As we approach the holiday (i.e. gift-giving) season, don't forget to make sure to include the usual notes in your gifts indicating that they can be returned. Otherwise, you'll just cause the recipients to save your gifts until they can be properly regifted onto some other ungrateful chump.

Anything free is cool, but getting a fully upgraded operating system for the great price of nothing is downright awesome. A recent exploit was uncovered that allows users to get a free copy of Windows 8 Pro directly from Microsoft's own website. Seriously.

As a technology writer, phone screenshots can pile up on your computer in no time. Testing out different apps, showing buggy software, and doing step-by-steps can lead to a plethora of mobile screenshots piling up on your computer's desktop. The problem with my screenshots is that they save as photo.png or photo.jpeg, as do many of my other photos. If I haven't finished a project or article, I tend to move them to different folders to save them for later. After a while, the screenshots begin ...

Cooking isn't something that interests me much, unless it results in a fast burning fuel and a successful rocket launch!

Thanks to Flutter, it's now possible to control the music on your computer simply by making a few hand gestures. The app is available for both Windows and Mac and uses your computer's webcam to monitor your hand movements. Through the use of a few simple hand movements, you can play, pause, forward or replay your music. Flutter works with iTunes, Spotify, Quicktime, MPlayerX and a few other programs.

Sea otters are the largest members of the weasel family. When people started hunting sea otters for their fur, their population fell from roughly 225,000 to about 1,500, until the International Fur Seal Treaty took effect in 1911. Since the international ban on otter hunting, the population has rebounded back to roughly 107,000.

Steam is an online platform that lets you download and play over 2,000 video games, from first-person shooters to RPGs, as well as a pretty long list of indie games. You can play on your PC, Mac, mobile device, or even your television, and it has a community of over 40 million gamers. Prices are different depending on the type of game and how new/popular it is, but they're generally about the same as what you'd pay for an Xbox or PlayStation version. They also have a decent list of free games...

In my first few articles, we focused on operating system hacks. These hacks have been primarily on older operating systems such as Windows XP, Windows Vista, and Windows Server 2003.

Earlier this month, Adam Cudworth, 19, launched a camera attached to a weather balloon into the edge of space. Battling tough winds, freezing temperatures, atmospheric pressure and tumbling speeds, the teenager from Worcestershire, England was able to capture these amazing pictures of the Earth's upper stratosphere. How to Send a Camera into Space

Got an upset stomach or a little heartburn? America's favorite pink pill will cure it right up. But did you know that there's actually metal hiding in those chewable Pepto-Bismol tablets? Yes, metal. Technically, it's a poor metal, but metal's metal, right? Well, we do tend to eat a lot of iron in our diets, because it carries oxygen throughout our bodies, so consuming metallic minerals isn't anything abnormal. But you'd never think that Pepto-Bismol is actually made up of metal.

WonderHowTo has seen its fair share of dragon-related projects, from dragon wings, to dragon kites, to less-complicated origami dragons, but we've yet to see anything quite like this. Radio-control plane builder Richard Hamel built this incredible seven-foot-long, fire-breathing dragon using a JetCat P80 turbine and a 50,000 volt stun gun, with a 2.4-gigahertz touchscreen radio controller to fly it.

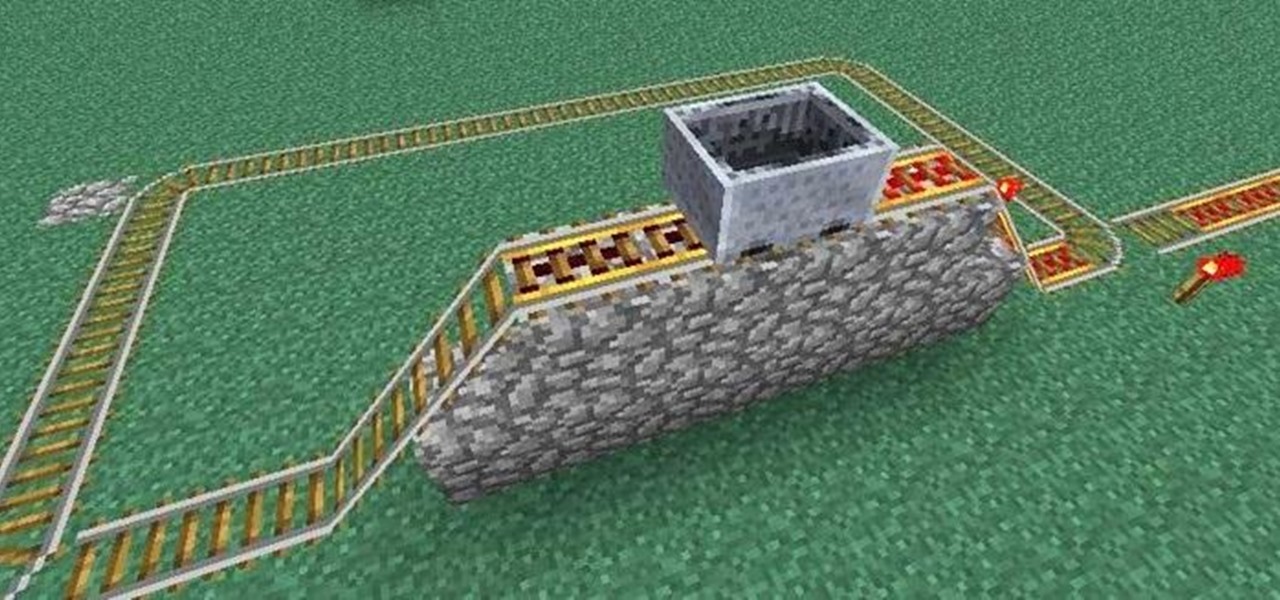
What's nice about Minecraft 1.3 is that it makes minecart stations so simple. Before, you needed redstone and buttons and powered rails in order to make a good minecart station. Now you hardly need anything at all! That said, if you want to be snazzy, all of the minecart stations we covered in this earlier article are still completely functional. You may also want to check out this article on how to make empty minecarts come back to you, if you want some extra bells and whistles.

Believe it or not, it's possible to make your very own lava—if you have a furnace capable of heating up to 1,200 degrees Celsius, that is. Bob Wysocki and Jeff Karson started the Syracuse University Lava Project to study basaltic lava and give students a hands-on way (hypothetically, of course) to learn about it. Oh, and they also want to use it for art projects. Sign me up for that class! It all starts with 1.1 billion-year-old basalt gravel, which apparently anyone can buy. They put the gra...

At a very early age, I would go on summer camping trips. I remember every night being handed a pack of sparklers that were my own, to swing around wildly, which gave me many valuable life lessons on cause and effect.

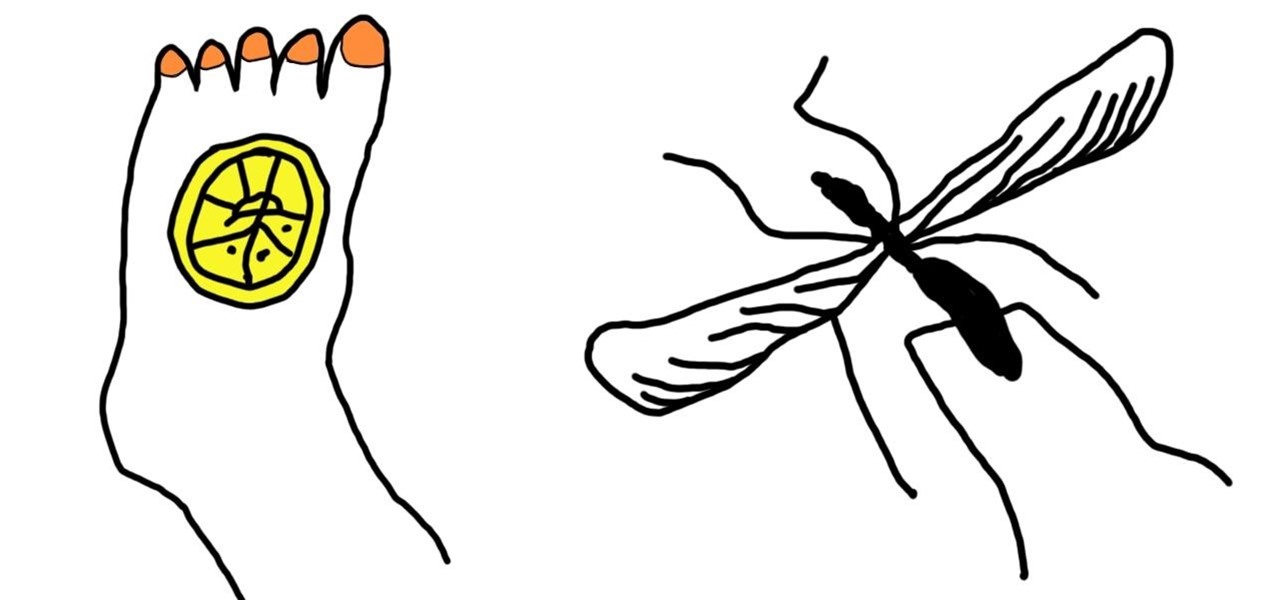
There are few things peskier in the summer than an unexpected mosquito bite swelling up on your arms and legs. Fortunately, there are many ways to heal your body of its annoying itch, ranging from fruit (lemon slices and banana peels) to common household items (baking soda and apple cider vinegar).

Everyone who owns or runs a website needs to know how they can improve traffic, and search engine optimization is the answer. This 13-part video series on SEO basics and strategies will give you more traffic for your site. It's jam-packed full of tons of great SEO tips! Check out each video in the series:

The most used and most washed articles of clothing are undergarments. Underwear, specifically bras and panties, are in desperate need of attention after each and every use. They're not like a pair of jeans, wearing them twice in a row is not a good idea, nor clean. Shabby’s not chic when it comes to lingerie. Use a little extra care to keep your lace and silk bras and panties looking good.

Wedding insurance, vacation packages, travel discounts – the American Automobile Association offers its members more than free towing.

When you're a writer with work published across various online platforms, building a portfolio of your work can be pretty time-consuming. That's where Authory comes in.

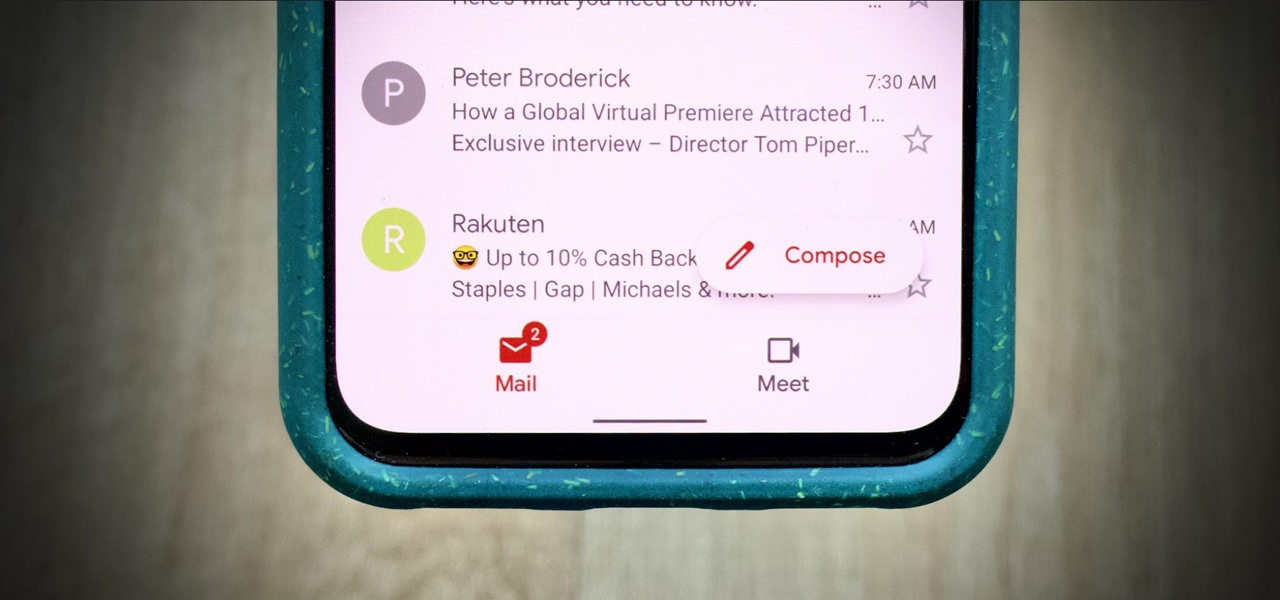
The new Google Meet integration in the Gmail app isn't quite subtle, to say the least. The feature takes up a huge chunk of the display, screen real estate that would otherwise be occupied by, you know, emails. While Google doesn't require you to live with the integration, it doesn't make it clear how to disable it. That's where we come in.

Determining the antivirus and firewall software installed on a Windows computer is crucial to an attacker preparing to create a targeted stager or payload. With covert deep packet inspection, that information is easily identified.

New year, new me. You finally committed to working on the best physical you by going to the gym multiple days a week. Except about an hour in, you start getting really tired of it all. Before you run to the exit, pick up your phone.

Google is an incredibly useful database of indexed websites, but querying Google doesn't search for what you type literally. The algorithms behind Google's searches can lead to a lot of irrelevant results. Still, with the right operators, we can be more exact while searching for information that's time-sensitive or difficult to find.

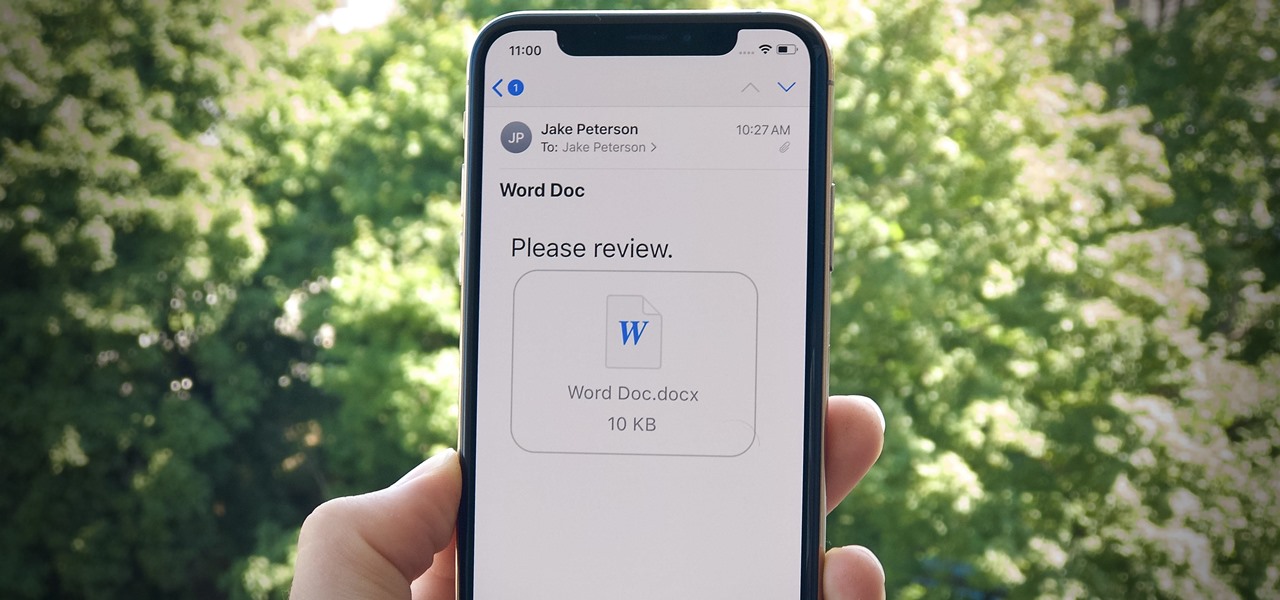
There's no doubt that Microsoft Word is the go-to for businesses worldwide. As such, you might receive Word documents to open on your iPhone, whether or not you actually have Word for iOS installed. If you prefer editing text documents with Pages, Apple's own word processor, you can import and export Word docs easily.

Microsoft.com is one of the most extensive domains on the internet with thousands of registered subdomains. Windows 10 will ping these subdomains hundreds of times an hour, making it challenging to firewall and monitor all of the requests made by the operating system. An attacker can use these subdomains to serve payloads to evade network firewalls.

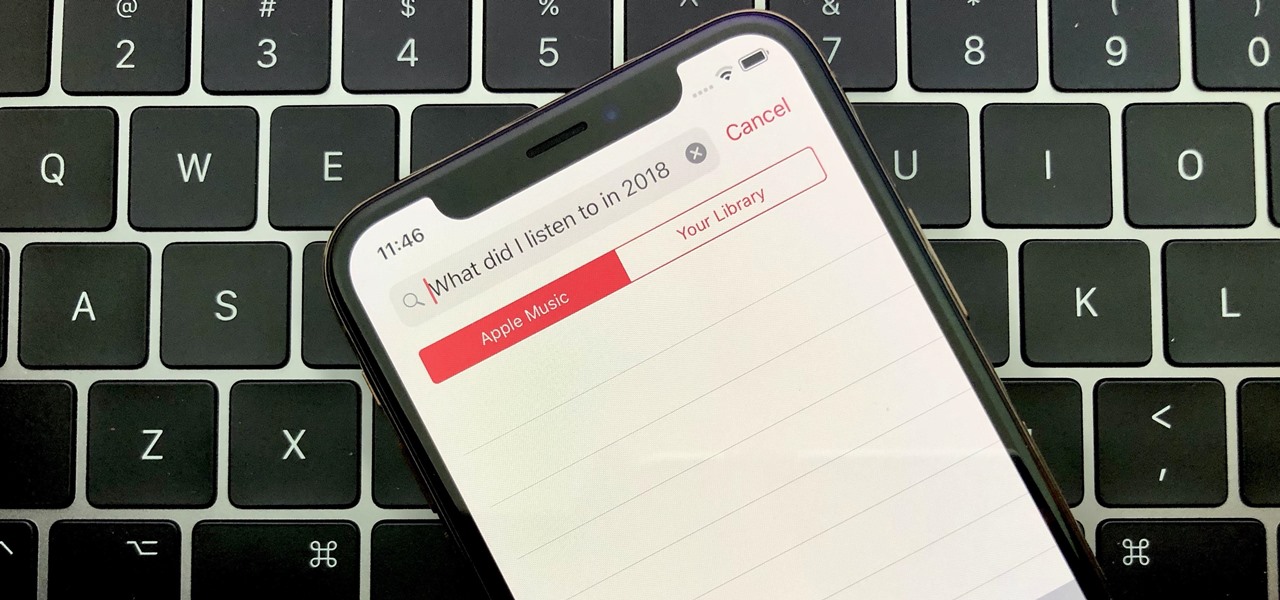
Around the end of each year, Spotify offers a year-in-review service so its users can see what they listened to the past year and share their listening histories in fun infographics. Apple Music does not have such a feature, unfortunately, but there is a way to curb that FOMO feeling this holiday season by downloading your listening history not just for 2018, but for the entire lifespan of your account.

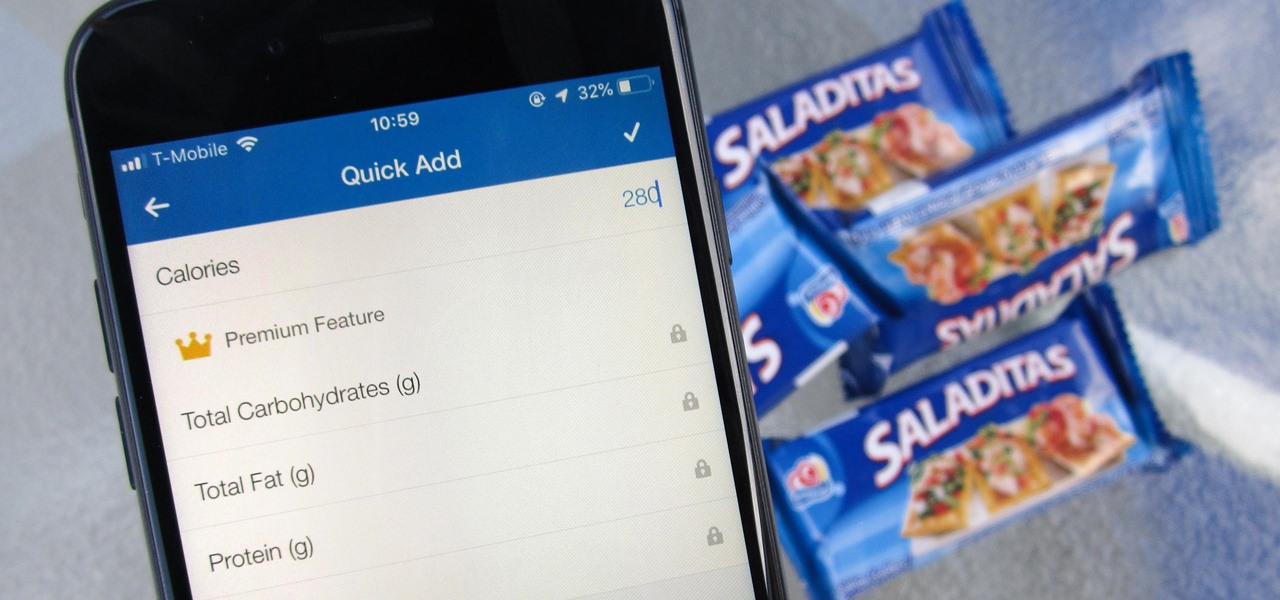
It's only normal to snack on a few french fries every once in a while when you're on a diet, but it's still important to hold yourself accountable, even when you cheat just a little bit. MyFitnessPal, for both Android and iOS devices, has a database of nutritional information to help keep track of the meals you eat, but it also has a way to add calories on the fly without digging for data.

It's not uncommon for hackers to attempt to move laterally between devices in proximity of a compromised device to maintain a prolonged presence in the network. Malware utilizing USB flash sticks to self-replicate and compromise air-gapped machines isn't a new concept.

As penetration testers, we sometimes need to securely store customer data for prolonged periods. Bruteforce-resistant, vault-like containers can be created with just a few commands to protect ourselves from physical attacks and unintended data disclosures.

In most macOS hacks, a non-root terminal is used to create a backdoor into the device. A lot of damage can be done as a low-privileged user, but it has its limitations. Think twice before granting a file permission to execute — an attacker might be able to convert your harmless scripts into persistent root backdoors.

After backdooring a MacBook not protected by FileVault or using a fake PDF to gain remote access, an attacker may wish to upgrade their Netcat shell to something more fully featured. While a root shell allows attackers to remotely modify most files on the MacBook, Empire features some useful post-exploitation modules which make hacking Macs very easy.

While hackers have taken advantage of numerous vulnerabilities in Adobe's products to deliver payloads to Windows users via PDF files, a malicious PDF file can also wreak havoc on a Mac that's using the default Preview app. So think twice before double-clicking a PDF open on your MacBook — it might just be a Trojan with a rootkit inside.

When you leave your iPhone on a table or anywhere within somebody else's eyeshot, a private message may pop up on your lock screen that could be read by anyone who sees it. But there's a way to keep others from reading your possibly sensitive text messages and emails without giving up the convenience of lock screen notifications entirely.

After a hacker has configured Metasploit on a remote private server, created a resource script for automation, and created a simple payload, he or she can begin the process of remotely controlling someone's Windows 10 computer with just a few moments of physical access — even if the computer is off.

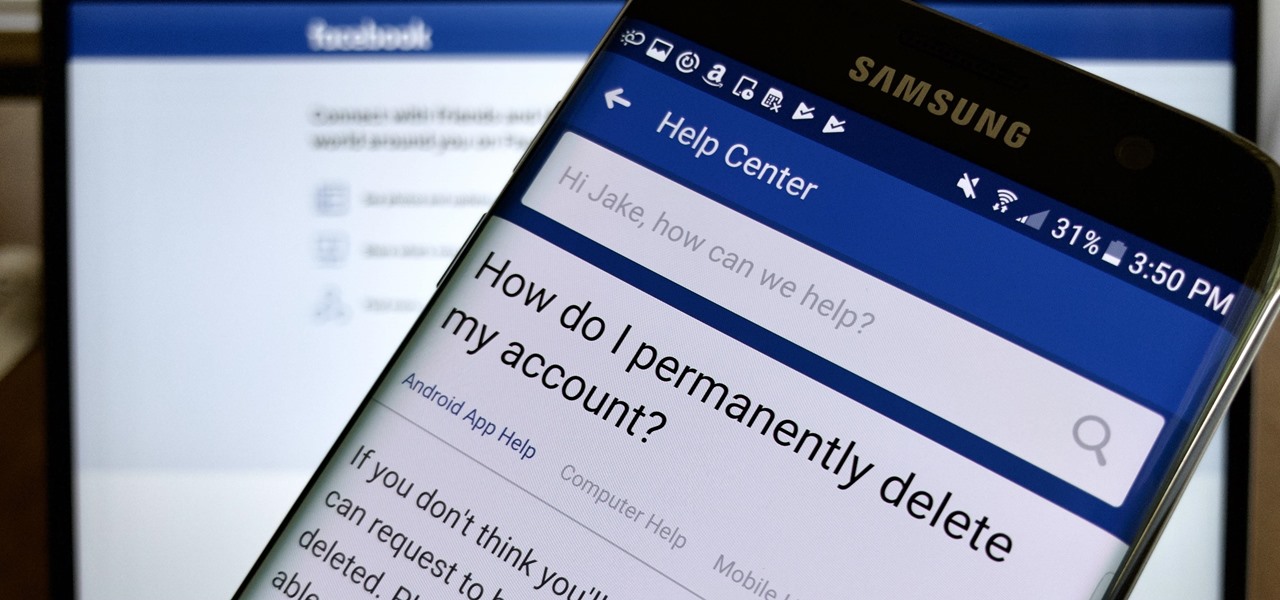
With the news that Cambridge Analytica obtained over 50 million Facebook users' information without their consent, there are no doubt many of us considering that terrifying yet alluring endgame — deleting Facebook. While difficult to figure out, deleting your Facebook account is actually a quick affair. You just need to know where to look.

One unique feature of Firefox Mobile is extensions. Extensions allow users to add in features that didn't originally come with the browser. These add-ons provide an array of features, including improvement to privacy and security.

The Pixel 2 has finally arrived. Google unveiled their newest flagship phones on October 4th, and there's quite a few changes in store. For one thing, most of Google's official renders have already showed us something new: The Pixel 2 and Pixel 2 XL will have a Google Search bar at the bottom of their home screens.

In my previous article, we learned how to generate a vulnerable virtual machine using SecGen to safely and legally practice hacking. In this tutorial, we will put it all together, and learn how to actually hack our practice VM. This will provide some insight into the methodology behind an actual attack and demonstrate the proper way to practice on a VM.

Recently, I ran across SecGen, a project which allows a user to create random vulnerable machines. I absolutely love vulnerable machines, since a vulnerable VM is a safe and legal way to practice hacking tactics, test out new tools, and exercise your puzzle-solving skills.

While the iMovie application for Mac has a few more bells and whistles, Apple's mobile version of its video-editing program is jam-packed full of features and more intuitive than its big brother. Still, before you dive right in to become a movie editor on your iPhone, it's good to know the basics first.