When making a convincing mixed reality experience, audio consideration is a must. Great audio can transport the HoloLens wearer to another place or time, help navigate 3D interfaces, or blur the lines of what is real and what is a hologram. Using a location-based trigger (hotspot), we will dial up a fun example of how well spatial sound works with the HoloLens.

Hello ladies and gentlemen, PySec here coming at you with another informative(hopefully) article for you all. In the last tutorial, we finally finished our discussion about IP Addressing and I intentionally didn't mention a really important concept with which IP Addressing wouldn't be feasible without it. What I'm talking about is how our network device gets the IP Address in order to communicate with other devices on the network/Internet. There are many different ways for that to be accompli...

Welcome back! Sorry I've been gone for so long, but if anyone has been keeping up with these articles, you'll know that when I get quiet, something is cooking under the surface. In other words, I've been working on a project lately, so I haven't had much time!

Welcome back! Sorry for being so quiet, I've been rather busy with this project lately! Anyways, in the last iteration of how to train your python, we covered lists. Today we'll be introducing iteration and the two loops python has to offer, for and while. Also, we'll be covering a couple general use functions. So, let's get started!

In the last iteration of how to train your python, we covered the concept of control flow and covered the booleans associated with it. Today, we'll be putting those to use as we discuss how to use if, else, and how to make conditional statements. So, Let's get started!

In the last iteration of how to train your python, we covered basic string manipulation and how we can use it to better evaluate user input. So, today we'll be covering how to take user input. User input is very important to scripting. How can we do what the user says if we can't tell what the user wants? There are multiple ways to take input, we can give the user a prompt and take input from them directly, or we could use flags/switches, and take their input before the script is even execute...

Last time in how to train you python, we covered the basics of variables and output. While we were covering variables, we talked briefly about strings. "String" is just a fancier way of saying "Word". A string is simply a set of characters encased in quotations, this lets python know that it is a word. Sometimes when we do things with strings we'll need to change them in order to do something. Python is case sensitive, for example "Null-Byte" is not the same as "null-byte". This is where mani...

Welcome back, rookie hackers! We recently began an exploration of ways to hack using the Bluetooth protocol. As you know, Bluetooth is a protocol that connects near field devices such as headsets, speakers, and keyboards. Its minimum range is a 10-meter radius (~33 feet) and maximum is at 100 meters (~328 feet).

Hello, fellow grey hat hackers and aspiring coders. I'm back again with another python tutorial. Just that this one is gonna be a lot cooler ;-). We gonna make an encryption program, that well you know encrypts all the files on your pendrive or hdd or whatever you want....Also lots of thanks to DrapsTV. They have helped me a lot with Python and making awesome programs. The video is here:

There are a bunch of new and interesting features packed inside of Windows 10, but one of the most exciting ones is the Microsoft Edge web browser, the long-awaited replacement of Internet Explorer.

Seldom in recent history has a cyber security event caused so much media stir (maybe because it happened to a media company?) and international relations upheaval. Cyber security breaches seem to take place daily of major corporations, but the Sony hack seems to have captured the American imagination and, for that matter, the whole world's attention.

Cryptography is the science of keeping secrets, or more specifically, the science of disguising them. As a point of fact, cryptography has progressed quite a bit farther and now encompasses file and message integrity, sender authentication, and pseudo-random number generators.

The new Samsung Galaxy S4 just received an update to Android 4.2.2, so why is it that my Galaxy Note 2 is still running an older version of Jelly Bean? It felt like yesterday that my device was finally updated to 4.1.2, but why even bother since 4.2 has been around since last November?

You may or may not have heard the term "greebles" or "kit-bashing" before, but if not, they may sound like nonsense. Particularly 'greebles', which sounds more like the name of a small, gremlin-like creature. However, I assure you that they are very important in prop-making, and if you can master them both, you'll be able to make intricate, great-looking props in hardly any time!

I can imagine you sitting there thinking to yourself, "I've played a lot of games! I bet he won't have any that I don't know about!" Well, that's entirely possible. I'm only drawing from my own personal experience here, so you may, in fact, know of all these games.

Since it's October and Halloween is fast approaching, it's time for a series of articles on how to make the coolest Steampunk Halloween decorations for your home! In this installment, we'll look at some jack-o'-lanterns, skulls, and a few other things that are easy to Steampunk, but will still keep that "spooky" Halloween feeling.

There are lots of people who want to stay anonymous online, and lots of reasons they want to do this. Staying anonymous on the internet isn't easy, and it's probably possible to trace almost anyone with enough time and resources. A lot of people think that they're completely secure with just one method of cover. For example, a lot of people thought anyone using the Tor network was nearly untraceable, but then things like this often cast doubt on just how secure these networks are. Unless you ...

WonderHowTo is a how-to website made up of niche communities called Worlds, with topics ranging from Minecraft to science experiments to Scrabble and everything in-between. Check in every Wednesday evening for a roundup of user-run activities and how-to projects from the communities. But don't wait—start submitting your own projects to the most appropriate World now!

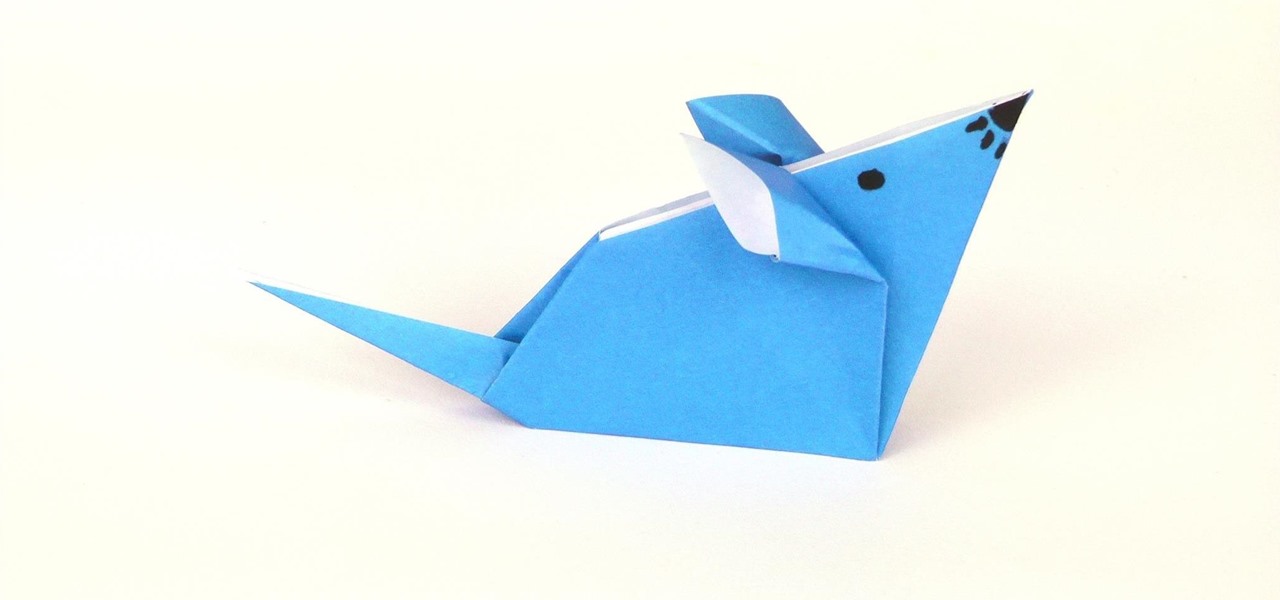
This tutorial teaches you how to fold an origami mouse with an ordinary sheet of paper. This model is suitable for beginners and children. Origami is great for small kids as the only material needed is paper, no scissors or glue that could do harm!

At a very early age, I would go on summer camping trips. I remember every night being handed a pack of sparklers that were my own, to swing around wildly, which gave me many valuable life lessons on cause and effect.

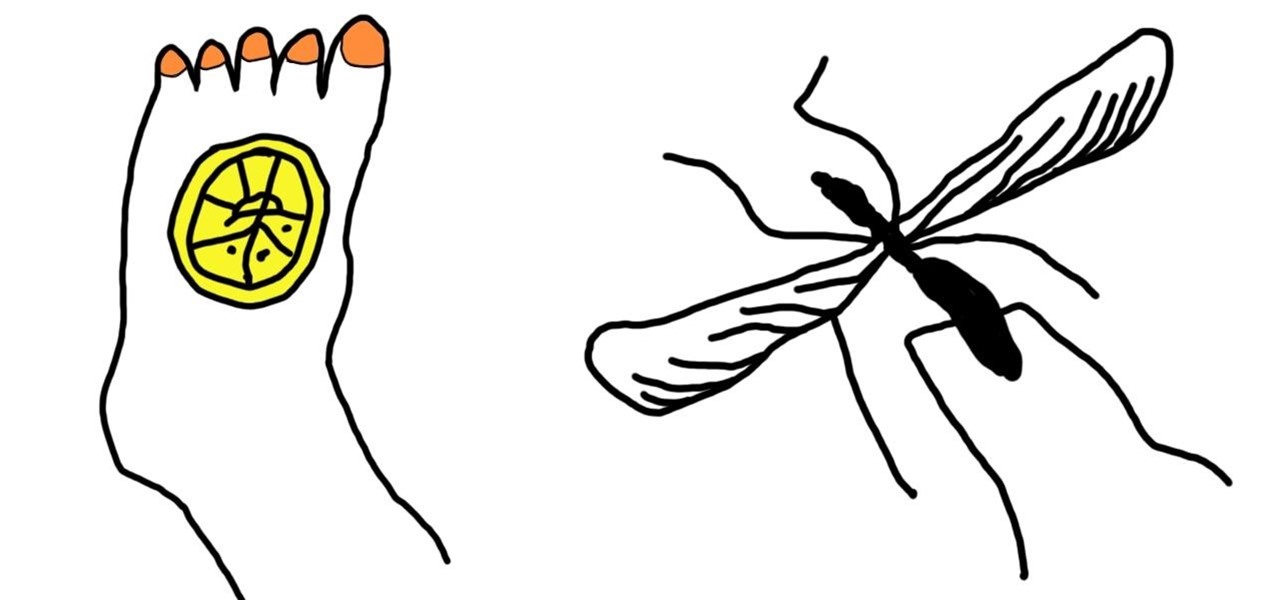
There are few things peskier in the summer than an unexpected mosquito bite swelling up on your arms and legs. Fortunately, there are many ways to heal your body of its annoying itch, ranging from fruit (lemon slices and banana peels) to common household items (baking soda and apple cider vinegar).
(Series designed to help explore whether your ideal employment ideas should be formalized into a business venture or as an employee or volunteer value added problem solver).

Everyone who owns or runs a website needs to know how they can improve traffic, and search engine optimization is the answer. This 13-part video series on SEO basics and strategies will give you more traffic for your site. It's jam-packed full of tons of great SEO tips! Check out each video in the series:

The most used and most washed articles of clothing are undergarments. Underwear, specifically bras and panties, are in desperate need of attention after each and every use. They're not like a pair of jeans, wearing them twice in a row is not a good idea, nor clean. Shabby’s not chic when it comes to lingerie. Use a little extra care to keep your lace and silk bras and panties looking good.

Wedding insurance, vacation packages, travel discounts – the American Automobile Association offers its members more than free towing.

For the average consumer, augmented reality is a fun way of dressing up photos and videos for social media. However, AR is also gaining momentum as a medium for storytelling, particularly in sharing powerful messages.

Attacks against databases have become one of the most popular and lucrative activities for hackers recently. New data breaches seem to be popping up every week, but even with all of that attention, databases continue to be a prime target. All of these attacks have to start somewhere, and we'll be exploring a variety of methods to gather information on PostgreSQL databases with Metasploit.

In the pursuit of large displays with thinner bezels, Samsung has sacrificed some components. While the loss of the headphone jack gets all the attention, there are other victims — namely, the notification LED.

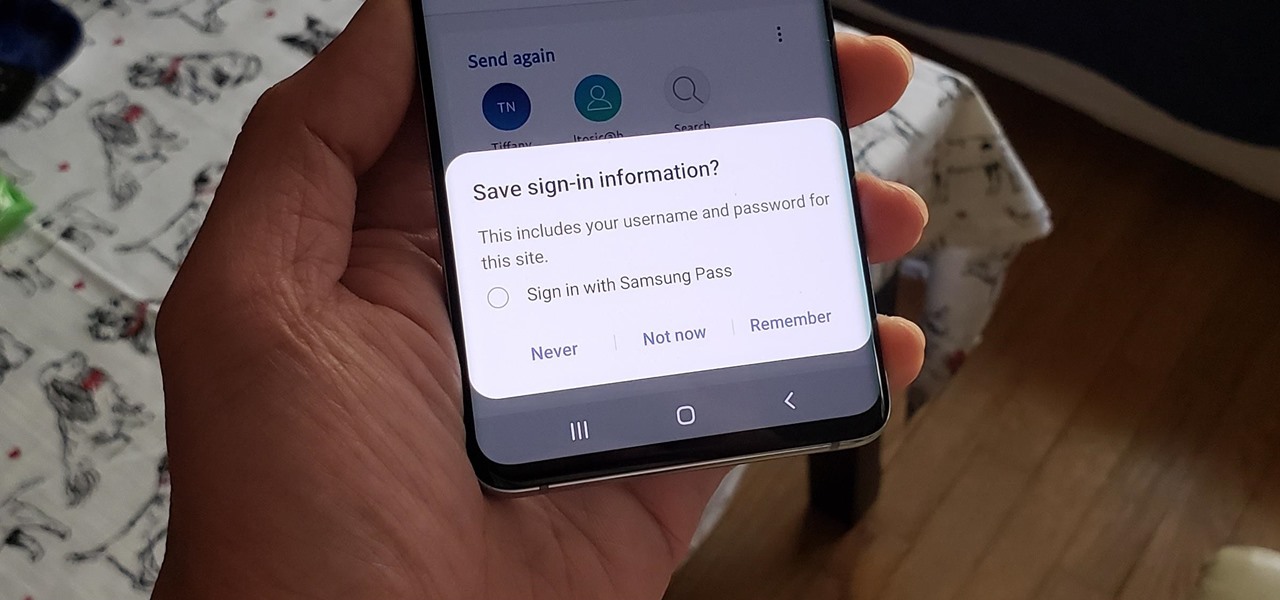
If you use Google Chrome on your computer, you've undoubtedly saved a ton of passwords since the browser always prompts you to. But Samsung uses their own password service on their phones by default, so you'll have to change a setting if you want to use your Chrome passwords to log into apps and sites on your Galaxy.

Facebook has announced the cancelation of its annual F8 developer conference, citing concerns around the developing coronavirus health crisis.

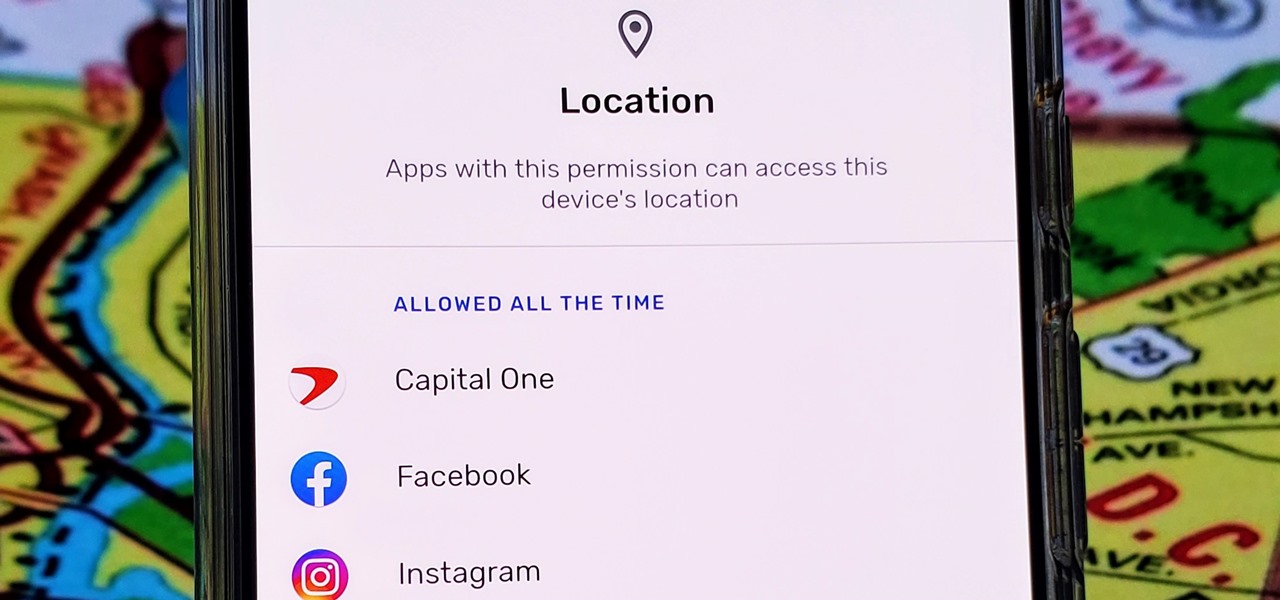
With Android 10, there are now three options when an app asks to access your location: Allow, Deny, and Allow While In Use. That last one prevents apps from seeing your location unless you're actively using them, and it's the default now. But when you first update, most of your apps will still be allowed to access your location in the background — at least, until you do something about it.

There are tons of apps to help you create unique and compelling posts and stories on Instagram, but you already have the tools you need to make something eye-catching. You can insert line breaks in captions, create translucent overlays for photos, rainbow-up your story font, and even add a 3D text effect to your stories.

If there's an influential tweet, you can see what people are saying about it by reading its comment thread. But what about quote tweets, aka tweets someone posted on their own timeline that quote the initial tweet? These don't show up in comment threads, but there is a way to find them.

Whatever it is you're into, Facebook Groups are a great way to connect with others that share your interests. And beyond matching you up with like-minded people, Groups also give you access to deals on items, help you organize play dates with families in the same area, and so much more.

Facebook is where a lot of people get their news. The problem, though? Your Facebook feed gets jumbled with random post times, which isn't useful for keeping up with new stories in real-time.

One of the hallmarks of augmented reality's coming of age is that the technology is starting to find a home in business categories that are less obvious compared to typical AR enterprise use cases.

While the automotive industry is moving towards adopting AR displays in future models, BMW is already shifting into the next gear with its vision of the technology.

One of the great things about Google Fit is how it gives you a central hub for all the fitness-related data in both your personal life and workouts. You can track the steps you take, log your heart rate measurements, or even record your sleeping habits. The easier it is to access this data, the more useful Google Fit becomes.

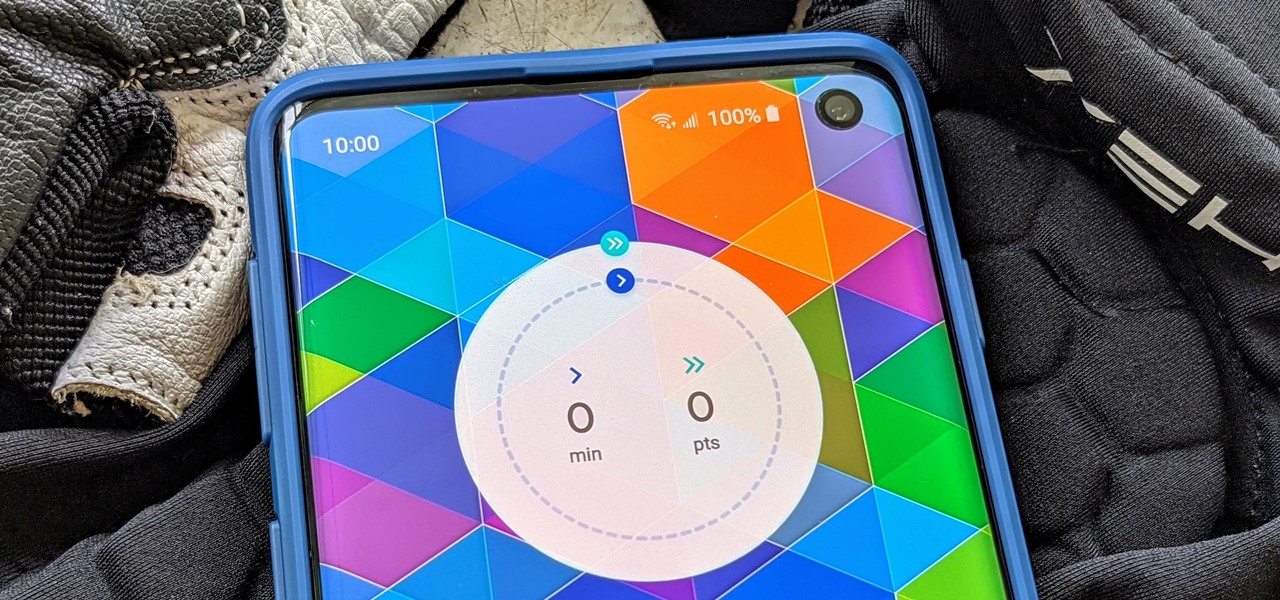
Google Fit houses all of your essential fitness-related information in the cloud for safekeeping at all times. You can easily let your device detect your workout sessions for you automatically based on a variety of sensors. At the same time, the Fit app makes it easy to manually start a workout as well.

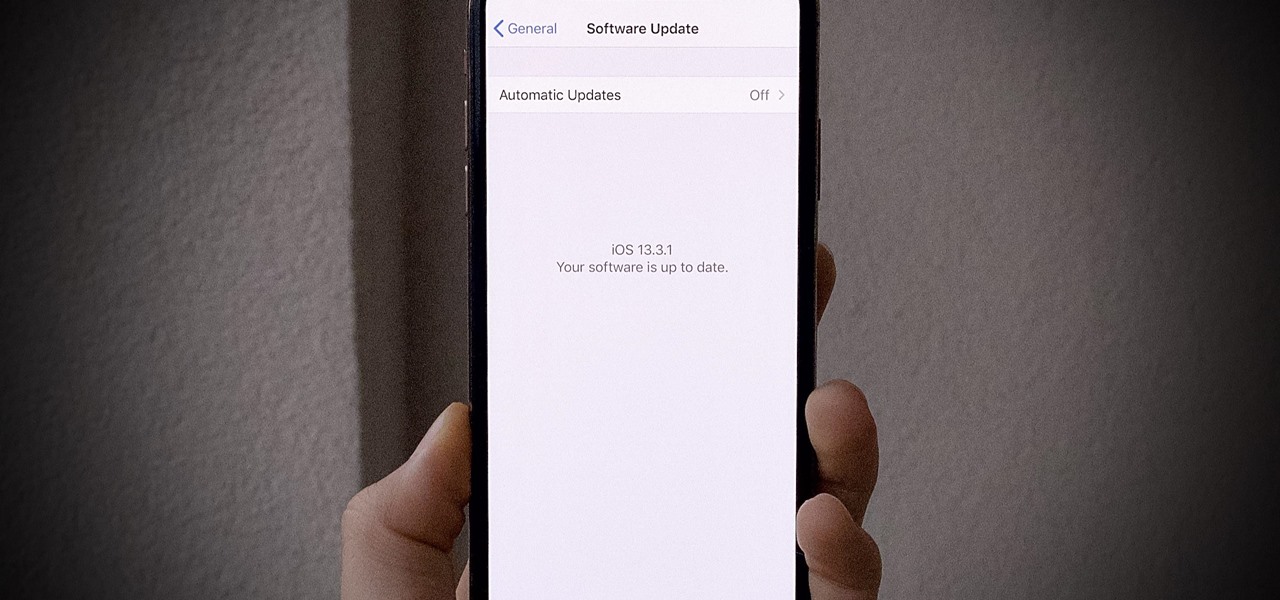
Yesterday, Dec. 17, Apple released the first developer beta for iOS 13.3.1. The update marked the first new beta in almost a month since iOS 13.3's fourth beta dropped on Nov. 20. Now, one day later, Apple has pushed out iOS 13.3.1 public beta 1 to everyone who wants to try out new features first.