Welcome back everyone. I apologize for the lack of training articles, but I've been rater busy lately. I've recently picked up a second job and my college courses are now back in session, so I'm a bit strapped for time.

Good day people, today we will examine some basic, for some people well-known attacks, also we will take a look at some advanced attacks.

Welcome back, everybody. In the previous article, we covered the ideas and concepts of well-known ports and trust exploitation in order to evade a firewall. Today, we'll be building the shell, the part that receives commands, executes them, and sends the output back to the attacker.

Brand loyalty is one of the main factors behind our decision to choose a particular mobile device, but it doesn't have to be the entire equation. Educated consumers know that certain devices simply fit their budget and usage better than others, which means you can't always let a logo dictate what kind of phone or tablet you buy.
Basically, this article is a true life experience writing from the introspective mind of the writer and do share more knowledge on how to deal with introvert lifestyle.

Android has a single text file named build.prop that determines tons of various system-wide settings on your device. You need root access to edit this file, since it's stored on the system partition—but the various lines of codes it contains are actually fairly easy to interpret and modify.

In this article, we will build a parallel password cracker using the techniques explained in the previous part. As SHA-512 is the digest function that Kali (and most modern Linux distributions) use to store our passwords, we will make a SHA-512 password cracker.

Hello again, ***UPDATE: Adding links to the other Two articles****

As many of you know, processor's clock frequency improvement got stuck in about 2003, causing the origin of multicore CPU (and other technologies). In this article I'll introduce you on how to run code simultaneously in various processors (I suppose that all of you have a multicore CPU). When you write code without any parallel directive, it only executes in one CPU at the same time (see it below). OpenMP make simple to work with various cores (if not with all of them) , without so much heada...

Welcome back! In the last iteration of how to train your python, we covered loops, today we'll be covering something that I wish I had learned about much earlier in my scripting career, errors. We all run into them, and they can be frustrating, but there is also a silver lining to them. Today, we'll be discussing why some errors are unavoidable, and what we can do when we run into them. Also, this article will be more of a concept and less of writing actual code, but the information is equall...

In general, smartphones and cars don't mix—but this is mainly because you have to take your eyes off the road to poke around on your handheld gadget. In reality, the only difference between your smartphone and your car's FHWA-approved infotainment system is that the latter is mounted in a fixed position and has an oversized interface that makes it easy to use without looking away from the road.

Apple Pay has been available to use in stores, as well as in select apps and websites, ever since its first appearance in iOS 8.1. Now, with iOS 12, there are currently 13 different iPhone models that support Apple Pay functionality without the use of an Apple Watch, and the list of partnered stores that accept Apple Pay has only grown. Here's our always-up-to-date list to keep you in the know.

Just the fact that you own an Android device means you're privy to an entire world of third-party development. Many of the mods you'll see here on Gadget Hacks can be performed fresh out of the box, but with root and Xposed, the list grows longer. But to truly be able to take advantage of all that Android's massive development community has to offer, you'll need to have a custom recovery installed.

There are a lot of techniques out there for how to cook the perfect steak, from flipping it multiple times to applying a spice rub or dry brine to aging the beef. But it turns out that there's a super-easy way to make a great steak at home, and all you need is a good cast-iron skillet and some salt.

Many of my aspiring hackers have written to me asking the same thing. "What skills do I need to be a good hacker?"

This year, like every year before it, Black Friday sales are starting earlier than ever. A lot of stores will be opening their doors as early as 5pm on Thanksgiving to get a head start on the madness (and it really is madness). As we've discussed in the past, one of the keys to emerging victorious on Black Friday is to plan, plan, plan. So, we've compiled some of the best deals in tech, gadgets and appliances to help you prepare for battle.

Life has many perils: parasites, predators, and pitfalls. Eventually, any organism will succumb, and if that organism has not first passed on its genes, those genes will face extinction.

In this article, I'll be continuing my series on microcontrollers. If you haven't read part one, I'd recommend heading over there and reading it!

A Steampunk's Guide to Sex was the subject of a recent successful Kickstarter campaign, and I now hold the finished book in my hands. As such, I can say (mostly) unreservedly that you should buy this book. Allow me to tell you why, before I get into the nitty-gritty about the book itself. Sex is something of an odd topic in America because it's perfectly legal, and yet taboo. Unlike things that are illegal and not taboo, like drug use, murder, theft, etc. What this means is that children can ...

In evolutionary times, we were far more likely to die from starvation than from diseases related to obesity. In those times, when food was available, it was best to stuff oneself.

If you've ever logged on to the popular music application Pandora, your password is saved onto that computer in the local storage...for good.

Traps are great, but sometimes you don't want to kill anyone, you just want to know when they're around. When that's the case, check out this handy alarm system that uses the power of doors! Doors, you say? Yes, doors! Some of you may already be familiar with how obnoxious doors can be in Minecraft, but if not, check out this video of it in action:

So, you're browsing the web on your iPhone using Safari, and you come across a picture you really want to keep forever and ever… what do you do? You can save it directly to your phone! But how do you download that web image? Best Buy has answers. The Best Buy Mobile team explains how simple it is to save web images from Safari on your Apple iPhone.

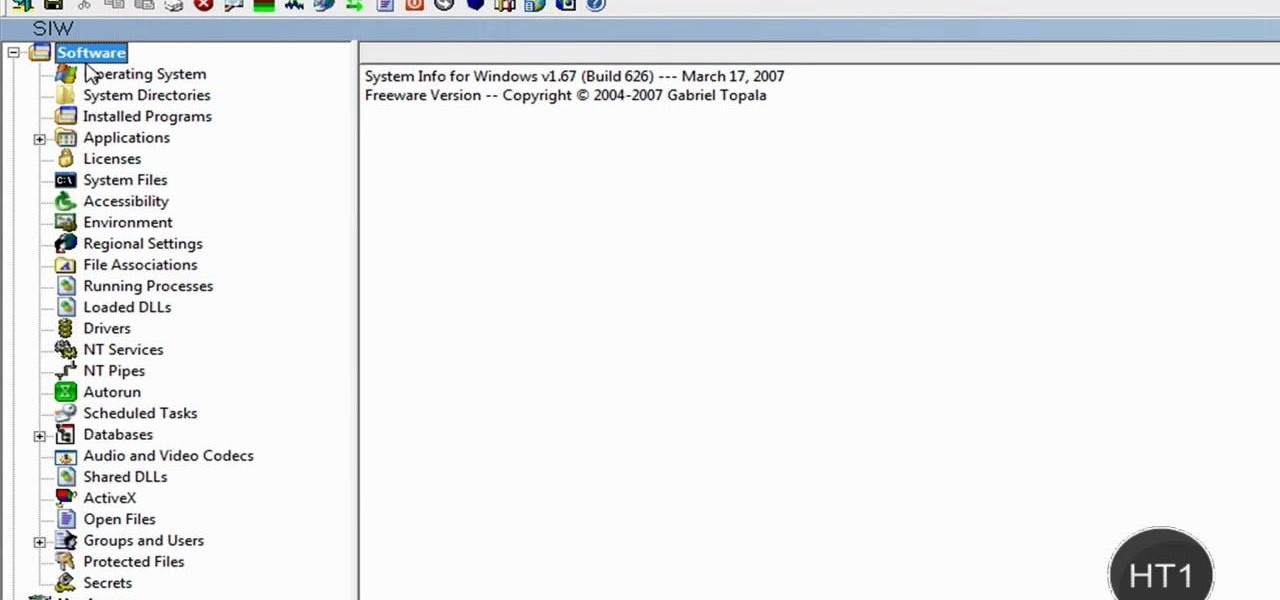
How to find out information / details about your computer? To find out the information about your computer, you need to download software from the website PC World. The following are the steps to download the software:

Learn how to clean out unwanted programs from your PC's hard drive. Running out of storage space on your PC? Free up some real estate by deleting programs you no longer need on your hard drive.

This video includes instructions on how to get your PlayStation Portable (PSP) onto the BGSU wireless network.

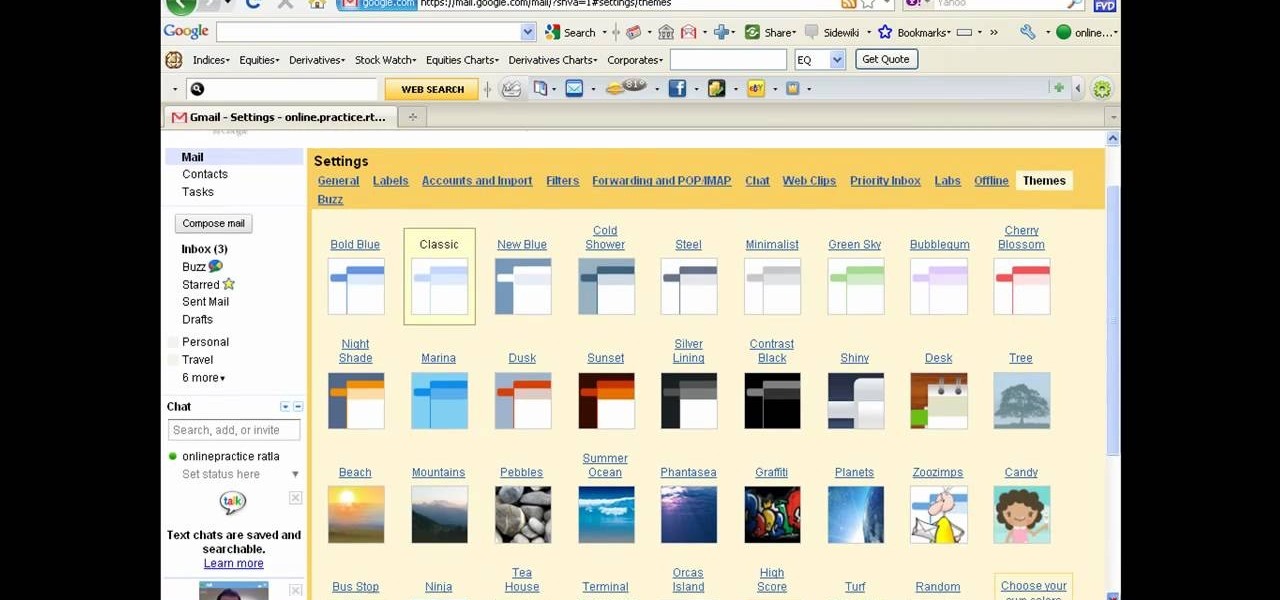
There a ways to personalize your Gmail experience, and one of those is picking personalized Gmail themes which make emailing funner. But if you're not sure what kind of theme you want to use from all the available Gmail theme choices, there's an option called "Random" which provides you a random theme based on your geographical location, and will change when in a different location.

Want to make a Bloody Jack like a champion bartender? This clip will show you how it's done. With the proper technique, mixing the perfect drink can be easy. So easy, in fact, that this free video bartenders' guide can present an overview of the process in about a minute's time. For more information, including a full list of ingredients and complete instructions on how to mix this drink yourself, take a look.

In this video tutorial, viewers learn how to enable hidden God Mode in Windows Vista 32 bit and 7. This option does not work on Windows Vista 64 bit. Begin by right-clicking on the desktop. Then go to New and select Folder. Now name the folder to a desired name and paste this code behind it: .{ED7BA470-8E54-465E-825C-99712043E01C}. Users will now have a full list of control options for their computer system. This video will benefit those viewers who use Windows 7 and Vista, and would like to ...

In this video, Rick Pin teaches us how to measure the clutch fork pedal travel in a Saturn S series. First, remove the air box and the resonator box from the vehicle. Also remove the duct work from the vehicle and set aside. Once these are removed, you will be able to see the plate cylinder underneath where the air box was. To measure the fork travel, us a piece of wire with tape on it that has measurements listed. Push down on the clutch travel as you do this, then remove the wire and you wi...

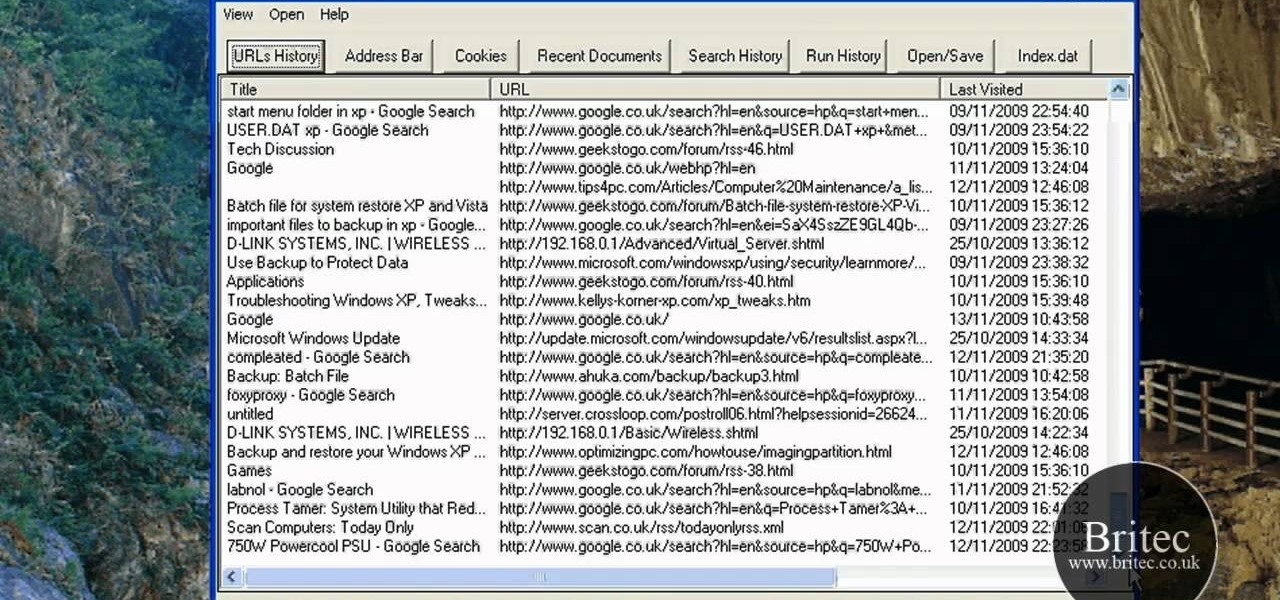
Interested in reading the list of web addresses in an index.dat file on a Microsoft Windows computer? This clip will teach you everything you'll need to know. With WinSpy, it's easy! So easy, in fact, that this home-computing how-to from the folks at Britec can present a complete overview of the process in just over two minutes. For more information, including detailed, step-by-step instructions, take a look.

Want to make a Special K like a champion bartender? This clip will show you how it's done. With the proper technique, mixing the perfect drink can be easy. So easy, in fact, that this free video bartenders' guide can present an overview of the process in about a minute's time. For more information, including a full list of ingredients and complete instructions on how to mix this drink yourself, take a look.

This video tutorial is in the Computers & Programming category where you will learn how to secure your wireless internet connection. If you don't secure your wireless internet connection you are allowing others to enter in to your network. Open the set up CD and first change the network name from the default name to anything that you like. For this go to step 3 of 'naming your network', type in your network name and click 'next'. Then you enable security on the network by choosing 'WPA2'. Nex...

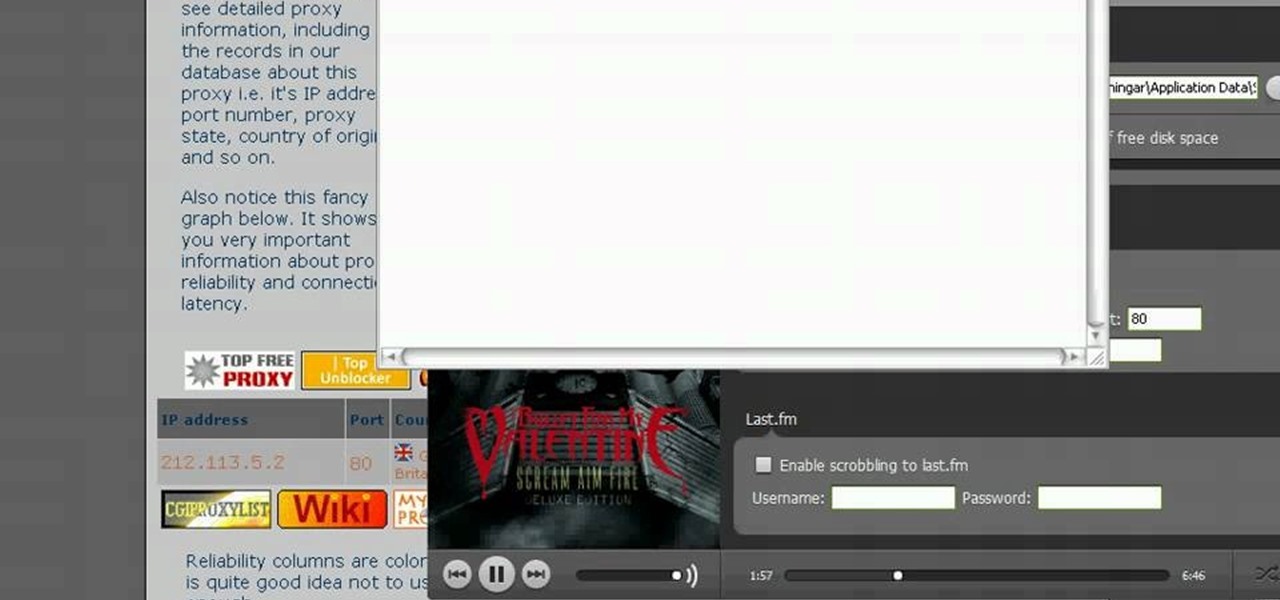
In this tutorial, we learn how to remove the ads from Spotify. First, you will need a proxy, which you can get from the website: Proxylist. Just simply click on a free proxy once you get to the site, then write down the proxy and port. Next, go to edit, then preferences. After this, change the auto-detect to https, then put the proxy next to the box that says "host". Next, type in the port next to where it says "port", then click on the "apply" button listed at the bottom of this window. Now ...

In this video, we learn how to submit a children's book manuscript to publishers. First, you will want to type your manuscript oh white paper and make sure it's double spaced and indented at the beginning of each paragraph. Use one inch margins on each side as well. Make sure the pages are number consecutively and your name, address, phone number, and e-mail are listed on the cover page. Don't break the text up and don't include pictures unless you're a professional illustrator. When you are ...

In this video, we learn how to upload Wordpress files using Filezilla. Before you get started, you will need to know the host, username, and password for your domain name. After this, click the quick connect button to connect to your server. The left hand side will show the local files on your server. Look in the root directory of your server and right click, then choose "create directory". Now, click on the plus sign to see a blog sub directory. Next, find where you downloaded Wordpress onto...

In this video tutorial, viewers learn how to uninstall the video card drivers on a Windows computer. Begin by clicking on the Start menu. Then right-click on My Computer and select Properties. Now click on the Hardware tab and click on Device Manager. In the list, click on Display Doctors and select the desired video card. Now double-click on the video card and select the Driver tab. Finally, click on Uninstall and follow the process to remove the drive. This video will benefit those viewers ...

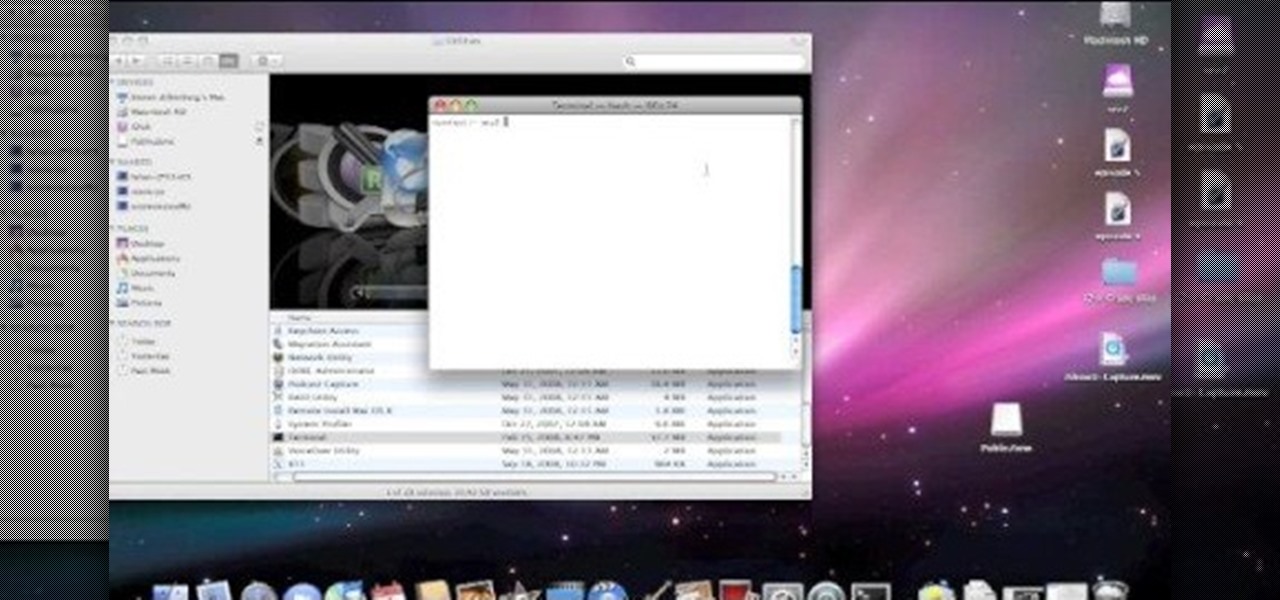
In this tutorial, we learn how to eject devices from the use of the terminal for Mac. First, go to the terminal of your computer where you will see a notepad sort of page. Next, type in "df" and then press return. You will now see a list displaying processes on your computer. On the bottom will be your public zoning device, which is your USB device. Next, type in "hdiutil eject -force (the code under "mounted on)- volumes-publiczone". This is not case sensitive, but don't forget or add in any...

In this video tutorial, viewers learn how to speed up the Windows XP Start menu. Begin by clicking on the Start menu and select the Run program. Then type in "regedit" and click on OK. Now select H KEY_CURRENT_USER, go to Control Panel and click on Desktop. On the right side of the window, scroll down the list to find Menu Show Delay. Double-click on it, change the value to 0 and click OK. This video will benefit those viewers who use a Windows computer, and would like to learn how to speed u...