Apple pushed out iOS 12.1.3 developer beta 2 to all developers on Wednesday, Dec. 19. It's an interesting and mysterious update, as it follows the sudden release of iOS 12.1.2. That software only had one beta version before its stable release, which would explain why the iOS 12.1.3 dev beta skipped version 1 and went straight to version 2 since it's basically a continuation of the first iOS 12.1.2 beta.

For many, phones are starting to replace televisions as the primary device for watching videos. Thanks to their portability and easy to use apps, it's often simpler to watch Netflix, Hulu, YouTube, or Prime Instant Video on the smaller screen. But not every phone is suited to fit this need, so we did some testing to find the best of the best when it comes to streaming videos.

Smartphones and laptops are constantly sending Wi-Fi radio signals, and many of these signals can be used to track us. In this guide, we'll program a cheap IoT device in Arduino to create hundreds of fake networks with common names; This will cause nearby devices to reveal their real trackable MAC address, and it can even let an attacker take over the phone's data connection with no warning.
While there are over 100 cool features iOS 12 has to offer, there are some things Apple has made more annoying on iPhones or just has not addressed yet.

For years, Skype has been synonymous with video calling and messaging. However, as the industry moved toward encryption and privacy, Skype usage was discouraged by experts due to its murky encryption. To combat this, Skype has introduced true end-to-end encryption.

Mozilla has created yet another browser for Android. Similar to Firefox Focus, Firefox Rocket was designed to address specific problems: limited internal storage and low data caps. However, in the process of solving these problems, they created one of the fastest browsers on the market.

When you first update to iOS 12 on your iPhone, notifications on the lock screen and in the history will be grouped automatically into stacks based on a variety of factors for each app. For example, articles from Apple News will be stacked together based on sites. But you can also change this so that all alerts from a particular app will be grouped in one bundle, not separate ones.

A burner number isn't just for criminals and cheating spouses. In this digital world, with many of our interactions being conducted online, a throwaway phone number acts as a buffer — it lets you enjoy the web without having to give out your personal information, such as real name or phone number.

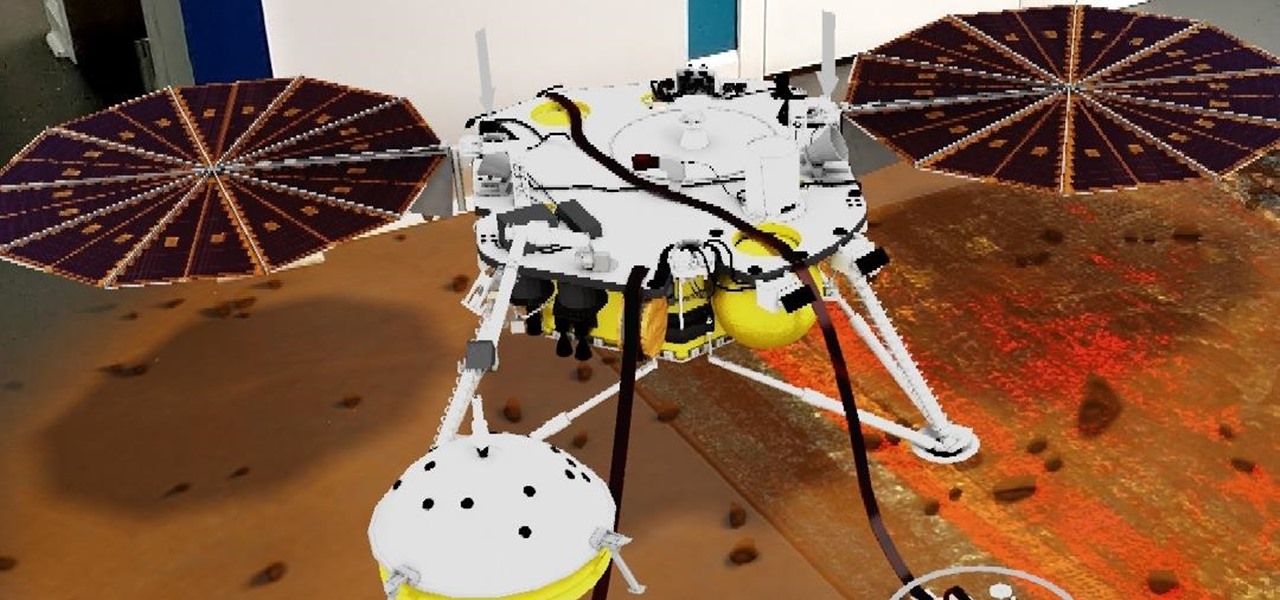
In the latest installment in its burgeoning augmented reality journalism practice, The New York Times is bringing its readers closer to Mars and NASA's latest spacecraft set to travel to the red planet.

It turns out that coming up groundbreaking technology and raising billions may actually be the easy part for Magic Leap, as a new report has revealed yet another legal entanglement at the Florida-based company.

Android's share intents system is great in theory, but the execution can sometimes be frustrating. When you tap the "Share" button next to a link, app, or file, you see a list of apps you can share that item with. But it seems like every time you use this function, the list of apps is in a different order — especially when it comes to the Direct Share targets at the top.

As the first Animal Crossing game on mobile devices, it's clear that Nintendo had a more social experience in mind for Pocket Camp, and I'm not talking about all the animal friends you can make. You can add other players to your list of human friends, and they're incredibly useful for a wide array of tasks.

The Xposed Framework has an official repository for downloading modules which can be easily accessed by searching the Download section in your Xposed Installer app. But not every module is available on the Xposed repo — in fact, many unique and interesting modules are only hosted on third-party servers.

By default, when you receive a FaceTime video call on your iPhone, the speakerphone kicks in immediately after answering unless you're wearing headphones. It's the exact opposite when it comes to FaceTime audio calls, but it's pretty easy to remedy if you'd rather have the speakerphone kick in instead of the built-in ear speaker.

Within the last week, there have been at least three times when someone asked me to play a good playlist. This is always a tough call. What if I play something that nobody likes? I probably will.

In the SoundCloud app, when you find an awesome song, you can build off of it by creating one killer music station that will give you like-minded songs you might not have ever discovered otherwise. And finding cool new songs and artists isn't the only reason to create a SoundCloud station — it's a great opportunity to set the tone of your workday or your party without ever worrying about the music ending.

In this article, I am most likely going to humiliate myself by showing you all the horrible hashtagging I am wont to do. When it comes to hashtags, well, everybody knows if you desire any chance at all of getting noticed on Instagram, you got to hashtag.

Sometimes you need a password to gain access to an older running Windows system. Maybe it's a machine in your basement you forgot about or a locked machine that belonged to a disgruntled employee. Maybe you just want to try out your pentesting skills.

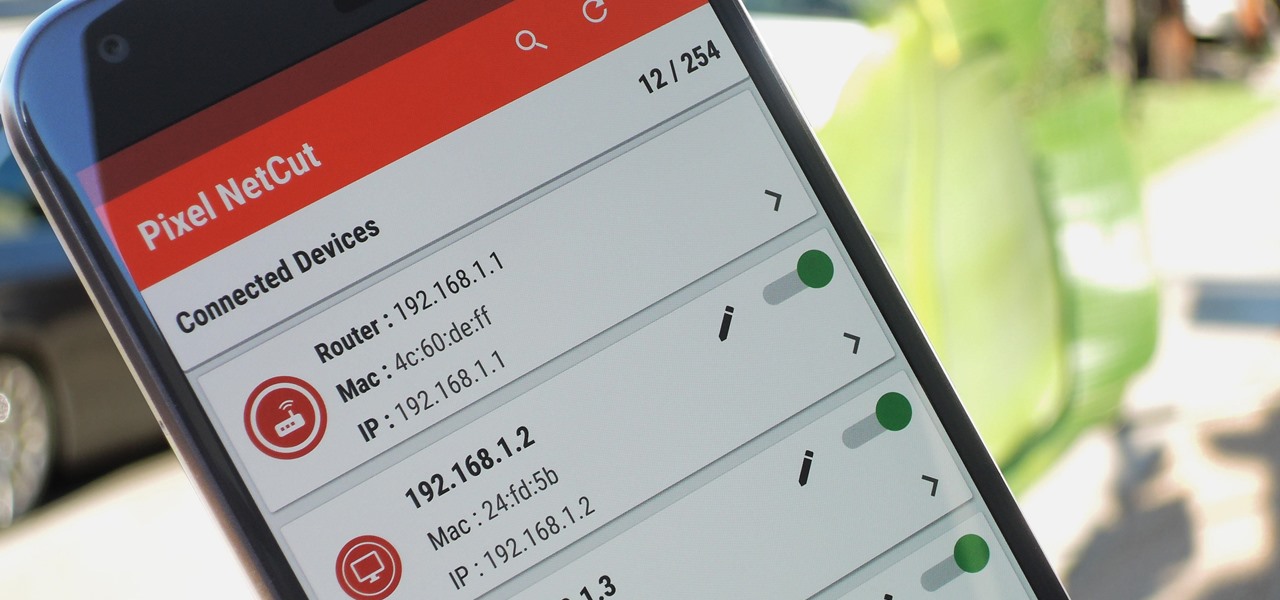
Let's say you gave your Wi-Fi password to your neighbor a while back, under the assumption that they'd only use it while they were at your house sharing stuff via Chromecast. But now, your connection is slower than it normally should be, and you have this sneaking suspicion that the dude in apartment 3C is flat-out piggybacking off of your home network.

With the release of the Mirai source code, botnets are back in a big way. In the early days of botnets, zombies (infected hosts) would report to IRC (Internet Relay Chat) channels for CNC (command and control) instructions. Modern botnets have evolved, but they continue to use the same concepts as their predecessors.

Welcome back everyone! It's been awhile hasn't it? Sorry for being so quiet, but my CCNA courses have really picked up recently. In the last article we covered how to import modules and how we can use them. In this article, we'll actually be covering a module that is essential to the hacking aspect of Python, sockets.

Hello everyone! I hope you are having a great day so far. Today, instead of caring about networks we are going to talk about subnetting based on host requirements as promised in my first article about subnetting. Just like in the previous articles we will jump right into the examples because that's the best way to learn.

How much you've actually spent and how much you think you've spent are usually two completely different results, and is especially true on Amazon when it's so easy to click and buy. You might think you've given Amazon a couple thousand over your lifetime, when the fact is that it's three or four times that amount.

Hello, everyone. Stealth is a large part of any successful hack; if we don't get noticed, we're much less likely to be caught. In these next few articles, we'll be building a shell based on keeping us hidden from a firewall. There are many ways to stay hidden from a firewall, but we'll only be incorporating a couple into our shell. This article will outline and explain these evasion concepts and techniques.

Another series I am now starting, might have to slow down on all of these series, but why tf not. What Is CMD?

The Google Cast feature that serves as the primary interface for the Chromecast and comes bundled with Android TV devices like the Nexus Player is a marvel of modern technology. But as these things go, troubleshooting issues can be difficult with something so groundbreaking, especially when you consider that there are two parts to the equation—the casting device (your phone, tablet, or computer) and the receiver.

Before we dive into the world of frustration, I first would like to thank whoever of the admins and mods made the folder for Raspberry Pi in the How-To's, thank you. Now with that outta the way, this article is about Metasploit on Raspberry Pi (hence the title). I should say that I ran into a error, but I think I figured what the problem is. First of all this is not on Kali Linux, but on a regular Linux OS. With that said let's open up a terminal and begin.

Hello, everyone. If you've been following my recent articles, you'll know that I've been rather busy lately working on a project, a rather large one. I've been working with Pheonix750 and Ciuffy to build the Null Byte suite of tools! I got the green light from our admin a while ago, and we've been developing like mad ever since! I'm very excited to launch this project. So, let's start by explaining what it is...

In the tech world, it's all too common to slap a fake label and packaging on a lower quality product, especially SD cards. If you've ever bought an SD card on the cheap from a slightly-less-than-reputable source (or even a reputable source, in some cases), how do you know if it's the real deal?

This Video will show you how I make Cucumber and Tomato Salad.

One of the biggest new features in the soon-to-be-released Android 6.0 Marshmallow is something Google is calling "Now on Tap." Essentially, this service will be able to scan the contents of any screen on your Android device, then after you long-press the home button, it will provide you with relevant information about anything—from movie times to directions or dinner reservations.

Both the Galaxy S6 and S6 Edge have had root methods available to them before the phones were even released, but the problem with these existing root methods is that they would trip the KNOX counter on your device.

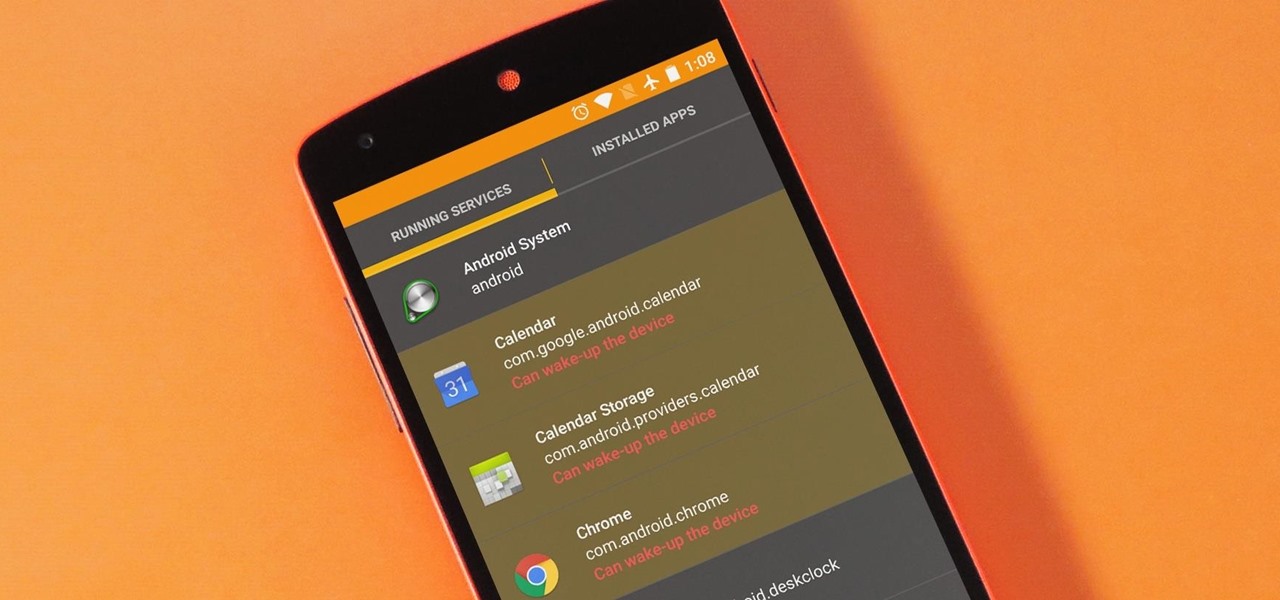
The vast majority of Android apps use background services to sync data, check for location updates, and perform various silent tasks. These background services can start up whenever they'd like, and they continue to run in the background even when you're not actively using the app that they originated from.

For all of the flak that it catches, Wikipedia is still a great source of information. Contributors take their work very seriously, so the vast majority of information is cited, and the site serves very well as a starting point to learn about a new topic.

The Watch Later feature lets you conveniently save videos to watch at a later time, using a playlist. Hover your cursor over the thumbnail of a video, like the one below, and click the clock icon to automatically add the video to your Watch Later list.

iTunes 12 was released alongside Yosemite this year, but it didn't pack quite the punch that the operating system did. Instead, iTunes received a minor facelift, with few new features and somehow lacking the intuitive feel of its predecessor. If you're not thrilled with iTunes 12, we've got a few tips to help you feel like you've got iTunes 11 back on your computer!

App-locking apps have been around for a while, but none have had quite the panache of developer Fazil Kunhamed's latest offering, Oops! AppLock. While others use a PIN or password to restrict access to apps that are installed on Android, AppLock uses a stealthy volume button combo.

If you accidentally deleted a few contacts in Gmail, don't worry. You could still restore or find those email ids. This video will show you how to recover those contacts and bring back to your contact list. The process of recovering those contacts is quite easy. So please watch the video and follow all the steps carefully.

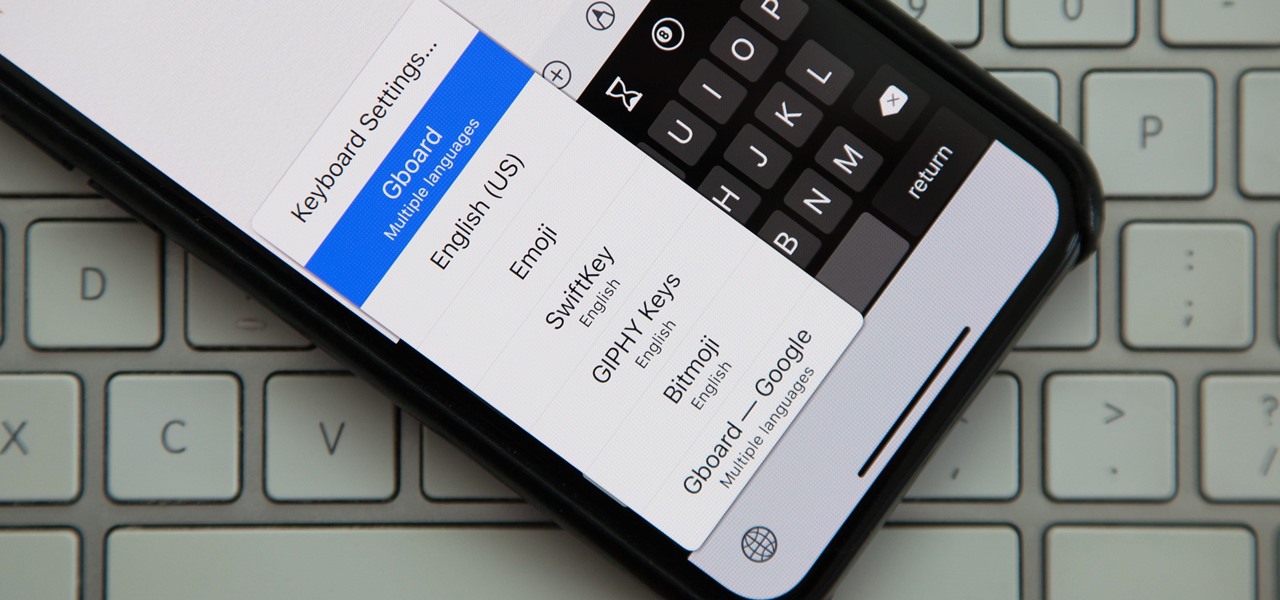
Back in iOS 8, Apple introduced the option to use third-party keyboards on iPhone, and since then, there have been a ton of third-party keyboards available such as Gboard, AudioShot, SwiftKey, Slated, and many more. However, adding and even using these keyboards can be kind of tricky.