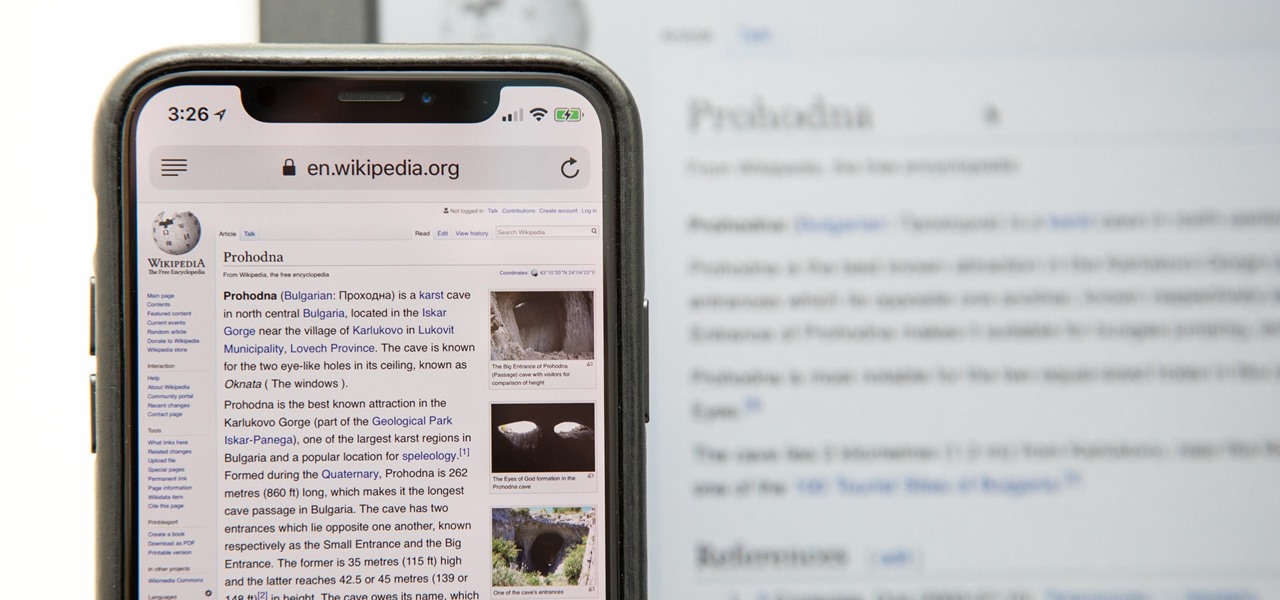
The day has finally come, and after quite a bit of hype and buildup, Windows 10 is now officially available. The update itself is on a staged rollout, which means it will be slowly becoming available to users over the coming weeks and months, so don't panic if you haven't already received an update notification. Besides, you have until July 29th, 2016 to download your free copy of Windows 10 if you're eligible, so there's plenty of time to get your ducks in a row.

I am very new to Null Byte but I find much of its content and community incredibly interesting. I spent quite a bit of time just chronologically going through the posts and I noticed a common theme in many of the beginner posts. Many people seem to want to know the 'secret' or a paragraph on "How to Hack" and become a hacker in a few minutes. I started off this post as a reply to a question from a beginner but thought it might be beneficial to have for those stumbling across this site.

Welcome back, my rookie hackers!

Hello you sexy, savage, surreptitiously tech-savvy penetrators (Pun intended)!

All of those keys on your keyboard can do much more than just help to update your Facebook status or fire off a scathing tweet. By learning all of the keyboard shortcuts for apps on your Mac, you can cut back on mouse or trackpad usage to perform actions faster and more efficiently.

If you have some photos, videos, and documents that you want to keep completely hidden and encrypted on your Android device, Andrognito is the app you need. We showcased this app in the past, but since then, CODEX has rebuilt it from the ground up with new and improved features.

There's something primal about the smell of smoking food. Somewhere deep in the recesses of our souls, we remember a time when humans only ate by the fire. Or perhaps that's just something I tell myself. Either way, it's hard to smell smoke and food and not feel like you should be eating. And, as chef Edi Frauneder said in a recent Saveur article, "Grilling is convivial. There's something about this act of coming together over an open flame that just says vacation."

Having websites coded for mobile browsing is great for small screens, but if you have a Plus model iPhone or even the iPhone X, desktop versions of websites might show you more of what you want. Plus, there's the case of poorly designed mobile websites, where the desktop view is clearly the better option with more functionality and features. Luckily, asking for desktop sites in Safari is simple.

A long time ago I was reading an issue of Saveur and saw an article about a trendsetting bar in Portland. The bartender at the joint had started making enormous blocks of smoked ice for his cocktails. When a patron ordered a drink that called for the smoked ice, the bartender would chip off a large chunk and place it in a glass with the booze. Then, as the ice slowly melted, the drink would take on more and more smoky notes, and the flavor profile of the beverage would change with every passi...

Do you remember my last article on how to hook any web browser with MITMf and BeEF? Well, we are using the tool once again, but this time for auto-backdooring....

If you read my last tutorial on using SEToolkit, you probably know that SEToolkit is an effective way to make malicious actions look legitimate. But, that was only the beginning... the truth is, Metasploit and SEToolkit belong together, and help each other very well.

Disclaimer: All information in this tutorial is for entertainment and educational purposes ONLY. You pesky teenagers.
Hello, Hackers/Viewers! My name is nullf0x, and I have 4 years of experience as a hacker. You might see everyday that one of your friends or acquaintances get a new virus in their computer. You might think, How cool would it be if I made a virus? or How cool would I be if i could remove viruses from others computers for money or free?

Hello, ladies and gents! Today I will be discussing the fun and excitement of backdoor on an OSX system.

Imagine this scenario: You exploited a system using metasploit and you want to install a backdoor. You have a few options;

On the internet, everything is possible, even if it's not grounded in reality (check no further than anything The Onion publishes). Witty headlines combined with clever photo edits make even the most absurd topic seem like a serious news story. Some of these stories are so convincing that they even fool news organizations, such as the New York Times and even the official newspaper of the Chinese Communist Party. While some of us can tell when something sounds a bit off, others (like our paren...

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Welcome back, my budding hackers! With this article, I am initiating a new series that so many of you have been asking for: Hacking Web Applications.

Eye contact is key in conversations, job interviews, and honesty, and it can help you access others' thoughts and spot heavy drinkers. Locking eyes with someone can even help you fall in love, whether you know them or not.

Hello my fellow hackers, Welcome to my republished revision of the ruby programming language, Part 1.

UPDATE NOVEMBER 2015: The root process has changed for the Nexus Player now that the device is running Android 6.0 Marhsmallow. I've updated this article with detailed instructions on the new root process, but the video below still depicts the old process for Android Lollipop.

We all fall sleep in different ways. Some may require absolute silence, others need white noise, and some enjoy listening to a song or two to help bring on the sleep. If you're in the latter group, like I am, there's a problem. Fall asleep before the music stops, and a loud song may jolt you awake in the middle of the night. With an iPhone, however, that issue can be avoided with a little setup.

Welcome back, my budding hackers! This is the initial post of a new series on how to hack Facebook. It's important to note here that each hack I'll be covering is very specific. I have said it before, but I feel I need to repeat it again: there is NO SILVER BULLET that works under all circumstances. Obviously, the good folks at Facebook have taken precautions to make certain that their app is not hacked, but if we are creative, persistent, and ingenious, we can still get in.

Cooking rice, pasta, and other grains in water is so boring. There is a much better way to guarantee they will have your mouth chewing something seriously tasty: cook them in something that isn't water. Alternative liquids such as stock, milk, juice, or even tea will give bland dishes a fresh new flavor boost. If you're not sure how your dishes might taste, never fear: we tested them out. Before getting started, be sure to read this article first so that you know why it's important to rinse y...

Yosemite is definitely an improvement over Mavericks, but there are still some painfully obvious and annoying bugs that occur within certain apps.

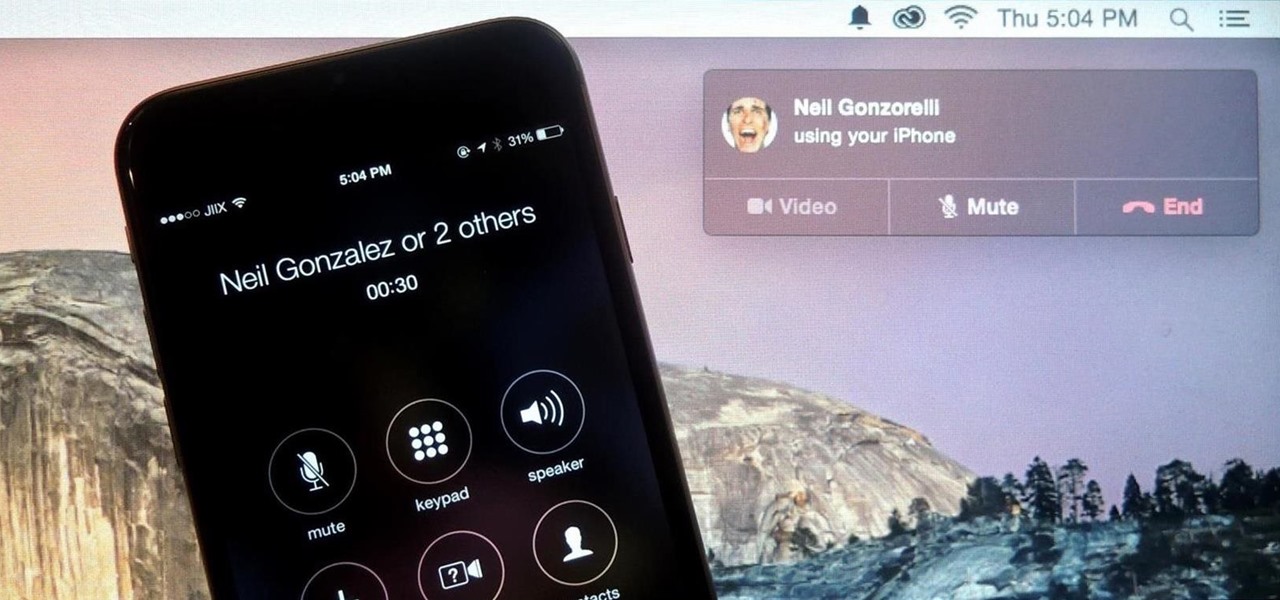
Earlier this year, Apple announced Continuity, a feature for Yosemite and iOS 8 that lets you connect your iOS devices to your Mac in order to access apps, receive phone calls, send text messages, and more while seamlessly switching between the two.

The importance of body language is stressed from an early age: watch those around you, and you'll know what they're thinking. While you might be skilled at deciphering the messages of crossed arms, slouched sitting, eye movements, and hand gestures, the key to understanding those around you is a little less obvious.

Hate slogging through pages and pages of weighty books and lengthy work documents? You may not be able to depend on speed-reading apps, but with the right font, you can increase the number of words you scan each second, speeding up your reading pace exponentially.

Welcome back, my greenhorn hackers! Before we attempt to exploit any target, it is wise to do proper reconnaissance. Without doing reconnaissance, you will likely be wasting your time and energy as well as risking your freedom. In previous guides, I have demonstrated multiple ways to perform reconnaissance including passive recon with Netcraft, active recon with Nmap or hping3, recon by exploiting DNS or SNMP, and many others.

When Android 5.0 rolls out to the Nexus 5, several changes and new features will come along with it. The over-the-air update is already rolling out, and if you don't want to wait, you can get it right now.

Aside from the occasional "creative" collage, most of your friends on social media are content with pretty basic image and video posts. You can easily one-up them with celebrity cameos or awesome time-lapse videos, but to truly outshine them, try your hands at some creative double exposures.

Welcome back, my hacker novitiates! A short while ago, I introduced you to regular expressions. Regular expressions are a language that is particularly useful for finding complex text patterns in streams of data.

One of the best ways to reduce clutter and enjoy the new iOS 8 wallpapers on your iPhone is to use the little-known trick of hiding all of your main home screen apps. This trick effectively moves your apps off the main home screen and over to additional home screen pages, or in your dock, making your main home screen beautifully clutter-free.

There are several reasons why restaurant food tastes so good. One is that the cooks know how to make reductions, which involves cooking down large amounts of liquid until it becomes a pool of thick, glossy sauce. While this technique isn't hard to learn, it can be time-consuming.

Remember when MITMing people to pentest webapps and log-ins you had to fire Ettercap,Arpspoof, SSLstrip, then look for credentials in the captured packets?

Check it out: you save more dough (ba dum bump) when you order a large pizza than with any other size. Why is this true? NPR reporter Quoctrung Bui's engineer friend pointed out that a medium pizza was twice as big as a small one, yet only cost slightly more.

If you have an artistic ability, I encourage you to learn how to airbrush on cars. Sure, it may be a little different, but if you already have the artistic ability, the rest is a walk in the park.

It is really quite easy to flash a custom recovery to your Nexus, and there are many excellent tutorials on how to do so (see the How-To below): The Easiest Way to Install a Custom Recovery on Your Nexus 7 Tablet « Nexus 7.

Let's be real, browser histories are virtually useless. Trying to find something you passed up a week ago is like, pardon the cliché, finding a needle in a haystack.