If your company has already released some popular and addictive game and you're thinking about creation a sequel, this article is just what you need. We gathered the main tips and advices that will be useful for the building a strategy and a sequel itself. Check out the following instructions and recommendations that can lend you a hand in making a sequel for your game.

Whether you are vegan, lactose-intolerant, or cooking for someone who is, standing before the non-dairy milk shelf in the grocery store can be daunting. Instead of playing it safe with the two most common milk alternatives—soy and almond—perhaps you should explore a few other choices that tend to be overlooked.

I mentioned in one of my earlier articles something about ghost hackers, and very shortly stated a thing or two of what they do.
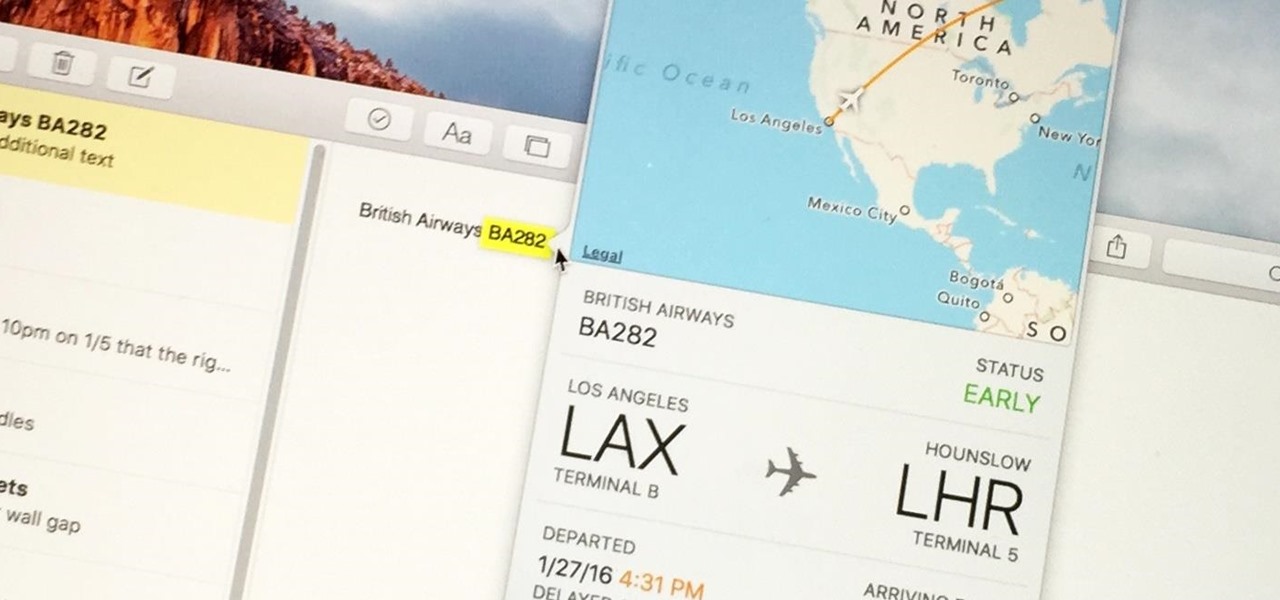
Turns out, you no longer need third-party flight tracking apps to get information on yours or others' flights—your iPhone and Mac can now give you flight details right from your Mail, Notes, and Messages apps.

Welcome back! In the last training session we covered how to write and execute scripts. But today we'll be getting back to the code!

Microsoft did a wonderful thing in 2015: for the first time, it was offering a free upgrade to Windows 10 for all current Windows 7 and 8.1 users. And, if you were lucky, the upgrade process was relatively simple and painless. There were, however, some questions after the everything was said and done.

Welcome back, my greenhorn hackers! Over the years, I have written many articles here on Null Byte chronicling the many the hacks of the NSA, including the recent hack of the Juniper Networks VPN. (By the way, my speculation in that article has proven to be correct. The NSA did embed a backdoor on those devices.)

We all know them, and many of us despize them. And some might support them, regardless many have different opinions.

Hello, Null Byte! Mkilic here. I doubt anyone knows I even exist on Null Byte, so hopefully this post will allow me to become more involved in the community and also help me learn even more.

After seeing the title of this post from me, you might be thinking, "Why did The Joker made another post on a topic on which we already have a nice sticky post?"

It should come as no surprise that, according to Details Magazine, nearly half of all people who make New Year's resolutions pledge to lose weight, eat healthier, and/or get fit. There are innumerable companies out there that are ready and willing to take advantage of this momentum: from those hocking "magic bullet" pills that will increase your energy or reduce your belly fat to the myriad shake- and juice-based diets that put you at a near-starvation calorie input—and will probably have you...

You might be familiar with the use of zucchini blossoms in cooking and maybe even know how to make herbal simple syrups. But if you really want to show off as someone who knows how to use flowering plants in food, try adding some flower water to your cooking/baking repertoire.

Switching your favorite facial cleanser isn't an easy choice. Since everyone's skin type can range from dry, to oily, to some complicated combination of both... well, let's just say that the conventional wisdom is to stick to what you know works.
Hello Strangers, This is my first article for null-byte and its about staying anonymous on the Internet. But the question is why would you want to stay anonymous online?

to stay secure, you dont just need Tor, and a VPN. You need good browsing habits. What are Browsing Habits You Ask?

Hey there, reader! In this tutorial we are going to explain how values are stored in variables as either signed or unsigned. Try to not get lost!

During my time living in dorm rooms and small apartments, I would find myself in need of many different appliances—a food processor for making hummus, a blender for vegetable smoothies, or even a mortar and pestle for muddling mojito-bound mint leaves. Luckily, there was one tiny, inconspicuous tool that solved all of these problems: the coffee grinder.

The first time I encountered a deviled egg, the name freaked me out. Why was it called a deviled egg? Was it the spawn of some demonic chicken? If I ate it, would my soul be at risk?

You want to become anonymous, and dont want your IP to be logged on websites? Well read along here. Continuing This Series:

Welcome back! In the last iteration of how to train your python, we talked about functions, and we even made our own! We're going to move on to more types of data arrays (much like lists) in today's discussion.

Elle, who grew up on the East Coast, would have described the weather as "brisk." I, a Southern California native, called it "deathly cold." As we waited for the water to boil over our campfire, despair began to creep in.

Nothing signals the end of fall and the start of winter like hot, seasonal drinks. And while pumpkin spice lattes may be the flavor of the day, and eggnog the Christmas favorite, one seasonal drink stands apart in my eyes: mulled cider.

Vegetables are perhaps the most important part of our diets, but often times they're an absolute pain to prepare. Cleaning every fleck of dirt off of dozens of leafy greens takes ages, and eliminating the more fibrous parts of certain veggies can be extremely tedious.

Hello everybody Joe here. Today I will be demonstrating how you can find XSS vulnerabilities in a website and what you can do with them

Well, first things firsts, it's been awhile! I'm sorry the series has been dead for a little bit, but I recently hit some personal relationship issues and needed to take some time to think. But, now that it's all said and done, the dust can settle and we can start training again!

As the days get shorter and the weather cools down, I prepare to "hibernate." I add piles of blankets to my bed, wrap myself in layers of flannel, and—most importantly—eat as if I'm storing energy for winter.

Fall is the time for comfort foods—and what is more comforting than crusty bread slathered in melted cheese? Owning a fondue pot is both convenient and wonderful, but not all of us have the luxury of space for nonessential kitchen appliances. However, there are plenty of ways to make an absolutely delicious, lump-free fondue without the traditional equipment.

Reddit, the self-proclaimed "front page of the internet," continues to take a big bite of my free time each and every day, as well as millions of its other users'. The clicking and scrolling through page after page never gets old, but you could speed things up with a few browser extensions and double your Reddit knowledge in half the time. Here are my favorite extensions you can try out for the Chrome, Firefox, and Safari web browsers.

Dumplings have been around for centuries in various forms; spätzle, as well as chicken and dumplings, are dough-y dumplings with no filling, whereas Russian pierogis and Chinese jiaozi are dumplings that contain meat, vegetables, or both.

Welcome back, my tenderfoot hackers! Recently, Microsoft released a new patch (September 8, 2015) to close another vulnerability in their Windows Vista, 7, 8, and 8.1 operating systems. The vulnerability in question (MS15-100) enabled an attacker to gain remote access to any of these systems using a well-crafted Media Center link (MCL) file.

Welcome back, my nascent hackers! Although my favorite TV show, Mr. Robot, had completed its first season already, I have not completed demonstrating the hacks that Elliot used in the show. (By the way, I can't wait for season 2!)

Last year, the Washington Post's Ashley Halsey wrote an article on what really happens to your luggage at airports. In it, they unwittingly published a photo of the master keys the TSA uses for TSA-approved baggage locks. Now, thanks to that picture and a French lock-picking enthusiast, anyone with a 3D printer can make their own master keys to unlock any TSA-recognized locks.

Welcome back, my fledgling hackers! In this series, I am trying to develop your knowledge of digital forensics, which is valuable whether you're choosing a career in it or just want to know how your hacker activity can be traced. Few professional digital forensic investigators have a hacking background, but the best ones do.

Cortana, Microsoft's voice-activated personal assistant, originally launch on Windows Phone, but is now built directly into Windows 10 complete with "Hey Cortana" voice search (take that, Apple). It can help you locate files, set up reminders, control music.

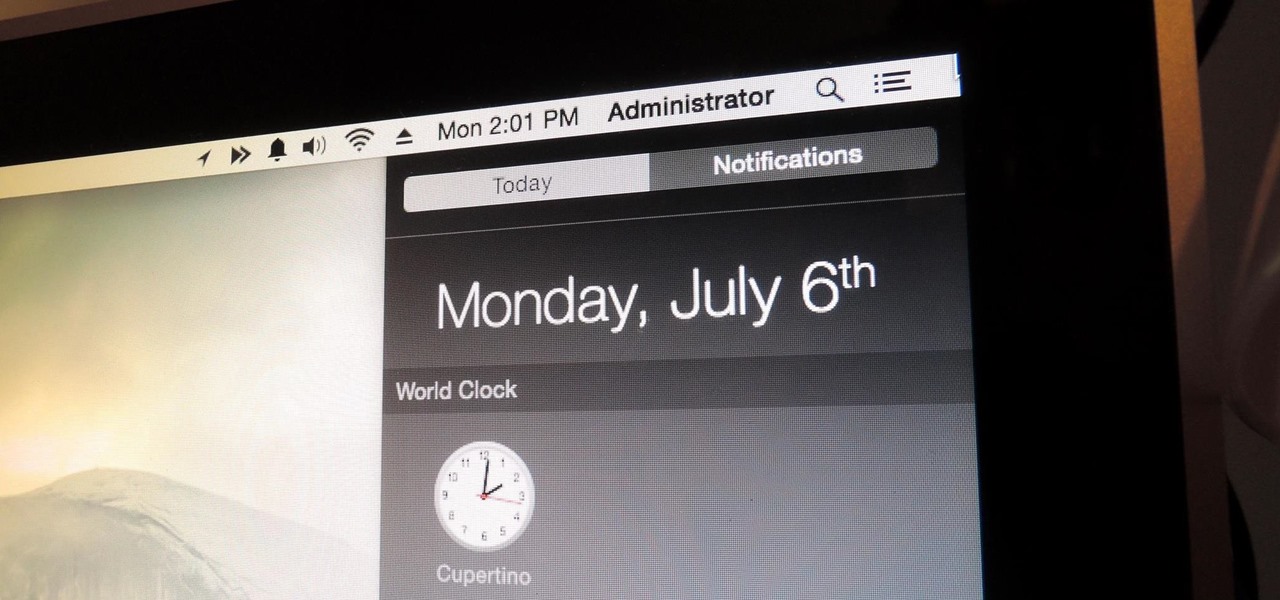
You can check stock quotes, make quick calculations, see the weather forecast, get reminders, and view upcoming calendar events all from the Notification Center on your Mac. But if that's all your using it for, you're just barely scratching the surface.

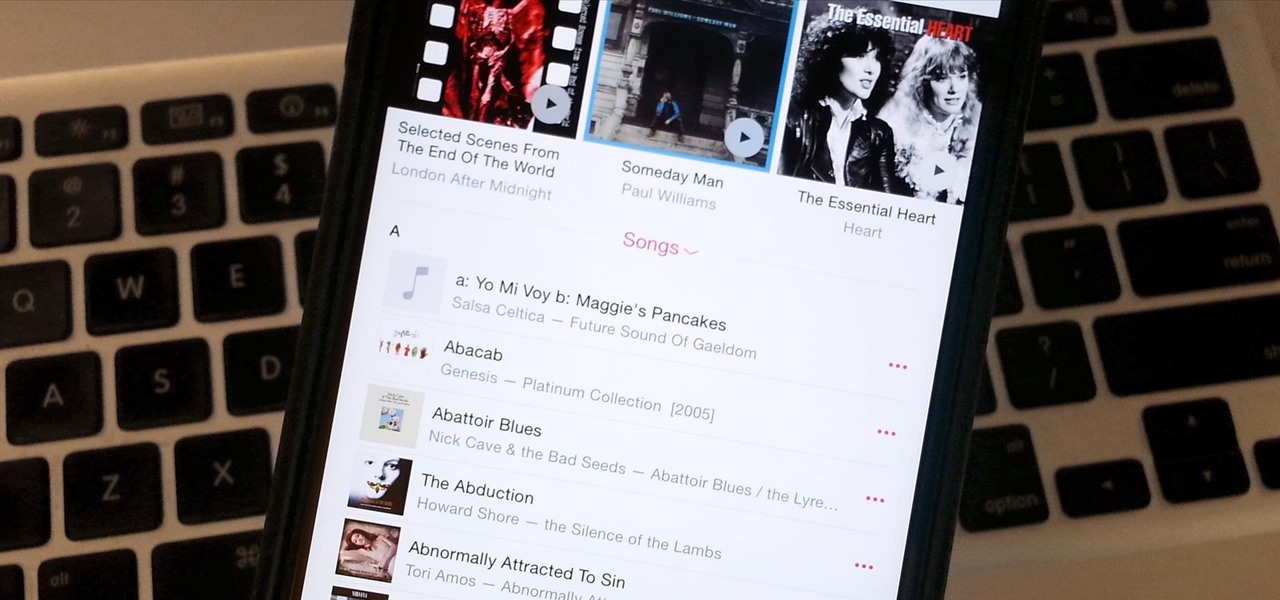
If you updated to iOS 8.4 already to try out the new Apple Music service, there's one important change you need to know about—there's no longer a "Shuffle" option for all songs in your library.

When it comes to smartphones, the biggest complaint voiced by most users is battery life. Sure, it's unrealistic to expect your Android device to run for weeks without a recharge, but many folks struggle to even make it through the day without having to top off their battery.

Notes on iOS has never been a particularly great app due to a lack of overall features compared to other note-taking apps like Evernote or Microsoft OneNote.

Amazon makes it exceptionally easy to purchase anything you want in just a few minutes. From textbooks for school to live ladybugs, its more surprising when you can't have something delivered to your doorstep in a few day's time.

Welcome back, my tenderfoot hackers! Have you ever wondered where the physical location of an IP address is? Maybe you want to know if that proxy server you are using is actually out of your local legal jurisdiction. Or, maybe you have the IP address of someone you are corresponding with and want to make certain they are where they say they are. Or, maybe you are a forensic investigator tracking down a suspect who wrote a threatening email or hacked someone's company.