If we learned anything from Mulan, it's that "the flower that blooms in adversity is the most rare and beautiful of them all." Well, these have been a trying couple of weeks in the US, hence the need for a blooming marshmallow flower.

Don't let the lack of owning a HoloLens stop you from joining in on the fun of creating software in this exciting new space. The HoloLens Emulator offers a solution for everyone that wants to explore Windows Holographic development.

If you're looking to mix up your home décor with something a little bit outside the traditional cabinet box set, check out the amazing Wave cabinet from NYC-based, Chilean designer Sebastian Errazuriz. This revolutionary design will change the way you think about interior decoration and furniture functionality.
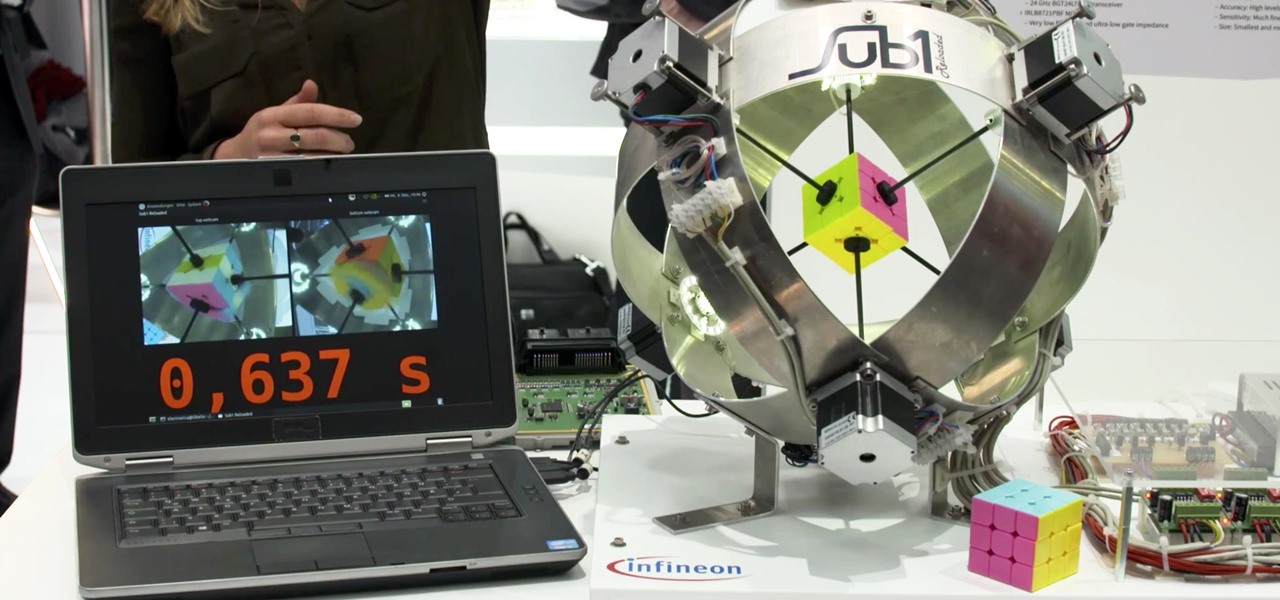
In December of last year, Australian Feliks Zemdegs broke the human world record for solving a Rubik's Cube with a time of 4.737 seconds. Well, this robot did it way, way faster by solving one in under 1 second. Don't tell me a robot takeover isn't real possibility.

Metasploit is an extremely popular pentesting tool capable of enumeration, exploitation, and injecting shell code, and is a part of almost every hacking toolkit. So there's no way I could leave this out of our series on getting your Mac set up for hacking.

With the holidays over, a lot of people with shiny new Google Homes are getting their first chance to explore the new Google Assistant. Before the Google Home's release, the Assistant was only available for the Google Pixel and Pixel XL, or in a text-based form with Google Allo—but now it's gone mainstream.

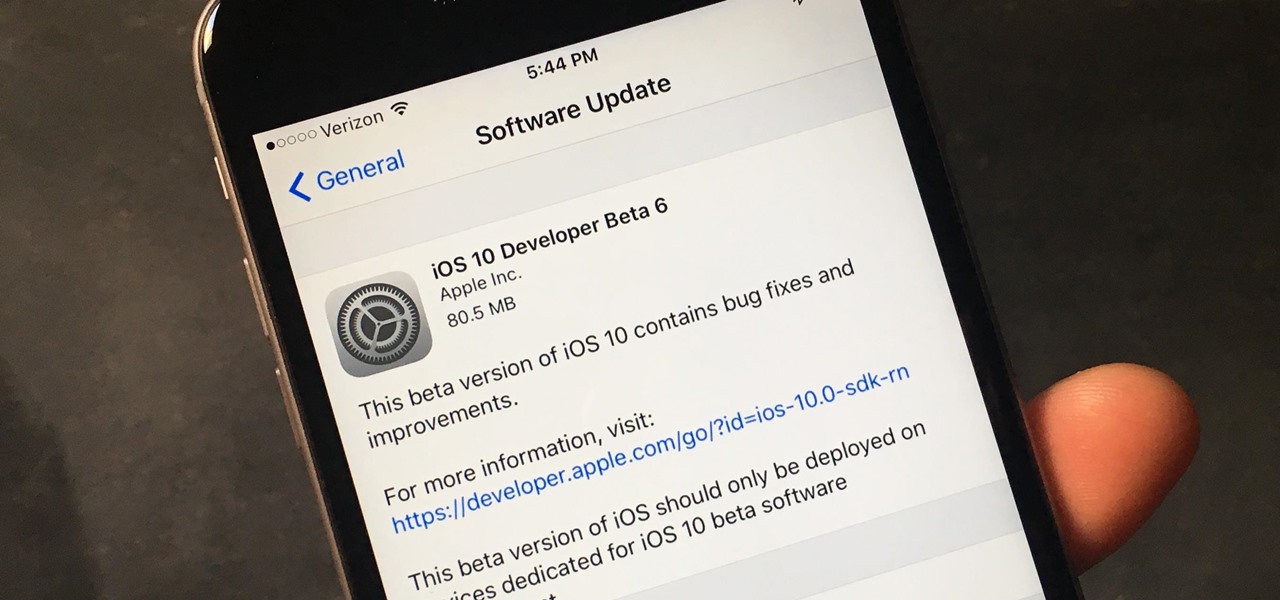
Apple has been aggressively smashing bugs with its last few updates to iOS 10, so it seems like all of the major work is done. With the iPhone 7 release date approaching fast, it's a good sign that the only remaining hurdles are relatively minor and cosmetic tweaks (though they still need to add the song lyrics they showed off a few months ago).

I fry foods a lot. A LOT. We're talking wings by the dozen here. As a result, I go through a ton of frying oil. Now, frying oil isn't the most expensive ingredient out there, but it adds up when you fry regularly. Of course, I always reuse my oil, but straining it can be a huge mess and it gets to a certain point where enough is enough. It's time to start fresh.

Augmented and mixed reality experiences attempt to break us out of windowed computing experiences and allow us to place software anywhere in the room. But that software doesn't have to take a rectangular form—theoretically, the web doesn't have to restrict itself to a page in a browser any longer. Does this mark the end of the web browser entirely? Probably not. A lot of information works well on the page, and the Microsoft HoloLens still uses a pretty standard version of their own Edge brows...

If you're standing in a foreign city, surrounded by signage in a language you don't understand, you won't suddenly be able to read it. But with a clever feature in Google's Translate app, your smartphone can.

There's been a lot of speculation as to what Apple's next iPhone models will have in store for us. There's a lot of credible rumors about the iPhone 7, but is there also a Pro model in the works? We may actually have a legitimate sneak peek at what that device could look like.

One of the more annoying parts about cooking or baking at home is dealing with sticky ingredients. You scrape the peanut butter out of the jar and into a measuring cup to make sure you have the right amount for your recipe, then scrape the correct amount into the bowl you're cooking with.

This is my first article on here, it's based off of a project that I'm working on at school which is on three ways to bypass windows user password's. If all goes as planned and you all would like I'll work on part two and part three and post them as soon as I can. I do have to give credit to Puppy Monkey Baby and The Defalt, both of whom are my classmates at college and have helped me with writing this article.

Although there has been much speculation about how much damage could be done if hackers were to take control of a country's SCADA systems, there have been few examples - until a few months ago, with the power outage in Ukraine caused by hackers.

Google is reportedly working on an iOS keyboard that brings key features to the iPhone, including Google's image and text search functions. (GIFs, yay!) According to The Verge, the keyboard has been in development and testing for months, and will act much like the Android version.

When you think of all the fun and games smartphones have to offer, it's easy to forget that they also make a great tool for getting things done. With utilities like document scanners, calendars, to-do lists, office apps, and password managers, that little computer you carry around in your pocket has the potential to increase your productivity levels in all aspects of life.

It's about that time again. Spring weather is here, a new season of Game of Thrones is upon us, and we're getting ready for the next version of Android.

What's up guys? Welcome to a sort of general walkthrough on how one might approach a reversing and analysis on a crypted malware. This is by no means a universal technique so don't assume that this will occur in every scenario, it's more of a demonstration than anything really.

Welcome back, NB community, to my series on sorting. I introduced in my last article the concept of complexity. When I say complexity, I'm talking about time complexity.

Whether you're ready to admit it or not, we've all got our alter egos—especially when it comes to the internet. Perhaps you have one Facebook account that you use publicly, while maintaining a second account for more private interactions.

Welcome back, my hacker novitiates! Often, to hack a website, we need to connect to and exploit a particular object within said website. It might be an admin panel or a subdirectory that is vulnerable to attack. The key, of course, is to find these objects, as they may be hidden.

This article is to all the newbies on here wanting to become a hacker. Since I have seen many newbie questions on here, I need to address this.

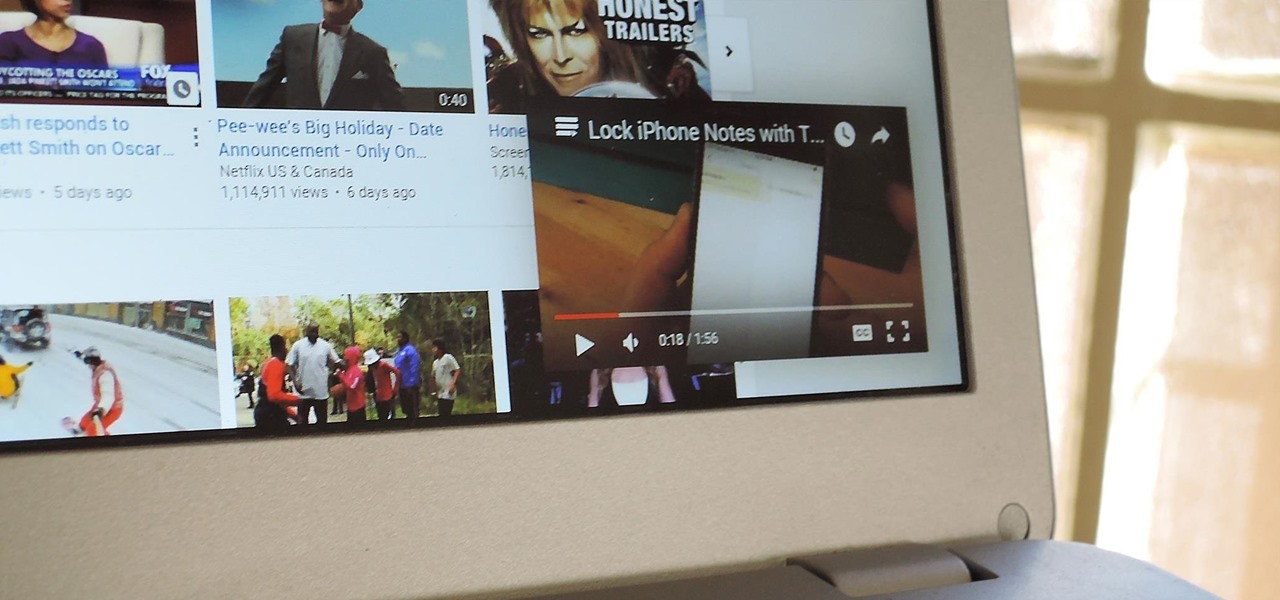
If you've ever used the YouTube mobile app for Android or iOS, you've probably noticed a cool little multitasking feature it has. While watching any video, you can simply swipe down on your screen to shrink the video down to a thumbnail view, which then allows you to browse the rest of YouTube while the original video keeps playing.

I mentioned in 2015 I wanted to start a 'DoXing' series, and since I havent seen this on Null Byte, I am now going to introduce this to the community.

If Android is all about options, then iOS is all about new features. Every year without fail, Apple announces a cool software component that brings something new to the table, and this year was no different.

Similar to the feature that lets you dim the light on your PS4's DualShock controller, your Playstation 4 is filled with useful tricks that you may not know about, especially when all you want to do is pick up and play. One of these useful tricks is the ability to turn your TV on using the PS4 controller.

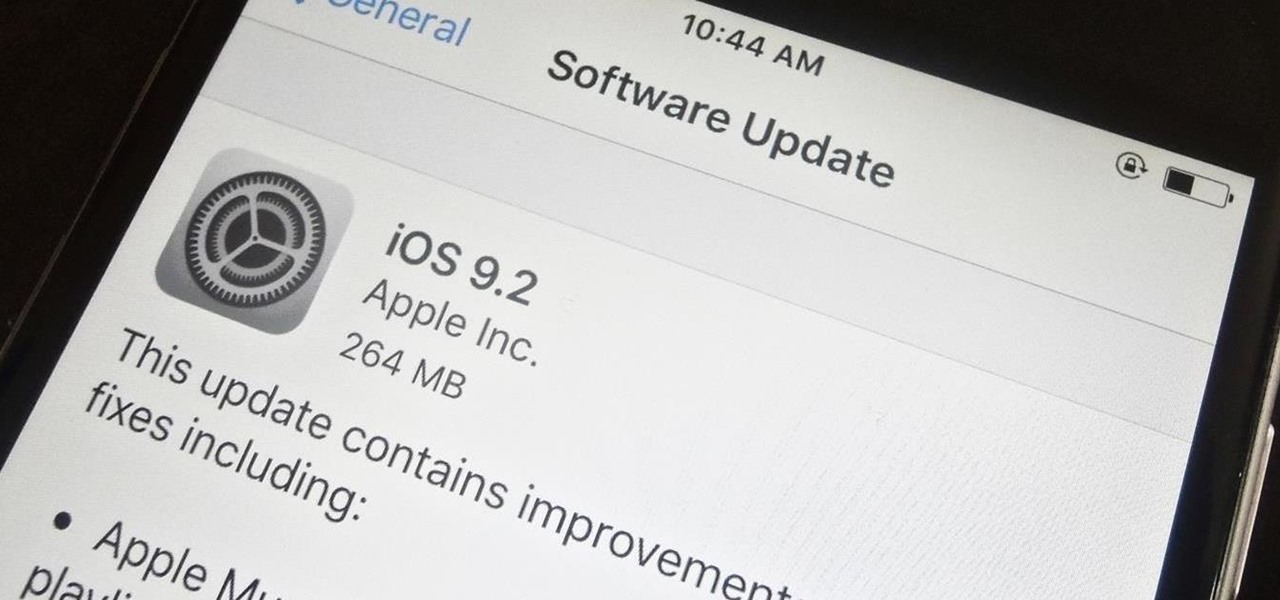
We're near the end of a productive year for Apple, one that introduced a new Apple TV, the iPad Mini 4 (in conjunction with the Apple Pen), the iPad Pro, and the iPhone 6S and 6S Plus, as well as iOS 9. Now, the second major update to iOS 9—version 9.2—has just been released to the public.

A lot of people think that TOR services are unhackable because they are on a "secure environment", but the truth is that those services are exactly the same that run on any normal server, and can be hacked with the same tools (metasploit,hydra,sqlmap...), the only thing you have to do is launch a transparent proxy that pass all your packets through the TOR network to the hidden service.

Windows 10 runs on laptops, desktops, tablets, and even phones—but even though the operating system should scale accordingly, fonts and icons aren't always perfectly sized for every screen. Luckily, though, there's a handy new menu for adjusting the size of your screen's contents, which you can use to make everything bigger or smaller to match your preferences.

In the wake of Apple Music making its debut on Android devices, Google has finally released its highly anticipated YouTube Music app. With these two tech heavyweights throwing their hats into the ring, the streaming music world is about to get rocked.

Welcome back, my fledgling hackers! Over the years, we have examined multiple ways to own, exploit, or compromise a system. On the other hand, we have not spent a lot of time on denial-of-service (DoS) attacks.

Greetings dear null byters, today we start a new series, we will start to attack users using social networking that are popular such as Facebook, Skype, and much more, and in part 1 of the series will engage users of Skype.

Unlike in the physical world, on the internet you're actually able to shut people up and block spoilers of newly-released movies, your favorite TV shows, or a sports event you've yet to watch on your DVR.

Editor's Note: The research described in the article below has been criticized and any conclusions based off this research should be examined with a skeptical eye. The article has been edited to reflect these issues.

Recently I've been looking around our wonderful community and I've seen some absolutely hands-down fantastic python scripting articles. But, in the end, these series weren't very extensive. I've been wanting to do a series on teaching python for a while now, and I don't mean just the basics, I mean to make an extensive series that takes it all the way from "Hello, World!" to popular third party modules, and everything in between!

Welcome back, my amateur hackers! As many of you know, Null Byte will soon be re-establishing its IRC channel. In preparation of that event, I want to show how to set up a secure IRC client with OTR, or Off the Record.

Welcome back, my tenderfoot hackers! In this series, we are exploring the myriad of ways to hack web applications. As you know, web applications are those apps that run the websites of everything from your next door neighbor, to the all-powerful financial institutions that run the world. Each of these applications is vulnerable to attack, but not all in the same way.

The peanut butter and jelly sandwich has officially left the building. When you eat this every other day in elementary school, you've sort of reached your limit. The thing is, peanut butter itself is delicious and quite versatile if used in the right way. Let's explore this kitchen cabinet staple and showcase it via the three dinner courses.

Hello Hackers/Viewers, It is a new day, and you might be thinking, It is so boring, why not try to be cool with computers in front of my friends? That is why, I have made this tutorial to make fake viruses using notepad to look cool!

Apple has once again improved functionality of Siri, their personal voice assistant for iPad and iPhone, in iOS 9—and this update is a big one. You can now use Siri to find photos based on location and date, set up contextual reminders, find your friends and family, and more.