
How To: Evil-Twin (Part 1) - Setting Up the Dhcp Server.
Hello again, ***UPDATE: Adding links to the other Two articles****


Hello again, ***UPDATE: Adding links to the other Two articles****

Welcome back, my greenhorn hackers! Throughout this series on Metasploit, and in most of my hacking tutorials here on Null Byte that use Metasploit (there are many; type "metasploit" into the search bar and you will find dozens), I have focused primarily on just two types of modules: exploits and payloads. Remember, Metasploit has six types of modules:

If you haven't read the last article, feel free to stop by and give it a read, but abstaining from reading it will not, for the most part, be detrimental to your understanding.

Hello, fellow hackers. I'm sure we've all seen it somewhere: the undying question of "How do I hack the game so-and-so?" And the answer usually is, "Come back when you actually know how to hack!" But how does one even go about "hacking" a game? What could that even mean?

With as much creativity and freedom that we have on Android, it feels a little underwhelming that the only gesture we can perform on the status bar is a downward swipe to expose the notification tray or quick settings. Maybe this is a field for Android to expand on in the future, but until that day, third-party developers are exploring this now.

Welcome back, my tenderfoot hackers! Recently, Microsoft released a new patch (September 8, 2015) to close another vulnerability in their Windows Vista, 7, 8, and 8.1 operating systems. The vulnerability in question (MS15-100) enabled an attacker to gain remote access to any of these systems using a well-crafted Media Center link (MCL) file.

Welcome back, my nascent hackers! Although my favorite TV show, Mr. Robot, had completed its first season already, I have not completed demonstrating the hacks that Elliot used in the show. (By the way, I can't wait for season 2!)

Welcome back, my tenderfoot hackers! Well, the first season of Mr. Robot just ended and Elliot and fsociety successfully took down Evil Corp! They have effectively destroyed over 70% of the world's consumer and student debt! Free at last! Free at last! Of course, global financial markets crashed as well, but that's another story.

Welcome back, my fledgling hackers! In this series, I am trying to develop your knowledge of digital forensics, which is valuable whether you're choosing a career in it or just want to know how your hacker activity can be traced. Few professional digital forensic investigators have a hacking background, but the best ones do.

Downloading YouTube videos for offline use to watch later has always been a problematic endeavor. Dedicated third-party apps don't last long in the App Store, web-based converters aren't very functional on mobile, and rogue apps outside the App Store are tricky to sideload and open up the possibility of vulnerabilities. But that doesn't mean you still don't have a few good options.

I am very new to Null Byte but I find much of its content and community incredibly interesting. I spent quite a bit of time just chronologically going through the posts and I noticed a common theme in many of the beginner posts. Many people seem to want to know the 'secret' or a paragraph on "How to Hack" and become a hacker in a few minutes. I started off this post as a reply to a question from a beginner but thought it might be beneficial to have for those stumbling across this site.
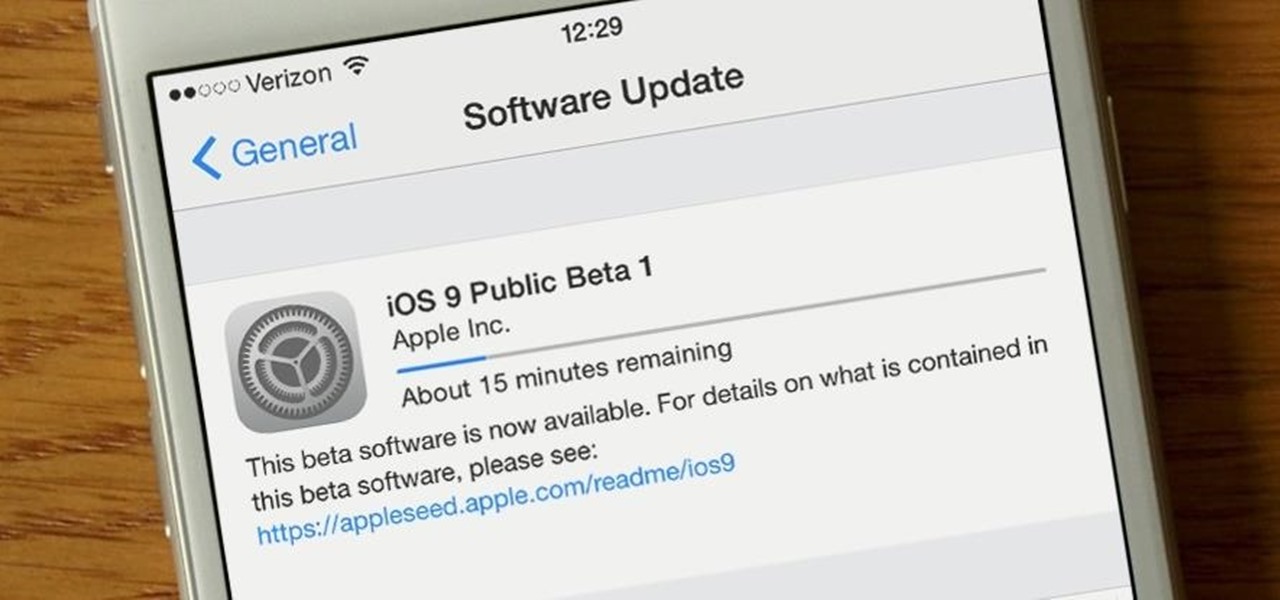
A month after its initial release to developers, iOS 9's Public Preview build is now available to everyone. If you signed up right from the start, you should receive an email or push notification letting you know of its availability. If you didn't, make sure to sign up for the Apple Beta Software Program.

As it stands, Firefox OS isn't a very popular third-party operating system for Android devices, especially when compared to others like CyanogenMod, but Mozilla developer Fabrice Desré is attempting to change that.

Grilled cheese is one of my favorite foods, ever. However, there are times in my life when I haven't had access to a full kitchen, and it's pretty hard to make a good grilled cheese sandwich without one.

Welcome back, my tenderfoot hackers! Have you ever wondered where the physical location of an IP address is? Maybe you want to know if that proxy server you are using is actually out of your local legal jurisdiction. Or, maybe you have the IP address of someone you are corresponding with and want to make certain they are where they say they are. Or, maybe you are a forensic investigator tracking down a suspect who wrote a threatening email or hacked someone's company.

Welcome back, my rookie hackers! In my ongoing attempts to familiarize aspiring hackers with Linux (nearly all hacking is done with Linux, and here's why every hacker should know and use it), I want to address a rather obscure, but powerful process. There is one super process that is called inetd or xinetd or rlinetd. I know, I know... that's confusing, but bear with me.

Mother Nature is one creative entity, especially when it comes to fruit. Let's face it: most major supermarkets stock only the most common fruits like apples, pears, and grapes, but they're so basic. Why not explore other options, from the stinky-yet delicious durian to the captivating citrus caviar that is finger limes?

Welcome back, my tenderfoot hackers! Now that we have begun this trip down web app hacking lane, we need to first address target reconnaissance. Like any hack, reconnaissance is critical. (Are you tired of me saying that yet?)

Magic Leap, the virtual-reality software group backed by Google, just released a teaser video on their YouTube channel. In a word, it's amazing.

Welcome back, my aspiring hackers! As I mentioned in earlier posts, the best hackers (or at least those not behind bars) have a keen understanding of digital forensics. If I am tasked to intrude upon an enemy's file server to retrieve war plans, such as in this tutorial, it is essential to my country's (and my own) well-being that it not be traced back to me. Understanding digital forensics helps us to leave without a trace and never have a trail back to us or our employer.

Welcome back, my budding hackers! This is the initial post of a new series on how to hack Facebook. It's important to note here that each hack I'll be covering is very specific. I have said it before, but I feel I need to repeat it again: there is NO SILVER BULLET that works under all circumstances. Obviously, the good folks at Facebook have taken precautions to make certain that their app is not hacked, but if we are creative, persistent, and ingenious, we can still get in.

Most people's fascination with social media these days is the instant gratification that can come with it. Whether you post an image on Facebook, Instagram, Snapchat, or Twitter, a minute or two later your phone will receive a notification informing you of a buddy or two who liked it.

While I do enjoy the vanilla Android Lollipop experience that comes with the Google Play Edition HTC One, I do miss the sweet camera that ships with Sense. Luckily, the people behind Liberty ROMs found a way to port that camera over and now we can enjoy the best of both worlds... well, sort of.

Brought to you by Tomcat. Falling snow, warm fireplace, delicious hot cocoa, quiet reading time, mouse. Quick quiz - which one is not like the other? Nothing can ruin a perfectly cozy afternoon in your home like a pest on the loose. With dropping temperatures, you may have some unwelcome residents, like mice, looking for shelter from the cold.
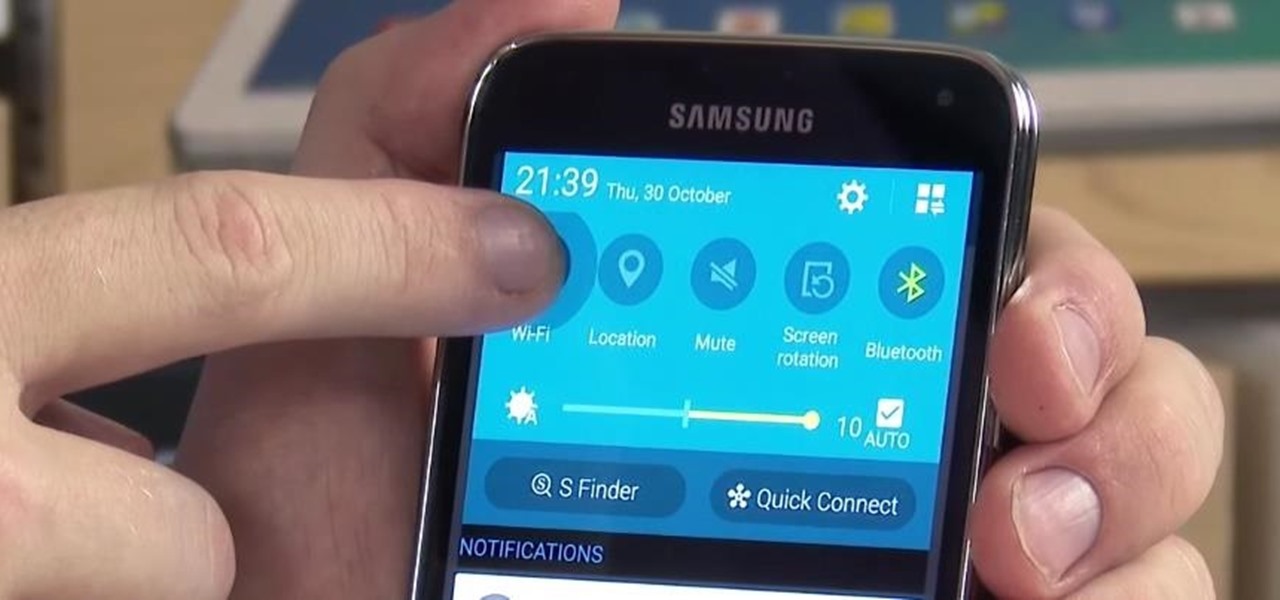
With Nexus devices already enjoying Android 5.0 Lollipop, most other manufacturers are scrambling to get their flagships updated to Google's latest operating system. While HTC has promised Lollipop by the end of 2015, OEMs such as Motorola and Sony have already issued updates to their latest models. Then there's Samsung.

Aside from being able to change the wallpaper and add shortcuts, the Galaxy S4's lock screen doesn't offer much in the department of personalization. The lock screen is efficient and practical, but it's also a little bland.
While the Quick Settings feature on Android is great, manufacturers like HTC, LG, and Samsung took it a step further in their custom skins. For instance, on Samsung devices, you can access the most common toggles at the top of the Notification tray, and you can tap once to access more tiles. This makes toggling cellular data, Bluetooth, and Wi-Fi a fast and painless process.
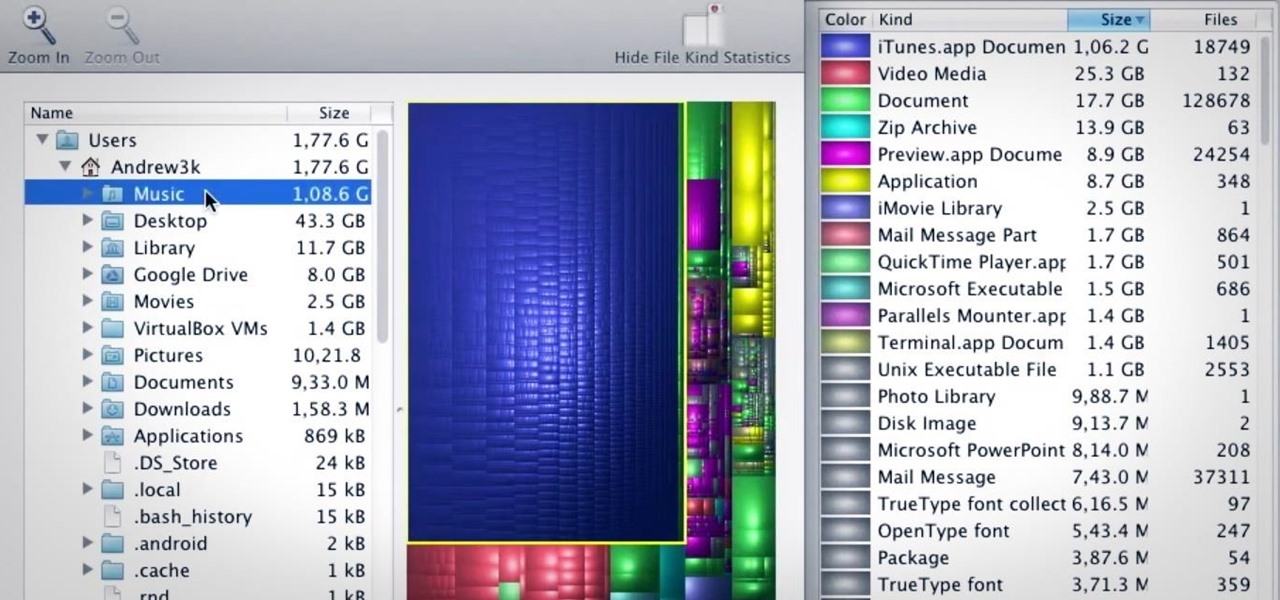
I love my MacBook Air, but the fact that it runs on only 128 GB of flash storage causes me to move most of my files to the cloud. I don't mind having to be connected to the internet in order to access my files, but it's definitely a hassle trying to figure out which files I should move in order to save the most space. Usually, I don't even bother even trying until I see the dreaded "Your startup disk if almost full" warning. Currently, the only real way to find your biggest files in Mac OS X ...

Apple definitely wasn't first to the widget game, but any iPhone running iOS 8 or higher can add widgets to their Today View found via a swipe down from the top of the screen when on the home screen or in any app. There's even access to widgets on the lock screen via the same swipe down on iOS 8 and iOS 9 (on iOS 10, iOS 11, and iOS 12, all you have to do is swipe right on the lock screen).

Now that you've updated your iPad, iPhone, or iPod touch to iOS 8, there's a lot of cool new things to explore. If you felt a little overwhelmed from all of the detailed information available in our Coolest Hidden Features of iOS 8 post, then I've got a simple breakdown of all of the new features available with quick links to their walkthroughs and pictures, if available. Watch the short video roundup, or skip below for the list.

Welcome back, my aspiring hackers! Many of you have installed Kali Linux as a virtual machine (VM) using VMware or VirtualBox, while others have installed Kali (or BackTrack) in a dual-boot system. The drawback to installing these hacking systems as a VM is that it then requires an external wireless adapter (your wireless adapter is piped through the VM as a wired device, eth0), but it makes for a great place to test your hacks while honing your skills.
If you notice any issues with your LG G3, pinpointing the culprit can be an arduous task. It could be a hardware issue, a resource-heavy app, or a bloatware-infested operating system.
It happens to everyone: you set a lock screen password in a hurry and cannot remember it the next day. To unlock your device again, you need to reset the password (or PIN, pattern, etc). There are two official methods of doing this.
If you thought iOS 7 was a drastic change from previous iterations, iOS 8 will certainly continue to rock the boat. From a revamped Control Center to enhanced "Continuity" to ephemeral messaging, Apple's newest mobile operating system will have many of you relearning the "basics."

There are a lot of techniques out there for how to cook the perfect steak, from flipping it multiple times to applying a spice rub or dry brine to aging the beef. But it turns out that there's a super-easy way to make a great steak at home, and all you need is a good cast-iron skillet and some salt.
Now that all variants of the Galaxy S5 have finally been rooted, we can start exploring all of the tweaks and hacks that Superuser privileges open up to us.

With its growing popularity, it's clear that the Chromecast isn't going away anytime soon, with options for casting games, cloud files, music, and much more. But not all content providers are in a hurry to add support for the device, and SoundCloud is one of them. While My Cloud Player is by no means an official SoundCloud app, it comes pretty darn close.
Videos are great for catching fleeting moments, and photos are insanely easy to share with anyone, but how can you get the best of both worlds?

We've all walked into a restaurant with the best of intentions only to order something absurd, like a cheese-injected burger topped with bacon on a brioche bun. It's delicious for the few minutes it takes to eat the thing, and then you're left with a bellyful of regret and an inability to directly look at the numbers on your scale. Turns out that getting yourself to make healthy choices isn't as hard as one might think.

Welcome back, my hacker novitiates! Recently, I demonstrated a hack where you could redirect traffic intended for one site, such as bankofamerica.com, to your fake website. Of course, to really make this work, you would need to make a replica of the site you were spoofing, or better yet, you could simply simply make a copy of the original site and host it on your own server!