While still extremely awesome, the Samsung Galaxy Gear smartwatch is limited as to what you can download on to it, especially apps. It also doesn't have its own internet access (only Bluetooth), so apps like Instagram, Facebook, and Vine have yet to make their way to the Gear Store.

Welcome back, my fledgling hackers! It's been awhile since we did a Metasploit tutorial, and several of you have pleaded with me for more. I couldn't be happier to oblige, as it's my favorite tool. For the next several weeks, I'll intersperse some new guides that'll help expand your Metasploit skills and keep you abreast of new developments in Metasploit, so look for them in the near future.

Welcome back, my fledgling hackers! The database is the hacker's "pot-of-gold," as it contains information that is very valuable to both the business and the hacker. In this, the second of my series on hacking databases, we're on the "hunt" for Microsoft's SQL Server. Although far from the most commonly used database (Oracle hold's that title), Microsoft's SQL Server is very often found in small-to-medium sized businesses. Even a few big businesses use it.

Note to admins: If there's anything wrong with the links or the article itself (legality), let me know.
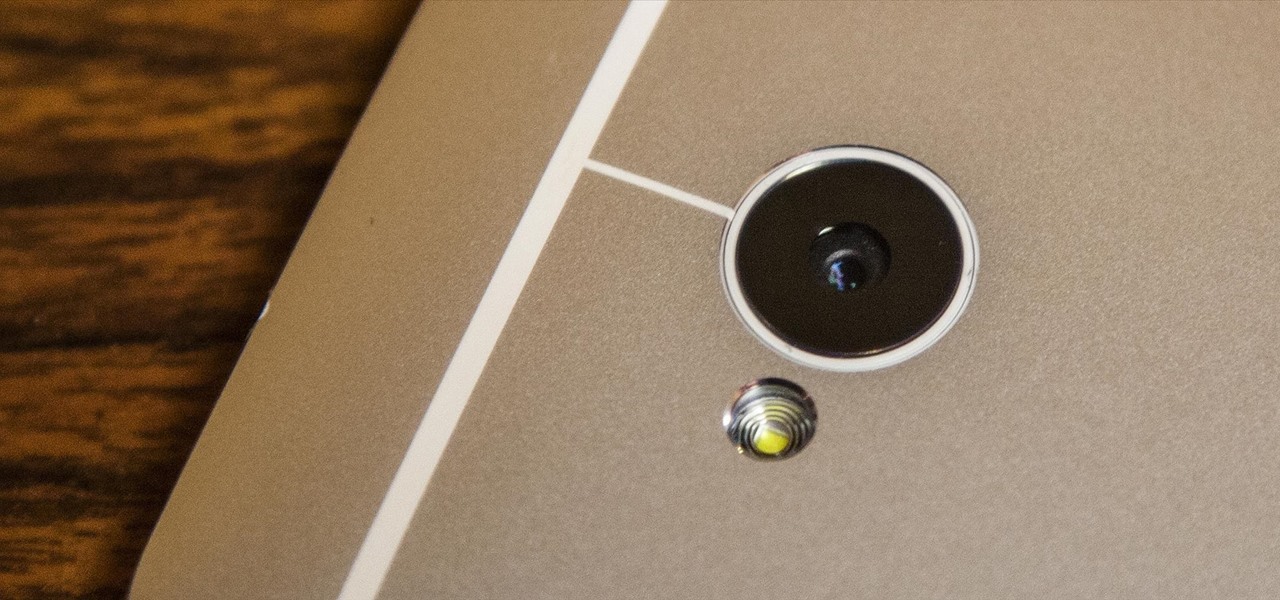
Most smartphone manufacturers focus on megapixels when it comes to cameras, but HTC took a different direction with the HTC One. Instead of trying to compete with the 13MP camera on the Samsung Galaxy S4, or the 20MP camera on the Sony Xperia Z1, or even the newer iPhone's 8MP, they decided on a simple 4MP camera. At first, you might think that 4MP is terrible, but not so fast. There are many advantages to your HTC One's camera that other phones just don't have.

Welcome back, my aspiring hackers! As mentioned several times in previous Linux tutorials, nearly everything in Linux is a file, and very often they are text files. For instance, all of the configuration files in Linux are text files. To reconfigure an application in Linux, we simply need to open the configuration file, change the text file, re-save, and then restart the application and our reconfiguration is applied.

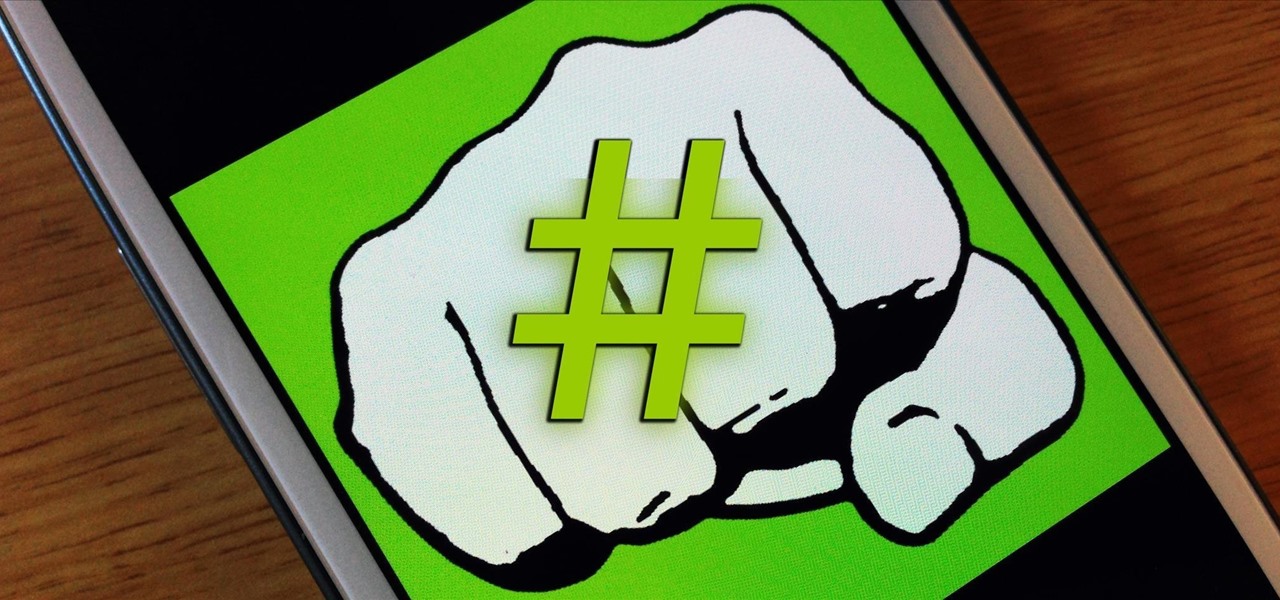
If you're a Twitter user, it's a safe bet to assume that you've used a hashtag. On all social networking sites that have the capability, such as Instagram, Facebook, and Google+, the pound (#) symbol is used to mark and designate specific keywords or topics in order to make it effortless for users to connect with one another.

It's that time of the year again when scores of students are flocking to stores for school supplies. Pens, pencils, books, and for math students, calculators.

Welcome, my hacker novitiates! As part of my series on hacking Wi-Fi, I want to demonstrate another excellent piece of hacking software for cracking WPA2-PSK passwords. In my last post, we cracked WPA2 using aircrack-ng. In this tutorial, we'll use a piece of software developed by wireless security researcher Joshua Wright called cowpatty (often stylized as coWPAtty). This app simplifies and speeds up the dictionary/hybrid attack against WPA2 passwords, so let's get to it!

Welcome back, my hacker novitiates! Finding vulnerabilities in systems can be one of the most time-consuming tasks for a hacker. There will be times, though, when you'll find yourself in a position that you know that a particular port represents a vulnerable application or service.

Welcome back, my greenhorn hackers! Continuing with my Wi-Fi hacking series, this article will focus on creating an invisible rogue access point, which is an access point that's not authorized by the information technology staff and may be a significant security vulnerability for any particular firm.

A spare key is one of those things that never seems like a huge deal until you need it. If you've ever lost your keys, had them stolen, or locked yourself out of your house or car, you know how difficult and embarrassing it can be trying to get your door open.

Welcome back, my hacker apprentices! In recent weeks, the revelation that the NSA has been spying on all of us has many people up in arms. I guess I take it all in stride as I just assume that the NSA is spying on all of us—all of the time. Don't get me wrong, I don't condone it, but I know the NSA.

Welcome back, my novice hackers! Most of my tutorials up until this point have addressed how to exploit a target assuming that we already know some basic information about their system. These include their IP address, operating system, open ports, services running, and so on.

Writing longhand may boost learning and goal achievement, but that doesn't mean squat if you don't have pen and paper on you.

Welcome back, my neophyte hackers! Several of you have written me asking how to crack passwords. The answer, in part, depends upon whether you have physical access to the computer, what operating system you are running, and how strong the passwords are.

So, you've finally converted from an iPhone to a Samsung Galaxy S3 smartphone. Great. Only now you're overwhelmed with the unfamiliar look and feel of the Android operating system.

A flat soda tastes awful. It's almost as bad as drinking a room temperature milkshake. Of course, you can always opt to buy single-serving cans or 20 ounce bottles, but that's always going to be more expensive than 2-liters.

LEDs have slowly become the standard for DIY lighting projects because they consume less power and last way longer than regular light bulbs do. Light-emitting diodes have no filament, meaning they generate their light solely by the movement of electrons in a semiconductor material.

One of the best things I love most about any new gaming console are the apps—I can switch from playing Assassin's Creed III to re-watching the fifth season of Breaking Bad on Netflix without ever getting off the couch. Beat that Atari.

There are a number of reasons why you might want to trick a web server into thinking you're on a different operating system (OS) or web browser. One might be that you want to test the mobile version of your website from your computer. Or perhaps for some reason a website is restricted to a certain OS or browser and you wish to circumnavigate that barrier. Today's guide shows you how to do just that!

I love my Mac just the way it is. Well, minus the fact that I accidentally deleted iPhoto and would now have to pay $14.99 to get it back. Other than that, my Mac is pretty sweet.

Welcome back my fellow hackers! In my last few articles, I've concentrated on what is called a listener, which is basically the same thing as backdoor and rootkit, only "listener" sounds much less malevolent than the other two terms.

One of the most frustrating things on the Internet are sites that make you register just to view content. I'm not talking about paywalls—I mean the sites that make you give them personal information to look at free articles or forum threads. Most people are uncomfortable with this because a lot of these sites either spam you themselves, or sell your information to someone else who will.

This guide will explain how to configure a USB Flash Drive / Memory Stick so that you can run a keylogger within just a few seconds of plugging it in any computer.

Clearing the cache on your computer is (usually) a quick and easy way to help speed it up. Deleting those temporary files frees up space, helping you computer run smoother, especially if you have not cleared the cache for a extended period. However, finding the different caches in Windows 8 is a little trickier than in previous Windows systems.

There's really nothing safe about transmitting sensitive information electronically, but even if it gets there safely without being seen by prying eyes, there's no guarantee what happens to it once it reaches its destination. And let's face it, there are some things that you just don't want floating out there forever. So what can you do? Whether you want to send an email, a text, or a link, there are ways to send messages that self-destruct so that once they're read, they immediately vanish. ...

Have you ever seen one of those Snapple machines with the lever coin return? I will show you how to get free drinks or snacks out of this type of machine.

Open your video in Final Cut Pro. Go to Effects>Video Generators>Boris. Then drag the option called Title 3D over your video. Then select Title 3D and go to your controls. Then click on "Title 3D Click for options". Now a new box should be open. Type your text into it. Then, highlight your text and pick the font size, then hit enter. Next, select the font. After that, go to the bottom test menu, and select Drop Shadow. Make the shadow distance 2. For the shadow opacity, turn it up all the way...

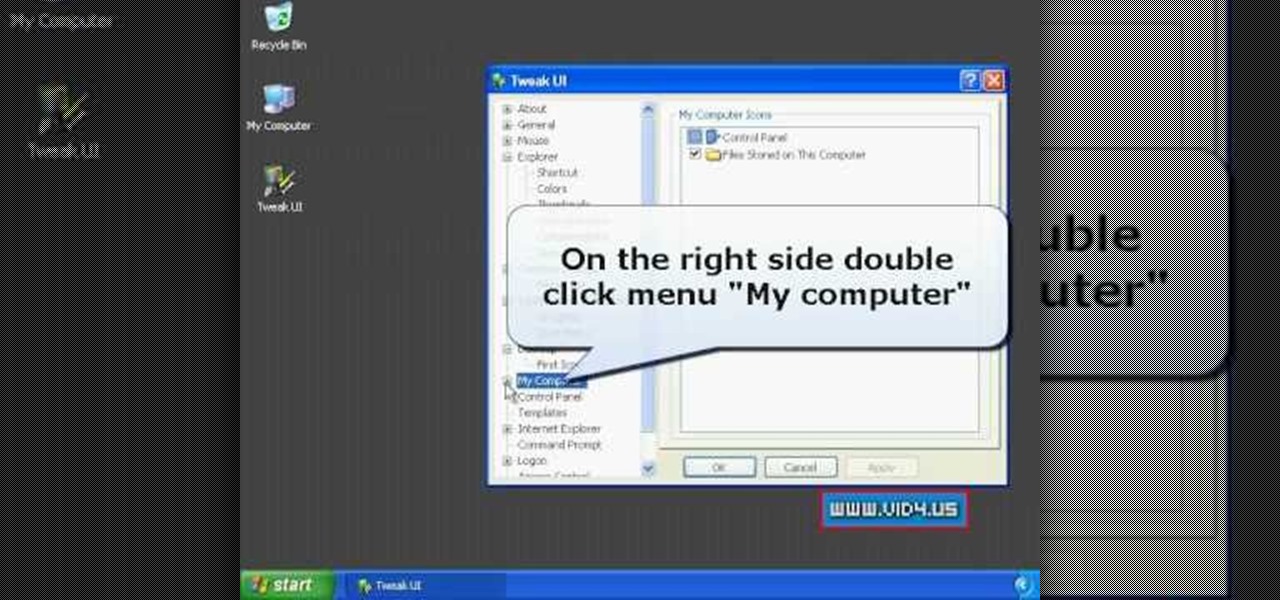
Firstly download the TweakUI into your computer, which is free. Fire up TweakUI and click on menu "Explorer", uncheck menus: "Allow help on start menu"; "Allow log off on start menu" and so on play with the settings however you like. And select "Light arrow", next click on "Thumbnails" menu and drag the slider all the way to the right, increase the size of thumbnails to 120 pixels. Next double click menu "Common Dialogs" and uncheck all three menus. Next double click menu "Taskbar and start m...

In this how-to video, you will learn how to remove the Windows genuine advantage notification from your operating system. First, open my computer and go to the windows folder. Look for the system32 folder and open it. Search for WGAtray.exe. Select both wgatray.exe and wgalogin and delete. Next, go to the run command and type in regedit. Click okay to open the program. Now, back up the registry. Once this is done, it will be safe to edit the registry. Now, navigate to hkeylocalmachine, softwa...

Danny Lipford gives us tips on setting up and maintaining a portable generator. Set-up usually includes assembly of things like wheels and handle kits. Most portable generators come without oil so you will need to add it. Be sure to check the owner’s manual for the proper type of fuel to use.

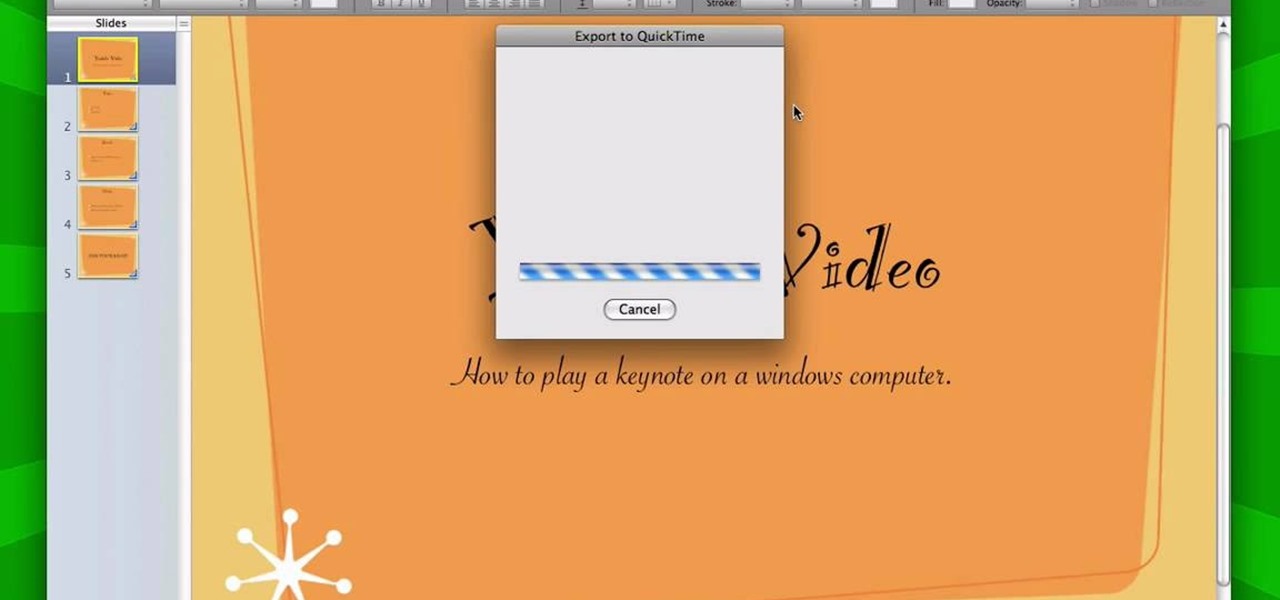
It is a great video tutorial about how to create a keynote presentation to run on a windows platform. After opening the keynote presentation, click on file menu and open up the export window. This window shows different file formats and types. By using this we can export a quick time movie, an html, PDF, images, flash or a PowerPoint presentation file.

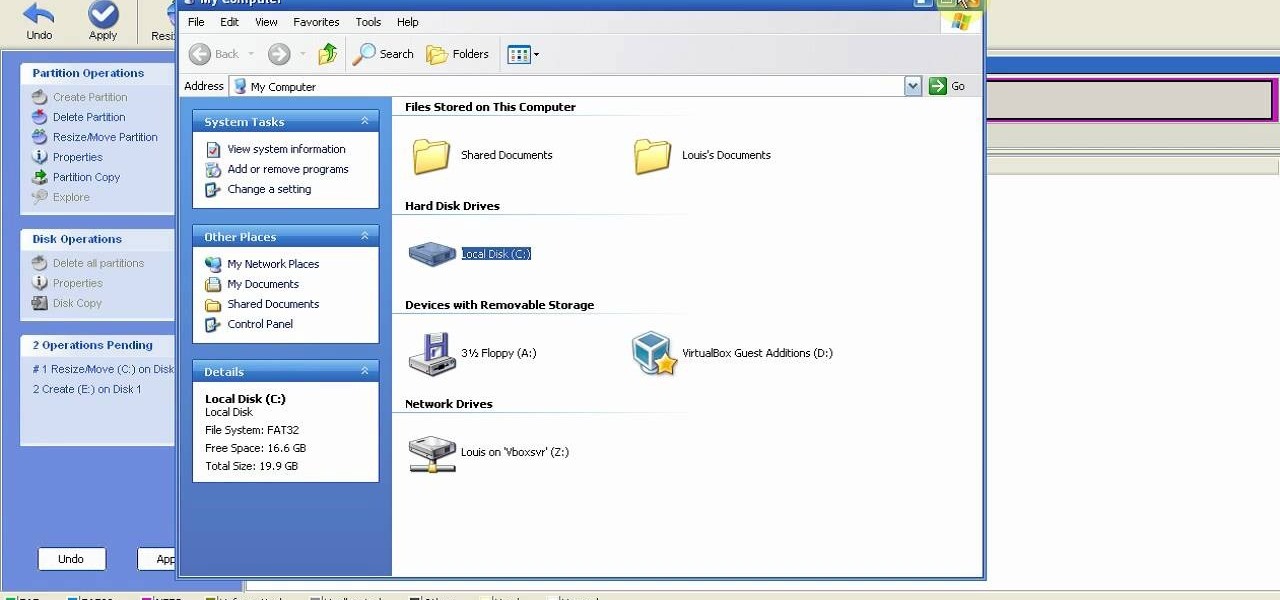
This is a step by step tutorial how to Partition & resize your hard drive with EASEUS. To resize hard drive Open EASEUS Partition Manager. Click on the drive you want to resize. Then click Resize/Move. Go to the end and left-click with your mouse dragging in the direction you want to go. In the display you can see the size that's being created. When you have the size drives you want, just stop and click OK. If you shrunk one drive you can now create a new drive using the unallocated space. Th...

Accidents are the worst. They're costly, time consuming and an all around pain in the butt. Rear-end collisions are among the most common types of accidents on the road. Take these simple precautions to avoid a rear-end collision.

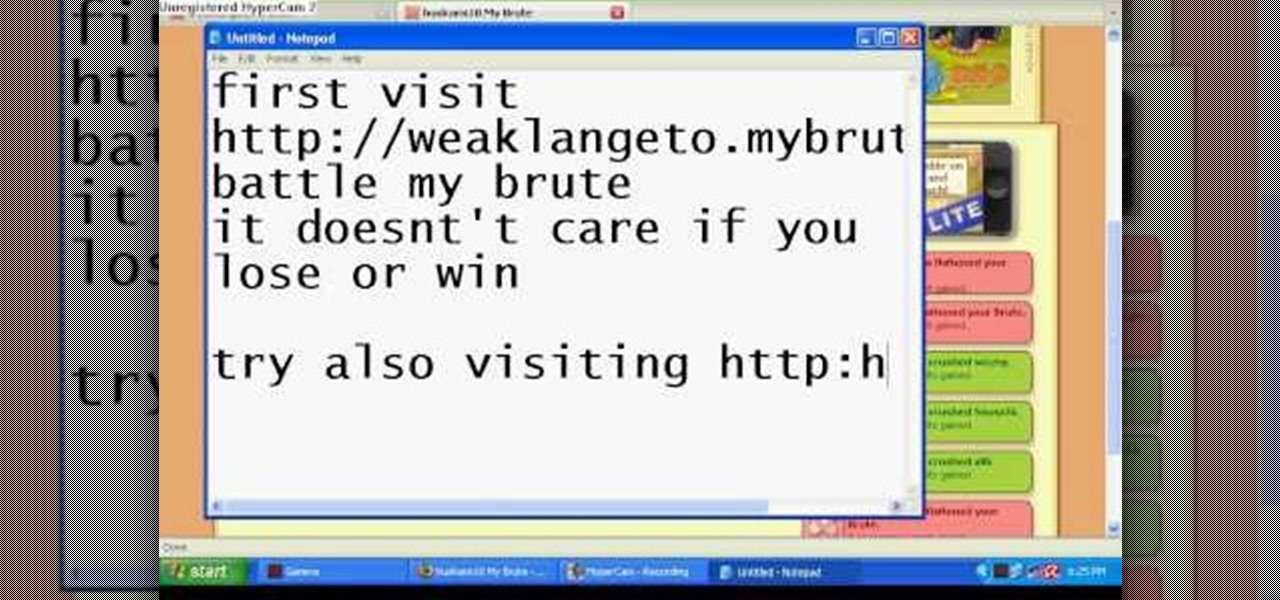
Hack mybrute with this mybrute cheat. MyBrute hacks, cheats, tricks. Watch this video tutorial to learn how to hack a wolf or bear in MyBrute (07/26/09). Without Cheat Engine!

Though most warts disappear eventually without treatment, it's still useful to know how to prevent these unsightly marks from ever popping up. Watch this video to learn how to reduce your chances of warts.

A CNC router machine is probably the most useful tool a hobbyist can own, but the price for a CNC machine on the market is way more than the average hobbyist is willing to spend. You can build your own CNC with very basic tools, little knowledge of machinery, mechanics, or electronics, but be warned, these machines are inherently dangerous, so wear the proper protection and use common sense. At the very least, read the instructions and precautions on every tool you use.