With the latest version of ARKit and a new set augmented reality development tools set to arrive this Fall with iOS 13, Apple has taken an unprecedented step in recruiting Chinese developers to fill the App Store with mobile AR apps now, likely with an eye to the future.
Augmented reality has taken the advertising industry by storm, but the technology has a steep learning curve. Luckily for advertisers, Unity is here to flatten the curve a bit.

Perhaps it's a coincidence that the Vuzix Blade smartglasses look like the sunglasses that a police officer would wear, but a new partnership with an AI software company makes the wearable a perfect fit for law enforcement.
Apple released the third public beta for iOS 12.4 on the afternoon of May 28. The update arrives roughly three hours after Apple published 12.4's third developer beta, and eight days after 12.4 public beta 2. At this time, it seems beta 3 is a minor update for 12.4, which itself is a small upgrade to iOS 12 as a whole. We expect iOS 12.4's shining feature to be Apple Card support.

Apple just released the first version of the iOS 12.1.2 beta to developers on Monday, Dec. 10. The update arrives mere days after the Cupertino-based company seeded the official version of iOS 12.1.1 to the public, itself of which had been in beta development since Halloween.

With developers chomping at the bit to play with ARKit 2.0, Unity has updated its ARKit plugin to enable access to the new augmented reality superpowers of the toolkit.

On the one year anniversary of the introduction of ARKit, Apple is planning to reveal major updates its augmented reality toolkit for mobile apps at its Worldwide Developers Conference in San Jose, California next week.

Just weeks after officially launching its mobile augmented reality toolkit, Google can now claim one of its first Android and ARCore app exclusives with the Curate app from Sotheby's International Realty.

Remember that scene in Tim Burton's Batman where the Joker and his goons defaced dozens of priceless works of art? A collective of digital artists have found a less criminal, more geeky way to do the same thing.

Accused of violating whistleblower and age discrimination laws by its security director, Magic Leap has taken an internal situation to the US District Court to clear its name of the allegations.

If you ever thought the Snorlax in Pokémon Go should be taller, and you have an iPhone compatible with ARKit, get ready to look up.

It appears that the new AR app from LEGO is inching closer to release.

Until Star Wars Jedi Challenges arrives in November, a forthcoming ARKit revision of HoloGrid: Monster Battle from Tippett Studios and Happy Giant, might be the closest most Star Wars fans can get to playing the HoloChess game from the movie.

IKEA won't be alone among ARKit apps for visualizing home décor and improvements when iOS 11 arrives next week.

Admit it — many of us have not gotten in the Uber's we've requested. Sometimes, you just need to get someone else a cab that you're not going to be going with. No biggie ... but your friend doesn't have any connection to Uber or the driver, which can be a little awkward. Uber is addressing this slight issue today, with an update that allows you to officially request Ubers for others.

In Indianapolis, two-year-old Kenley Ratliff has passed away from what is suspected to be Rocky Mountain spotted fever (RMSF), a tick-borne illness. The young girl fell ill with a fever, and just a week later, passed away. Now her family and doctors are looking into the cause of her death and warning others to check themselves for ticks this summer.

The common thread between this week's Brief Reality stories is that augmented reality is beginning to prove its worth as a technology that improves workflows and processes. From customer service to healthcare to manufacturing, augmented reality is helping companies improve productivity.

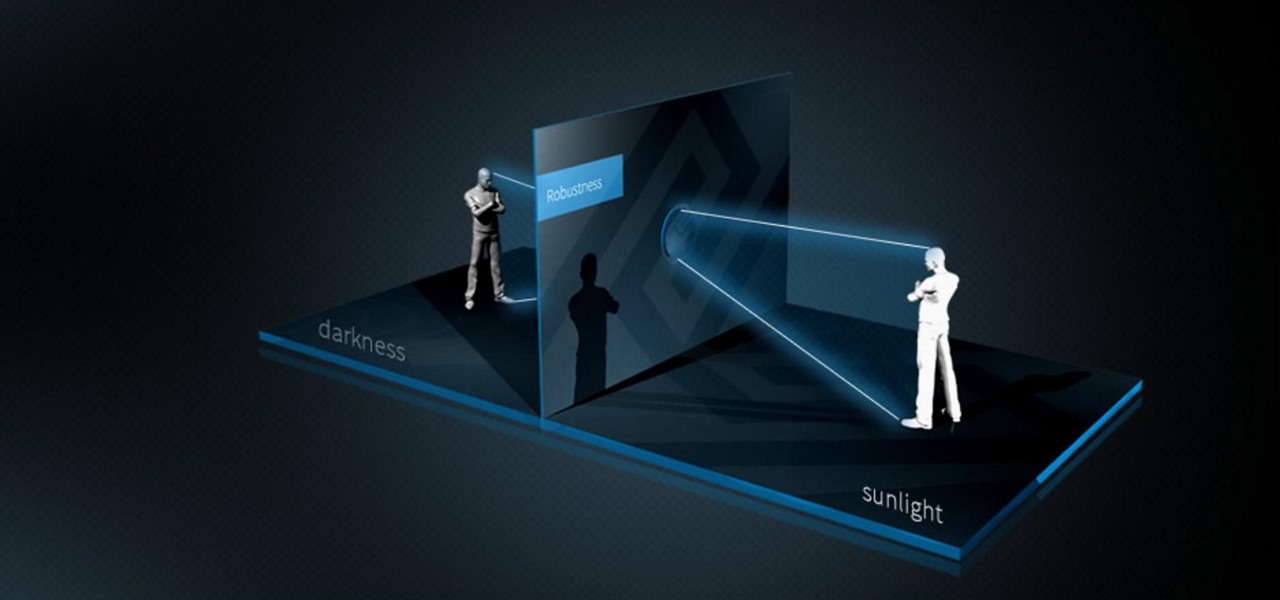
Meta's long-awaited Meta 2 development kit finally began shipping in late-December last year, after having been delayed about six months. While very few have received a dev kit at this point, some more information about the headset has just been announced; Depth-sensing technology from pmdtechnologies is included in the dev kit headset.

Presented by Apartments.com When looking for a new apartment, it's hard not to notice the improvements (on large and small scale) needed prior to moving in. While your landlord may be taking care of new carpeting, cleaning the central air vents, and fresh paint on the walls, there may be some additional improvements on your list that you can take care of on your own. Here are five quick improvements you can check off your list before the big move.

Android's auto brightness feature was recently updated, and as of version 5.0, a new "Adaptive brightness" feature was added. This allows users to set a preferred overall brightness level, but still have the ambient light sensor adjust the backlight accordingly.

In previous posts here, I have pointed out that hackers are in high demand around the world and in nearly every industry. Every military and espionage unit of every country is trying to hire high-quality, experienced hackers as fast as they can to hack their adversaries' computer systems in order to gain a strategic advantage and to spy.

If you purchased your Nexus 5 from Google Play in the United States, we've got great news for you. In an unprecedented move, Google has started offering customers the chance to exchange their broken or water-damaged Nexus 5 for a new or refurbished unit—free of charge.

If you read my article on the OSI model, you got a good overview on communications from that model's perspective, but how does that relate to TCP/IP? We're going to take it a step further, getting into the idea behind the two address concept. How does an IP address and a MAC address work together? If you want to hijack sessions and all sorts of lulz like that, you need to understand these concepts. Let's get into it, mates!

Apple just released iOS 13.5 for public beta testers today, Monday, May 18. The GM (golden master) for iOS 13.5 arrives just three hours after Apple released it to iPhone developers, and 12 days after the release of iOS 13.5 dev beta 4.

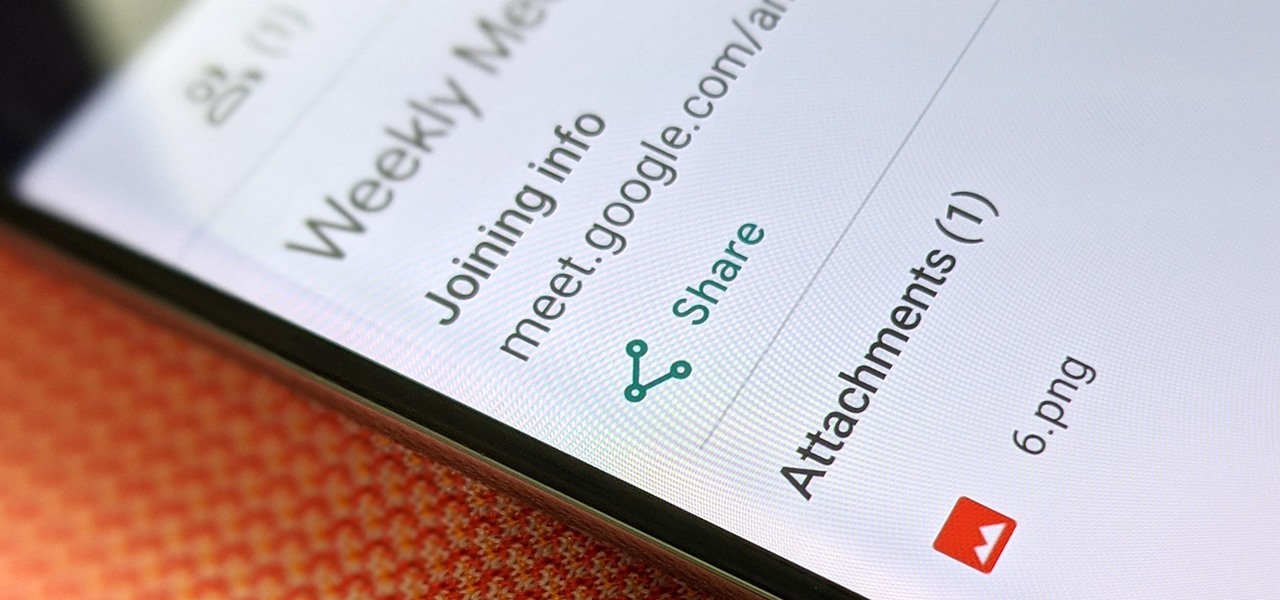
Google Meet might not have virtual backgrounds like Zoom, but it hits all of the other basics, from hosting many multiples of video participants to sharing your screen, that you'd expect from a robust video conferencing platform.

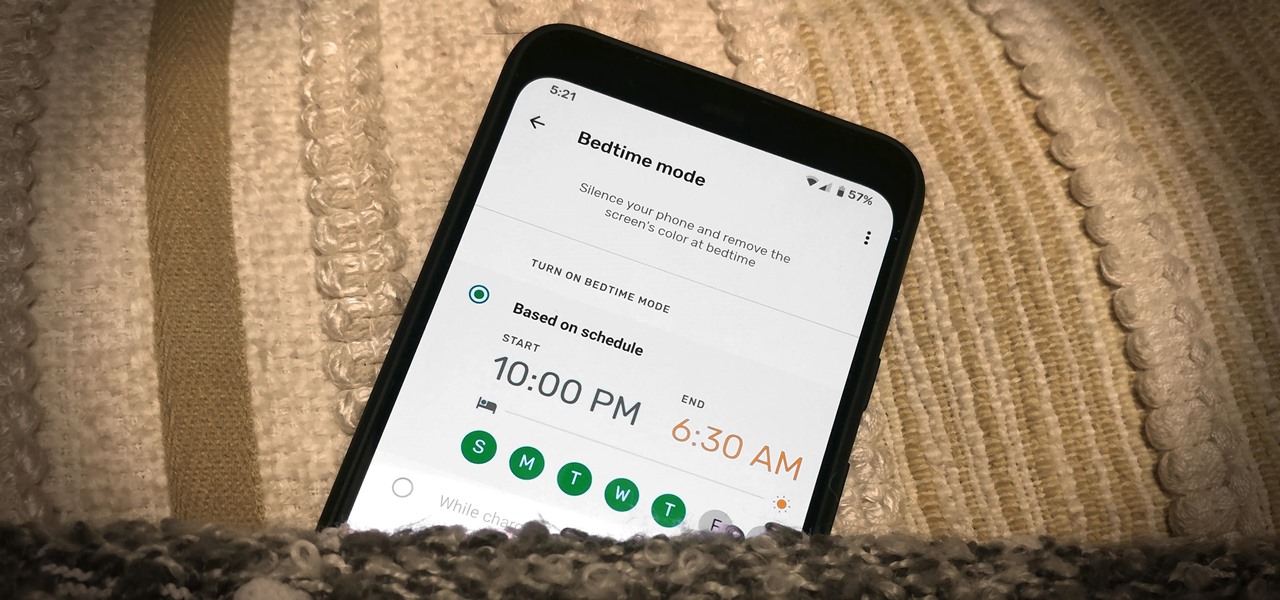
Apple added a Bedtime Mode to its Screen Time tool for curbing smartphone distractions. Google's version of Screen Time, called Digital Wellbeing, actually predates Apple's, but a recent update is finally bringing in Bedtime Mode.

It wasn't too long ago that the power menu for stock Android didn't offer much beyond turning the device off, but Google has steadily added more functions, like capturing screenshots and provisioning access to emergency information.

In his famous 1996 "Content is King" essay, Bill Gates predicted that content is where tech companies will make money on the Internet. The adage clearly holds true in the current phase of augmented reality experience.

It's the holiday season, and the tech industry is giving consumers several AR products and apps as gift-giving options.

Smartglasses from Apple have become the holy grail of augmented reality, and 2020 has been the rumored time horizon for the product's arrival for the past two years. The latest analyst report sheds more light on its potential debut next year.

It happens to all of us. You're ahead of the pack, clearly in first place, when someone launches the Spiny Shell (aka, the blue shell). It catches up and circles you before crashing into your kart, and there's seemingly nothing you can do about it. But what if I told you there are two ways to avoid this fate in Mario Kart Tour?

If waveguide display maker DigiLens has its way, enterprise businesses and consumers will soon be able to purchase smartglasses for less than $500 — as long as they can supply their own computing and battery power.

Less than three weeks after Rovio Entertainment announced the game, the augmented reality adaptation of Angry Birds is now available for the Magic Leap One.

Though not as popular as Super Mario or Zelda, Konami's Contra nevertheless remains as one of the greatest titles that helped put Nintendo on the map. This retro shooter is set to make a comeback, and has been soft-launched in select Asian countries ahead of a worldwide release. Of course, you can try the game yourself right now, thanks to a nifty workaround.

While it has been slower to arrive than a walker limping through thick Georgia mud, location-based augmented reality game Walking Dead: Our World finally has a confirmed launch date: July 12.

Last week's Augmented World Expo felt like a distant memory by this Monday, as Apple unveiled ARKit 2.0 at its annual Worldwide Developers Conference. Certainly, this news would overshadow anything augmented reality this week as it nearly eclipsed AWE when early reports leaked of the toolkit's new superpowers.

The premise of Jurassic World revolves around splicing genes to create new dinosaurs, so it is fitting that the location-based AR game is a clone of Pokémon GO merged with the DNA of the Jurassic Park franchise.

Despite numerous reports announcing its stateside arrival, "Final Fantasy Awakening" has yet to show up in the iOS App Store, much to the chagrin of millions of fans in the U.S. Unfortunately, the game seems to be stuck in soft-launch limbo, with no word as to when it'll land stateside. With a little hack, however, you can give this immersive game a try right now.

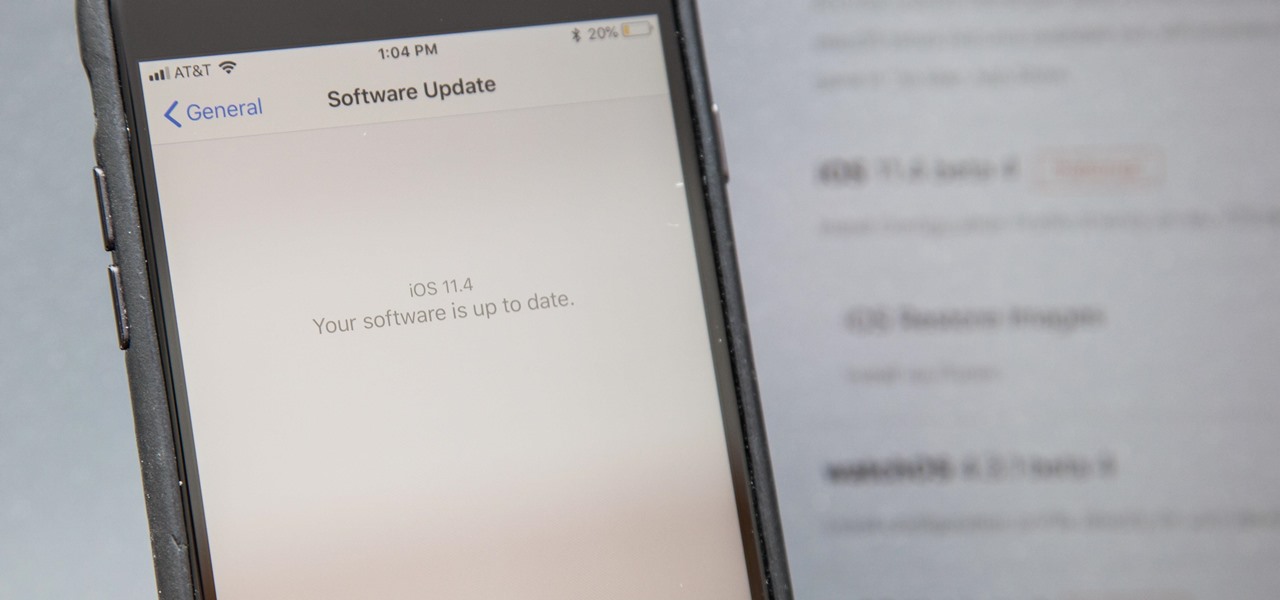
Apple released the fourth developer beta for iOS 11.4 on Monday, May 7, followed the next day with the public beta release. This update arrives just six days after the company seeded beta 3 to users, which fixed an 11.3 issue with 3D Touch, among other various bugs.

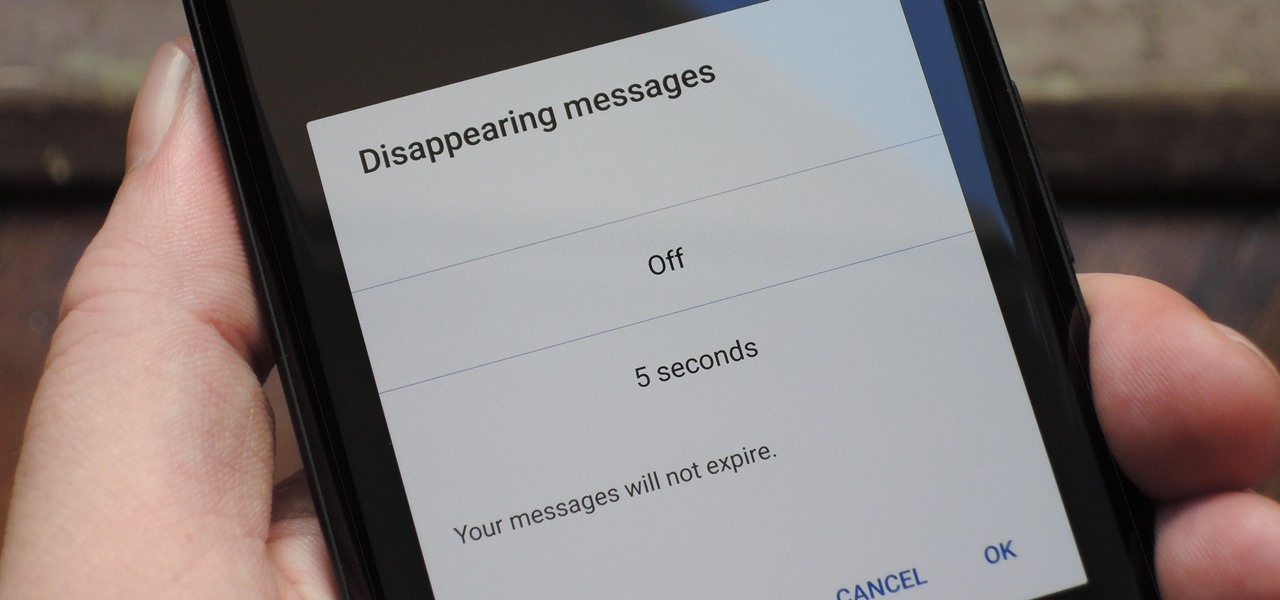
With Signal's class-leading end-to-end encryption, you can be sure your messages will remain secure as they travel to the recipient. However, once the message arrives, its privacy is completely dependent on the receiver, who could share it anywhere if they wanted. To patch this vulnerability, Signal added disappearing messaging.