
How To: Create Backdoor on OSX
Hello, ladies and gents! Today I will be discussing the fun and excitement of backdoor on an OSX system.


Hello, ladies and gents! Today I will be discussing the fun and excitement of backdoor on an OSX system.

Imagine this scenario: You exploited a system using metasploit and you want to install a backdoor. You have a few options;

On the internet, everything is possible, even if it's not grounded in reality (check no further than anything The Onion publishes). Witty headlines combined with clever photo edits make even the most absurd topic seem like a serious news story. Some of these stories are so convincing that they even fool news organizations, such as the New York Times and even the official newspaper of the Chinese Communist Party. While some of us can tell when something sounds a bit off, others (like our paren...

With only a few days until Apple Watch preorders begin, and just a couple of weeks until its official release, the biggest question in Apple Land seems to be: "Are you going to get an Apple Watch?"

Welcome back, my budding hackers! With this article, I am initiating a new series that so many of you have been asking for: Hacking Web Applications.

Today I am going to teach the various ways that you can use social engineering to hack a system. For those of you that have followed my past tutorials, you know that social engineering can unlock a world of possibilities. This is because no matter how many firewalls, no matter how many patches there are on a server, the password is kept in the minds of people...and people, are not as smart as computers.

Eye contact is key in conversations, job interviews, and honesty, and it can help you access others' thoughts and spot heavy drinkers. Locking eyes with someone can even help you fall in love, whether you know them or not.

Hello my fellow hackers, Welcome to my republished revision of the ruby programming language, Part 1.

We all fall sleep in different ways. Some may require absolute silence, others need white noise, and some enjoy listening to a song or two to help bring on the sleep. If you're in the latter group, like I am, there's a problem. Fall asleep before the music stops, and a loud song may jolt you awake in the middle of the night. With an iPhone, however, that issue can be avoided with a little setup.

Cooking rice, pasta, and other grains in water is so boring. There is a much better way to guarantee they will have your mouth chewing something seriously tasty: cook them in something that isn't water. Alternative liquids such as stock, milk, juice, or even tea will give bland dishes a fresh new flavor boost. If you're not sure how your dishes might taste, never fear: we tested them out. Before getting started, be sure to read this article first so that you know why it's important to rinse y...
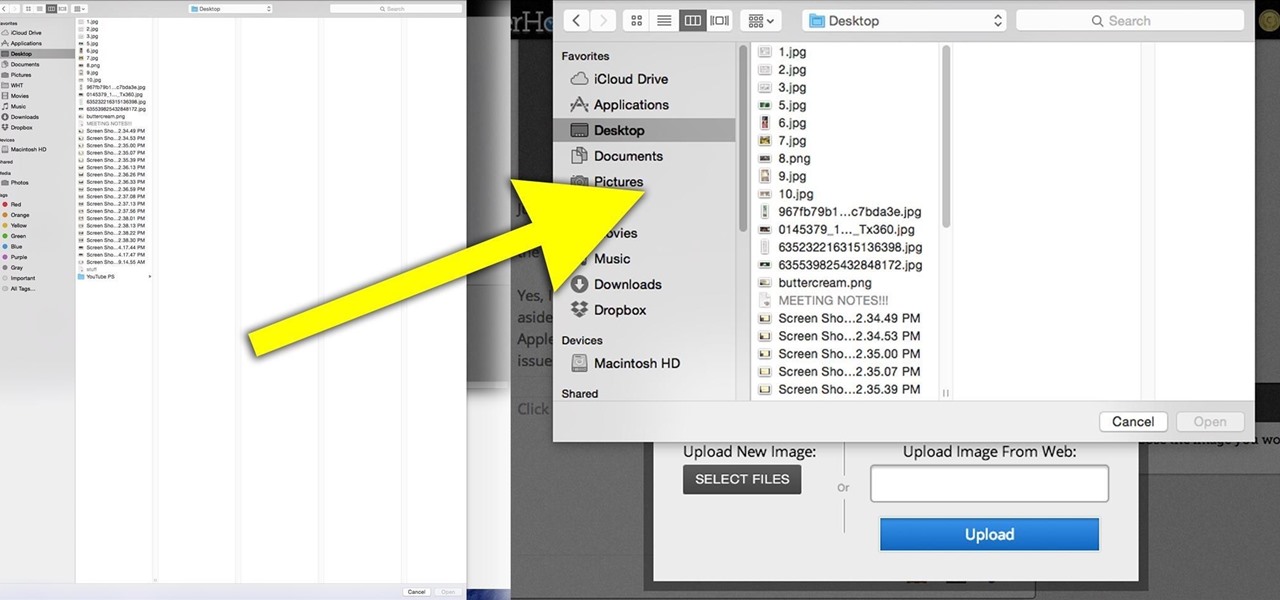
Yosemite is definitely an improvement over Mavericks, but there are still some painfully obvious and annoying bugs that occur within certain apps.
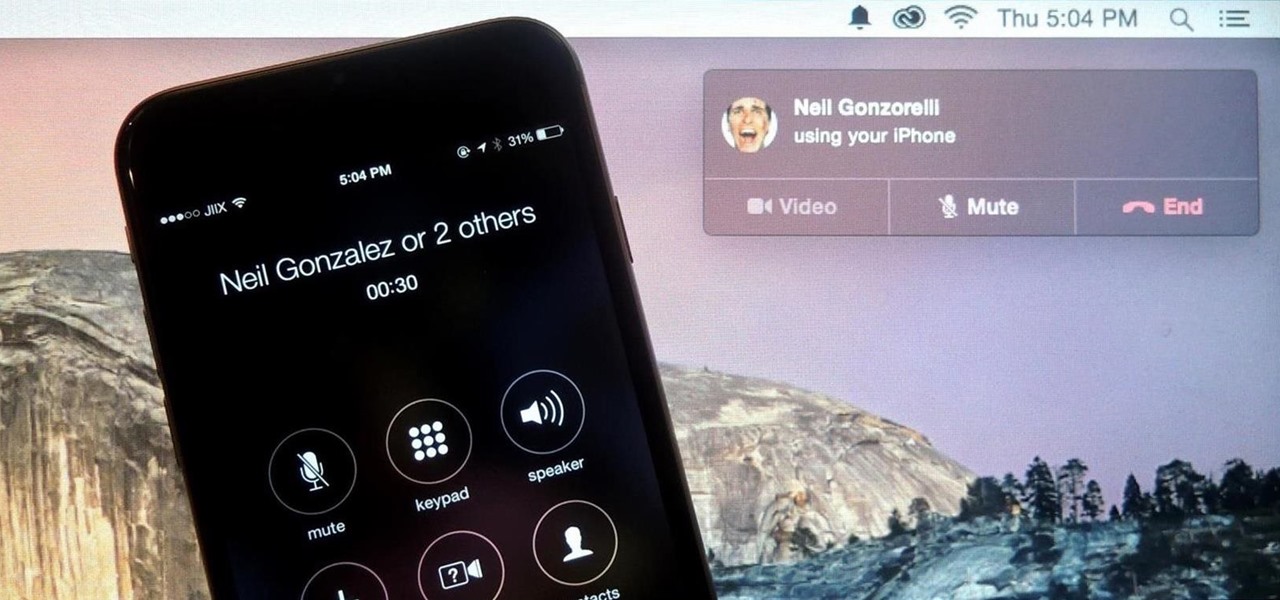
Earlier this year, Apple announced Continuity, a feature for Yosemite and iOS 8 that lets you connect your iOS devices to your Mac in order to access apps, receive phone calls, send text messages, and more while seamlessly switching between the two.

The importance of body language is stressed from an early age: watch those around you, and you'll know what they're thinking. While you might be skilled at deciphering the messages of crossed arms, slouched sitting, eye movements, and hand gestures, the key to understanding those around you is a little less obvious.

Hate slogging through pages and pages of weighty books and lengthy work documents? You may not be able to depend on speed-reading apps, but with the right font, you can increase the number of words you scan each second, speeding up your reading pace exponentially.

Welcome back, my greenhorn hackers! Before we attempt to exploit any target, it is wise to do proper reconnaissance. Without doing reconnaissance, you will likely be wasting your time and energy as well as risking your freedom. In previous guides, I have demonstrated multiple ways to perform reconnaissance including passive recon with Netcraft, active recon with Nmap or hping3, recon by exploiting DNS or SNMP, and many others.

When Android 5.0 rolls out to the Nexus 5, several changes and new features will come along with it. The over-the-air update is already rolling out, and if you don't want to wait, you can get it right now.

Aside from the occasional "creative" collage, most of your friends on social media are content with pretty basic image and video posts. You can easily one-up them with celebrity cameos or awesome time-lapse videos, but to truly outshine them, try your hands at some creative double exposures.
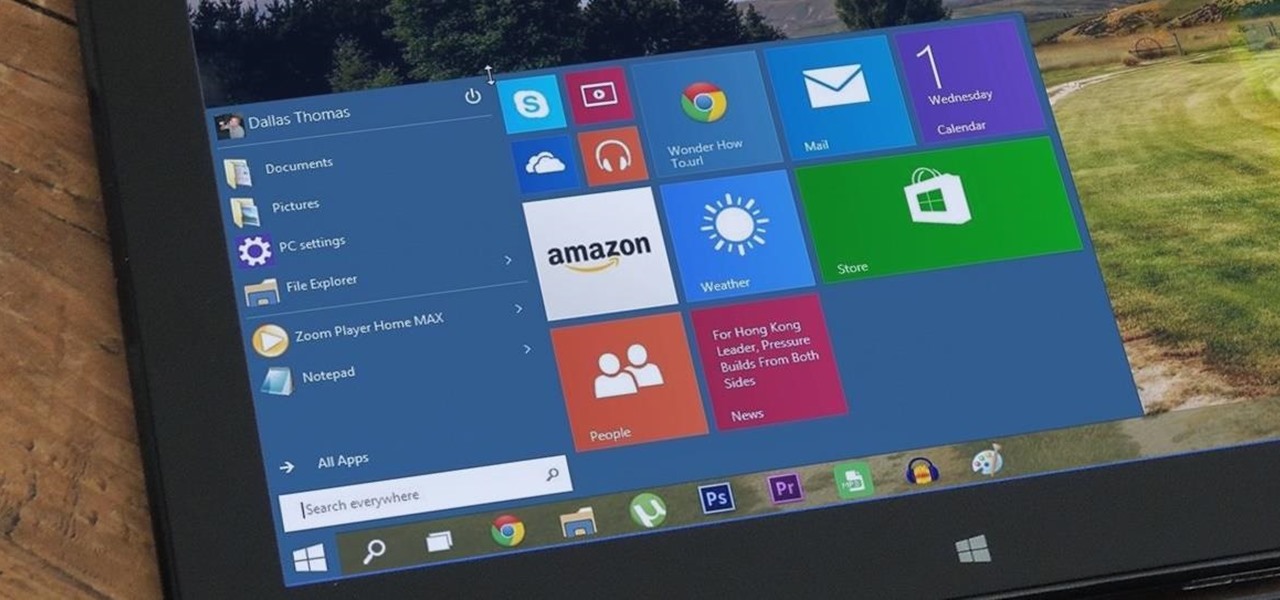
At a closed-door presentation on September 30th, 2014, Microsoft unveiled the latest iteration of its industry-leading operating system. Dubbed Windows 10 (seems as if Redmond isn't too fond of the "9" moniker), this new version brings along with it many UI optimizations and under-the-hood tweaks. With a particular focus on optimizing the interface for traditional mouse and keyboard computers, one of the most noticeable changes is the return of the Start Menu. While touch-optimized devices wi...

One of the best ways to reduce clutter and enjoy the new iOS 8 wallpapers on your iPhone is to use the little-known trick of hiding all of your main home screen apps. This trick effectively moves your apps off the main home screen and over to additional home screen pages, or in your dock, making your main home screen beautifully clutter-free.

There are several reasons why restaurant food tastes so good. One is that the cooks know how to make reductions, which involves cooking down large amounts of liquid until it becomes a pool of thick, glossy sauce. While this technique isn't hard to learn, it can be time-consuming.

What if the code you are trying to reverse engineer is obfuscated or somehow corrupted? What if no way is left? Here comes what I like to call (wrongly and ironically) the "brute force of reverse engineering".

Welcome back, my rookie hackers! Now that nearly everyone and everyplace has a computer, you can use those remote computers for some good old "cloak and dagger" spying. No longer is spying something that only the CIA, NSA, KGB, and other intelligence agencies can do—you can learn to spy, too.

If you've already read the first part exploring what geniuses actually eat as opposed to what the rest of us are told to eat for brain health, you've noticed that there are some big discrepancies. Instead of favoring healthy, wholesome foods high in antioxidants, lots of high-achieving types tend to go for caffeine, sugar, and processed foods. One notable health habit practiced by many: eating breakfast.

Check it out: you save more dough (ba dum bump) when you order a large pizza than with any other size. Why is this true? NPR reporter Quoctrung Bui's engineer friend pointed out that a medium pizza was twice as big as a small one, yet only cost slightly more.

Welcome back, my rookie hackers! Most often, the professional hacker is seeking protected information from the target system or network. This might be credit card numbers, personally identifiable information, or intellectual property (formulas, plans, blueprints, designs, etc.). Most of my Null Byte guides have been focused on getting into the system, but this only begs the question—"what do I do when I get there?"

Let's be real, browser histories are virtually useless. Trying to find something you passed up a week ago is like, pardon the cliché, finding a needle in a haystack.

Last year, The New York Times wrote that certain restaurants in Manhattan and Brooklyn banned patrons from taking photos of their meals. That means no flash photography, no standing on chairs for a better angle, not even a quick pic for your Instagram followers before the first bite. Little do these restaurants know, this ban can actually make their customers' food taste worse, so to speak.

Tequila is a hard liquor that's often been misunderstood. Produced from the agave plant, this aged spirit has complex flavors that bloom the longer it's aged and can rival the finest scotch.

To flip, or not to flip, that is the real question. When you're nervously standing over the stove or grill, what do you do with that steak before you?

One of the down-sides of international long-haul travel is layovers between flights in unfamiliar places. We have a flight to Europe this year via Guangzhou, China, and I've been putting together my notes on how to make the best use of 7 hours between flights, which I'd like to share.

As fellow softModders, I'm sure you strive to find any and every way to make your phone unique. Wallpapers and icon packs are great to get started, but to really stand out from the rest, try changing your HTC One's boot animation.
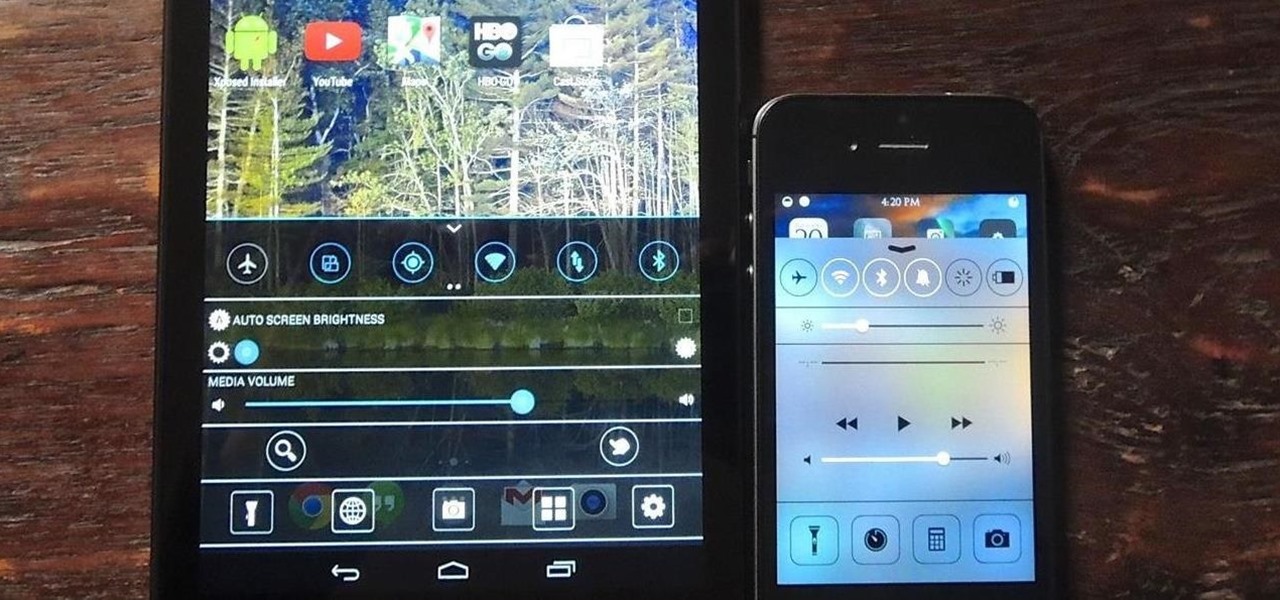
There are two types of tablet users in the world—those who like their quick settings up top, and those who want them on the bottom. I fall into the latter category, and there are a couple of reasons for it.

A picture is worth a thousand words, and depending on what you're taking a picture of, it could be worth a lot more. Our phone's camera can easily capture high quality photos, scan barcodes, and make us Instagram famous. You can compare prices of items and download applications just by scanning a QR code. Of course, we can always do this stuff a little bit better on our iPhones.

The lock screen music player in iOS 7 has all the controls you'd ever need from a lock screen, but it's not as visually appealing as I hoped it would be. Yes, it does show you the album cover art, but the way everything is presented makes it feel cluttered.

Welcome back, my apprentice hackers! As many of you know, I have been hesitant to adopt the new Kali hacking system from Offensive Security. This hesitancy has been based upon a number of bugs in the original release back in March of 2013 and my belief that BackTrack was easier for the novice to work with.

You probably already know by now that a custom Android ROM can change your user experience and give you what feels like a new OS on your device, and there's no shortage of them out there to try out.

Parlez-vous français? While we all wish we were fluent in multiple languages like Jason Bourne, most of us are probably one-trick ponies. When traveling abroad, or even when taking language courses, having a translator handy is extremely important.

It's no surprise that Costco has great deals, and that's why millions pay annual fees for the privilege to shop in their wholesale outlets. Just take their hotdog and soda combo for $1.50—it's the same price now as it was 27 years ago.

This tutorial is for everyone who is trying to learn how to windsurf. If you already know how to windsurf and just want to freshen up on the theory or if you have never tried it and want to give it a go, this is the series to check out.

The space on your phone is extremely valuable, so getting the most out of your screen real estate can help you out when multitasking or for just making your device feel bigger. One thing that is often overlooked when it comes to saving space on the screen is the keyboard.