Many online users worry about their accounts being breached by some master hacker, but the more likely scenario is falling victim to a bot written to use leaked passwords in data breaches from companies like LinkedIn, MySpace, and Tumblr. For instance, a tool called H8mail can search through over 1 billion leaked credentials to discover passwords that might still be in use today.
After the limited initial release of the massively popular game on the Android platform, many users have been stuck waiting to play Fortnite. That's because, initially, Epic Games only released the game to Samsung Galaxy devices, and asked non-Samsung users to join an invite list. Well, the wait is finally over.
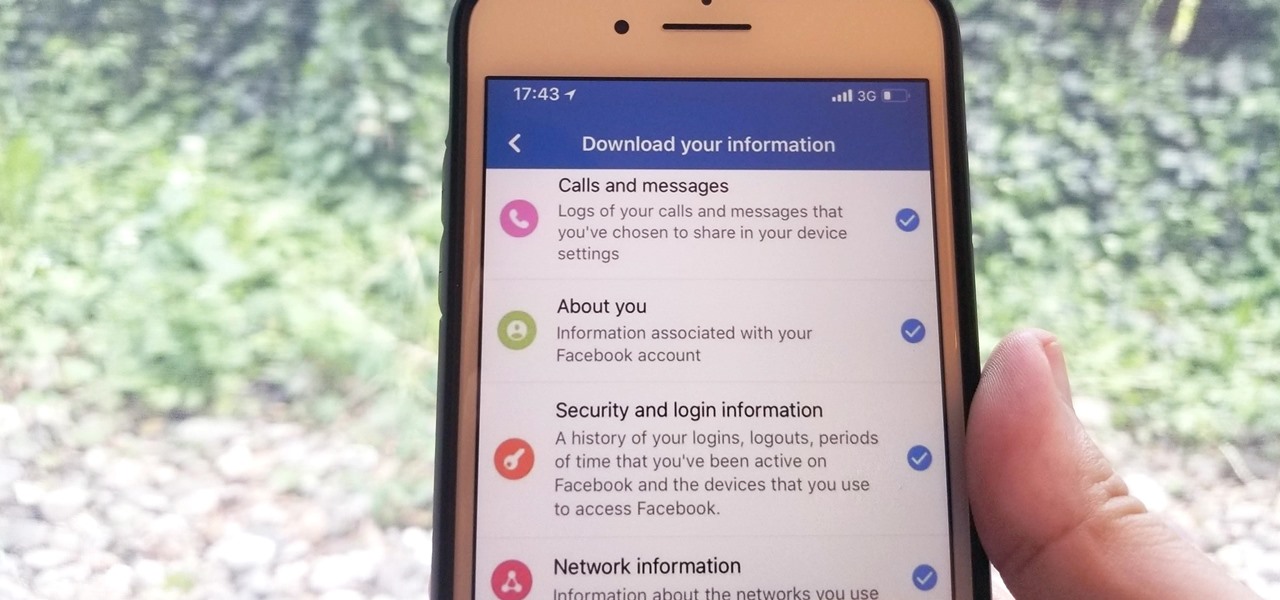
We've been able to download our Facebook data onto our computers for a while now, but now you can do so right from the comfort of your iPhone or Android phone. With it, you'll be able to integrate your data into other apps that support it or even just download it before you deactivate your account.
One of the better additions in the stock Android launcher is the Google Now page. Residing to the left of the home screen, this page presents a host of information based on the user's interests, which Google bases on analyzed data. Recently, the Google Now page design received a makeover which Nova Launcher users can now enjoy.

The iOS App Store is a big place, offering over two million applications in total. However, there are actually some apps you can and should install on your iPhone that the iOS App Store doesn't include. And no, these apps do not require any difficult jailbreaking or complicated sideloading techniques — they are really simple to install.

Longtime Next Reality readers may remember my Wish List for Microsoft early last year. It was a post in which I put my head together with a number of other community developers to create a list of features that would make Windows Mixed Reality and HoloLens better for developers. It would seem that one of the most sought-after features is finally here ... well, sort of.

Facebook really wants your phone number, nagging you for one as soon as you join. This isn't all bad since it can help secure your account with two-factor authentication. On the flipside, this makes it easy to reveal the private phone numbers of virtually anyone on Facebook, including celebrities and politicians. We're going to look at how a hacker would do this and how to protect yourself.

If you want to root your phone, it's a huge plus. If you want to install a custom ROM like LineageOS, it's an absolute must-have. Custom kernels like ElementalX, custom recoveries like TWRP — none of this happens unless you buy a phone with an unlockable bootloader.

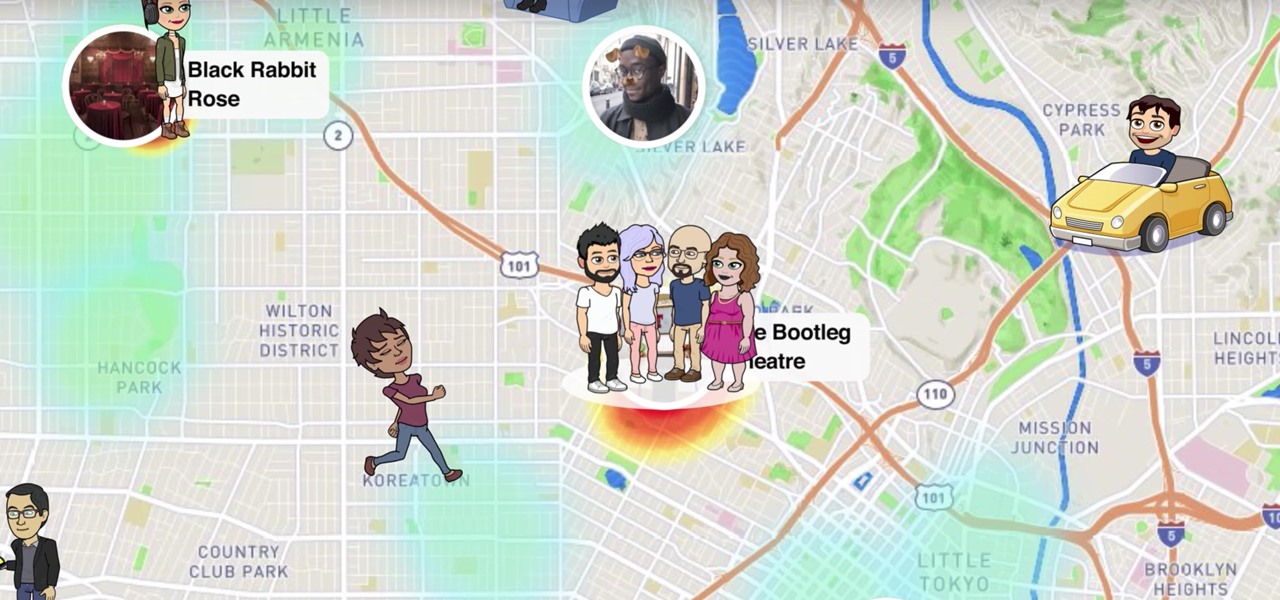
Snapchat recently updated their Android and iPhone apps with a new feature called Snap Map which lets you share your current location with other Snapchatters, as well as see their current locations. It may sound like an interesting new feature, but sharing your exact location with all of your Snapchat followers is dangerous, to say the least. Luckily, it's easy to turn this feature off.

The modern age of techno-dating has made an interesting landscape for social interactions when there is some modicum of romance (or lust). For those of us born before the internet evolved into the prolific monster it has become, we first met our love interests face to face. Today, however, apps like Tinder have changed the introductory stage, for better or worse.

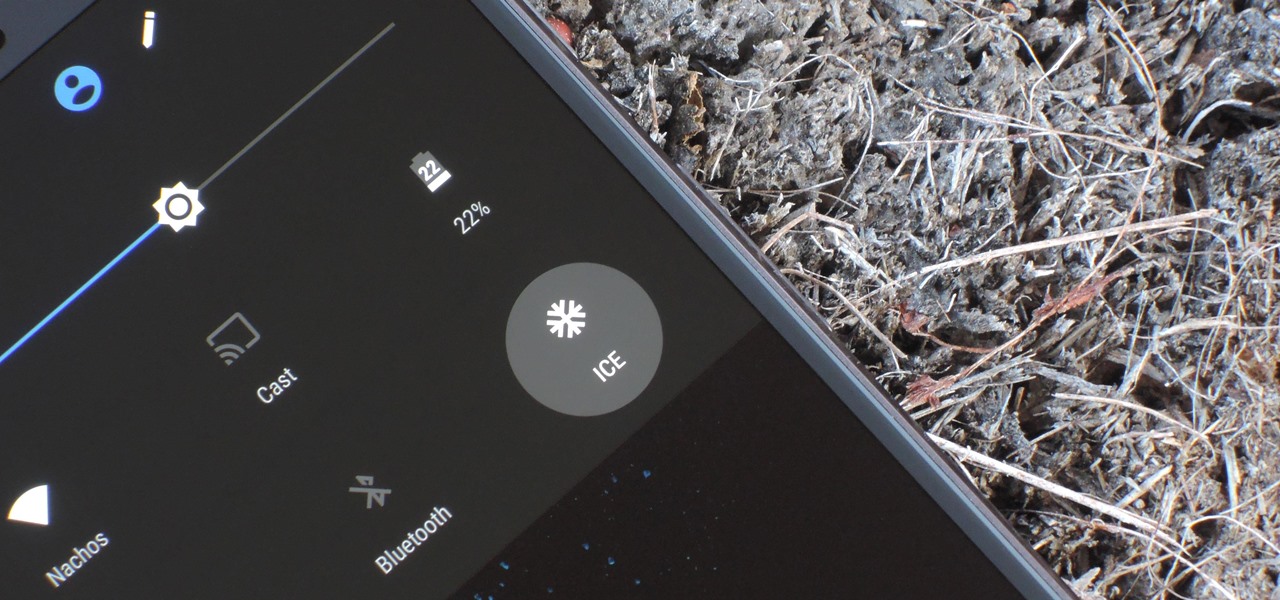
If you're ever in a major accident or have a bout with acute onset health problems, first responders will need to know as much information about you in order to provide proper care. For this reason, paramedics and firemen have been trained to search a subject's cell phone to find ICE (in case of emergency) contacts that know your allergies, blood type, and other vital details.

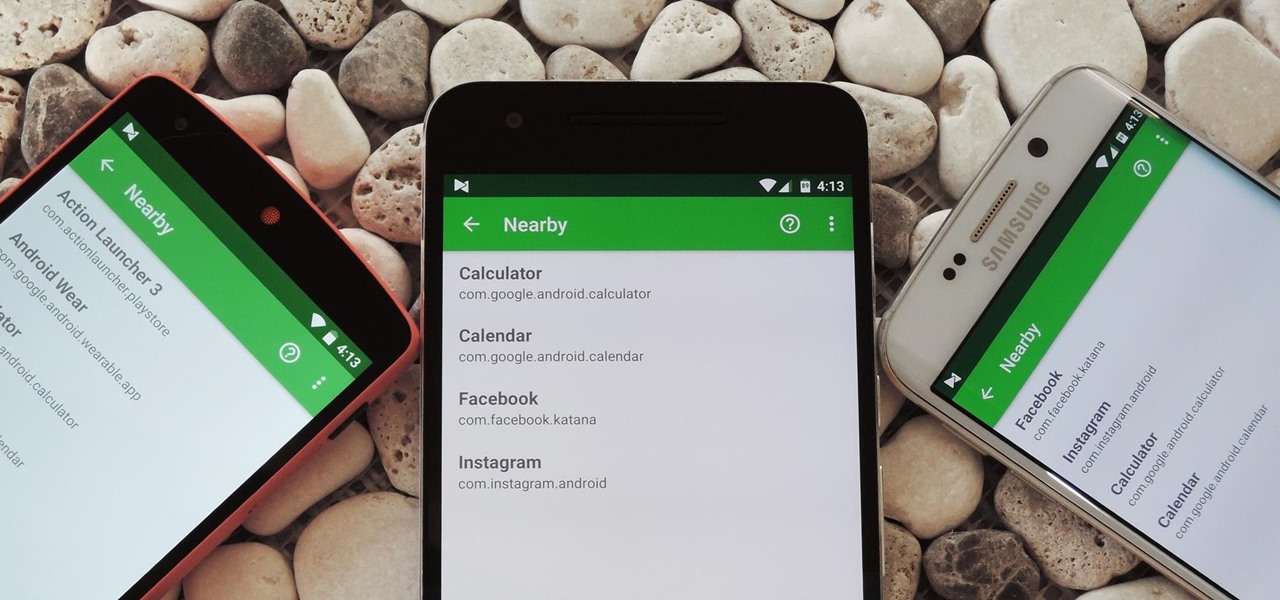
Google has an intriguing feature called Nearby that lets users share content without being on the same Wi-Fi network, or without even exchanging contact info first. Instead, the function uses an array of standard smartphone features, as well as subsonic sound, to identify other devices that are in the room, then makes a secure connection to transfer any data.

What's good, peeps? I've been noticing some rather advanced tutorials slowly emerging here on Null Byte and I know that people want more of them but I've been reluctant to post something of such caliber because I fear that the information will just go over their heads, but hey, as long as it's there, people can always go off to research themselves and eventually understand. So here is my contribution to the gradual and inevitable progression of Null Byte!

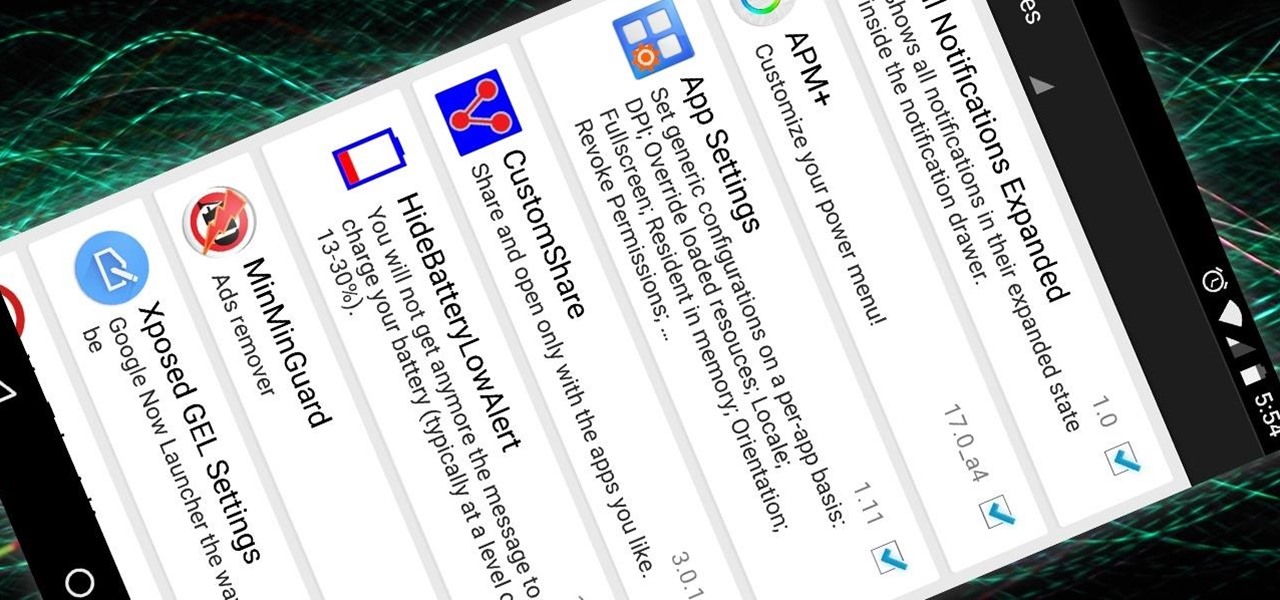
The Xposed Framework was just recently made available for Android Marshmallow, but everything isn't quite back to status quo just yet. Sure, some Xposed modules function properly, but others are a bit buggy, and several don't even work at all. This is mostly a result of changes to the Android system that Lollipop modules relied upon, and such modules will need to be updated for Marshmallow compatibility.

Video covering how to set up a Venn diagram. The video covers how to draw the diagram and then look at a set of data and place the data in the correct part of the Venn diagram. The sample problem is as follows.

Now that the Xposed Framework has finally been updated for Android Lollipop, we're starting to notice that some modules function properly, while others are a bit buggy or even worse—don't work at all. Most of this is a result of changes to elements of the Android system that KitKat modules relied upon, and such modules will need to be updated for 5.0 compatibility.

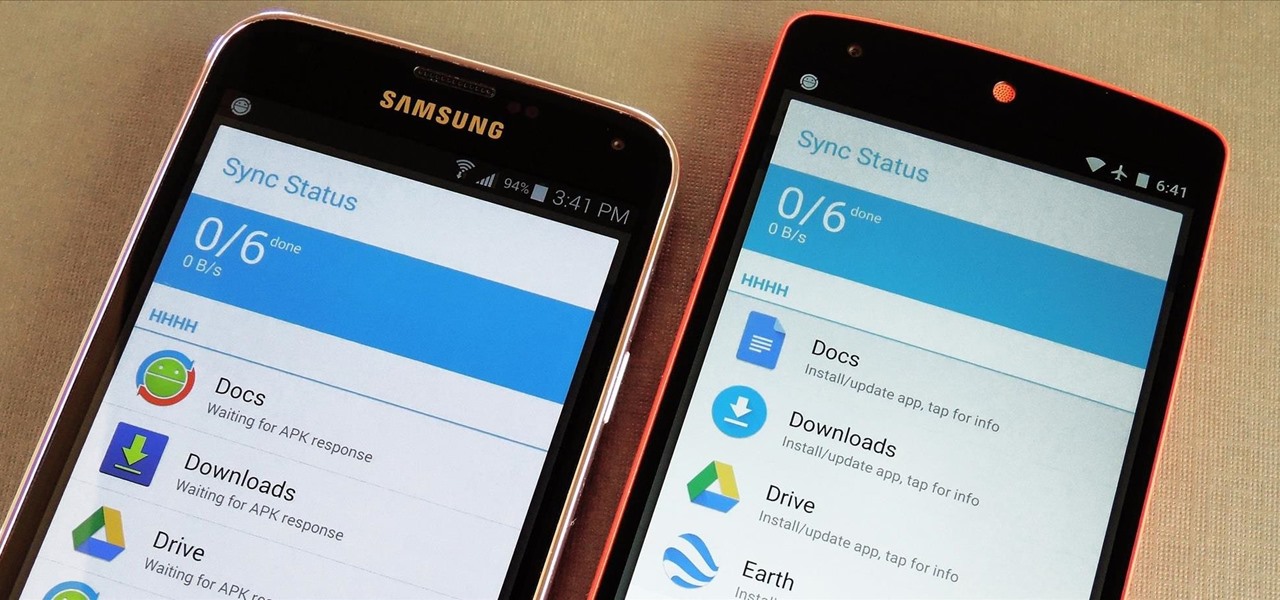
If you own multiple Android devices, you're surely familiar with the struggle of keeping apps and games in sync. While games with proper Google Play Games support will indeed sync progress across your phone and tablet, many developers neglect to include this feature in their wares.

What if someone asks you to do a Nmap scan but you left your pc at home? What if a golden opportunity shows during a pentest but you were walking around the building, taking a break?

Android uses a set of permissions that apps can request to perform certain actions, and you're notified of these permissions each time you install an app. The problem here is the fact that you aren't given any built-in way to deny apps these permissions (although Danny just showed a workaround for this).

Welcome back, my greenhorn hackers! Sometimes, we don't have a specific target in mind, but rather we are simply looking for vulnerable and easy-to-hack targets anywhere on the planet. Wouldn't be great if we had a search engine like Google that could help us find these targets? Well, we do, and it's called Shodan!

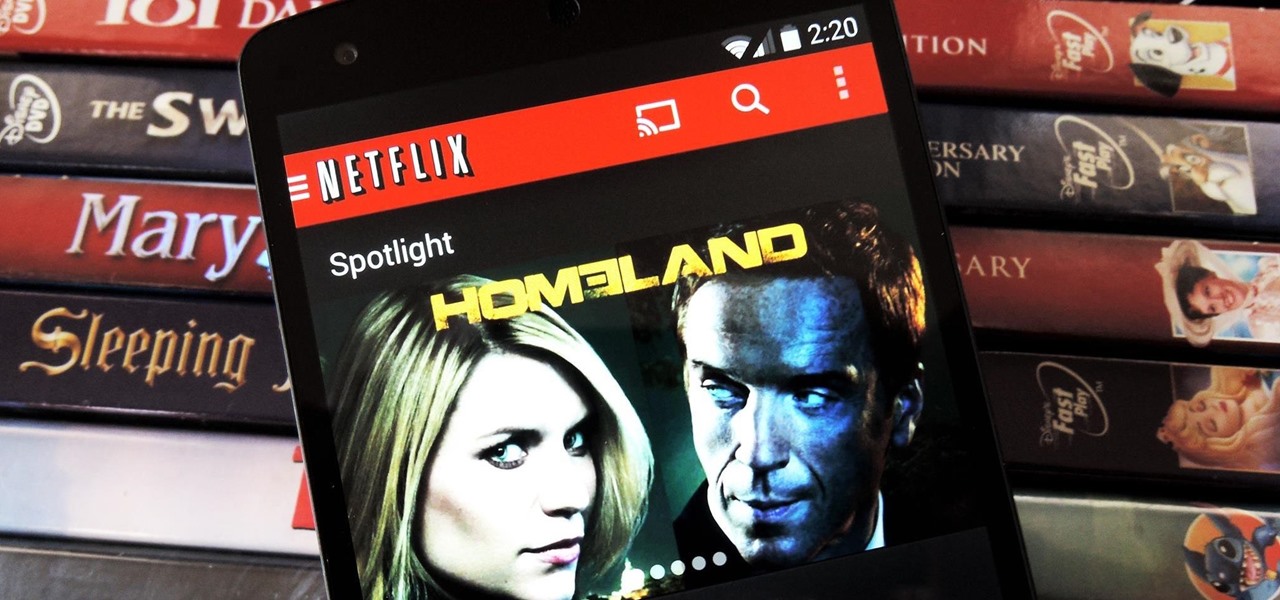
Out amongst the ether of the internet lies a completely different version of the Netflix library you've come to know and love. Because of licensing and rights fees, the streaming media giant maintains separate libraries for each country it services. Ultimately, this means that certain movies and TV shows are only available in certain countries.

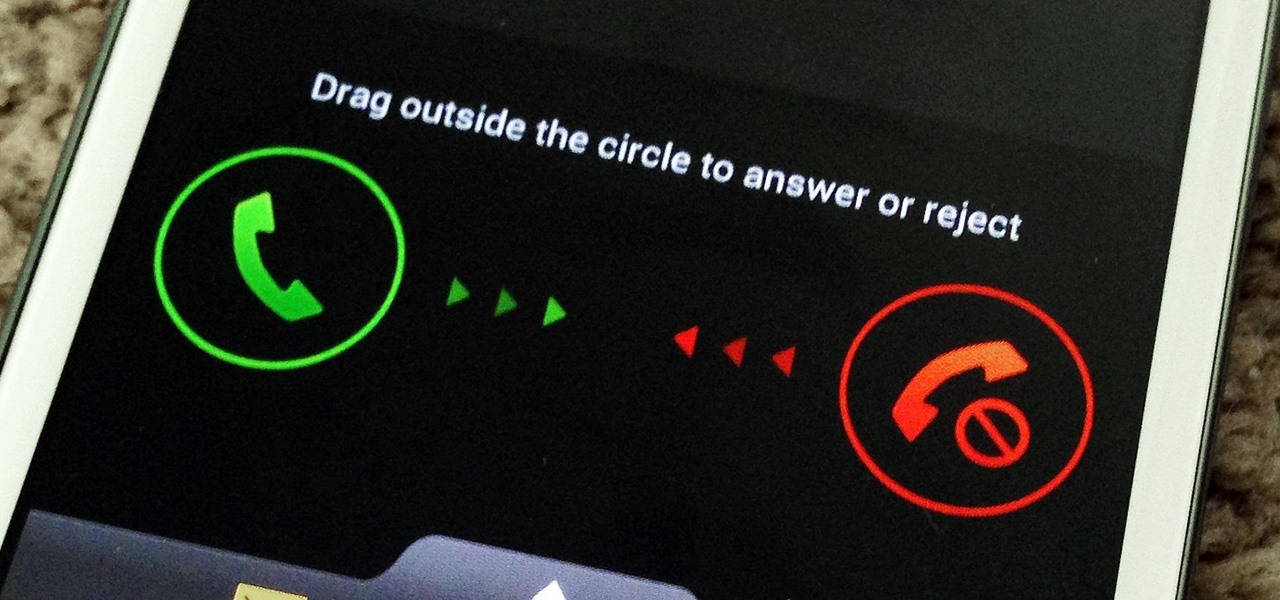
You don't have to be in debt to receive annoying calls from unwanted numbers. You may love your grandma, but if she calls you three times a day to ask how to turn on the television, you might just want to push all of her calls to voicemail.

Welcome back, my fledgling hackers! One of the first issues any hacker has to address is reconnaissance. Before we even begin to hack, we need to know quite a bit about the target systems. We should know their IP address, what ports are open, what services are running, and what operating system the target is using. Only after gathering this information can we begin to plan our attack. Most hackers spend far more time doing reconnaissance than exploiting.

Video: . This video explains how to install Android OS on a PC using VirtualBox. How to install Android OS on a PC Using VirtualBox.

When LinkedIn first arrived on the scene, I thought it was a great resource for staying connected and getting in touch with those people in your desired career path. Keyword: Thought. Like most businesses, money and shareholders seem to have taken over the driver's seat, pushing the company towards a business-first, users-second approach.

The most recent version of the iPhone Software (iOS 5) has the ability to utilize emoticons by use of the native keyboard and software, no third-party app or jailbreak required. Just follow these simple steps for unlocking the emoticon keyboard:

One of American Apparel's most famous articles of clothing for women is their Le Sac dress, which is no ordinary dress. It's simplistic look mocks it ingenious design, which can be shaped, formed, mutated, tie, and tucked in at least TWELVE different ways to create a different dress for each day of the week. The Architectural Mini look is just one of the ways to style it, and this video shows you exactly that. Use this art deco style for a sexy, architectural inspired halter look.

Can you believe this dress? American Apparel have outdone themselves again! A dress that's not just "one" dress, but at least "eight" dresses. The Le Sac dress is a marvelous article of clothing because it can be worn every day of the week… without looking like a hobo. It's a different style each day, with at least TWELVE different styles. And there's even a look for you dominatrices out there, a super sexy and daring S&M style Dominatrix look. See how easy it is!

American Apparel is famous for selling articles of clothing that can be worn in multiple ways. Their latest creation is the Le Sac dress. This dress can be tied and twisted all over the place to come up with TWELVE or more styles! You can wear this outfit every single day and everyone would think you were in something new. So, if you are looking for a sexy, Greek-inspired off the shoulder look, check this official tutorial out for the Grecian look. Learn how to wear your Sac and look amazing.

The fine folks at ITS Tactical made this detailed tutorial on how to make a two-piece lock pick set out of only a few paper clips and using only a multi-tool in the construction. The host begins by demonstrating how to construct the pick, then how to use it on a real lock. It is not as easy as using a real lock pick, but will still work. As the host emphasizes at the beginning of the video, these picks are only to be used in emergency situations, and NOT to break into other people's homes wil...

Many people are frustrated with how big and in-your-face the Facebook news ticker is. If you want to shorten it so that it doesn't take up so much space, try adjusting the length of the ticker with the bar that exists between it and the chat list.

Watch this video to learn how to use Tweetbot and Flipboard. Tweetbot is great for organizing lists in Twitter. Then, you can use Flipboard to create a virtual magazine of your interests. Follow your passions on twitter with these two excellent apps, Tweetbot and Flipboard.

Every year, many people fall victim to scammers trying to dupe taxpayers out of their hard-earned money. The IRS compiles an annual list of the twelve most popular tax scams perpetrated on the public. Check out this video to learn out about the top tax scams to avoid.

MySQL is a structured query language (hence the 'sql'), and is an open source language published by Oracle. If you want to learn how to manipulate and use databases (such as customer lists or membership rosters), you will need to learn MySQL.

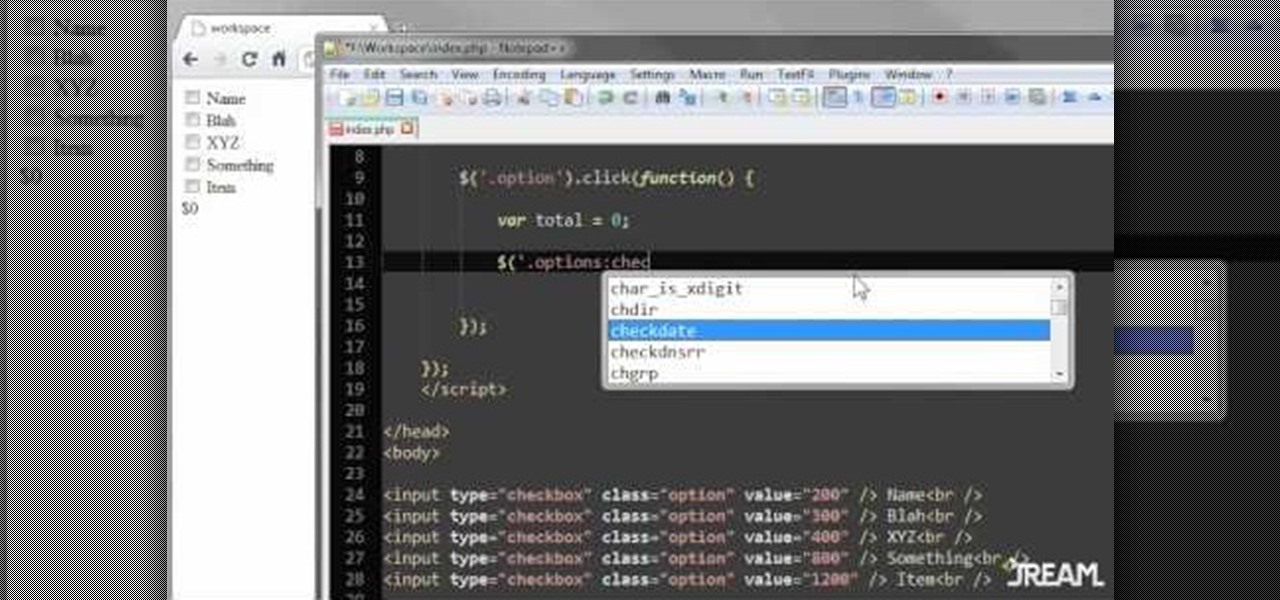
Create a list with checkboxes and assign a price to each item. As your customers check or uncheck the boxes, they'll see the estimated price below change in accordance. This is a quick and easy trick visitors to your website will definitely appreciate.

Who uses phonebooks these days anyway? Even if you still find some use out of your current Yellow Pages tome, it's more likely than not that you're searching up "Thai food restaurants" on Google than actually flipping through pages to find a listing.

Real snakes give us the heebie jeebies. With their slippery skin, scales, and overall slimy quality, they top our list of most feared animals. But we sure love 'em when they come in a cute paper form!

These crafts are ideal handmade gifts, especially if there is a belly dancer on your list. You will need a needle, sturdy thread, scissors, small pliers, clear nail polish and craft glue. And, of course, the medallion you want to use!

If you're looking for some good ideas on what to get your friends, family and loved ones this Hanukkah season, check out this video that lists several creative and inexpensive ideas, such as a personalized dreidel platter or personalized menorah labels.

Whether they're your own children or a niece, godson or grandchild, this gift guide is perfect for figuring out what to give the kids on your gift list. Every gift is innovative, eco-friendly and facilitates talking between children and parents.