
How To: This Yogurt Trick Will Help You Get Professional-Tasting Sourdough Bread at Home
Sourdough is a delightful twist on your traditional bread, but creating and maintaining a sourdough starter can be a headache for many home bakers.


Sourdough is a delightful twist on your traditional bread, but creating and maintaining a sourdough starter can be a headache for many home bakers.
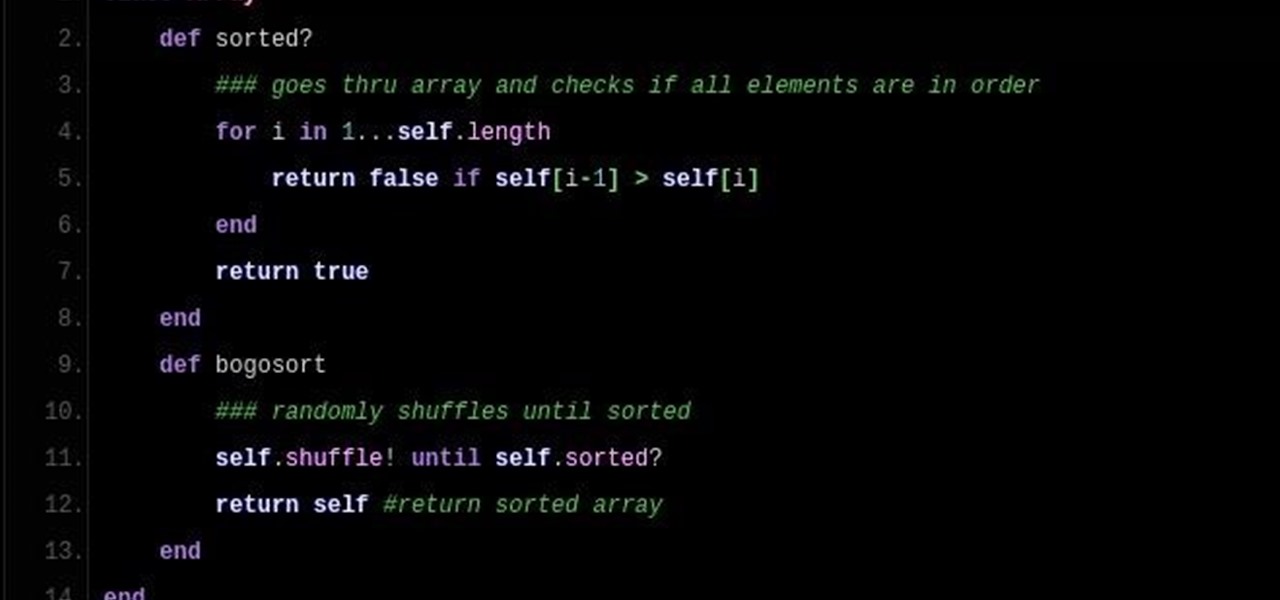
So DTM insisted I write up a little article on Bogo Sort. What Is Bogo Sort?

This is not essentially the next part in the series, but an expansion of previous part about why should you not use cryptocurrencies.

Welcome back, everyone. In the previous part of this rapid-fire miniseries, we built the attacker portion of the shell. In this article, we'll just be testing it to see if everything works correctly.

Hello ladies and gentlemen, PySec here coming at you with another informative(hopefully) article for you all. In the last tutorial, we finally finished our discussion about IP Addressing and I intentionally didn't mention a really important concept with which IP Addressing wouldn't be feasible without it. What I'm talking about is how our network device gets the IP Address in order to communicate with other devices on the network/Internet. There are many different ways for that to be accompli...
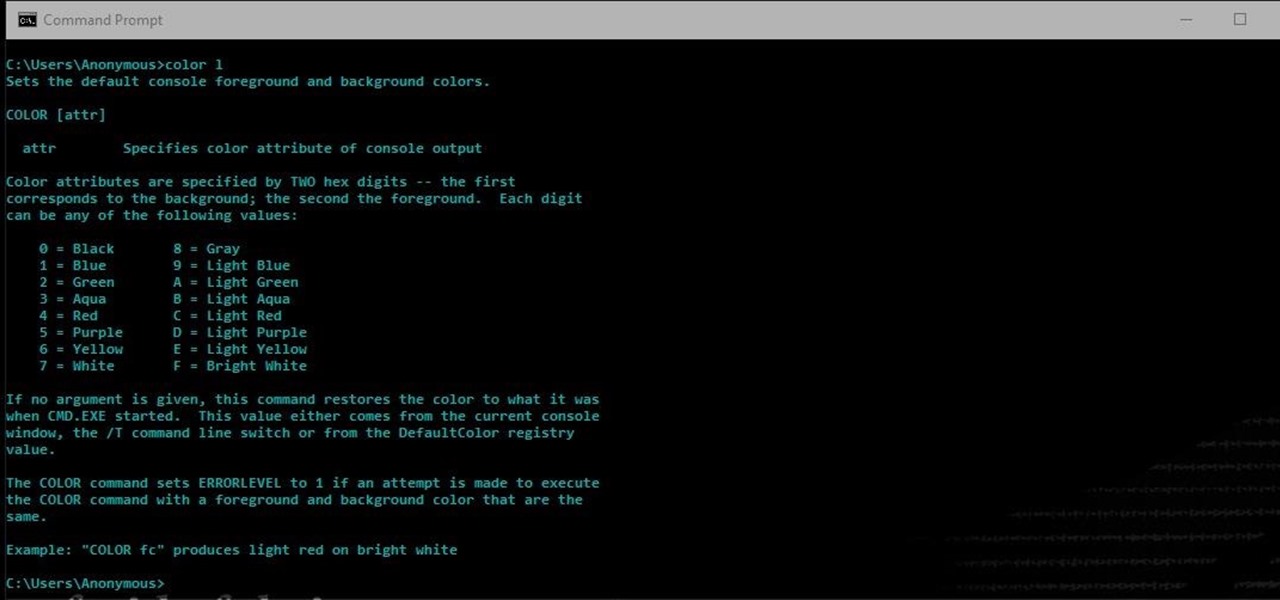
Another series I am now starting, might have to slow down on all of these series, but why tf not. What Is CMD?

Samsung makes some wonderful phones, but one thing I've noticed is that battery life can start to degrade over time, causing the phone to die a lot faster than it used to. If you've been experiencing this issue, and have asked yourself, "Why does my Galaxy S5 die so fast?" there are a few likely causes—and we've got you covered with troubleshooting tips and simple fixes below.
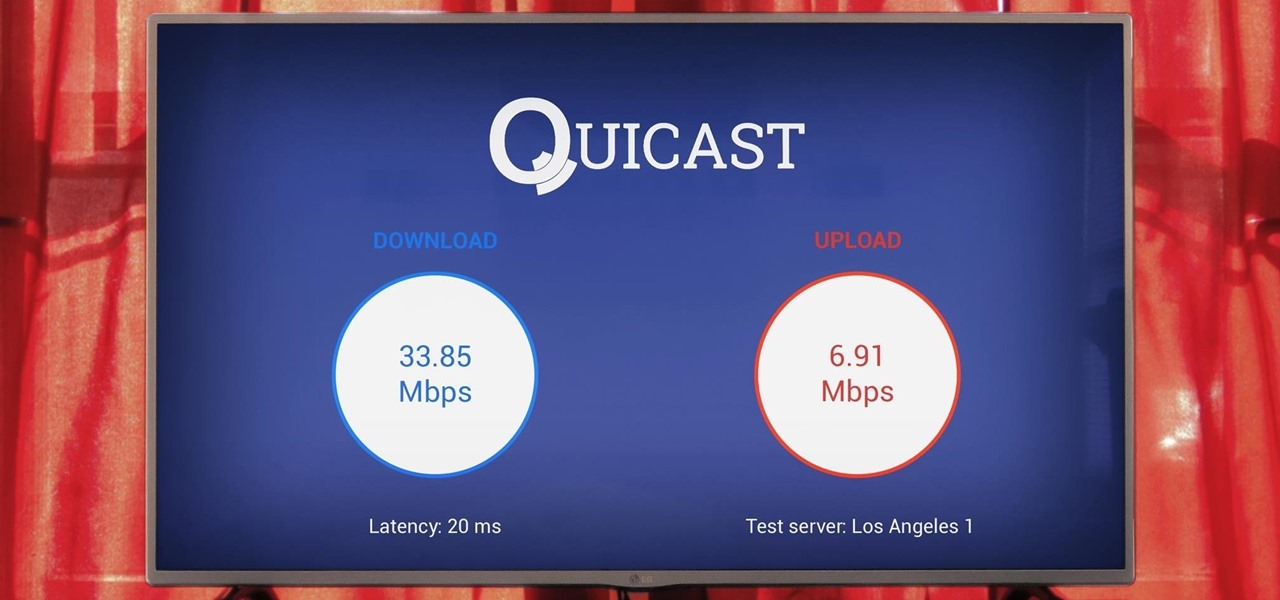
The Google Cast feature that serves as the primary interface for the Chromecast and comes bundled with Android TV devices like the Nexus Player is a marvel of modern technology. But as these things go, troubleshooting issues can be difficult with something so groundbreaking, especially when you consider that there are two parts to the equation—the casting device (your phone, tablet, or computer) and the receiver.

Hello there Nullbyte users! This will be my first article here.

In this article I will show you how to obtain victim's credentials without cracking any hashes. There are a couple of ways to perform this task (for example dumping the SAM file and cracking the NTLM hashes), but here I will explain how to do it using PowerShell and a bit of social engineering. We are going to create a fake login popup.

Step 1: What Exploit Development Is and Why Should I Be Interested on About This Topic

This is a little c++ program that I thought would be handy in the future. Although, I apologize in advance for any errors in the code since I haven't had the chance to compile it yet. Anyway, please if you are a script kiddie please do me a favor and at least read this article fully. :)

Hello, *Note This is my first how to post on here, so please correct anything that I have missed and let me know if anything I explained is unclear and I will try to clearify. Also I am a NOOB when it comes to this art, so I might have missed something, if so please inform me so I can better myself*

Recently I was trying to install Kali Live on a USB drive with persistence and struggled to find a tutorial online that was simple and actually worked. After some trial and error I figured out how to do it correctly and decided to make an article for anyone who is experiencing the same difficulty I did. You will need an USB with at least 8GB. Mine is 132GB, nice and large.

In Minecraft 1.9 New Command Blocks can be used to make elevators. You types different commands to achieve controlling the elevator for movement you like. This tutorial tells in Minecraft 1.9 how to use command blocks to make elevator. Lets just have a look at it!

In an article published in early-2015 by Peninsula Press, it was reported that the demand and the salaries for cyber security professionals are exploding! They cite that 209,000 cyber security jobs were unfilled last year, and that job postings have increased over 74% in the last 5 years. Job opening are expected to grow by another 53% over the next 3 years. You are definitely in the right field, my tenderfoot hackers! Some researchers are expecting information security jobs to continue to gr...

In the second part of this tutorial, we are going to crack the hashes that we've captured previously. I'm going to explain how to do it with the powerful John the Ripper. It comes with Kali by default, so no need to install!

If you have a specific app you want to lock so that others can't access it, the most secure way of doing so is with biometrics. While there are options to lock apps with either a PIN or pattern, these can easily be figured out with a simple glance over your shoulder. It's much more difficult for someone to crack your fingerprint ID, unless they chop off your finger, of course.

One of the biggest new features in the soon-to-be-released Android 6.0 Marshmallow is something Google is calling "Now on Tap." Essentially, this service will be able to scan the contents of any screen on your Android device, then after you long-press the home button, it will provide you with relevant information about anything—from movie times to directions or dinner reservations.
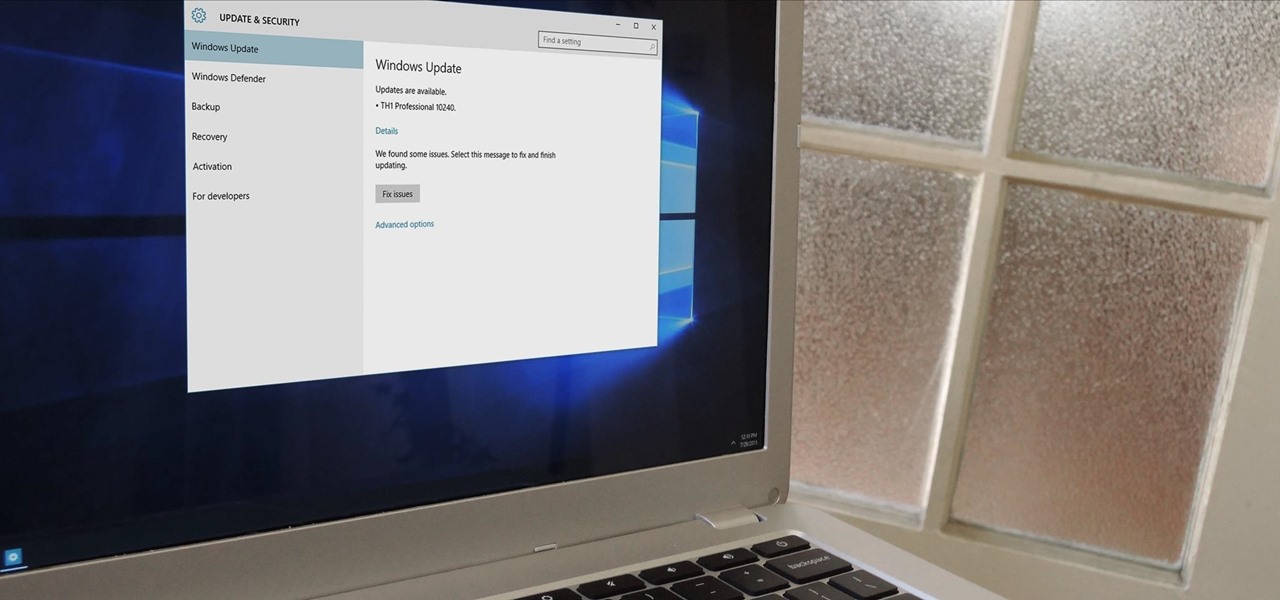
In a bit of a strange decision, Microsoft has made it to where some users don't have a choice in the matter of applying failed automatic updates. When a Windows or driver update comes your way and fails to apply for any reason, your computer will continue to attempt applying the broken update at seemingly random intervals. The Pro and Enterprise editions of Windows 10 will allow you to delay or stop updates altogether when something like this happens, but the Home edition has no such setting.
Well, this is my first article so if it sucks tell me...lol!! Story Time

The Apple Watch may be a much simpler device than your iPhone, but that doesn't mean it's free of bugs, glitches, and crashes just like your other devices. A common problem that you'll run into is a frozen screen due to a malfunctioning app. While this can be frustrating, the solution can be as simple as a quick reboot.

Video: . IF function

Once your furniture is finally moved in, settled upon a spot, and used for comfort or leisure, chances are it won't move very often. We tend to leave—and use—our furniture in the same spot for years, which can leave signs of great wear beneath, deeply indenting our carpeted floors and fancy rugs.

I've been lucky enough to never be a victim of street crime, but I have read and seen too many articles and videos to completely rule it out as a possibility. You can do some things to prevent it, but if your life suddenly turns into a scene from Friday the 13th, you'll want to be prepared with some sort of way to let others know you need help. This is where Shake2Safety comes in, a free Android app from Phontonapps.

One of the Note 3's best features is Multi Window mode, which allows users to display more than one app on the screen at the same time, taking advantage of the large and high-resolution display.
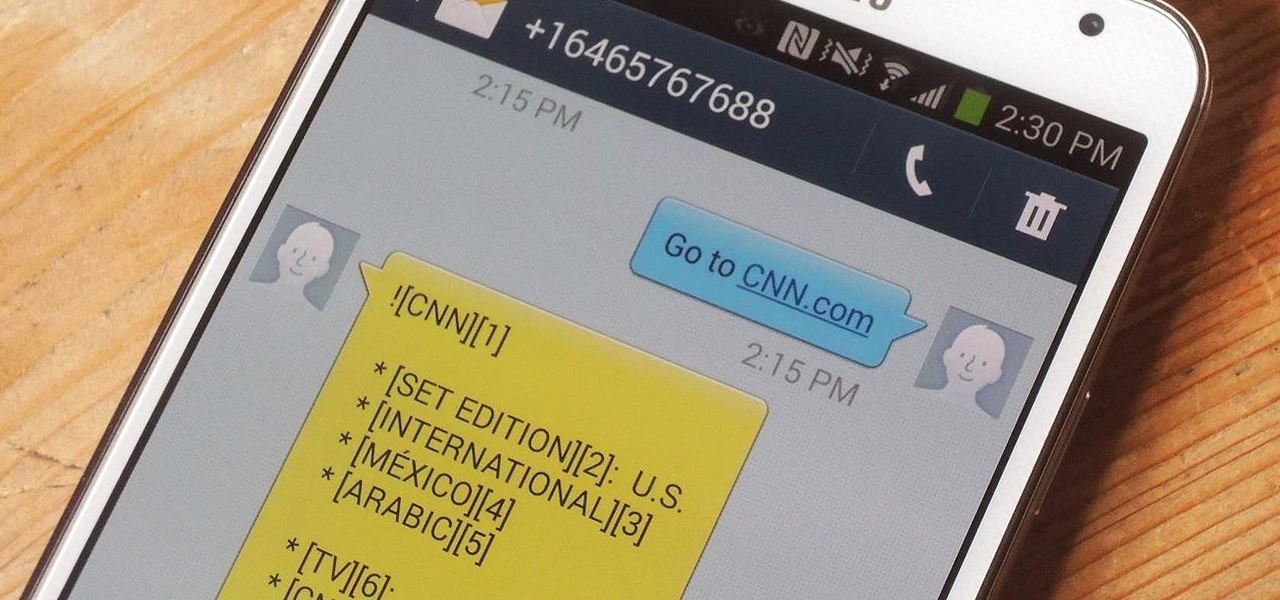
In places like underground bars or national parks, your phone's Internet service is sure to slow down to a very sluggish pace, making it difficult to surf the web. Or worst case, data will be non-existent, leaving you with only low-level network support for calls and SMS text messages.
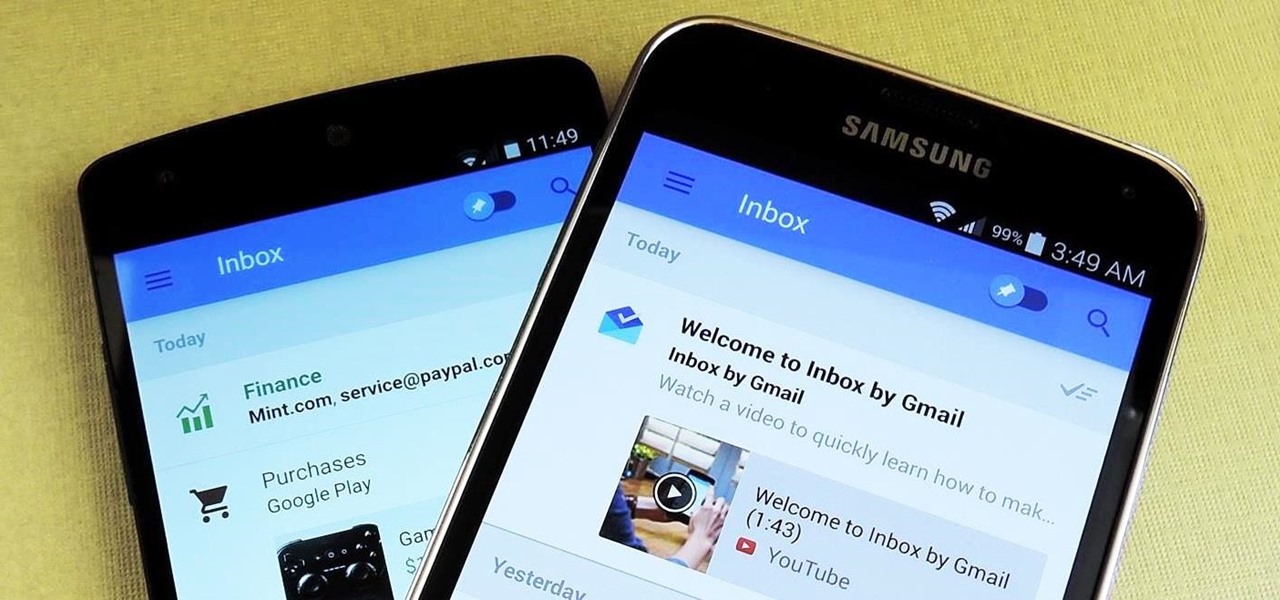
Google's new Inbox by Gmail service offers a new take on email with a particular emphasis on productivity. But, as an invite-only service at this stage, not many people can access Inbox just yet.

Third-party keyboards have become a game changer for iPhone owners since their integration in iOS 8. And while the major players from the Android realm—Fleksy, SwiftKey, Swype—already have their keyboards on the iOS App Store, their products are relatively standard fare.
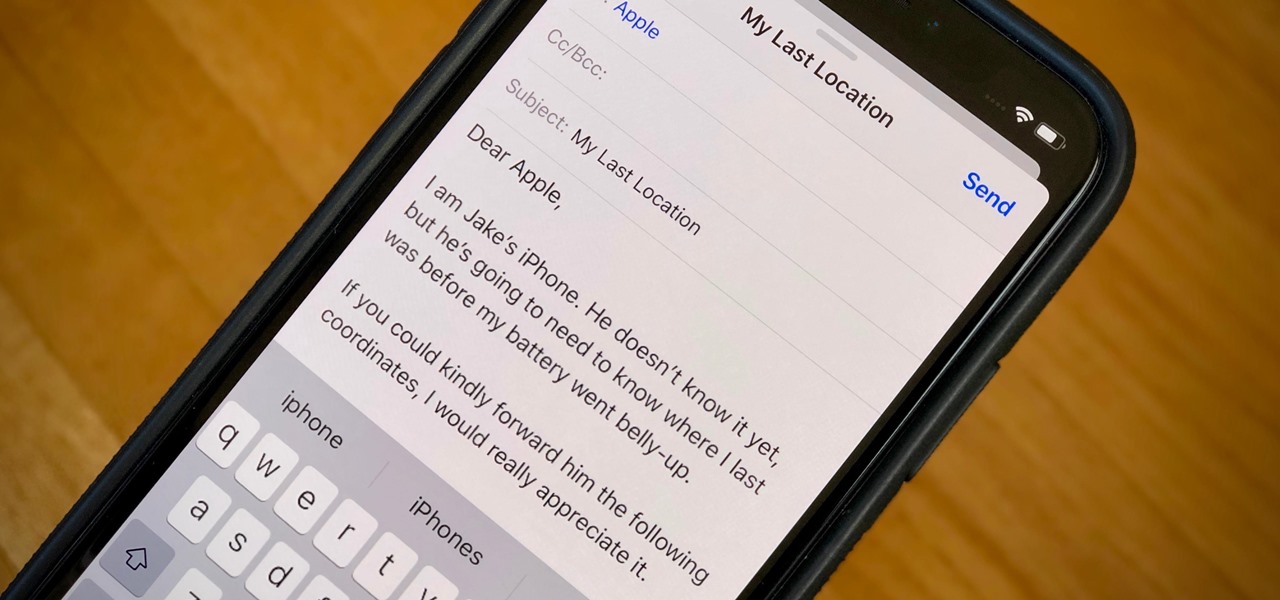
When your iPhone can't be found, Find My iPhone is a true lifesaver. When you use the feature, you can ping your iPhone and even see its current location on a real-time map. But what happens when your iPhone runs out of battery? Find My iPhone can't locate a dead iPhone, can it? You might be surprised to know it can, to a certain degree.

With root access, you're granted greater control over your device, allowing you to do things that your Android system wouldn't allow otherwise. Things like installing Xposed mods are made possible with root, but other advantages address performance and security, like stopping your Android logging, which is exactly what we'll be going over today.

Being healthy and active will help you live longer, but finding the strength to work out? That's hard. What does it do for me right now? I mean, here I sit, writing this article, thinking about going for a run, and I feel good just for thinking about running. But will I do it? Nah, I'm too lazy.

There are so many mods we can apply using a custom recovery. From themes to bug fixes and feature ports, a typical rooted user spends a decent chunk of time in TWRP Recovery.

There are two types of bricks ("brick" as in "bricking your phone")—soft and hard. Soft bricks are recoverable—something has probably gone wrong with some critical system partition, causing a bootloop or inability to boot in some way. Fine. Re-flashing everything should fix that instantly. Hard bricks are not recoverable—if you manage to hard-brick your Nexus, you are in trouble.
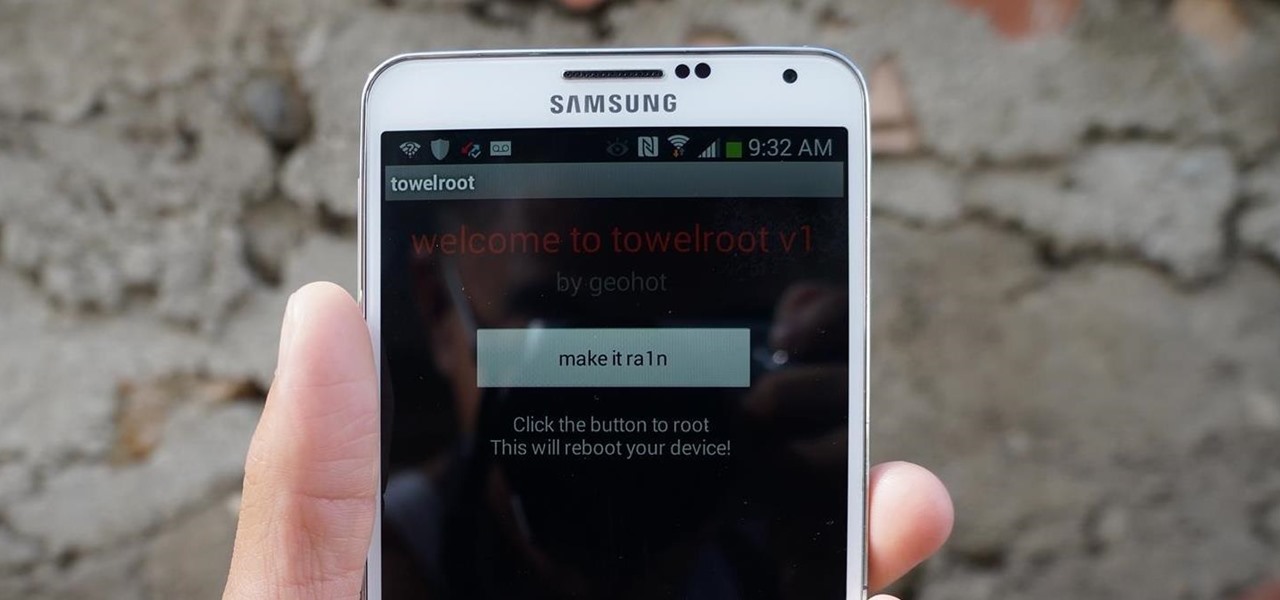
AT&T and Verizon customers, it's finally happened. After many long months of waiting, and a fairly significant bounty up for grabs, your Galaxy Note 3s can finally be rooted! Best of all, it may be the simplest method for achieving root we've ever encountered.

While AT&T and Verizon may not have had a chance to screw Note 2 owners with unrootbale devices—mainly because they've screwed us over by not issuing KitKat updates—it's safe to say that they can in the future. And while Sprint and T-Mobile subscribers have been able to root, the various methods can make the process somewhat confusing, especially for first-timers.
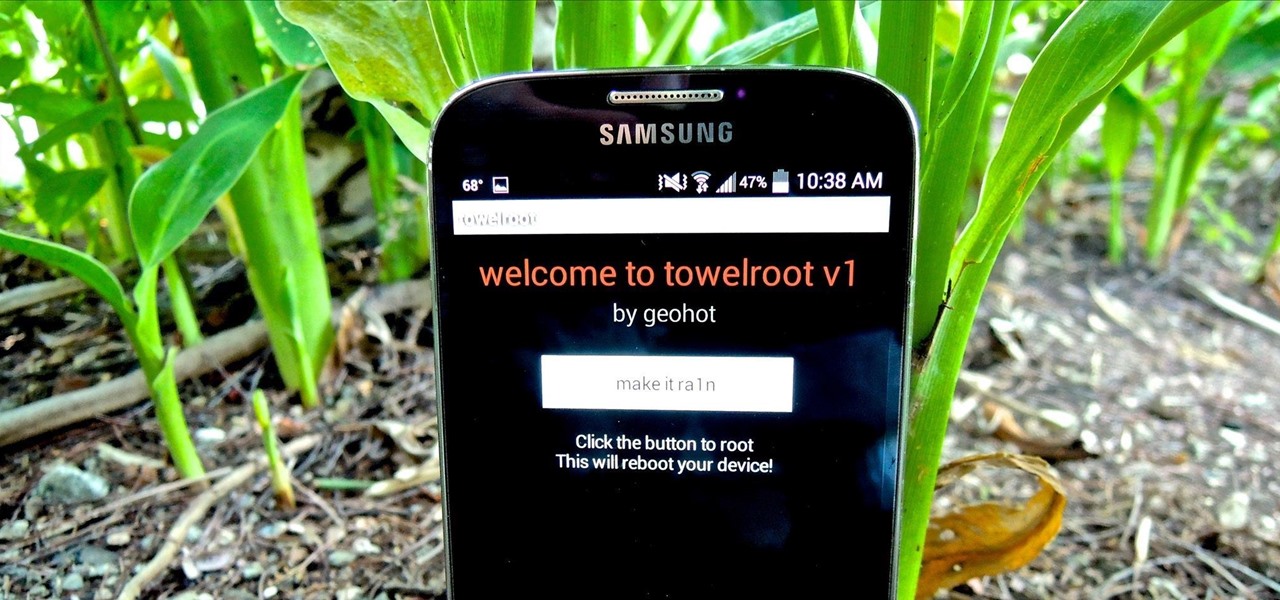
Something pretty awesome happened over the last couple of days. George Hotz, better known as Geohot, the infamous hacker known for jailbreaking iOS and exploiting the Sony Playstation 3, has brought joy to owners of just about all Android smartphones and tablets, especially those on AT&T and Verizon.
In a era where cyber security is becoming increasingly important, Comcast has decided to use its customers' routers to provide hotspot access to the public. A new program, outlined by Dwight Silverman over on the Houston Chronicle website, seeks to provide Xfinity customers with city-wide Wi-Fi hotspots by using, well...other customers' wireless routers.

It has been a long while since I last came here to write an article. Graduate school keeps you busy. After I looked over what I had written previously, I decided that I should introduce another fun topic from cryptography. In this case, steganography.

Google Glass is all about transforming the world around us with little to zero interaction from the wearer. Much of this is done using augmented reality—a live view of physical, real-world environments that are augmented by computer-generated input in the form of graphics, sights, and sounds.