Welcome back, my fledgling hackers! Hacking has a long and storied history in the U.S. and around the world. It did not begin yesterday, or even at the advent of the 21st century, but rather dates back at least 40 years. Of course, once the internet migrated to commercial use in the 1990s, hacking went into hyperdrive.

Greetings all. Today I intend to append a new series to my mini-collection of posts. This series will consist of informative guides for the purpose of depicting certain aspects of the White Hat profession that I believe are of profound importance. Furthermore, I will keep this series simple for everyone to follow, regardless of your tech level. So without further ado, let's get right into it.
Have you ever used an open wifi, which after you connect displays a website to enter your credentials to get internet? That website is called captive portal and widely used in airports, hotels, universities etc. Have you ever wondered what would happen if someone would set up an open wifi with the same name displaying a very similar web page asking for credentials? Usually if there are multiple wifi networks with the same name and encryption, devices only display the one with the highest sign...

Hi, everyone! Recently, I've been working on a pretty interesting and foolish project I had in mind, and here I'm bringing to all of you my findings. This guide's main aim is to document the process of building an Android kernel, specifically a CyanogenMod kernel and ROM, and modifying the kernel configuration to add special features, in this case, wireless adapter Alfa AWUS036H support, one of the most famous among Null Byters.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Making a good pie crust can seem intimidating to the uninitiated, but once you master this skill, a whole world opens up to you. Not only can you make all manner of fruit, custard, and cream-filled pies once you know all the tricks, you can branch out into the world of quiches, savory pies, and flaky, crispy turnovers, too. We've already told you how to get perfect, firm fruit pie fillings, so now, let's learn about crust.

My first encounter with a phablet was late last year with the AT&T version of the Samsung Galaxy Note 2, having never touched or even seen its highly-acclaimed and pioneering predecessor. Initially, I was a bit overwhelmed by the enormous screen and taken aback by the dated stylus, which brought up ugly memories of my dad using his ten pound PalmPilot.

Despite the security concerns that have plagued Facebook for years, most people are sticking around and new members keep on joining. This has led Facebook to break records numbers with over 1.94 billion monthly active users, as of March 2017 — and around 1.28 billion daily active users.

I don't know how many of you had this experience in your youth, but when I was a kid, I used to actively think about what would happen if I suddenly woke up in a fantasy land, or were to pass through a portal into another space and time. I knew it wouldn't really happen, but when you're a kid, these can be important issues to you. So I slept with my glasses on every night, just in case. Photo from George Pal's The Time Machine.

One of the hardest, most intimidating parts of making your own Steampunk guns from scratch is the wooden stock of the gun. To be fair, it's probably the hardest part. It requires the most artistry, and is the easiest to mess up.

In the first part of this two-part guide, I covered cutting, grooving, beveling, making holes, and stamping/tooling. I hope you enjoyed that part, because we're pushing the accelerator to the floor and moving ahead at full speed!

Notch loves Halloween. He must, because he keeps putting scarier and scarier things into Minecraft around Halloween time!

This article is a guide for making Chainmail Armor from start (simple wire) to finish (a finished chainmail shirt). We will be using the European 4 in 1 weave, as this is the most common weave. This is the weave that you usually see in movies. There are several sections to this guide: Materials, Making the Rings, Weaving the Rings, and Making the shirt.

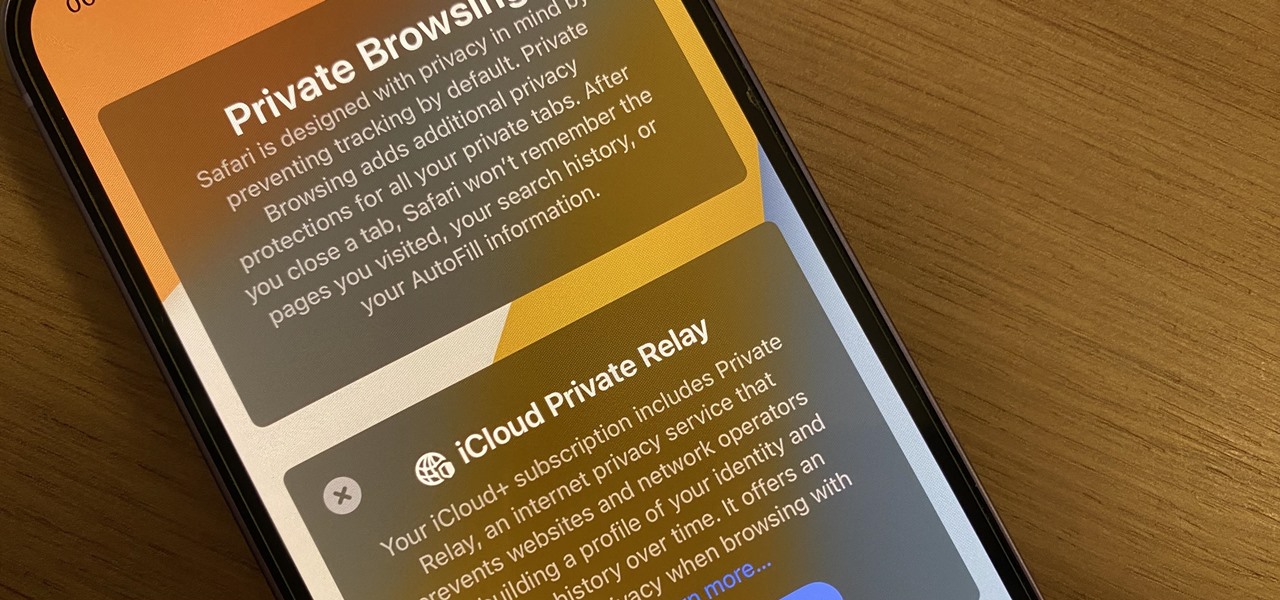
Visit a webpage on your iPhone, iPad, or Mac, and there's a good chance you'll be bombarded with distractions such as ads, fullscreen pop-ups, cookie consents, log-in requests, notifications, email signups, sticky videos, and calls to action. If you're using Safari and content blockers, "Block Pop-ups," and Reader mode can't hide the elements you need, Apple's got a new tool you should be excited about.

There are many ways to calculate basic math problems and solve algebraic equations, geometric expressions, and trigonometric functions on your iPhone, but Apple just came out with one that will blow you away.

Apple has already released iPadOS 18, but there still may be work to complete on iPadOS 17. That brings us to iPadOS 17.8. Is there one, and can you test-drive it on your iPad?

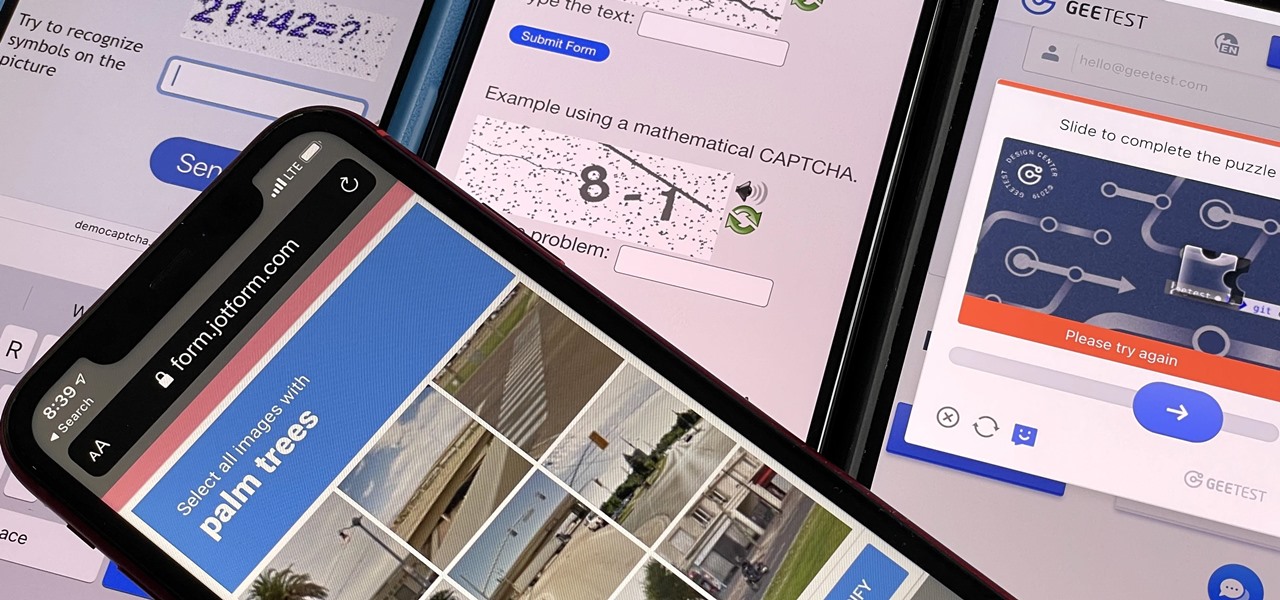
Some websites require you to perform a verification task so they know you're human and not a bot. It helps websites curb spam, abuse, unauthorized access, and cyberattacks but also adds an obstacle for anyone trying to visit their content. If you find it more of a nuisance than a necessary evil, there's an easy way to reduce the number of human verification prompts you receive on your iPhone, iPad, and/or Mac.

Apple just released its biggest update to iOS 17 yet, and there are 60 exciting new changes for your iPhone. With iOS 17.2, you get a brand new app, more Apple Music enhancements, upgrades in Messages, and a new security feature that was announced last year, as well as changes for Weather, notifications, Apple TV, Books, and more.

Safari's massive upgrade in Apple's latest iPhone software update includes new features you won't find in any other web browsers on iOS, from better ways to stay organized to enhanced security and further privacy protections.

Gaming just got easier, thanks to Apple. A secret feature on your iPhone or iPad makes it so much easier to beat that level or opponent you can't seem to defeat, and it can even help you learn to play a new game faster.

Apple's Always-On display feature for the iPhone 14 Pro and 14 Pro Max can show important information on the screen even when the device is sleeping. While the dimmed Lock Screen may seem like a WYSIWYG component, there are actually a few ways you can customize it to fit your needs better.

Your iPhone's Camera app isn't the only place you can use Portrait mode for selfies. An easy-to-miss feature built right into iOS lets app developers leverage Apple's powerful Portrait mode effect in their own apps, so you can add a shallow focus effect to photos and videos when using the front-facing camera in FaceTime and apps like Facebook, Instagram, Snapchat, and Zoom.

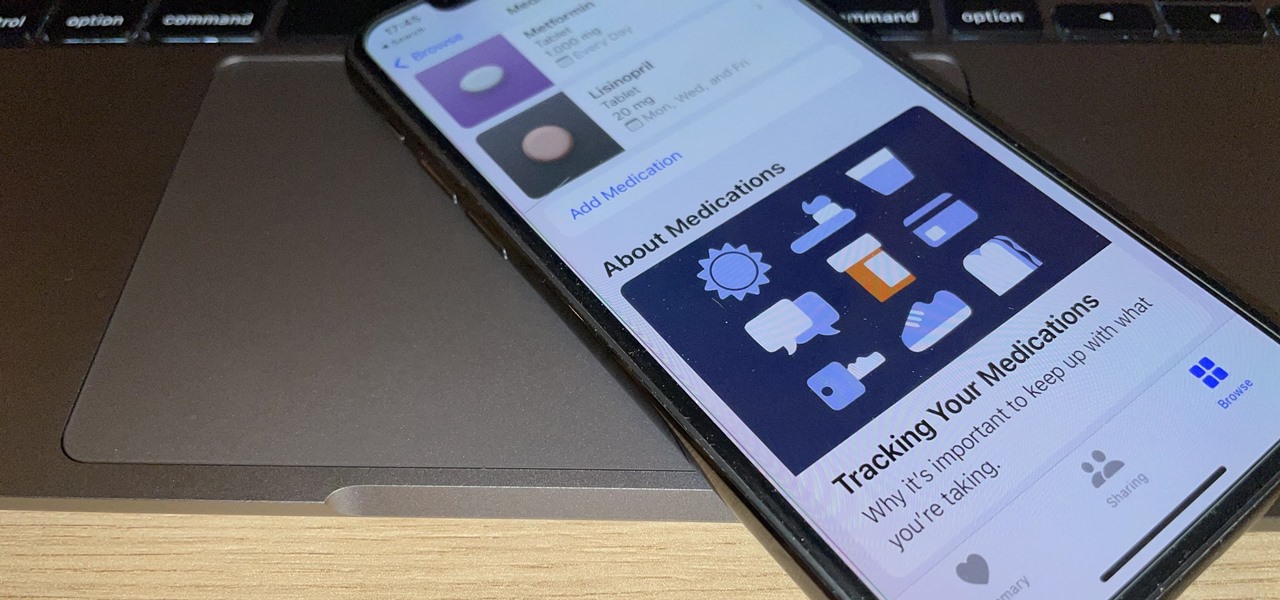
You've probably already been using iOS 16 on your iPhone for months, but there's a good chance you haven't found or explored everything the new software has to offer. Health-related features are usually the first to be ignored or go unnoticed, but they're essential to know about even if you don't plan on using them right away.

Customization has always been the main draw of Android for me, but Apple has an impressive feature on iOS 16 that lets iPhone users create customized emoji wallpapers for their home and lock screens. While Android doesn't have something like that built-in by default, it's easy enough to make emoji wallpapers for your Android phone.

When the topic of Pokémon Go comes up, the typical response is, "Do people still play it?" The answer is a resounding yes!

You may prefer reading news stories, web articles, and books on your iPhone over listening to them in spoken form. Still, sometimes it's necessary when driving, walking, cycling, cleaning, working, or performing other activities requiring a little multitasking. To help you out, Apple has a text-to-speech service on your iPhone — you just need to know how to find and set it up.

One of the most useful new features Apple included on iOS 16 lets you instantly lift the subject out of a photo, separating it from the background. Once extracted, you can paste, save, or drop the cutout wherever you want as a new image, and you can even make it a sticker in messaging apps.

Some apps look great with Dark Mode, and some do not. So when you have system-wide Dark Mode enabled on your iPhone and are using an app that only looks good in Light Mode, you'd normally have to turn the dark appearance off manually, then switch it back on when you leave. But there's a workaround that can automate the process for you.

Have you ever seen an image on social media, somebody's blog, or a news website that shows an iPhone or iPad screenshot with an actual iPhone or iPad model framed around it? You can do that too, and it's really easy to accomplish with a third-party app — but you can do the same thing with a shortcut that won't bug you to pay or subscribe.

While hitting snooze won't help you much if you fall back asleep, it can help you wake up more gently. However, your iPhone's default nine-minute snooze may be too long or too short for your preferences. If you tend to fall back asleep quickly, you might be better with a two-minute snooze.

There are many things your iPhone or iPad can do, and Apple does an excellent job of documenting everything on its website. But there are some features that won't show up in any Apple manuals or help pages.

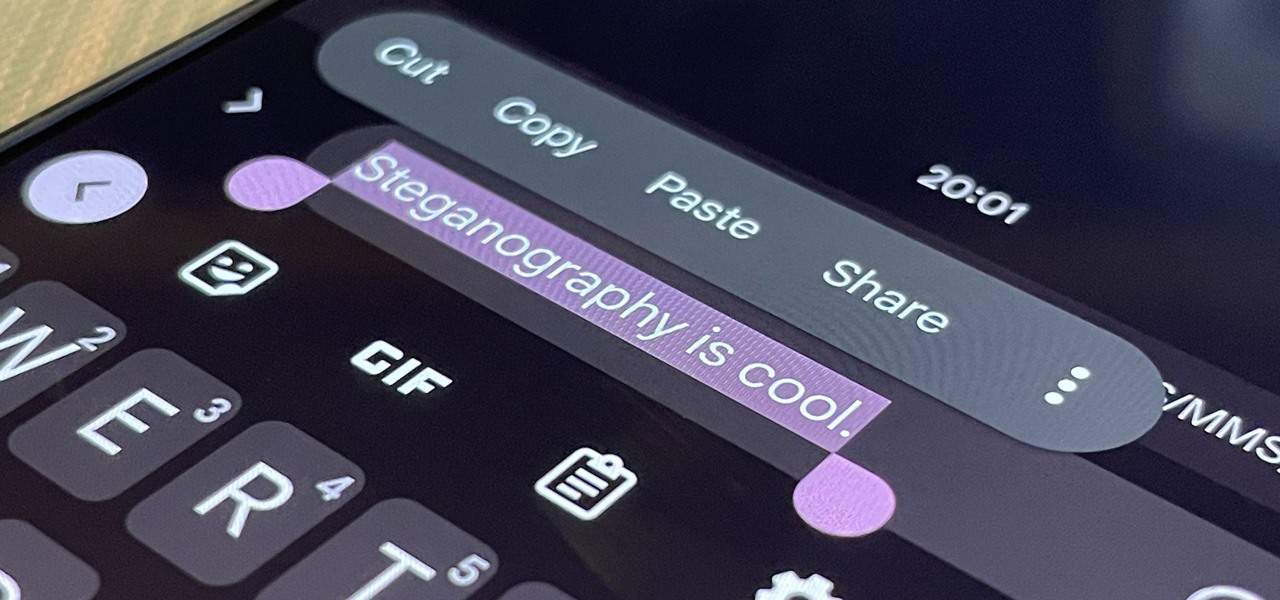
With a simple web-based tool, you can hide secret messages for family, friends, and fellow spies inside of plain text communications, and anyone that intercepts the messages will be none the wiser.

You've probably already used a few Safari Extensions on your Mac, but if you haven't explored Safari's web extensions on your iPhone yet, you're missing out on some fantastic possibilities to increase productivity, make tasks easier, filter out noise, and bring more fun to your browsing experience.

If you've recently built a Wi-Fi spy camera out of an ESP32-CAM, you can use it for a variety of things. A baby monitor at night, a security camera for catching package thieves, a hidden video streamer to catch someone going somewhere they shouldn't be — you could use it for pretty much anything. Best of all, this inexpensive camera module can perform facial detection and facial recognition!

In the Facebook app for Android and iOS, the shortcut bar has a few necessary tabs to go home and view notifications and settings. But other tabs can make the interface feel cluttered if you don't use them often enough — or at all. Thankfully, there's a quick trick to get rid of them for a cleaner navigation bar.

Apple pushed out the Release Candidate for iOS 14.6 on Monday, May 17. The 18F71 build includes new features and bug fixes, including an option to unlock your iPhone with Voice Control. It comes just hours after Apple announced Spacial Audio and Lossless Audio playback for Apple Music, new features that will require iOS 14.6 to run.

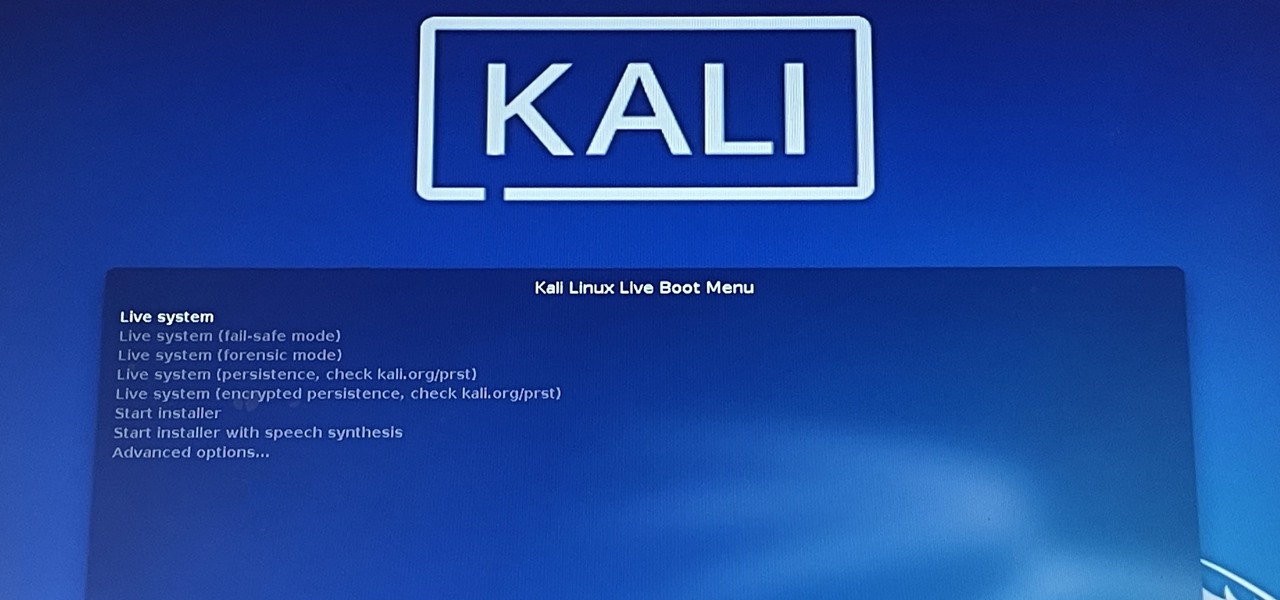
Kali Linux is the go-to Linux distribution for penetration testing and ethical hacking. Still, it's not recommended for day-to-day use, such as responding to emails, playing games, or checking Facebook. That's why it's better to run your Kali Linux system from a bootable USB drive.

If you buy an Android phone from any of the big US carriers, it will come with several extra apps in addition to any apps the manufacturer preinstalled. It's all in the name of profit, of course. Some of these apps are from companies that paid the carriers to distribute their software, and some are from the carriers themselves, usually aimed at upselling you or perhaps collecting a little data.

While obvious, it's a lot more difficult to hack into a locked computer than an unlocked computer. As a white-hat hacker, pentester, cybersecurity specialist, or someone working in digital forensics, there's an easy solution — make it so that the computer won't fall asleep and lock automatically in the first place.

Outside of iPhone releases, software updates are arguably the most exciting aspects of iOS life. It's like Christmas morning when your iPhone installs an update, as you dive through your device to find all the new features and changes Apple thought to include. With iOS 14.4, there are at least 10 such new additions just waiting for you to explore.