Hacker's are always looking for new ways to exploit systems and exfiltrate passwords, even in hashed form. Sophisticated brute-force attacks powered by high-end GPUs can perform millions of password attempts per second. But Ubuntu and Debian users aren't completely helpless. There are ways to harden the hashed password to better defend against Hashcat attacks.
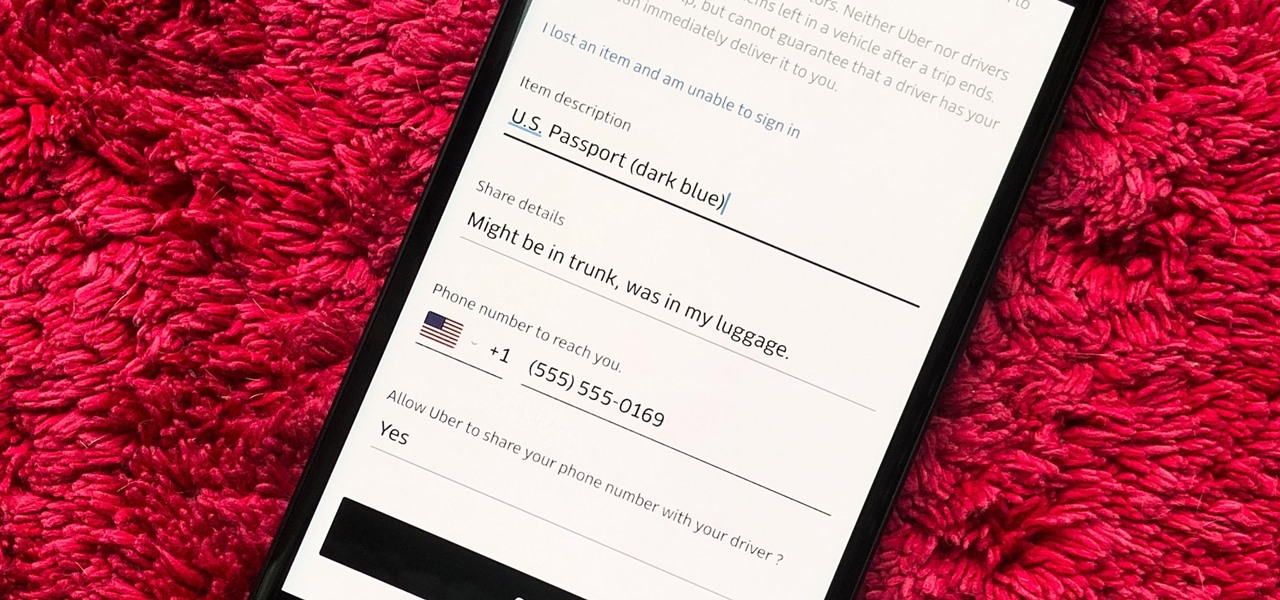
You would think that recovering your smartphone or another important item that you leave behind in an Uber ride would be a simple process, but it can actually be a pain in the ass. You have to find out how to report it to the driver, hope the driver is honest, pay a fee, and contact Uber directly if none of that works. But we're here to help make this process as easy as possible for you.

WhatsApp is the go-to messaging app for millions worldwide and its easy to see why. The app can be considered the Swiss Army Knife of texting thanks to numerous features like Group Chats and Status Stories, in addition to striking a great balance between ease of access and overall security.

Recently, Google's Messages app has become an important cog in the Android ecosystem. That's because, for the time being, it's one of the only texting apps which supports RCS Universal Profile for iMessage-style conversations. Even better, Google just gave it a highly sought-after feature: dark mode.
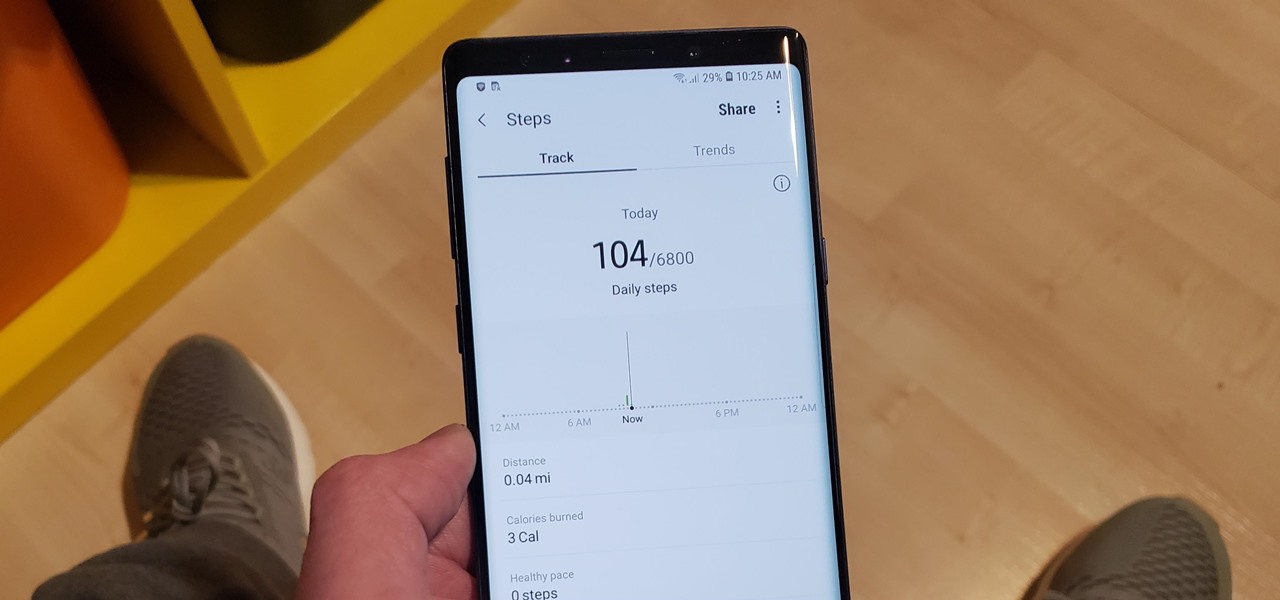
Once known as S Health, Samsung Health has become one of the most comprehensive health apps available for Android. In fact, we all can benefit from the features the app brings to the table — whether you're a marathon runner or a couch potato. If you're in the latter category, the app has a simple feature that can nudge you towards becoming more active.

So, you've lost your Apple TV remote. Maybe it's busted. What are you supposed to do now? You could go out and buy a new one, but they're expensive if you have a newer Apple TV with a Siri Remote, and wouldn't you rather spend that money on a movie? You might be without a working dedicated remote, but you likely have the next best thing already in your pocket.

A powered-off MacBook can be compromised in less than three minutes. With just a few commands, it's possible for a hacker to extract a target's password hash and crack it without their knowledge.

The Pixel 2 XL had what Google called a circular polarizer to ensure the screen would be visible from any orientation while wearing polarized sunglasses. They made a pretty big deal out of it at their 2017 event, but in 2018, there was no mention of whether or not this feature would return in the Pixel 3. It did.

Good news for beta testers — Apple released iOS 12.1 beta 4 to public testers Monday, Oct. 15. The update comes just hours after the company seeded beta 4 to developers and only six days after all beta user received iOS 12.1 beta 3.

Just six days after the release of dev beta 3, developers now have their hands on the fourth iOS 12.1 beta. While Apple has recently followed a lengthy and inconsistent release schedule with its beta software, the company seems to want to keep testers happy with 12.1 — beta 4 might have come less than the standard seven days after beta 3, but at least it's here quickly.

Apple released the third public beta for iOS 12.1 to software testers on Tuesday, Oct. 9, and there's not a whole lot to be excited about. The update came just hours after Apple released iOS 12.1 dev beta 3 to registered app developers, signaling a return to the traditional Tuesday release schedule for iOS betas. At least, for now.

Apple pushed out its newest beta, iOS 12.1 beta 3, to registered developers on Tuesday, Oct. 9, right at 11 a.m. PDT. The new update does not appear to offer any new features or changes, rather it seems to be simply a routine upgrade. Developers should expect simple bug fixes and security patches, instead of the feature-ridden update seen last week.

One of the more compelling human interest stories of the summer has been the plight of the Thai Wild Boars soccer team, who were trapped in a cave for weeks.

When you want to post a breathtaking landscape or picture-perfect portrait that you just took with your DSLR camera to Instagram, Facebook, or some other social platform, there's an easy way to do so — even if you don't have a computer handy, which is typical when you're out and about.

You've protected your Ubuntu system from physical attacks, annoyed network hackers, and sandboxed potentially malicious applications. Great! Now, the next logical steps to locking down your OS include thoroughly auditing Ubuntu for weak points, using antivirus software that respects your privacy, and monitoring system logs like a boss.

Don't think because your MacBook is using FileVault disk encryption your device is secure or immune to hackers. Here's how to find out if that FileVault password is strong enough to withstand an attack from a motivated attacker.

It's possible to stream a MacBook's entire computer screen without using Apple's Screen Sharing application and without opening any ports on the target device. A hacker with low user privileges on the backdoored Mac may be able to view a victim's every move in real time no matter where they are.

After the spectacular rise and fall (and rebirth) of Glass, Google is taking another run at augmented reality smartglasses.

The conversation of which operating system is most secure, macOS vs. Windows, is an ongoing debate. Most will say macOS is more secure, but I'd like to weigh in by showing how to backdoor a MacBook in less than two minutes and maintain a persistent shell using tools already built into macOS.

We know Android 9.0 will have the formal designation of Pie, following Google's age-old tradition of naming their OS after items you'd normally find on a dessert menu. And thanks to a slew of new features that centers around your overall security, P could also stand for Privacy.

Continuing with its new paradigm of using augmented reality to cover the news, The New York Times has published a feature story that takes a peek into the late David Bowie's eclectic wardrobe of on-stage outfits.

While much of the technical specifications of the Magic Leap One: Creator Edition still remain a mystery, some clues to its internals are hidden among the guides in the now freely-accessible Creator Portal.

Introduced on the iPhone 6s, 3D Touch is just about the closest thing to a "right-click" that we have on iOS. Apple and app developers utilize this feature to give us helpful options that might otherwise clutter the overall app experience, as well as opportunities to "peek" into an action without committing to it. Safari on iPhone is no exception.

Although expected to be only a modest upgrade over the S8, we can't help but be excited about the Galaxy S9's unveiling late next month. Among the many rumors and questions we're looking to see addressed, one of the biggest queries we have is, of course, with the price tag. We might not have to wait a month for the goods, however, thanks to a new pricing announcement out of South Korea.

It seems fitting that Time magazine's first augmented reality cover is an issue guest edited by Bill Gates, since the company he founded is currently leading the AR charge via the HoloLens.

Attention Android users — the famously iPhone-only HQ Trivia is here! If you've been waiting for the worldwide sensation to come to your smartphone, now's your chance to dive into the excitement.

SSH is a powerful tool with more uses than simply logging into a server. This protocol, which stands for Secure Shell, provides X11 forwarding, port forwarding, secure file transfer, and more. Using SSH port forwarding on a compromised host with access to a restricted network can allow an attacker to access hosts within the restricted network or pivot into the network.

Threats to your privacy and security are everywhere, so protecting your data should be the highest priority for anyone with a smartphone. However, one threat many people overlook is the company who supplies the operating system your Android phone runs — Google.

JavaScript is one of the most common languages used on the web. It can automate and animate website components, manage website content, and carry out many other useful functions from within a webpage. The scripting language also has many functions which can be used for malicious purposes, including stealing a user's cookies containing passwords and other information.

Razer took to the stage this month to unveil their new flagship phone, fittingly called the Razer Phone. The device is targeted at gamers, but has a list of specs that make it an intriguing daily driver for any user. Its headlining feature is an 120 Hz IGZO display, the first of its kind in a flagship smartphone released in the US. Tonight, Razer officially opened up orders for the new phone on their website.

In our previous article, we learned how to take advantage of a feature, Dynamic Data Exchange (DDE), to run malicious code when an MS Word document is opened. Because Microsoft built DDE into all of its Office products as a way to transfer data one time or continuously between applications, we can do the same thing in Excel to create a spreadsheet that runs malicious code when opened. The best part is, it will do so without requiring macros to be enabled.

Barrow's article on Pupy made me wish for a RAT that could target an OS frequently used by gatekeepers at startups, tech companies, and creative firms: macOS. Once run, a RAT can do severe damage by dumping a user's stored credentials for many accounts. The best loot lives in the Chrome Password cache, and EvilOSX, an OS X RAT, infiltrates macOS and dumps these credentials.

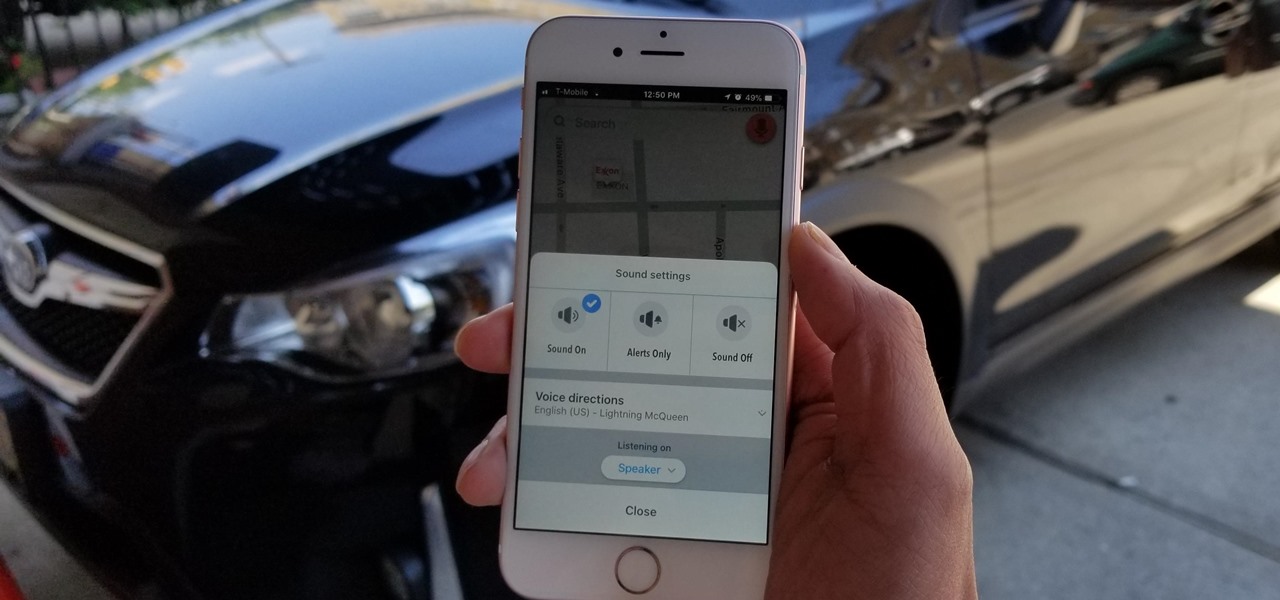
If you've been looking for an alternative to Google Maps, look no further than Waze. In addition to benefits like crowd-sourced traffic data, police trap locations, and road work avoidance, the app even lets you personalize the voices used for navigation and directions.

As augmented reality becomes more and more integrated into the mainstream, people have been wondering the future of AR is going to look like. Jay Samit has a pretty clear idea.

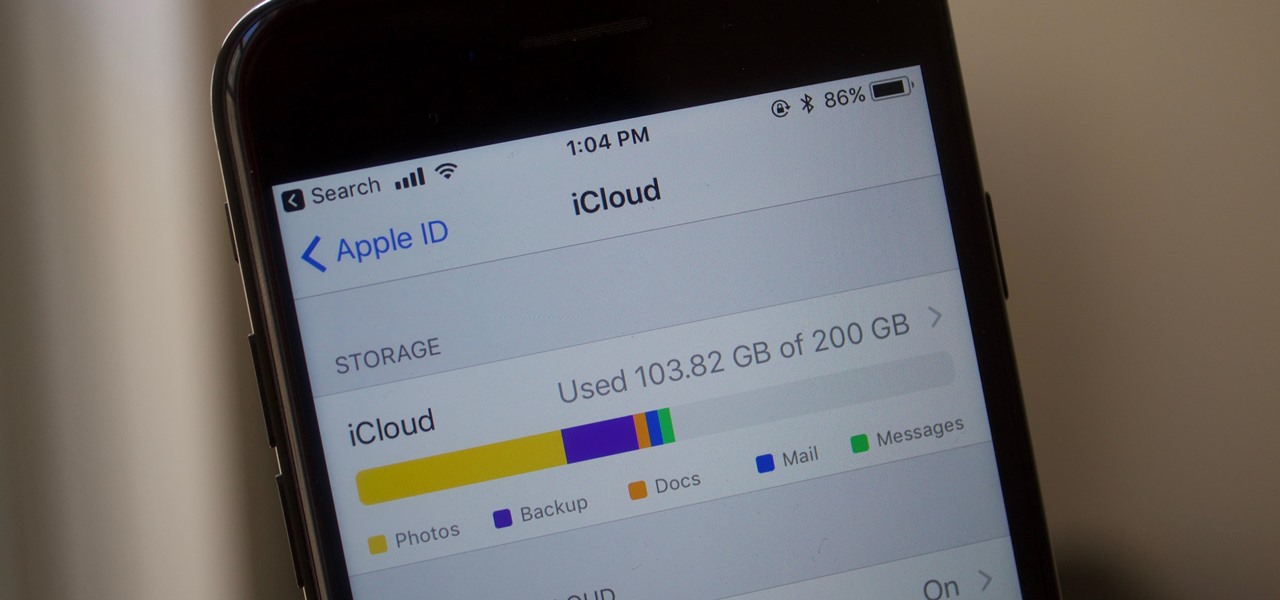
iCloud can occasionally be the worst part of being an Apple user. It's useful for backing up your information, however, sometimes the problems that stem from Apple's cloud service are so tremendously frustrating they almost seem intentional. Well, buckle in, because it's possible there may be a widespread login issue.

Firefox Focus is Mozilla's effort to make your internet experience a little more secure. Originally released in November 2016 for iOS, Focus blocks internet trackers, search history, anything that gets in the way of a clean, private browsing experience.

ASUS is gearing up to move its augmented and virtual reality departments into an independent startup named Glamorfy, according to a recent report from tech news site Fudzilla.

WinFuture, a German tech-news site, has leaked a spec sheet for the upcoming Samsung Galaxy S8 and S8 Plus. We previously covered all speculation and leaks in our rumor roundup, but thanks to Roland Quandt, we now have a very clear look at what to expect from Samsung's latest flagship release.

At a global security conference in Munich, philanthropist and businessman Bill Gates spoke about the next pandemic and a dire lack of global readiness. Here's how his statement could come true—and how to be ready when it does.

The force is strong with this project. Colin Furze is a British YouTuber who is a self-proclaimed "garage inventor and video maker." In a recent collaboration with eBay, Furze created the "ultimate Star Wars project," an 18-feet-tall playhouse version of the AT-ACT from Rogue One: A Star Wars Story.