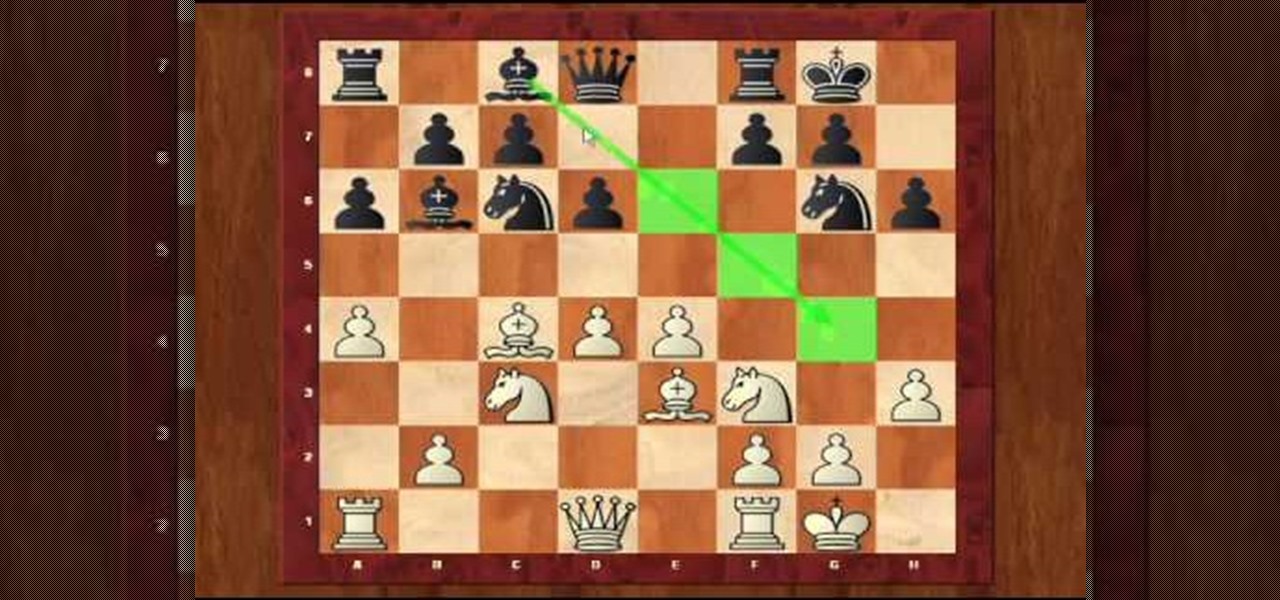
This explores Bobby Fischer's strategies in, and versus, various openings. This video looks at Fischer's play in the King's Gambit Accepted opening (ECO C33). The match was played in 1968 against Minic Dragoljub at the Vinkovci tournament. Learn from the masters!
This explores the Ruy Lopez Classical Defense opening (ECO C64). The video includes a match between Emanuel Lasker and Wilhelm Steinitz in the Chess World Championship rematch in 1896. See the Spanish Opening here, and learn it for yourself.

This explores Fischer's opening strategies versus various openings. This video looks at one of his defenses against the King's Pawn Opening. The match was played in 1966 in Santa Monica against Wolfgang Unzicker.

Here, we explore Fischer's opening strategies versus various other openings. This video looks at his King's Pawn Opening versus Bent Larsen's French Defense. The match was played in 1971 in Denver, with Fischer winning.

Sean Astin hosts AFI's filmmaking tutorial series, LIGHTS, CAMERA, EDUCATION! Here, we explore "The Pitch" or presenting your ideas for your film script.

Pull out your Nintendo DS and your Castlevania: Dawn of Sorrows video game and get ready to demolish it (as it in beat it). This extensive video walkthrough series on Castlevania: Dawn of Sorrows provides all the maps and secrets you need to know about in the DS game.

Learn how to exercise your dog. Follow a regular exercise routine together with your pet. It will benefit you both!

Learn how to sew a button by hand. Not wearing your favorite shirt because it’s missing a button? Don’t worry—sewing on a new one is simple and fast.

Explore your kid's creativity with crafts! Learn how to make bunny, Batman, pirate, butterfly, and many more masks out of foam in this free crafting video series.

Find out the benefits of hot cereal grains and how to make oatmeal, cracked wheat, brown rice, and other rolled grains; explore hot cereals and healthy alternatives to oatmeal in this free video on whole grain cereal tips.

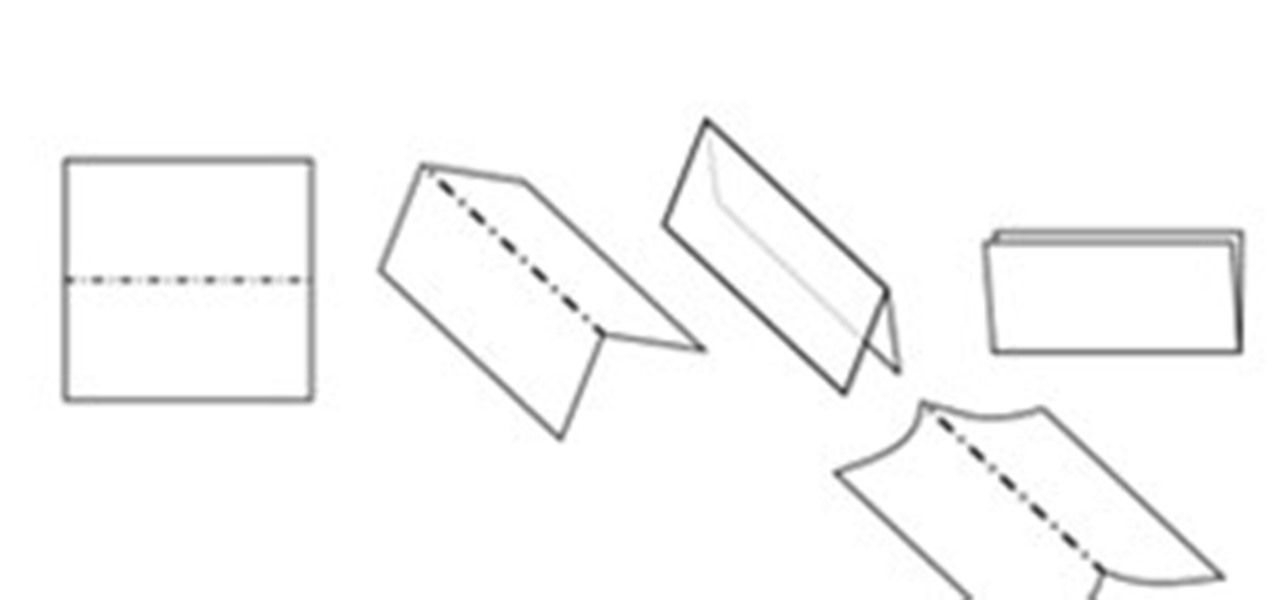
In this article you will learn how to understand written origami instructions, called diagrams. You can follow the video below or read the entire article

There's always a faster and more efficient way of doing things when it comes to Facebook. And if you have a Facebook Fan Page (Like Page) for your website, it's easily done right from your mobile device. Learn this super quick tip to post updates, videos, and pictures right to your Fan Page via your mobile device. Super easy you can do it in seconds.

This video tutorial from dproxisback presents how to download and install Handbrake DVD ripping tool.To avoid installation problems, carefully choose application version for each type of computer and operating system.Open your internet browser and visit http://handbrake.fr/?article=download web page.Choose correct version for your type of operating system (MacOS, Linux, Windows).Download and install the application. Run Handbrake once it's installed.Click File-Select Source. Browse for your f...

A low tunnel is a kind of mini-greenhouse for your garden. Growing vegetables in a low tunnel requires proper ventilation. In this tutorial, you'll learn how to provide the right ventilation for your low tunnel, keeping your plants happy and healthy.

Garlic is great for spicing up your meals (and keeping vampires away!) and fall is a great time to grow it. In this video tutorial, you'll learn how to grow garlic in your garden. Get some garlic bulbs from a seed catalog, nursery or organic grower, and you'll soon have a garlic crop to be proud of.

Come the fall, your garden is probably going to be looking pretty spare. But it doesn't have to be that way. There are vegetables that will thrive in the fall. In this Growing Wisdom gardening tutorial, you'll learn how to grow vegetables in the cooler months.

Autumn leaves may be beautiful, but they can also be incredibly annoying as they pile up around your garden. But there are things you can do with autumn leaves, like mulching them, composting them and turning them into a living fence. In this episode of Growing Wisdom, Dave Epstein walks you through how to make a leaf fence.

Like any article of clothing, ties can get stains on them Learn how to remove stains from polyester or silk ties in this free clothing care video from a dry cleaner.

This how to video is a good general reference for anyone making their own pants, trousers, or jeans; basically any article of clothing with a fly front. The example uses a Suitability pants pattern, and can also be used to substitute a button fly. Watch and learn how to sew on a zipper to a pair of pants or trousers using a sewing machine.

Action games encompass a wide array of categories, ranging from racing games that pit you against players the world over for track domination, to endless runners that push you to set ever higher scores, and RPGs that let you embark on adventures in fantasy worlds. With such a huge selection of titles to look through, it's all too easy to overlook a game you might otherwise like.

When it comes to attacking devices on a network, you can't hit what you can't see. Nmap gives you the ability to explore any devices connected to a network, finding information like the operating system a device is running and which applications are listening on open ports. This information lets a hacker design an attack that perfectly suits the target environment.

A new study published by American University demonstrates how Pokémon GO and other augmented reality games can help city governments bring communities closer together.

Backdooring a powered-off MacBook is easy when a few minutes of physical access is allowed. That attack works well if the hacker also shares a Wi-Fi network with the victim, but this time, I'll show how to remotely establish a connection to the backdoored MacBook as it moves between different Wi-Fi networks.

So much information exists online that it's easy to get lost in data while researching. Understanding the bigger picture can take a lot of time and energy, but narrowing the question to one that's easy to answer is the first step of any investigation. That's why analysts use open-source intelligence (OSINT) tools like Maltego — to help refine raw data into a complete understanding of a situation.

Whether you're riding the subway on your way home from work, or stuck in the backseat of the car on a long road trip, there are times when you need to entertain yourself without a mobile data connection. A good mobile game would pass the time perfectly, but not every game works without an internet connection.

Fish are delicate, flaky, and can be damn tricky to cook; more often than not, you end up with a hard, dry block of flesh that makes your taste buds sad. And the best ways to cook fish that you know of—c'mon, who doesn't love a fried fish—take way too much effort for you to bother with on a weeknight. Or maybe you're looking for a healthier way to enjoy fish that doesn't require batter or frying at all.

Hello everyone! How's subnetting going? Did you practice a lot? I hope you did, but even if you didn't we will go through some more examples so you can be feeling confident after reading this article. It's all about that bad boy binary!

Hello ladies and gentlemen, I'm back with another informative(hopefully) article for you all. Once again I would like to apologize for my absence for about a week or so. I have some stuff going on with my life and university and I haven't found enough time to make a fully in-depth article. In this article I'm going to walk you through one of the main networking protocols when it comes to communication across the Internet between programs, aka UDP(User Datagram Protocol).

Good day people, today we will examine some basic, for some people well-known attacks, also we will take a look at some advanced attacks.

In this article, we will build a parallel password cracker using the techniques explained in the previous part. As SHA-512 is the digest function that Kali (and most modern Linux distributions) use to store our passwords, we will make a SHA-512 password cracker.

As many of you know, processor's clock frequency improvement got stuck in about 2003, causing the origin of multicore CPU (and other technologies). In this article I'll introduce you on how to run code simultaneously in various processors (I suppose that all of you have a multicore CPU). When you write code without any parallel directive, it only executes in one CPU at the same time (see it below). OpenMP make simple to work with various cores (if not with all of them) , without so much heada...

Welcome back! In the last iteration of how to train your python, we covered loops, today we'll be covering something that I wish I had learned about much earlier in my scripting career, errors. We all run into them, and they can be frustrating, but there is also a silver lining to them. Today, we'll be discussing why some errors are unavoidable, and what we can do when we run into them. Also, this article will be more of a concept and less of writing actual code, but the information is equall...

Welcome back, my novice hackers! This new series on Bluetooth hacking was inspired by a recent episode of Mr. Robot (my favorite TV show). In episode 6, Eliot hacked the bluetooth keyboard of the police office in order to hack the prison and release his nemesis, Vera. This is just one of the many hacks we will explore in the series.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Everybody loves the stars. Well, I certainly do. As a child I'd spend hours outside during summer nights marveling at the seemingly endless amount of sparkling dots spanning the sky. Maybe you have children of your own and want to create a sparkle in their eyes, or in your own. This tutorial will provide a basic method of bringing the stars inside—at least, in part.

With Apple's Yosemite build of Mac OS X came Continuity, a feature that has allowed us to connect our mobile devices to our computers, letting us access apps, send text messages, answer phone calls, and more while seamlessly switching from one device to the other.

Brought to you by Chevy. Video: .

I honestly believe that everyone on earth owns the same blue cooler—you know the one. Cooler technology hasn't changed since the '50s, and frankly, it's time to mix things up, with a built-in blender perhaps? With the Coolest Cooler, it's actually possible!

While some mobile sites have built-in text-resizing tools, many do not. A lot of those that don't won't even let you pinch-to-zoom. That makes it difficult for people with low vision to read small fonts on their iPhones. In some cases, like with photo captions, even those with perfect eyesight suffer.

Welcome back, my tenderfoot hackers! I have written many tutorials on hacking using Metasploit, including leaving no evidence behind and exploring the inner architecture. Also, there are my Metasploit cheat sheets for commands and hacking scripts.