
News: Holographic Fitting Rooms Are Here with HoloLens & Pictofit
If you've been longing since the '90s for the total Clueless experience of virtually trying on clothes, you missed out by not attending London Fashion Week earlier this year.


If you've been longing since the '90s for the total Clueless experience of virtually trying on clothes, you missed out by not attending London Fashion Week earlier this year.

The HTC Vive and Valve's SteamVR make for one of the more compelling virtual reality experiences, mixing in real-world motion tracking with the immersive headset. But third-party manufacturers couldn't tap into the Vive's full potential and make creative new peripherals—until now.

I fry foods a lot. A LOT. We're talking wings by the dozen here. As a result, I go through a ton of frying oil. Now, frying oil isn't the most expensive ingredient out there, but it adds up when you fry regularly. Of course, I always reuse my oil, but straining it can be a huge mess and it gets to a certain point where enough is enough. It's time to start fresh.

You might not think a mixed reality headset could help kids eat their vegetables, but that's the exact premise behind Habit.at—the app that won the "Social Good" category at the 2016 HoloHacks competition in Los Angeles.

In Italian, the word affogato means "drowned." Kind of a morbid name for such a delicious goodie, right? But there's a reason it's called that.

If you're standing in a foreign city, surrounded by signage in a language you don't understand, you won't suddenly be able to read it. But with a clever feature in Google's Translate app, your smartphone can.

This is my first article on here, it's based off of a project that I'm working on at school which is on three ways to bypass windows user password's. If all goes as planned and you all would like I'll work on part two and part three and post them as soon as I can. I do have to give credit to Puppy Monkey Baby and The Defalt, both of whom are my classmates at college and have helped me with writing this article.

What's up guys? Welcome to a sort of general walkthrough on how one might approach a reversing and analysis on a crypted malware. This is by no means a universal technique so don't assume that this will occur in every scenario, it's more of a demonstration than anything really.

Welcome back, NB community, to my series on sorting. I introduced in my last article the concept of complexity. When I say complexity, I'm talking about time complexity.

Hello ladies and gentlemen, I'm back with another informative(hopefully) article for you all. Once again I would like to apologize for my absence for about a week or so. I have some stuff going on with my life and university and I haven't found enough time to make a fully in-depth article. In this article I'm going to walk you through one of the main networking protocols when it comes to communication across the Internet between programs, aka UDP(User Datagram Protocol).

This article is to all the newbies on here wanting to become a hacker. Since I have seen many newbie questions on here, I need to address this.

I mentioned in 2015 I wanted to start a 'DoXing' series, and since I havent seen this on Null Byte, I am now going to introduce this to the community.

If Android is all about options, then iOS is all about new features. Every year without fail, Apple announces a cool software component that brings something new to the table, and this year was no different.

First of all, Merry Christmas and Happy New Year to all Null-Byters that learn and teach in this wonderful site. In this article we will explore the basics of the meterpreter's IRB (Interactive Ruby Shell).

A lot of people think that TOR services are unhackable because they are on a "secure environment", but the truth is that those services are exactly the same that run on any normal server, and can be hacked with the same tools (metasploit,hydra,sqlmap...), the only thing you have to do is launch a transparent proxy that pass all your packets through the TOR network to the hidden service.

Welcome back! Sorry for being so quiet, I've been rather busy with this project lately! Anyways, in the last iteration of how to train your python, we covered lists. Today we'll be introducing iteration and the two loops python has to offer, for and while. Also, we'll be covering a couple general use functions. So, let's get started!
Hello! My name is An0nex. I am an ethical hacker who wants to share the art of hacking with all of you guys!

In the last iteration of how to train your python, we covered the concept of control flow and covered the booleans associated with it. Today, we'll be putting those to use as we discuss how to use if, else, and how to make conditional statements. So, Let's get started!

In the last iteration of how to train your python, we covered basic string manipulation and how we can use it to better evaluate user input. So, today we'll be covering how to take user input. User input is very important to scripting. How can we do what the user says if we can't tell what the user wants? There are multiple ways to take input, we can give the user a prompt and take input from them directly, or we could use flags/switches, and take their input before the script is even execute...

Last time in how to train you python, we covered the basics of variables and output. While we were covering variables, we talked briefly about strings. "String" is just a fancier way of saying "Word". A string is simply a set of characters encased in quotations, this lets python know that it is a word. Sometimes when we do things with strings we'll need to change them in order to do something. Python is case sensitive, for example "Null-Byte" is not the same as "null-byte". This is where mani...

Editor's Note: The research described in the article below has been criticized and any conclusions based off this research should be examined with a skeptical eye. The article has been edited to reflect these issues.

Recently I've been looking around our wonderful community and I've seen some absolutely hands-down fantastic python scripting articles. But, in the end, these series weren't very extensive. I've been wanting to do a series on teaching python for a while now, and I don't mean just the basics, I mean to make an extensive series that takes it all the way from "Hello, World!" to popular third party modules, and everything in between!

Welcome learners, lets us proceed further with the information we already have. In this post we will explore more about finding hacked accounts online. We will look into how to find juicy info in pastes which are deleted on Pastebin.

This is second post in my series of posts for finding hacked accounts online. Please do read the part 1 of the post at http://null-byte.wonderhowto.com/how-to/find-hacked-accounts-online-part-1-0164611/

Welcome back, rookie hackers! We recently began an exploration of ways to hack using the Bluetooth protocol. As you know, Bluetooth is a protocol that connects near field devices such as headsets, speakers, and keyboards. Its minimum range is a 10-meter radius (~33 feet) and maximum is at 100 meters (~328 feet).

Hello, fellow grey hat hackers and aspiring coders. I'm back again with another python tutorial. Just that this one is gonna be a lot cooler ;-). We gonna make an encryption program, that well you know encrypts all the files on your pendrive or hdd or whatever you want....Also lots of thanks to DrapsTV. They have helped me a lot with Python and making awesome programs. The video is here:

Welcome back, my amateur hackers! As many of you know, Null Byte will soon be re-establishing its IRC channel. In preparation of that event, I want to show how to set up a secure IRC client with OTR, or Off the Record.
There are a bunch of new and interesting features packed inside of Windows 10, but one of the most exciting ones is the Microsoft Edge web browser, the long-awaited replacement of Internet Explorer.

Hello Hackers/Viewers, It is a new day, and you might be thinking, It is so boring, why not try to be cool with computers in front of my friends? That is why, I have made this tutorial to make fake viruses using notepad to look cool!

Apple has once again improved functionality of Siri, their personal voice assistant for iPad and iPhone, in iOS 9—and this update is a big one. You can now use Siri to find photos based on location and date, set up contextual reminders, find your friends and family, and more.

Now that we have our vulnerable server, it's time to start up BeEF. Getting Started

First, I want to give credit to the author where I first found how to do this: Astr0baby's Blog. This article was dated, so I took the script on his page and reworked it to make it work today. (I also included the way to make it hide the cmd line popup.) Requirements

Seldom in recent history has a cyber security event caused so much media stir (maybe because it happened to a media company?) and international relations upheaval. Cyber security breaches seem to take place daily of major corporations, but the Sony hack seems to have captured the American imagination and, for that matter, the whole world's attention.

Are you stranded in a hotel room with no kitchen, but craving the comfort of a home-cooked meal? Fear not, I have found some interesting ways to cook food without the luxury of an oven, stove, microwave, or even a toaster!—also known as "hotel room cooking."

Nostalgia sometimes gets the best of us—hence the reason we geek-out when we see emulators for SNES on Apple devices or N64 on Android.
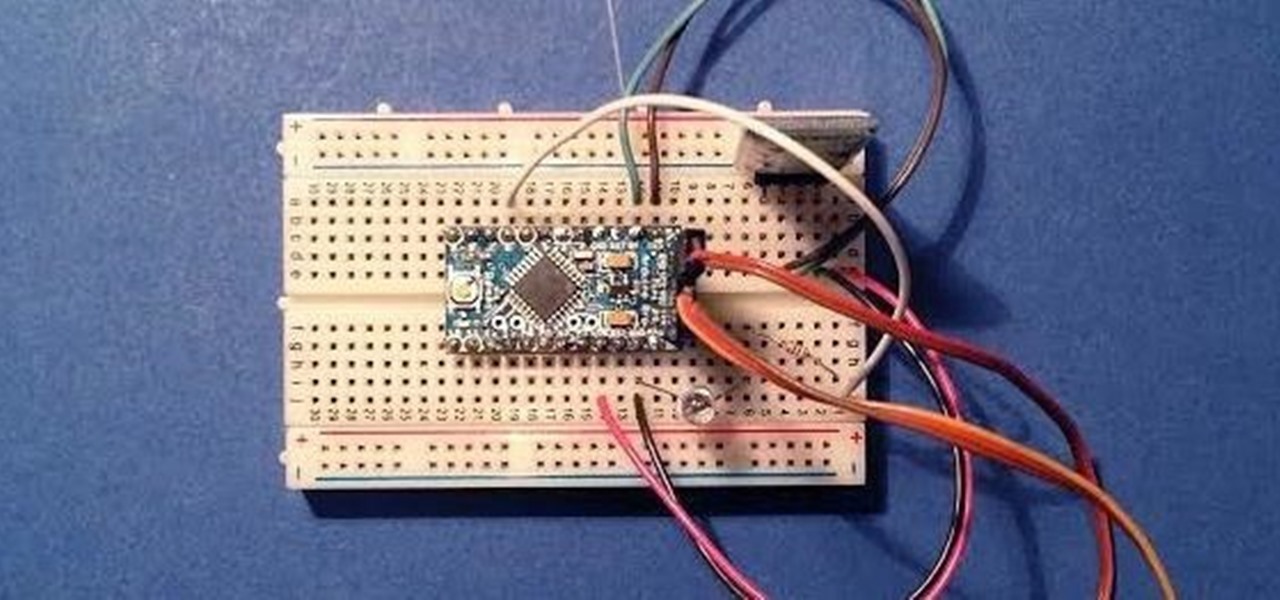
Since its creation, Arduino has been growing exponentially more popular as DIY enthusiasts and Makers alike realize its potential. As new versions of the device are released, many easy-to-use peripherals are showing up on the market also.
Back in the day when computers relied on CRT monitors, having a static image displayed for too long actually resulted in the image being burned into the screen. For this reason, screensavers were developed, which display animated images in constant motion to prevent burning in when you stepped away from your computer.

If you have a hard time remembering what you've just read on your iPad or Kindle, try changing the font next time. The typeface you use to read books, newspapers, and online articles is either hurting or helping your memory, and you'll be surprised which ones are killing your brain cells.

You've got to be sick of it by now. Those meaningless and unsatisfying articles, lists, and videos you were duped into clicking on because their headline made them impossible to resist.

Yesterday, I wanted to remove BackTrack from my system and install Kali, and at the same time didn't want to damage my Windows 7 or my hard drive. I searched a lot of articles, but almost all of them wanted me to have a backup Windows 7 CD, which I don't possess.