Your maximum heart rate is an important piece of information to know if you are exercising seriously and want to make sure you are going hard without damaging your body. This video will teach you an easy, conservative way to estimate your maximum heart rate. With this knowledge and a heart monitor you will be able to assess the quality of your workout more accurately.

You know that question your girlfriend asks that you never ever say "yes" to? "Does this (insert article of clothing) make me look fat?"

Looking for a way to save on your energy bills at home? How about line drying your clothes? According to the Energy Information Agency, clothes dryers account for 5.8 percent of home electricity usage. Line-dry your washed clothes and linens to keep them from wearing out, and save money on your energy bill at the same time.

Here's a quick and simple way to repair small cooling fans and extend their life. It's a video made with a how-to article from http://beecherbowers.com This is a delicate mr. fixit tutorial. Clean the fan so that it runs smooth and quiet. You need oil to do this repair.

Operation fire-saw. The British Army use tips from Bushcraft & Survival Skills Magazine to boost morale in Afghanistan and to practise their firelighting skills using an article written by firelighting expert Dave Watson.

In this how-to video, the LoveFeed tackles The Washington Post's article, "How To Have A Good Divorce." Divorce is stressful, but it doesn't need to be ugly. Watch this video relationship tutorial and learn how to get a good divorce.

While one can achieve a number of realistic vintage keyboard sounds through sample libraries like the Reason Abbey Road Keyboards refill, there's no beating the genuine article. If you find a vintage keyboard, however, it may need any number of repairs to get it sounding like it should. In this how-to, you'll learn a few quick tips for getting rid of electrical hum on a Wurlitzer 200 Electric Piano. Take a look!

While one can achieve a number of realistic vintage keyboard sounds through sample libraries like the Reason Abbey Road Keyboards refill, there's no beating the genuine article. If you find a vintage keyboard, however, it may need any number of repairs to get it sounding like it should. In this how-to, you'll learn how to get rid of electrical hum in a Wurlitzer 200 Electric Piano. Take a look!

Today's word is "juxtapose". This is a verb which means to put things side by side, often for comparison or contrast.

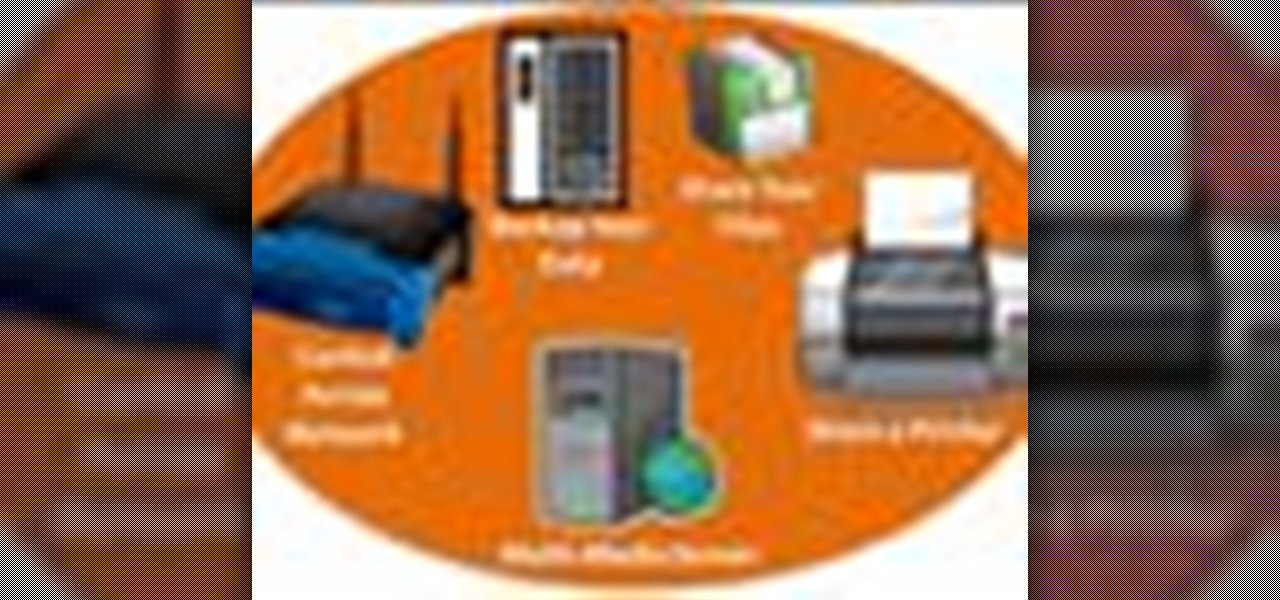
Use an old PC that has been setup as a server to perform helpful tasks such as backing up computers on your network, storing media files in a central location, share one printer with every computers computer in the house.

Thread Head Rob takes the cuff, collar, and pocket of a normal button down shirt and attaches them to a sweater for a cool new homemade article of clothing.

Build sound board for a studio at home, to insulate noise and sound. The subject of this DIY project was originally covered in a written article that is still required reading to finish the project as it gets into more detail regarding the actual construction of the boards.

First of all, I would like to apologize for a week long absents for the tutorials of this newly series, Raspberry Pi. But obviously I'm back and I present all you guys a article on turning your Raspberry Pi into a hacking platform. I'm gonna use the platform Kali Linux for the Raspberry Pi. I should note that I'm not gonna go into detail on how to install Kali Linux since OTW already has done a tutorial on how to turn your Raspberry Pi into a Hacking Pi. The point of this particular tutorial ...

Ever find a really cool article on the web that you'd like to read next time you are out and about, waiting in line or riding the bus? Watch this video to learn how to use iCloud to share links between your computer and your iPhone.

This video shows Thomas Maiorana of Boot y Amor follows up to his CRAFT: 07 article with tips on how to make your own shoes, as well as modify existing shoes.

The experts at ZIPS Dry Cleaners explain what to do when you get a stain on a dry-clean-only article of clothing.

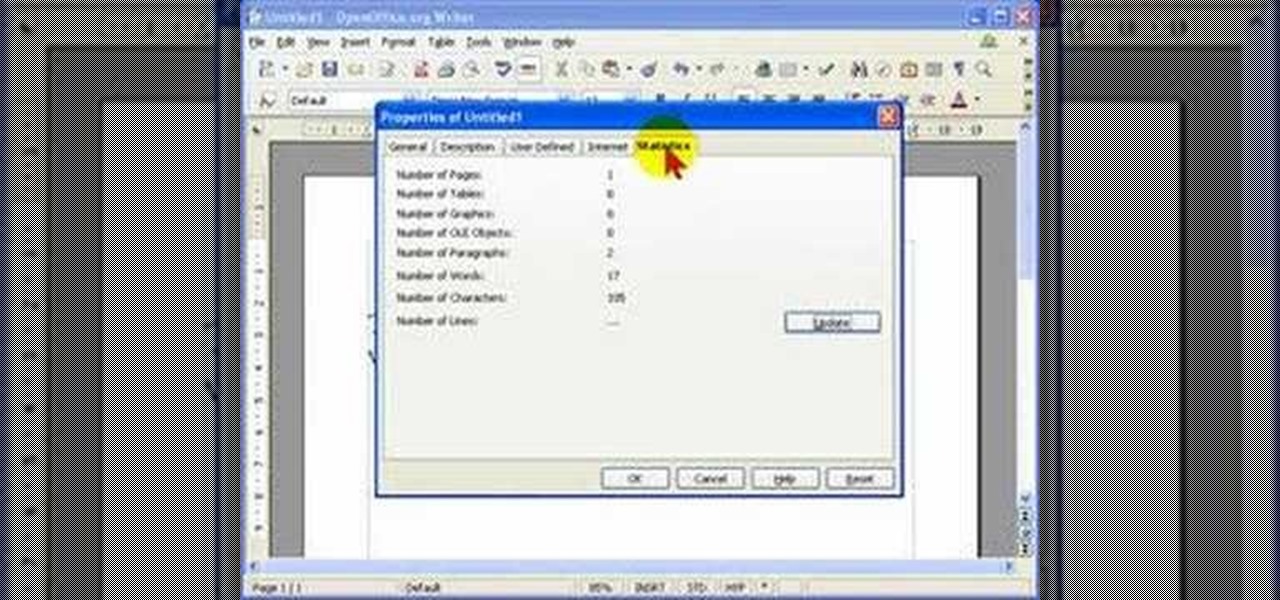
When creating word processed documents, there are often times when it is important that you know exactly how many words you have written - for example, student writing their dissertation, and journalists writing articles.

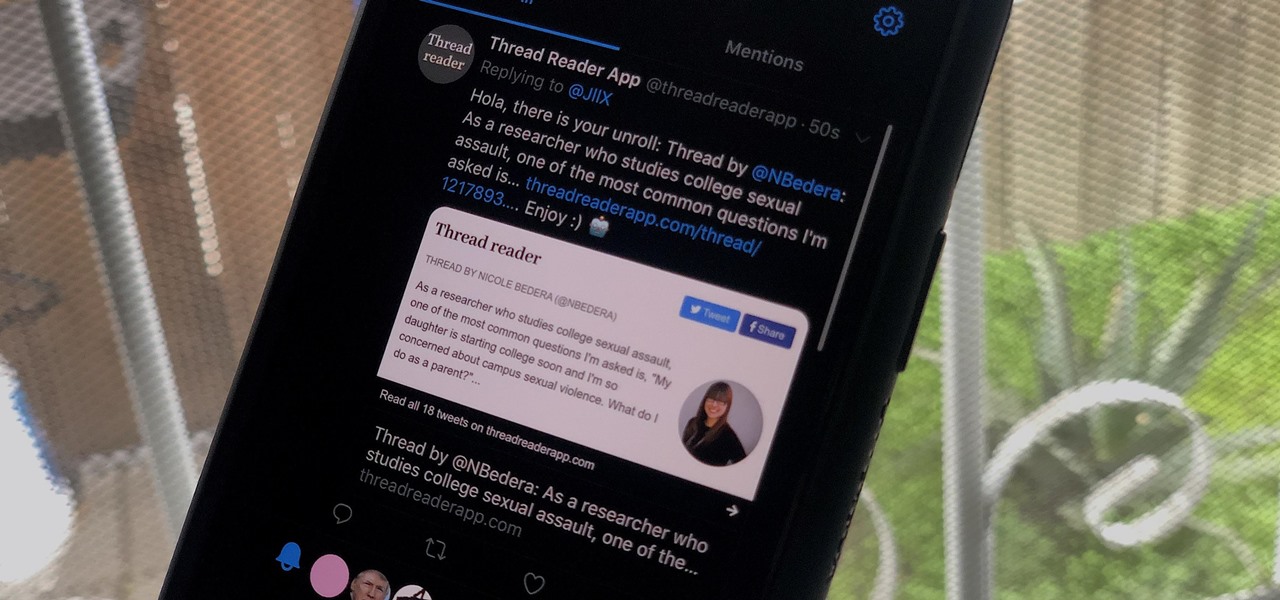
While tweetstorms were a part of Twitter since the beginning, threads, which makes tweetstorms more viable, didn't show up until late-2017. Still, threading multiple tweets at once to create long-form stories, opinions, tirades, and other lengthy Twitter posts, can be hard to digest. However, you can make reading them easier with just a single message.

Paywalls make it nearly impossible to access certain content unless you have a subscription. It's a practice that many news organizations and other online publications use to increase revenue: The New York Times, The Wall Street Journal, Vanity Fair, Wired, and so many more. But just because a paywall is in place doesn't mean you can't get around it on your iPhone.

One of the better additions in the stock Android launcher is the Google Now page. Residing to the left of the home screen, this page presents a host of information based on the user's interests, which Google bases on analyzed data. Recently, the Google Now page design received a makeover which Nova Launcher users can now enjoy.

What's good, peeps? I've been noticing some rather advanced tutorials slowly emerging here on Null Byte and I know that people want more of them but I've been reluctant to post something of such caliber because I fear that the information will just go over their heads, but hey, as long as it's there, people can always go off to research themselves and eventually understand. So here is my contribution to the gradual and inevitable progression of Null Byte!

Since I first announced the new Null Byte recognition for excellence a few weeks ago, several of you have written me asking, "How can I study for this certification exam, and what material will be covered on the exam?" Now I have an answer for you. The White Hat Hacker Associate (CWA) will cover 14 domains or areas. Everything you need to know is here on Null Byte. There will be no questions that are not covered here on this site, guaranteed.

Serving as the primary tool of distribution for many websites, social media is how most of us catch up what's going on around the world. While there is a bunch of clickbait going around on Facebook and Twitter, there are plenty of genuinely interesting articles being shared.

Why I split it into two articles: I love images and I'm sure lots of us do. I decided to put in a lot of images as examples rather than have paragraph upon paragraph of boring text. Also, I don't think any of us like overly long articles; but if you think it's better to have it all in one article, let me know

Video: . This video explains how to install Android OS on a PC using VirtualBox. How to install Android OS on a PC Using VirtualBox.

In the following video, I demonstrate how to create a device capable of charging the body of anyone who wears it with static electricity, allowing a powerful shock to be discharged into anything that is touched. This grants the wearer the ability to do some pretty amazing things, some of which are shown in the first segment of the video.

Check out this overclocking tutorial from HotHardware.com! Intel's Core i7 processor offers a significant performance increase over previous generation Core 2 processors. In addition, like the legacy Core 2 architecture, the new Core i7 also has a bunch more headroom for wringing upside performance out of the chip, maximizing value, power and return on your investment with overclocking. In fact, Intel actually built-in a predefined overclocking feature called "Turbo Mode". We explain how not ...

Watch this science video tutorial from Nurd Rage on how to make silver different colors by electrochemical anodizing. Without using paint, you can give a silver surface various colors by anodizing it.

One of American Apparel's most famous articles of clothing for women is their Le Sac dress, which is no ordinary dress. It's simplistic look mocks it ingenious design, which can be shaped, formed, mutated, tie, and tucked in at least TWELVE different ways to create a different dress for each day of the week. The Architectural Mini look is just one of the ways to style it, and this video shows you exactly that. Use this art deco style for a sexy, architectural inspired halter look.

Can you believe this dress? American Apparel have outdone themselves again! A dress that's not just "one" dress, but at least "eight" dresses. The Le Sac dress is a marvelous article of clothing because it can be worn every day of the week… without looking like a hobo. It's a different style each day, with at least TWELVE different styles. And there's even a look for you dominatrices out there, a super sexy and daring S&M style Dominatrix look. See how easy it is!

American Apparel is famous for selling articles of clothing that can be worn in multiple ways. Their latest creation is the Le Sac dress. This dress can be tied and twisted all over the place to come up with TWELVE or more styles! You can wear this outfit every single day and everyone would think you were in something new. So, if you are looking for a sexy, Greek-inspired off the shoulder look, check this official tutorial out for the Grecian look. Learn how to wear your Sac and look amazing.

The fine folks at ITS Tactical made this detailed tutorial on how to make a two-piece lock pick set out of only a few paper clips and using only a multi-tool in the construction. The host begins by demonstrating how to construct the pick, then how to use it on a real lock. It is not as easy as using a real lock pick, but will still work. As the host emphasizes at the beginning of the video, these picks are only to be used in emergency situations, and NOT to break into other people's homes wil...

We've all seen the breathtaking, colorful photos of the Eagle, Egg and Cat's Eye Nebulae. You may not recognize them by name, but you've seen them, whether in astronomy textbooks, magazines, websites, album covers, or tee shirts. They are some of the most striking photographs ever taken from the Hubble Space Telescope (HST).

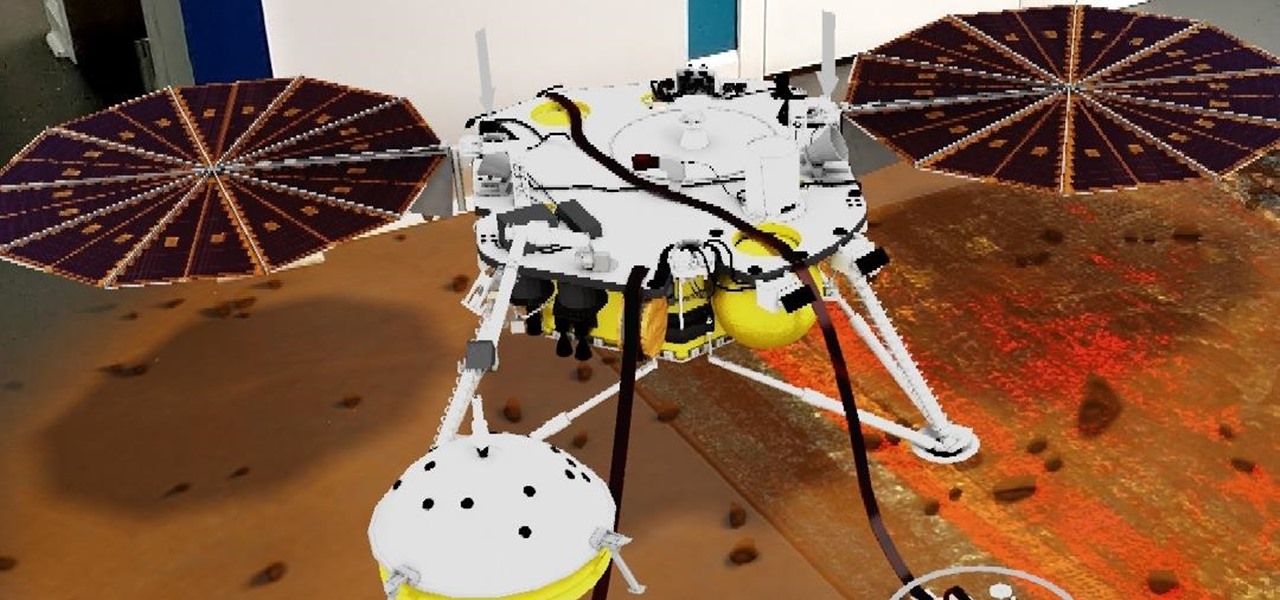
In the latest installment in its burgeoning augmented reality journalism practice, The New York Times is bringing its readers closer to Mars and NASA's latest spacecraft set to travel to the red planet.

The internet is chock-full of fun and interesting content, but there's only so much time in the day for consuming it. That's when saving webpages for later comes in handy. If you don't want your bookmarks and favorites folders to clutter up fast, consider using the "Reading List" feature built right in Safari on your iPhone.

Welcome back everyone! It's been awhile hasn't it? Sorry for being so quiet, but my CCNA courses have really picked up recently. In the last article we covered how to import modules and how we can use them. In this article, we'll actually be covering a module that is essential to the hacking aspect of Python, sockets.

Hello, everyone. Stealth is a large part of any successful hack; if we don't get noticed, we're much less likely to be caught. In these next few articles, we'll be building a shell based on keeping us hidden from a firewall. There are many ways to stay hidden from a firewall, but we'll only be incorporating a couple into our shell. This article will outline and explain these evasion concepts and techniques.

Before we dive into the world of frustration, I first would like to thank whoever of the admins and mods made the folder for Raspberry Pi in the How-To's, thank you. Now with that outta the way, this article is about Metasploit on Raspberry Pi (hence the title). I should say that I ran into a error, but I think I figured what the problem is. First of all this is not on Kali Linux, but on a regular Linux OS. With that said let's open up a terminal and begin.

Hello, everyone. If you've been following my recent articles, you'll know that I've been rather busy lately working on a project, a rather large one. I've been working with Pheonix750 and Ciuffy to build the Null Byte suite of tools! I got the green light from our admin a while ago, and we've been developing like mad ever since! I'm very excited to launch this project. So, let's start by explaining what it is...

Windows 10 has so many new features that we couldn't even cover them all with one article. From keyboard shortcuts to revamped search functions and all-new window gestures, Microsoft definitely piled on the fresh functionality in the latest version of their operating system.