The North remembers...that smartglasses are the future! Game of Thrones jokes aside, the smartglasses startup opened its doors, and we visited its Brooklyn store to get our hands the consumer-focused Focals smartglasses.
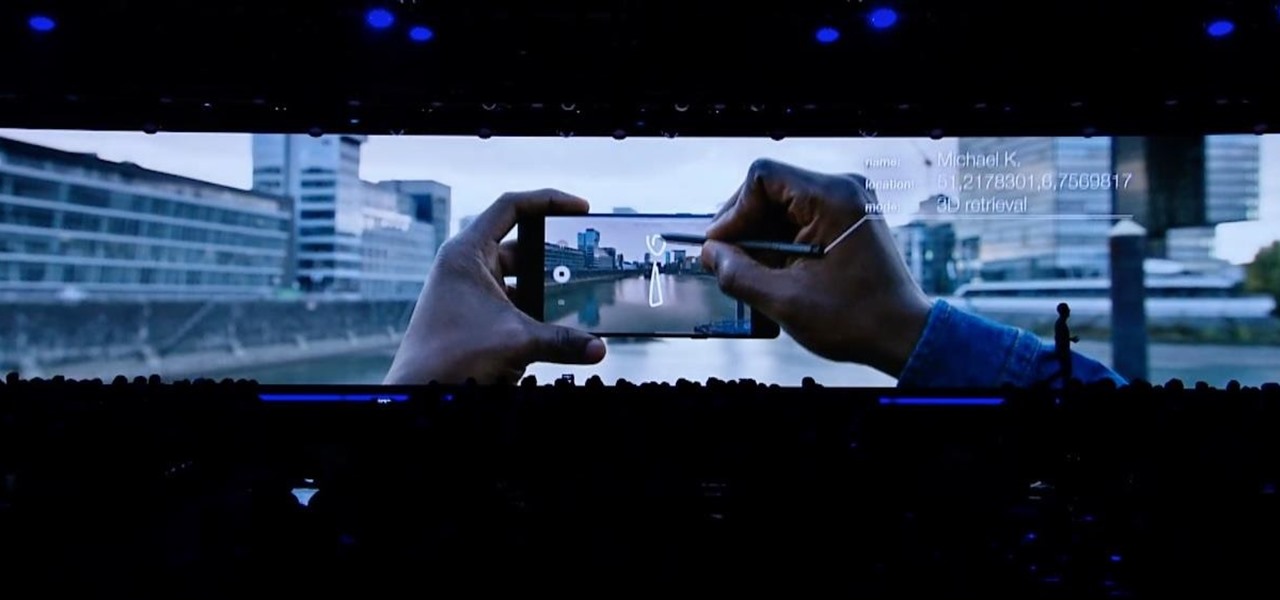
This week, at its developer's conference, Samsung took the wraps off a new tool from Wacom that bestows the S-Pen with AR powers, as well as its own entry to the AR cloud market called Project Whare.

This week, inside sources divulged details of how Apple nearly acquired Leap Motion, twice. Otherwise, companies offering or working on augmented reality technology had more successes than failures to talk about.

This week, Next Reality published profiles on the leaders in augmented reality hardware industry, with Magic Leap CEO Rony Abovitz topping the list. So, it should be no surprise that two app makers want to align themselves with Magic Leap's flagship product.

This week, Next Reality published its annual feature on the leaders in the augmented reality industry, the Next Reality 30. So it's no coincidence that the companies represented in the top four spots of the NR30 also made business headlines in AR this week.

Despite the launch of ARKit a year ago, and ARCore this year, a true killer app has not arrived for either platform, that's according to the head honcho for one of the leading development environments for 3D applications.

For the augmented reality hardware industry to progress towards the consumer segment, display technology needs to get better. Investors recognize that, and they are showing AR display makers the money.

Apparently, it's Google Week for the augmented reality business. Now that ARCore has a firm foothold in the app ecosystem, Google is making a case with educators and marketers that the apps should have a place in schools and campaigns, and the company is also encouraging developers to learn how to build apps using ARCore.

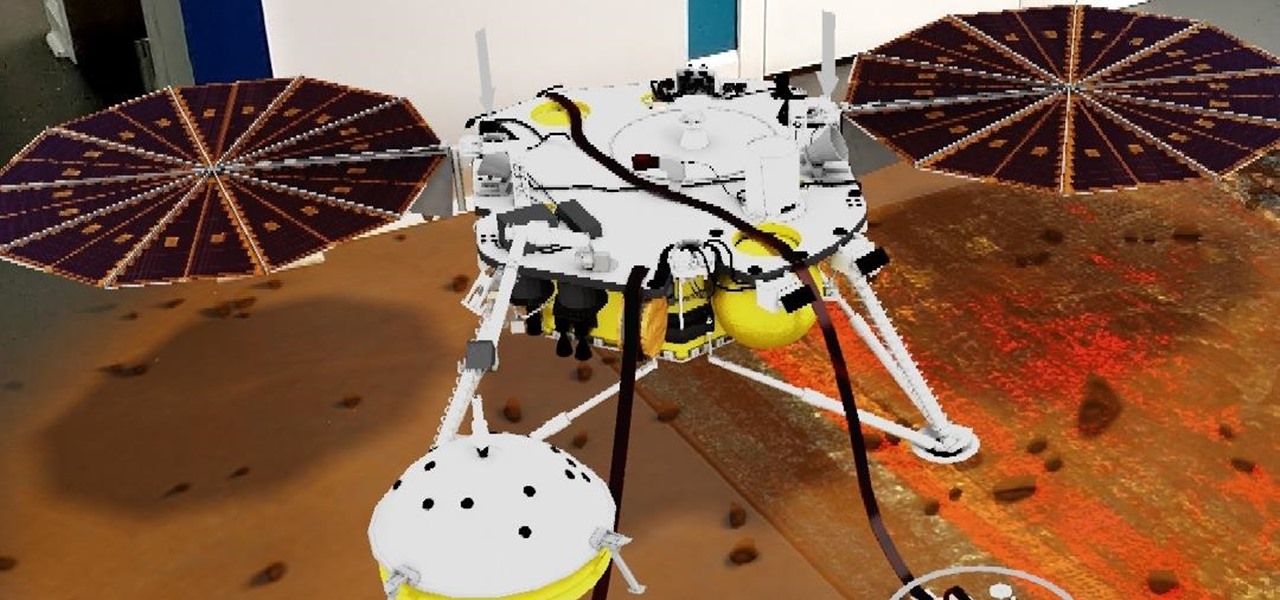
In the latest installment in its burgeoning augmented reality journalism practice, The New York Times is bringing its readers closer to Mars and NASA's latest spacecraft set to travel to the red planet.

As the calendar year (and, for many companies, the fiscal year) comes to a close, it appears 2017 may stand as the new high-water mark for investment in augmented and virtual reality technology.

When a firm like Techstars believes that augmented reality is an attractive industry to invest in, there's a high probability that it's right.

If competition in the augmented reality space was a spectator sport, then ARKit, ARCore, and HoloLens dominate the prime-time broadcasts on ESPN.

Every year, football fans get excited about the next crop of blue chip prospects joining their teams, from five-star high school recruits graduating to college to first-round rookies drafted into the NFL.

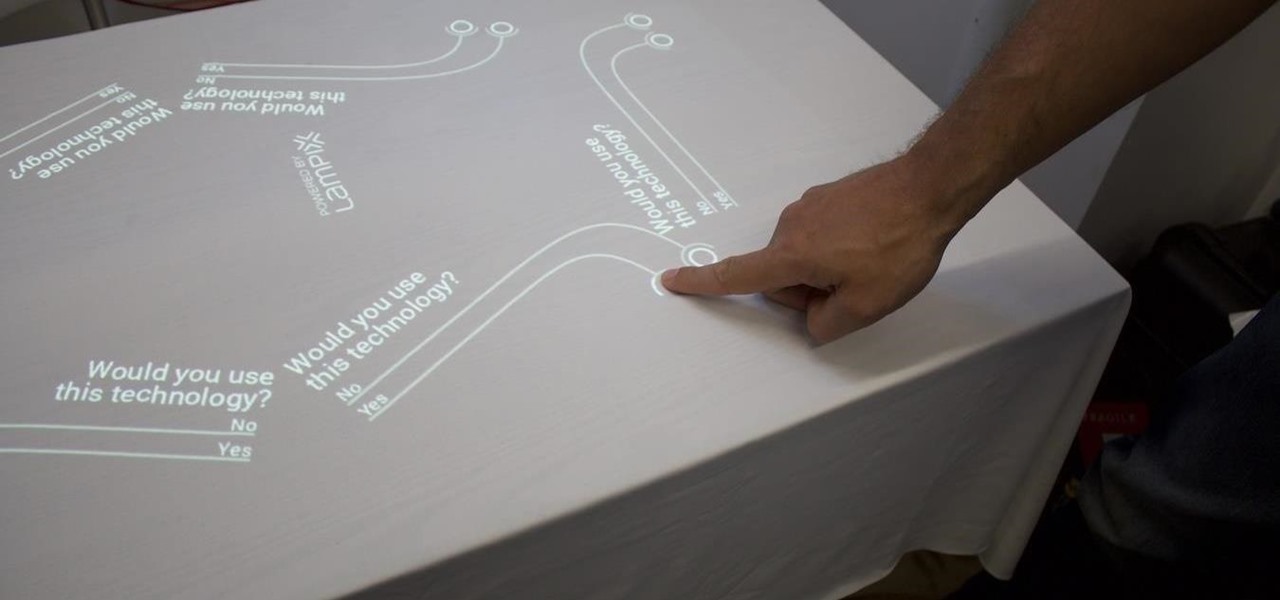
Over the past week, companies took a variety of approaches to investing in augmented reality. Lampix is backing its own effort to build an ecosystem for augmented reality platforms. Nokia and Xiaomi are teaming up on numerous fronts, potentially including augmented reality.

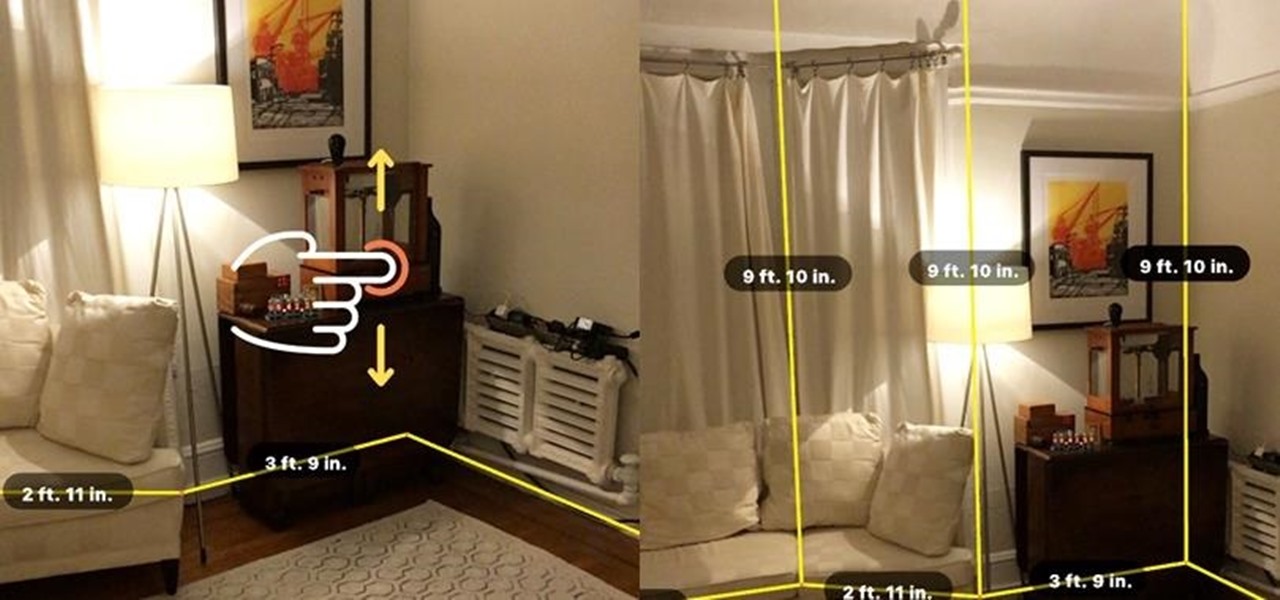
At the moment, it would be safe to say that demand for devices running Tango, Google's augmented reality smartphone platform, is relatively low among consumers. Kaon Interactive, a B2B software company who has built more than 5,000 interactive applications for use at trade shows, remote sales demonstrations, and other customer engagements, is betting that there is a market for the devices in sales and marketing.

HTC is working on another flagship device that's expected to be released in mid-April. After the disastrous reception of the recently released HTC U Ultra and HTC U Play, this new model could be the true HTC 10 successor we've all been waiting for.

Looking to get seriously tatted up? Your best bet is probably to head Down Under. Meet Steve Butcher, a New Zealand native who is changing the tattoo game in a big way. While there are a lot of amazing artists out there, the level of detail Butcher is able to achieve is truly unbelievable.

Welcome back everyone! It's been awhile hasn't it? Sorry for being so quiet, but my CCNA courses have really picked up recently. In the last article we covered how to import modules and how we can use them. In this article, we'll actually be covering a module that is essential to the hacking aspect of Python, sockets.

Hello, everyone. Stealth is a large part of any successful hack; if we don't get noticed, we're much less likely to be caught. In these next few articles, we'll be building a shell based on keeping us hidden from a firewall. There are many ways to stay hidden from a firewall, but we'll only be incorporating a couple into our shell. This article will outline and explain these evasion concepts and techniques.

Before we dive into the world of frustration, I first would like to thank whoever of the admins and mods made the folder for Raspberry Pi in the How-To's, thank you. Now with that outta the way, this article is about Metasploit on Raspberry Pi (hence the title). I should say that I ran into a error, but I think I figured what the problem is. First of all this is not on Kali Linux, but on a regular Linux OS. With that said let's open up a terminal and begin.

Hello, everyone. If you've been following my recent articles, you'll know that I've been rather busy lately working on a project, a rather large one. I've been working with Pheonix750 and Ciuffy to build the Null Byte suite of tools! I got the green light from our admin a while ago, and we've been developing like mad ever since! I'm very excited to launch this project. So, let's start by explaining what it is...

Welcome Back !! TheGeeks. SQL Injection (SQLI) Part-1

You must have read news about hackers dumping the data online, recent one was Ashely Madison. It's only the big companies' data, which gets noticed once it is out. There are many other small leaks which don't even get a mention. So this article is the first one of my series which will help you to find hacked accounts. Some of you must already know about this, but this post is intended for the new learners. This also serves as an example of my learning how a good service can be used in other w...

Hey beauties,it's summer time..we need to take extra care of our skin in summer.You must have all noticed skin problems in summer due to the hot-warm weather and the easy,simple and effective formula is to use toners in summer.In market their are so many toners are available but it's always better to use natural products for skin,and nothing can beat the Mint toner.so today I am sharing with you how to make mint toner at home

For all of the flak that it catches, Wikipedia is still a great source of information. Contributors take their work very seriously, so the vast majority of information is cited, and the site serves very well as a starting point to learn about a new topic.

In a era where cyber security is becoming increasingly important, Comcast has decided to use its customers' routers to provide hotspot access to the public. A new program, outlined by Dwight Silverman over on the Houston Chronicle website, seeks to provide Xfinity customers with city-wide Wi-Fi hotspots by using, well...other customers' wireless routers.

¤¤ TRAVEL TIPS TO VISIT SIEM REAP ANGKOR WAT (CAMBODIA) IN ONLY 2 DAYS¤¤ How to visit and what to see in a short time in this popular resort town as the gateway to Angkor Temples, cultural villages and authentic old markets.

Welcome back, my hacker apprentices! Although there is a multitude of different hacker types, the one target they all share is the database. I often refer to the database as the hacker's Holy Grail, or the ultimate prize for an effective hack.

We've all had to write an essay or research paper at some point, and undoubtedly the hardest part about it is always the citation, right? If you ask me, it's a huge pain in the arse. Even more so if you're gathering your facts from a huge variety of sources.

Welcome back, my greenhorn hackers! Several of you have you have emailed me asking whether it's possible to install a keylogger on a victim’s computer using Metasploit. The answer is a resounding "YES"!

"You can never know too much" is a saying you hear all the time. Funny thing is, I have no idea where it originated, and neither do most of the people who continually say it. Nevertheless, it's a statement that very few would argue with.

Even if you're not a hipster with your own self-sufficient garden, making your own edibles at home can be pretty cool. And while it's obviously easier to pick up a bottle of 7-Up at the store, there's something undoubtedly fun about making your own. For those addicted to their fizzy drinks, DIY soda is a great way to save some cash and make their drinks healthier with natural flavors and sweeteners, instead of something like corn syrup or aspartame.

These days, news papers, online editorials and magazines are filled with news on Iran and Syria. Of course, that is expected, as such sources need to stay current to stay in the game. My concern is that most of these articles talk about what to do about these situations.

In this tutorial, we learn how to write a literature review for thesis writers. The three elements are: discuss the most relevant theory, introduce and define key terms, and discuss recent research in the field. You will need to include the most important literature, quote directly only if you discuss at some length, and use indirect quotes as well. Focus on notions you will use in your empirical study. It should be ten pages or less and sources of all quotes must appear in your works cited p...

This is a video tutorial in the Pranks and Cons category where you are going to learn how to perform a simple mind trick with cups. For this you will need three cups or any similar articles under which another object can be hidden. You then ask one of your spectators to hide an object under one of the cups while your back is turned towards the cups. Then you turn around and point out the cup under which the object is hidden. The trick is to put an indiscernible mark on one of the cups that on...

If you own a Porsche, chances are you know how difficult it may be to work on it yourself without the proper help. Taking it to the mechanic is a safe way of making sure your car will be fine, but it's very expensive. Doing it yourself can be difficult, but if you have a good how to video or article it should be fine.

In this video, linguist Bud Brown provides a short lesson on speaking Tagalog. He teaches his viewers how to say that they have just something, such as saying that they have just eaten. There is a conjugation that should be remembered when you want to make a sentence of this form. You have to take the root of the word and double the first syllable of the verb. You then have to add the article "ka" before this verb. For instance, for the Tagalog verb "sabi" which means "to say", you would say ...

To do this, you must be using Safari; make sure you are not using Firefox or another program. This can be very useful for quickly finding information on web pages. Press Command F. This will open up a toolbar on the top of the page which will ask you what you are searching for. Type the word you are searching for into the toolbar. The word will be highlighted on the web page; you can then click the next arrows to find the section of the page you are looking for. This can be used to find speci...

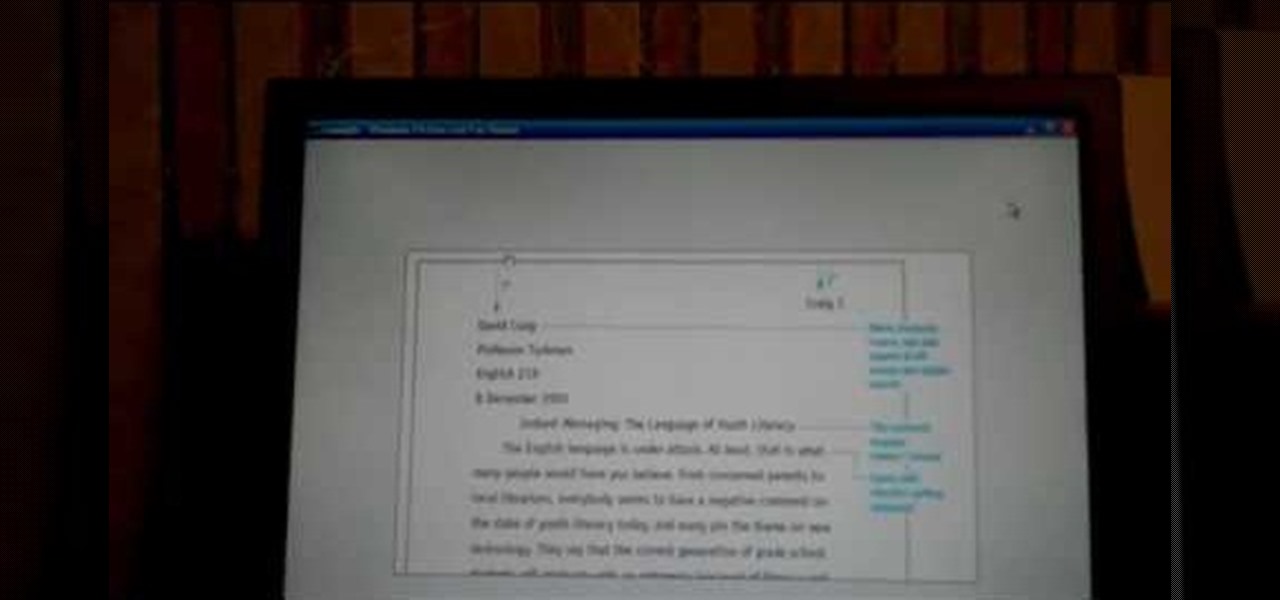
The video demonstrates how to get started with MLA (Modern Language Association documentation format) for an article. One of the first things that is important to understand is how to name your paper, and add a header format that will automatically paginate your paper so that you do not have to worry about it. The entries in your Works Cited need to be alphabetized and also need to be indented. Note that there is no extra space between the entries. You do not have to know how to manually form...

This is a presentation of how to face toughest interview questions. During most of the job interview, the interviewer is trying to find out your capabilities if the job. They want the client to explore why they want to be working here. They know that you want a job. But more specifically they need to know why you want to work in their firm and also your capabilities. So, you must be prepared to answer for this common question for most of the interviews. First of all you should understand why ...