
How To: Wardrive with the Kali Raspberry Pi to Map Wi-Fi Devices
Surveying a target's Wi-Fi infrastructure is the first step to understanding the wireless attack surface you have to work with.


Surveying a target's Wi-Fi infrastructure is the first step to understanding the wireless attack surface you have to work with.

In our first part on software-defined radio and signals intelligence, we learned how to set up a radio listening station to find and decode hidden radio signals — just like the hackers who triggered the emergency siren system in Dallas, Texas, probably did. Now that we can hear in the radio spectrum, it's time to explore the possibilities of broadcasting in a radio-connected world.

Windows 10 is officially here, and frankly, there's a ton of new features in Microsoft's latest operating system. From the return of the Start menu to the new Edge browser, Windows 10 can take some getting used to.

Apple AirTags are super helpful for keeping track of your keys, backpack, and other frequently misplaced items, but there are some pretty clever things you can do with them beyond finding regularly used stuff.

Facebook's annual earnings call on Wednesday didn't come with any big surprises, that is, if you took everything at face value.

When Microsoft unveiled Mesh a couple of weeks ago, the move revealed a major part of Microsoft's next steps toward dominating the augmented reality space, particularly with regard to enterprise customers.

While obvious, it's a lot more difficult to hack into a locked computer than an unlocked computer. As a white-hat hacker, pentester, cybersecurity specialist, or someone working in digital forensics, there's an easy solution — make it so that the computer won't fall asleep and lock automatically in the first place.

The iPhone 12, 12 mini, 12 Pro, and 12 Pro Max all have positive coverage surrounding their refreshed design, camera upgrades, and 5G connectivity. One piece of negative press you might've seen, however, is about the charger. Specifically, that there's a Lightning to USB-C cable in the box but no power adapter. That means you'll need a charger, and we've got some good recommendations for you.

In the tech world, our data is always under attack. When you download and install a new app, it can be difficult to know what information the app is actually accessing. Thankfully, a new emphasis on privacy in iOS 14 changes the game, exposing more of what your apps want access to — and even changing some behavior along the way.

If you're ever in a situation where you need to take a peek at the wireless spectrum, whether it's for Bluetooth or Wi-Fi devices, there's a fascinating Python 3-based tool called Sparrow-wifi you should check out. It's cross-platform, easy to use, and has an impressive GUI that shows you the signal strength of nearby devices.

While Apple and Samsung have started integrating depth sensors into the iPad Pro and Galaxy smartphones, more advanced AR experiences are arriving for standard smartphone cameras on Android devices.

A rather exciting development has recently surfaced in the jailbreaking scene for iPhone. The Checkm8 bootrom exploit was shown off to the public by axi0mX, which made way for the undefeatable Checkra1n jailbreak tool. With it, you can freely jailbreak a variety of older iPhone models without any restrictions. The success rate is quite high, too, when compared to other jailbreak methods.

For many of us, our work phone and our personal phone are one and the same. Just any old phone isn't going to cut it when you need to meet a deadline — a phone with built-in features that make it easier to get things done is almost a must.

Over the past decade, Marvel Studios has been a dominant force at the box office, raking in more than $21 billion dollars. Averaged out over that span of time, the yearly earnings of those movies outweigh the gross domestic product of some countries.

While photography usually gets all the love, our phones have gotten really good at capturing video. Think about it — when was the last time you needed a camcorder for a vacation? With mobile cameras getting better each year, we're now at a point where smartphones can be used for pro-level videography.

Streaming movies and TV shows on phones is more popular today than ever, but what about when you're on a plane, have a limited data plan, or will be in a no-service area? You'll want to download your movies and TV shows instead. While Netflix is excellent, you can't rent or download most of the latest movies and TV series. What you need is an app that lets you do just that.

Windows 10 and macOS have poor reputations when it comes to customer privacy and user policies. Our hacking Windows 10 and hacking macOS articles might make it seem like a reasonably secure operating system doesn't exist. But I'm here to tell you that there is a viable alternative that could provide some sense of security and trust.

No more carrying around heavy laptops and thousands of Linux Live CDs and USBs to always be ready for pentesting on the fly!

Did you know Kali 1.0.8? You probably did, and you probably know about the EFI boot option that has been added.

Rumors about the 2022 iPhone series stirred well before the iPhone 13 models were even released. While Apple remains quiet on the next big iPhone, as it always does, we're seeing more and more leaks and reveals for the iPhone 14 series as we lead up to a likely fall release.
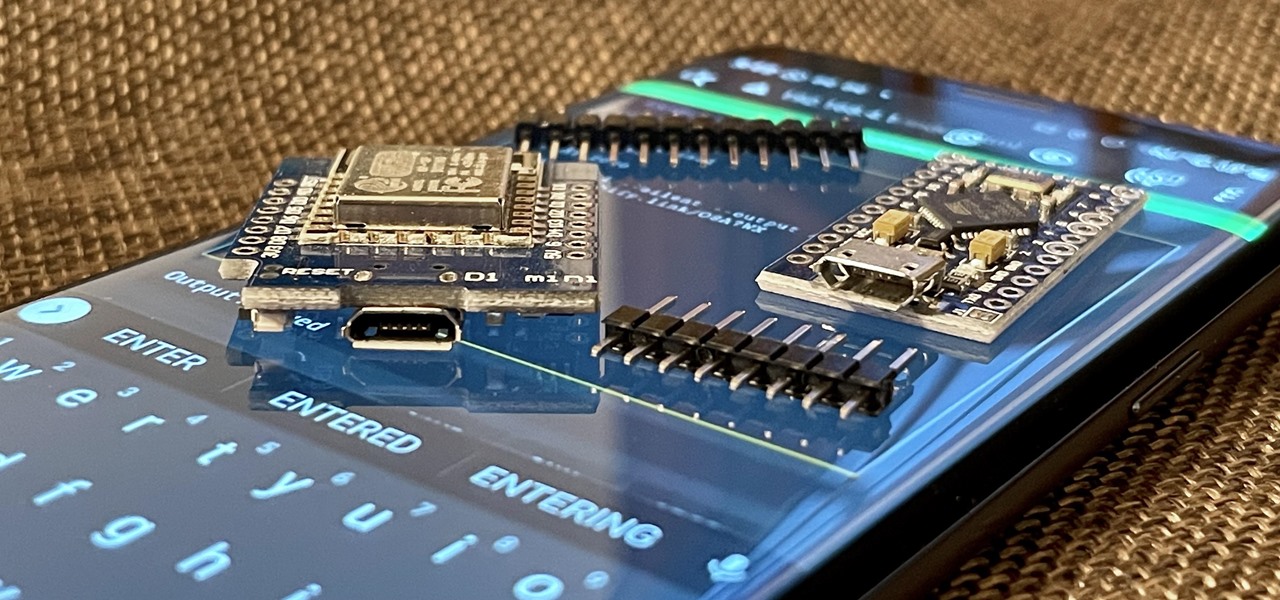
With just two microcontrollers soldered together, you can inject keystrokes into a computer from a smartphone. After building and programming the device, you plug it into a desktop or laptop, access it over a smartphone, and inject keystrokes as you would with a USB Rubber Ducky.

A dead man's switch is a fairly simple concept. If you don't perform a specific task before a set amount of time, it'll perform a specific action you set. They can be handy not just for hackers but for everyone who wants to protect themselves, someone else, or something tangible or intangible from harm. While there are more nefarious uses for a dead man's switch, white hats can put one to good use.
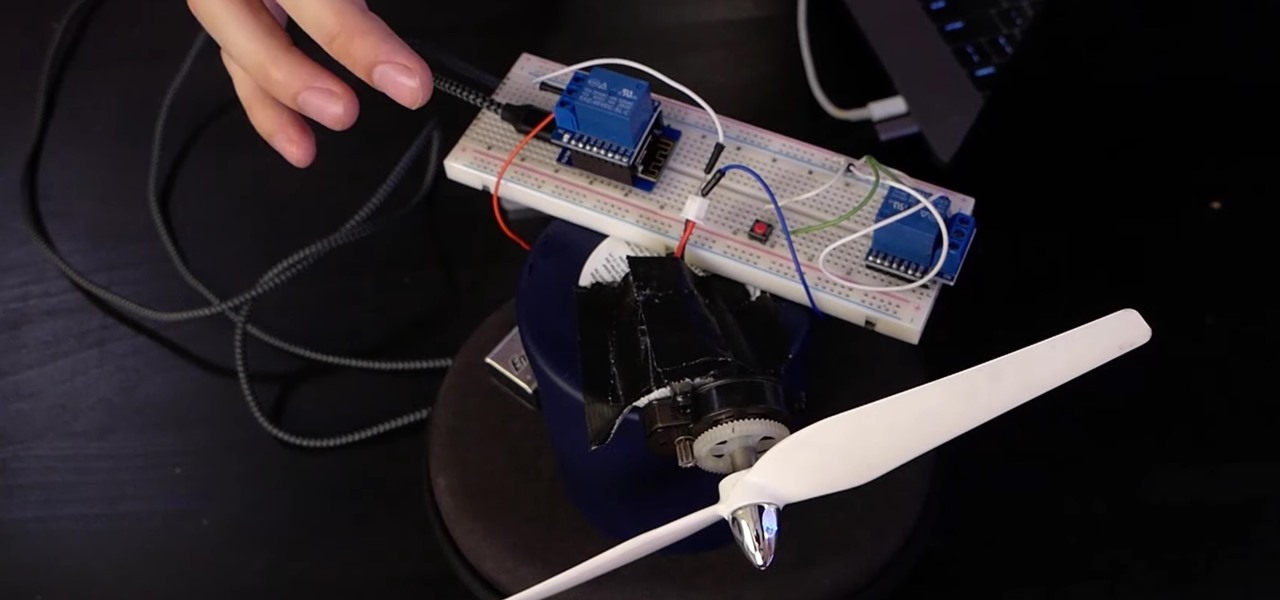
If you want to control electronic devices, such as a relay or motor, you can do so using MicroPython with an ESP8266 and web browser. Usually, you'd program an ESP8266 using Arduino, but C++, which Arduino uses, is not always the easiest programming language for beginners to learn.

Smartphones are vital travel companions. While you're on the go, they connect you with loved ones back home, help you find tickets and passes for tourist attractions, and make it easy to find your way through foreign roads — but even the most powerful smartphone could use help from travel accessories.

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.

Airgeddon is a multi-Bash network auditor capable of Wi-Fi jamming. This capability lets you target and disconnect devices from a wireless network, all without joining it. It runs on Kali, and we'll cover installing, configuring, and using its jamming functionalities on a small, inexpensive Raspberry Pi. When done correctly, it will deny service to a wireless network for up to several blocks.

Besside-ng is the hidden gem of the Aircrack-ng suite of Wi-Fi hacking tools. When run with a wireless network adapter capable of packet injection, Besside-ng can harvest WPA handshakes from any network with an active user — and crack WEP passwords outright. Unlike many tools, it requires no special dependencies and can be run via SSH, making it easy to deploy remotely.

Android comprises an entire ecosystem of apps, games, functions, and features, so it would only make sense that it has its own lexicon. Words, phrases, and acronyms that didn't exist ten years ago are now used in an off-the-cuff style by developers and support technicians across the web.

Check out this computer hardware tutorial from Dummies.com. This tutorial is made for PCs. Upgrading your laptop computer's memory is a simple, do-it-yourself process. This video shows how to open your notebook and install more RAM to give your laptop a performance boost. Upgrade memory or RAM on a laptop.

Whether you just got a brand new laptop or you've had an old notebook for several years, it's in your best interest to maximize your laptop battery life so you get the most out of your computer.

This video demonstrates how to connect your laptop to the internet from a WiFi spot. From the people who brought you the Dummies instructional book series, brings you the same non-intimidating guides in video form. Watch this video tutorial to learn how to connect your laptop to the internet from a WiFi spot, For Dummies.

How to safely clean your laptop computer. Watch now! Clean a laptop.

You can utilize your television to display your videos and other files that are on your laptop. Connect your laptop to your television.

This video demonstrates how to secure a laptop. From the people who brought you the Dummies instructional book series, brings you the same non-intimidating guides in video form. Watch this video tutorial to learn how to secure a laptop, For Dummies.

The internet is something most people rely on, so when you buy a used laptop without a wireless card or yours needs to be replaced, it's easier to do it yourself. Having someone else do it can cost more than you think, so here's an easy way if you own a Dell Inspiron E1505.

Jeremy at GamerTell shows us how to connect our X-Box 360 to the internet VIA Windows Vista and a Laptop Computer that is already connected to a wireless network. First we have to connect your laptop to your X-Box 360 using an Ethernet cable. Now we will turn on the Xbox 360. Make sure you are on the correct TV Input or channel. Now go to your laptop and Click on the start button on your laptop and find control panel. Once your in control panel select Network and Internet. Now we will select ...
In this video, Sky Van Iderstine will tell you how to get your IP address e-mailed to you every time it changes by using a freeware program, Wimp. With this information, you can then track your stolen Mac laptop or even desktop's location using www.ip-adress.com (the "adress" is not a typo.) Imagine the look of the police officers when you show them the satellite picture of your suspects location! Locate your stolen Mac laptop using Wimp.

Not sure I quite understand the point of modding two Powerbooks into a snowboard, but I admire the energy behind the project. Very rough translation via YouTube:


Wish you had $1000 to throw down for a projector? Well, if you have an old laptop lying around instead, here is a simple way to cheaply build your own digital projector. Lifehacker posts a HowTo excerpted from DIYer Randy Sarafan's 62 Projects to Make with a Dead Computer: (And Other Discarded Electronics).