Ever find a really cool article on the web that you'd like to read next time you are out and about, waiting in line or riding the bus? Watch this video to learn how to use iCloud to share links between your computer and your iPhone.

This video shows Thomas Maiorana of Boot y Amor follows up to his CRAFT: 07 article with tips on how to make your own shoes, as well as modify existing shoes.

The experts at ZIPS Dry Cleaners explain what to do when you get a stain on a dry-clean-only article of clothing.
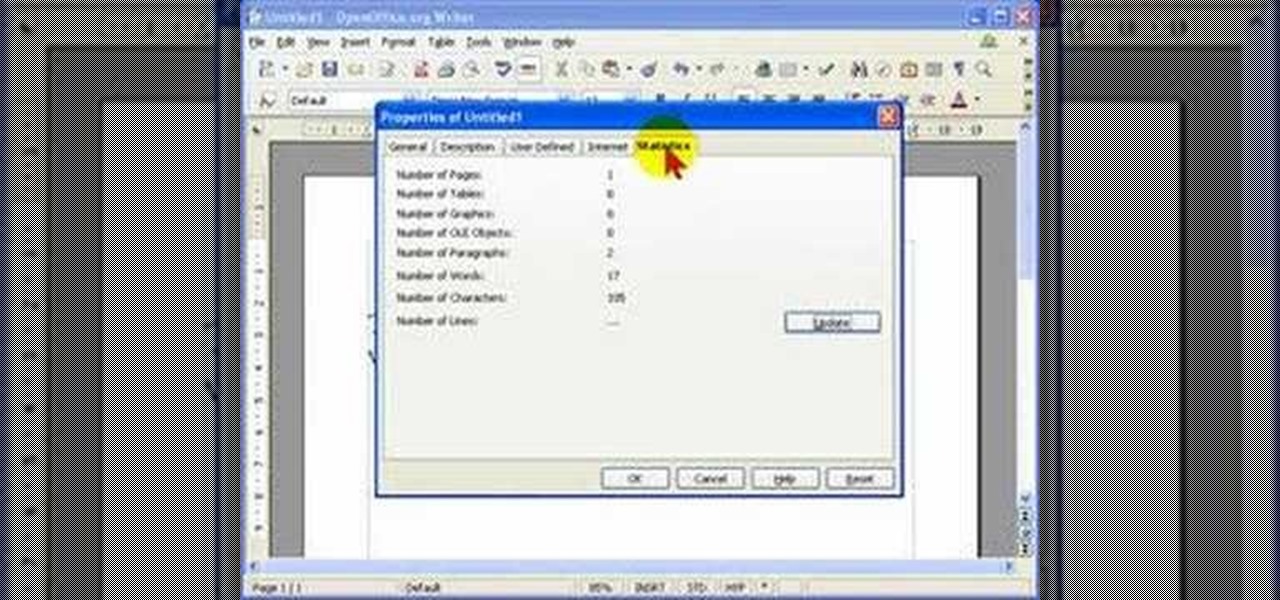
When creating word processed documents, there are often times when it is important that you know exactly how many words you have written - for example, student writing their dissertation, and journalists writing articles.
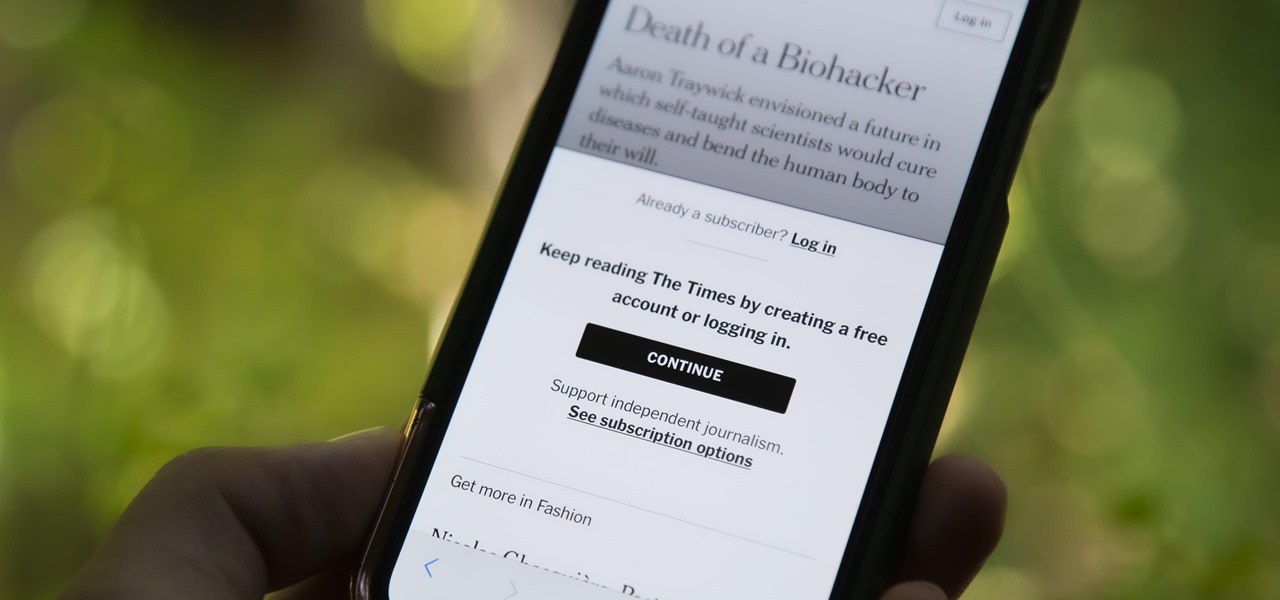
Paywalls make it nearly impossible to access certain content unless you have a subscription. It's a practice that many news organizations and other online publications use to increase revenue: The New York Times, The Wall Street Journal, Vanity Fair, Wired, and so many more. But just because a paywall is in place doesn't mean you can't get around it on your iPhone.
Video: . This video explains how to install Android OS on a PC using VirtualBox. How to install Android OS on a PC Using VirtualBox.

The Dark Knight Rises. The Amazing Spider-Man. The Avengers. Halloween is a few weeks away and all we're going to see are these same ol' superhero costumes. It's like that every year, due to the immense popularity of comic book films by DC and Marvel.

Chlorine gas is a very useful oxidant, which was first introduced as a toxic weapon by the German Army. Even today, it's still used as a weapon, most recently in the Iraq War by insurgents. But chlorine gas has more useful (and less lethal) applications, and if you want to learn how to make some at home, NurdRage has the answers.

In this video tutorial, you'll learn how to create a $30 steadicam for your Apple iPhone 4. The rig consists of a three-axis gimbal with a weight at the bottom.

One of American Apparel's most famous articles of clothing for women is their Le Sac dress, which is no ordinary dress. It's simplistic look mocks it ingenious design, which can be shaped, formed, mutated, tie, and tucked in at least TWELVE different ways to create a different dress for each day of the week. The Architectural Mini look is just one of the ways to style it, and this video shows you exactly that. Use this art deco style for a sexy, architectural inspired halter look.

Can you believe this dress? American Apparel have outdone themselves again! A dress that's not just "one" dress, but at least "eight" dresses. The Le Sac dress is a marvelous article of clothing because it can be worn every day of the week… without looking like a hobo. It's a different style each day, with at least TWELVE different styles. And there's even a look for you dominatrices out there, a super sexy and daring S&M style Dominatrix look. See how easy it is!

American Apparel is famous for selling articles of clothing that can be worn in multiple ways. Their latest creation is the Le Sac dress. This dress can be tied and twisted all over the place to come up with TWELVE or more styles! You can wear this outfit every single day and everyone would think you were in something new. So, if you are looking for a sexy, Greek-inspired off the shoulder look, check this official tutorial out for the Grecian look. Learn how to wear your Sac and look amazing.

The fine folks at ITS Tactical made this detailed tutorial on how to make a two-piece lock pick set out of only a few paper clips and using only a multi-tool in the construction. The host begins by demonstrating how to construct the pick, then how to use it on a real lock. It is not as easy as using a real lock pick, but will still work. As the host emphasizes at the beginning of the video, these picks are only to be used in emergency situations, and NOT to break into other people's homes wil...

What's better than one prank? Five pranks! This video from the notorious Kipkay provides five fantastic, funny, and facile pranks to pull off on your friends and family… maybe even your enemies.

We've all seen the breathtaking, colorful photos of the Eagle, Egg and Cat's Eye Nebulae. You may not recognize them by name, but you've seen them, whether in astronomy textbooks, magazines, websites, album covers, or tee shirts. They are some of the most striking photographs ever taken from the Hubble Space Telescope (HST).

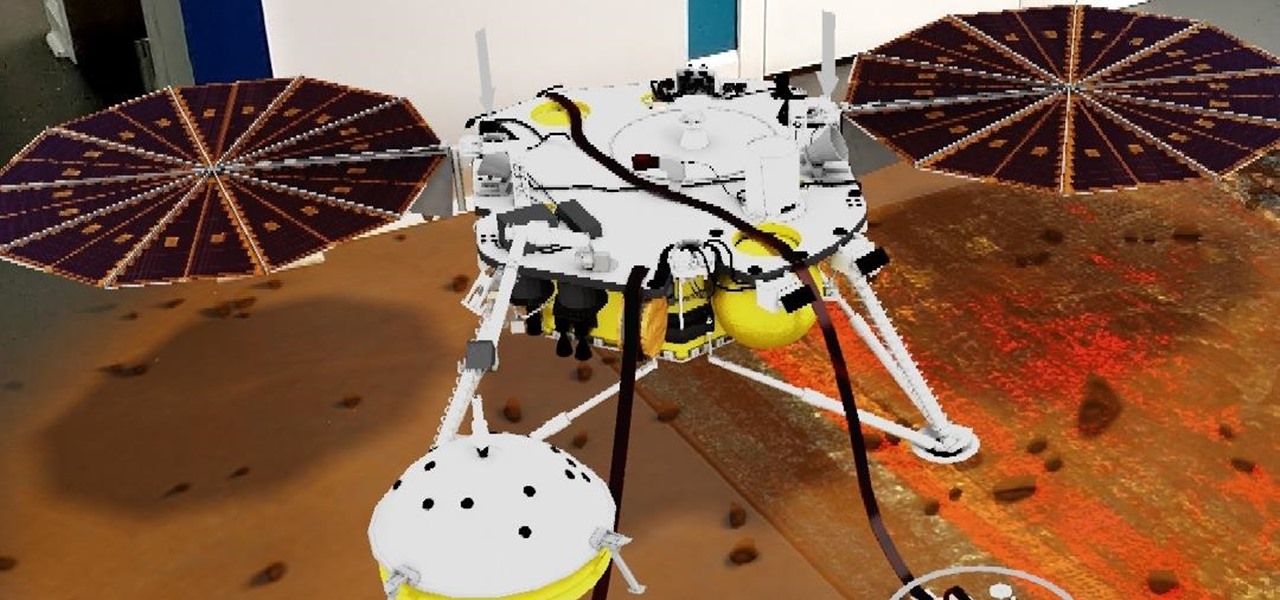
In the latest installment in its burgeoning augmented reality journalism practice, The New York Times is bringing its readers closer to Mars and NASA's latest spacecraft set to travel to the red planet.

The internet is chock-full of fun and interesting content, but there's only so much time in the day for consuming it. That's when saving webpages for later comes in handy. If you don't want your bookmarks and favorites folders to clutter up fast, consider using the "Reading List" feature built right in Safari on your iPhone.

Welcome back everyone! It's been awhile hasn't it? Sorry for being so quiet, but my CCNA courses have really picked up recently. In the last article we covered how to import modules and how we can use them. In this article, we'll actually be covering a module that is essential to the hacking aspect of Python, sockets.

Hello, everyone. Stealth is a large part of any successful hack; if we don't get noticed, we're much less likely to be caught. In these next few articles, we'll be building a shell based on keeping us hidden from a firewall. There are many ways to stay hidden from a firewall, but we'll only be incorporating a couple into our shell. This article will outline and explain these evasion concepts and techniques.

Before we dive into the world of frustration, I first would like to thank whoever of the admins and mods made the folder for Raspberry Pi in the How-To's, thank you. Now with that outta the way, this article is about Metasploit on Raspberry Pi (hence the title). I should say that I ran into a error, but I think I figured what the problem is. First of all this is not on Kali Linux, but on a regular Linux OS. With that said let's open up a terminal and begin.

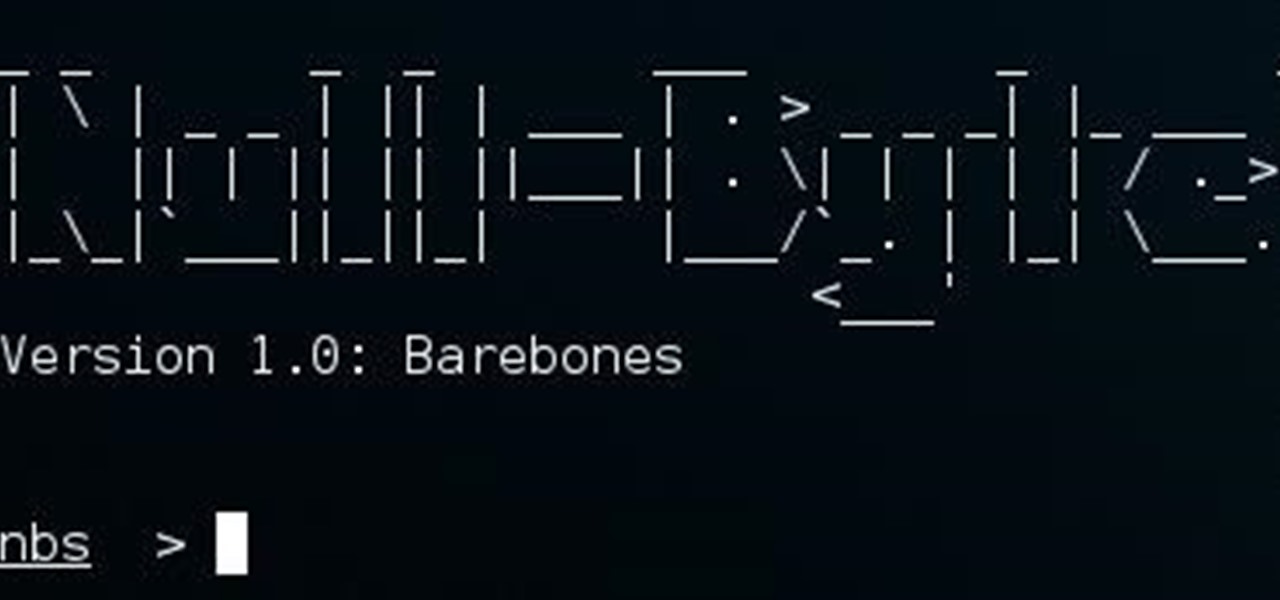
Hello, everyone. If you've been following my recent articles, you'll know that I've been rather busy lately working on a project, a rather large one. I've been working with Pheonix750 and Ciuffy to build the Null Byte suite of tools! I got the green light from our admin a while ago, and we've been developing like mad ever since! I'm very excited to launch this project. So, let's start by explaining what it is...

Windows 10 has so many new features that we couldn't even cover them all with one article. From keyboard shortcuts to revamped search functions and all-new window gestures, Microsoft definitely piled on the fresh functionality in the latest version of their operating system.

Welcome Back !! TheGeeks. SQL Injection (SQLI) Part-1

You must have read news about hackers dumping the data online, recent one was Ashely Madison. It's only the big companies' data, which gets noticed once it is out. There are many other small leaks which don't even get a mention. So this article is the first one of my series which will help you to find hacked accounts. Some of you must already know about this, but this post is intended for the new learners. This also serves as an example of my learning how a good service can be used in other w...

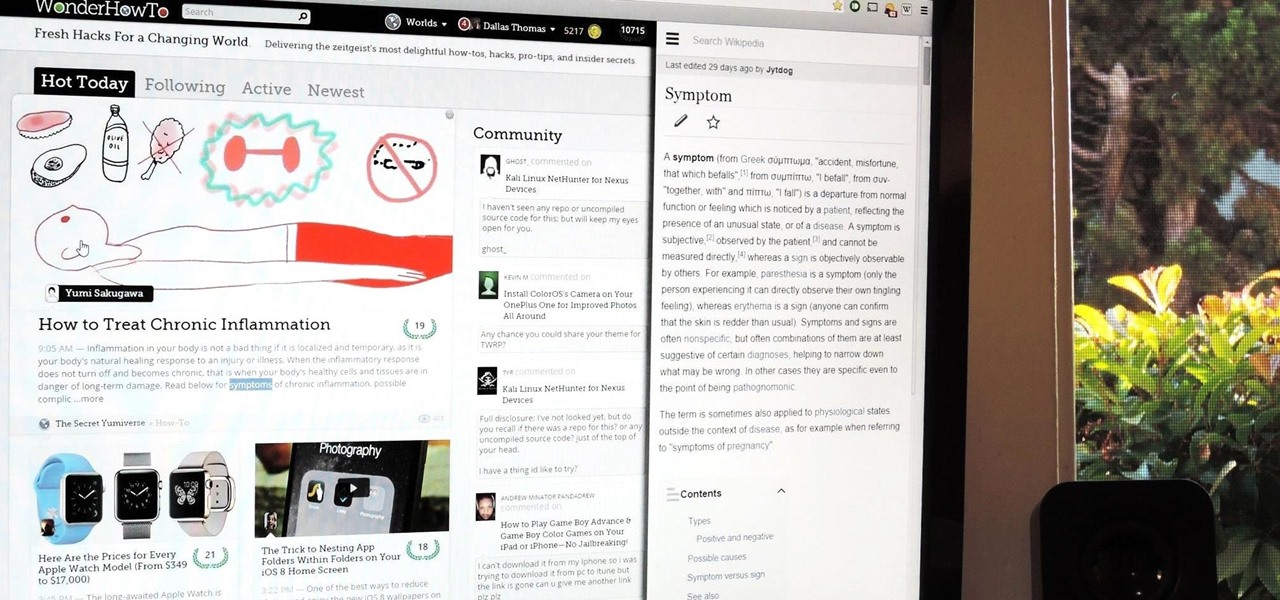
For all of the flak that it catches, Wikipedia is still a great source of information. Contributors take their work very seriously, so the vast majority of information is cited, and the site serves very well as a starting point to learn about a new topic.

We've all had to write an essay or research paper at some point, and undoubtedly the hardest part about it is always the citation, right? If you ask me, it's a huge pain in the arse. Even more so if you're gathering your facts from a huge variety of sources.

Welcome back, my greenhorn hackers! Several of you have you have emailed me asking whether it's possible to install a keylogger on a victim’s computer using Metasploit. The answer is a resounding "YES"!

These days, news papers, online editorials and magazines are filled with news on Iran and Syria. Of course, that is expected, as such sources need to stay current to stay in the game. My concern is that most of these articles talk about what to do about these situations.

Today is the anniversary of George Harrison's death nine years ago in 2001, and we thought a commemorative music lesson was in order. And instead of the usual Beatles fare, we thought we'd show you something a little less known, but just as good— "Handle with Care" by the Traveling Wilburys. Many still aren't familiar with the Traveling Wilburys, despite the superstar musicians involved, but that doesn't change the fact that these guys were awesome!

If you've ever been to a Marie Callender's restaurant, then you know their chicken pot pie is the most popular and most often requested dish. That's because chicken pot pies, while a rather simple concept, contain just enough bready goodness, veggies, chicken, and sauce filling to get you full and way satisfied.

Many, many Americans cannot do a single pull-up. That is just the state of our society. And it means that these people, if faced with a survival situation where they are dangling for a ledge or need to scale a building, are less likely to survive than they could be. This video will teach you how to develop your pull-up motion and techniques to improve your strength and survival ability.

If you want to learn how to play Eleanor Rigby by the Beatles on the ukulele in key g this might be for you. There are only two chords with some variations throughout this song. The first chord you need to play is B minor. The B minor chord consists of a bar on the second fret on the bottom 3 strings and the fourth fret on the fourth string. The next chord in the progression is B minor7. To play B minor7 use the formation for the B chord; however, in this variation you must put your finger on...

Lila from Asian Cooking Made Easy shares her recipe for Singapore Noodles, which she makes with shrimp, chicken, rice noodles and a semi-sweet curry sauce.

This is a demonstration of making a hand tied bouquet.Keep all the required articles nearby on the table.Take a few stems of lemon grass and bind them with a wire to form a single bunch.Tie the aspedestra leaves in a loop with wrapping a wire to the stem.Now take the stems with single flower like movie star roses or carnations or iris or tulips pluck or cut the loose petals.Now hold one of the stems loosely in the left hand,now with the right hand place the second stem so that the flower is o...

This is a tutorial for controlling the Pine tip moth. Identifying and controlling the pine tip moth consists of studying the small plants of pine. The attacks on pine trees is caused by Nantucket pine tree moth found along the Rio Grande Valley as far north as Espanola, it has spread to South Arizona and California by importing grafts from Mexico. The moths are 3/8 inch long reddish brown to grey in color. They attack the main stem of the baby plant and the pines instead of growing vertical g...

In this how-to video, you will learn how to play the song "Ehu Girl" on a ukulele. You will need a tuned ukulele and basic knowledge of chords. The song first consists of the chords C, F and G7. This will be repeated a few times. Move on to the chord progression Am, G, Am, and G. This is the part before the verse. Next, play the chords C, F, G7 into the progression C, F, G7, and Dm. Move on to G, Am, Am, Dm, and G7. The two progressions mentioned are the verses. Once this is complete, move ba...

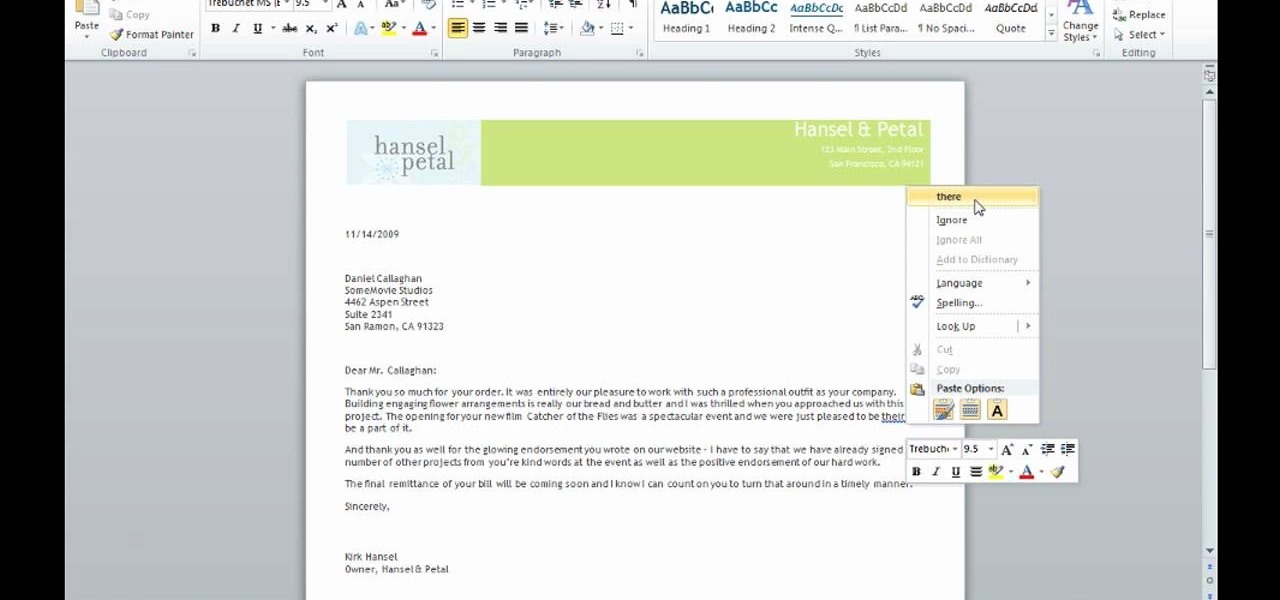
This video tutorial is a quick explanation of the ins and outs of spell and grammar check when using MS Word 2010. One of the main things highlighted in this video is that unlike previous additions, this year's version offers more contextual correction. For example, when the word their was used in an article, it was spelled correctly but used in the wrong context. The spell and grammar checker will underline this to let you know that it is incorrect. If you hit the spell and grammar check but...

Sometimes it can be difficult to find information essential to a citation on a webpage, like an author or a date. Here are some steps you can take to make up for this lack of information.

Projectors can be pretty pricey. 1080p projectors even worse. If that isn't reason enough for you to build your own, then what is? Systm shows you the complete, detailed process of building your own 1080p HD projector, so pay attention and take some notes!

Pixel Perfect is the "perfect" show to help you with your Photoshop skills. Be amazed and learn as master digital artist Bert Monroy takes a stylus and a digital pad and treats it as Monet and Picasso do with oil and canvas. Learn the tips and tricks you need to whip those digital pictures into shape with Adobe Photoshop and Illustrator. In this episode, Ben shows you how to create realistic reflections in Photoshop.