ready to let future Facebook augmented reality smartglasses read their brain? Well, ready or not, the tech giant is making progress in the area of brain control interfaces (BCI) by funding research.

Particular vulnerabilities and exploits come along and make headlines with their catchy names and impressive potential for damage. EternalBlue is one of those exploits. Originally tied to the NSA, this zero-day exploited a flaw in the SMB protocol, affecting many Windows machines and wreaking havoc everywhere. Here, we will use EternalBlue to exploit SMB via Metasploit.

If you record yourself for a vlog or story post using your selfie camera, it can be challenging to stay on message. You might worry too much about the way you look or sound to focus on what you want to say. Using a script can help, but looking away from the camera to read is unprofessional, even on social platforms like Instagram. What you need is a teleprompter, and there are apps for that.

Because of the way Android is laid out, you automatically lose a portion of the top and bottom of your screen thanks to the status and navigation bars. The thing is, you don't always need the navigation buttons. By hiding them, you can enjoy more of your Galaxy S10's big, beautiful display.

If you're a long-time Spark user, you'll know that one of the only drawbacks to the app used to be its lack of rich text-editing tools such as hyperlinking. If you needed to link out to a site in an email, your best bet was to grab a computer to get the job done. Well, close those laptops and shut down those PCs — Spark corrected this issue, implementing support for hyperlinking right into the app.

Newer businesses, or older businesses looking for more traffic and sales, often offer enticing deals to attract customers. On Yelp, any business has the option to provide a deal to users, which is essentially a Groupon-like coupon. But how do you find these deals in the Yelp app for Android or iOS?

Apple just released the sixth beta release for iOS 12.2 today, Monday, March 18. Just as expected, the update to the developer version dropped just past 1 p.m. EDT (10 a.m. PDT), and comes with new changes and features from iOS 12.2 beta 5 and beyond, including a new warranty status in the "About" page in Settings.

While the notch on Apple's newer iPhones started a wave of notches across the smartphone market, there are still plenty of users who don't like screen-obstructing zone up top, and you may be one of them. While it may soon disappear in future iPhone models, or at least get smaller, there are things you can do to hide the big notch you have right now.

Gboard has come a long way from its roots as the "Google Keyboard" in the earlier days of Android. It's now the most popular, feature-rich, and useful keyboard app on the market. Google even includes quite a few themes right out of the box for Gboard — but what if you could have even more?

The Google Phone app is one of the best dialers for Android today, especially with all of the unique and exciting features it brings to the table. Unfortunately, without owning a Pixel phone, you are unable to officially download the app, making a modified version your only option. However, this version of Google Phone is missing a few key features, such as spam protection and business search.

Many popular IoT devices have terrible security. For instance, a hacker who's on the same Wi-Fi network as a Sonos speaker can assume direct control over the device's behavior. If an IoT device doesn't secure the messages used to control it over a network, it's easy for somebody to write a few Python scripts to make it do whatever they want.

Instagram is all about the hook. If you want followers to stick around, you need to keep your content interesting and engaging. Rainbow text can really make your Stories pop, but it's not really an Instagram "feature," meaning it's not an easy task to accomplish. There is, however, an easy hack that takes all the work out of rainbow-colored text, making your Stories better overall.

Users are often the weakest link when probing for vulnerabilities, and it's no surprise they can be easily fooled. One way to do this is called clickjacking. This type of attack tricks the victim into clicking something they didn't mean to click, something under the attacker's control. Burp Suite contains a useful tool called Clickbandit to generate a clickjacking attack automatically.

Many online users worry about their accounts being breached by some master hacker, but the more likely scenario is falling victim to a bot written to use leaked passwords in data breaches from companies like LinkedIn, MySpace, and Tumblr. For instance, a tool called H8mail can search through over 1 billion leaked credentials to discover passwords that might still be in use today.

I hate folder names, especially the one Apple shoves down our digital throats. On a computer, they make total sense, but on my iPhone, it's just more clutter on the home screen. You can tell what folder is what just by looking at the app icons within it, so why are we forced to label them? Technically, we're not, since there is a workaround in iOS 12 and iOS 13 to make those labels disappear for good.

One of the things that sets a seasoned hacker apart from the script kiddies is the ability to effectively sneak past antivirus defenses when executing an attack. One way to do this is to use custom shellcode in an exploit. Not everyone is an expert at writing shellcode, but luckily there's an easy way to do this that is both quick and effective.

Although the Essential PH-1 got off to a rocky start, thanks to steady updates, it has slowly become one of the best Android phones to come out in recent years. For $499, the Essential Phone is a cheaper Pixel, receiving updates almost as soon as the Pixel lineup does. What's more, you get a phone with an easily unlockable bootloader, which is the first step to rooting.

Note-taking apps are a dime a dozen on the Play Store. However, due to their inability to sync across devices, many can't compete with Google Keep. Mozilla decided to throw their hat in the ring with Notes by Firefox, and unlike others, their notes app syncs easily with one of the most popular browsers, plus it's encrypted.

With all the web applications out on the internet today, and especially the ones built and configured by novices, it's easy to find vulnerabilities. Some are more perilous than others, but the consequences of even the slightest breach can be tremendous in the hands of a skilled hacker. Directory traversal is a relatively simple attack but can be used to expose sensitive information on a server.

When it comes to modding Android, there's no better tool than Team Win's TWRP custom recovery. You can use it to root your phone, flash mods like Magisk or Xposed, and even replace the entire operating system with a custom ROM like LineageOS — honestly, there's not much this utility can't do.

Database technology has vastly improved the way we handle vast amounts of data, and almost every modern application utilizes it in one way or another. But the widespread use of databases naturally invites a slew of vulnerabilities and attacks to occur. SQL injection has been around for awhile, and as such, there are many defense methods in place to safeguard against these types of attacks.

Once a hacker has created a PowerShell payload to evade antivirus software and set up msfconsole on their attack system, they can then move onto disguising their executable to make it appear as a regular text file. This is how they will get a Windows 10 users to actually open the payload without knowing they are doing so.

Uber as a service is great, but using it requires you to hand over your location data to the company. What's worse is that you may be giving them precious access to your GPS even when don't have the Uber app open. This is both a major privacy issue and a drain on your battery. Fortunately, some of you can fix this.

Predictive text is a common feature in most mobile keyboards these days. However, many times, its guesses are way off, sometimes hilariously so. As absurd as it can be, predictive text can also continuously suggest the same wrong word over and over. Thankfully, Gboard offers users a way to quickly remove these suggestions for good on both iOS and Android.

There are hundreds, if not thousands, of programming languages and variations of those languages that exist. Currently, in the augmented reality space, it seems the Microsoft-created C# has won out as the overall top language of choice. While there are other options like JavaScript and C++, to name a few, C# seems to be the most worthwhile place to invest one's time and effort.

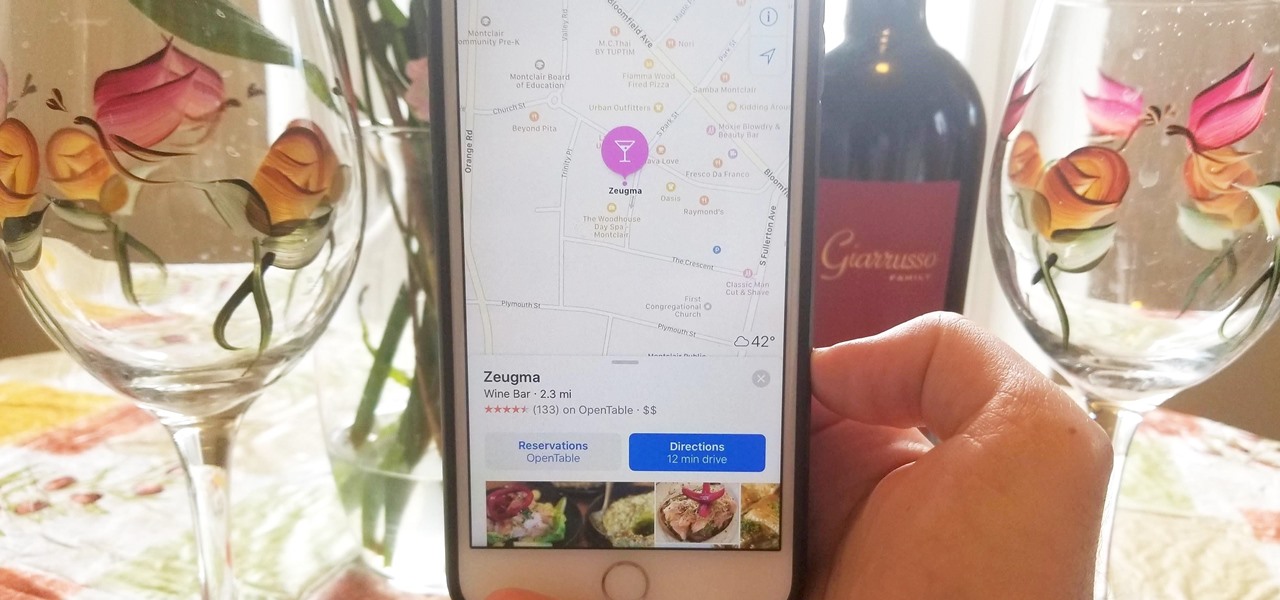
Apple has taken great strides to ensure that iPhone users are having an Apple Maps experience on par or even better than Google Maps can provide. One of the factors powering this is extensions, which adds functionality to certain apps by giving them permission to interact. Among all the possibilities, one extension will let you reserve dinner tables right from inside Apple Maps.