
How To: Deal with your labor fears
Labor is probably the most feared of pregnancy’s "unknowns." Here's how to manage it. You Will Need


Labor is probably the most feared of pregnancy’s "unknowns." Here's how to manage it. You Will Need

The biceps tendon attaches the biceps muscle to the radius. Learn how to diagnose and treat a biceps tendon tear in this medical how-to video. Usually the area is painful, swollen and bruised.
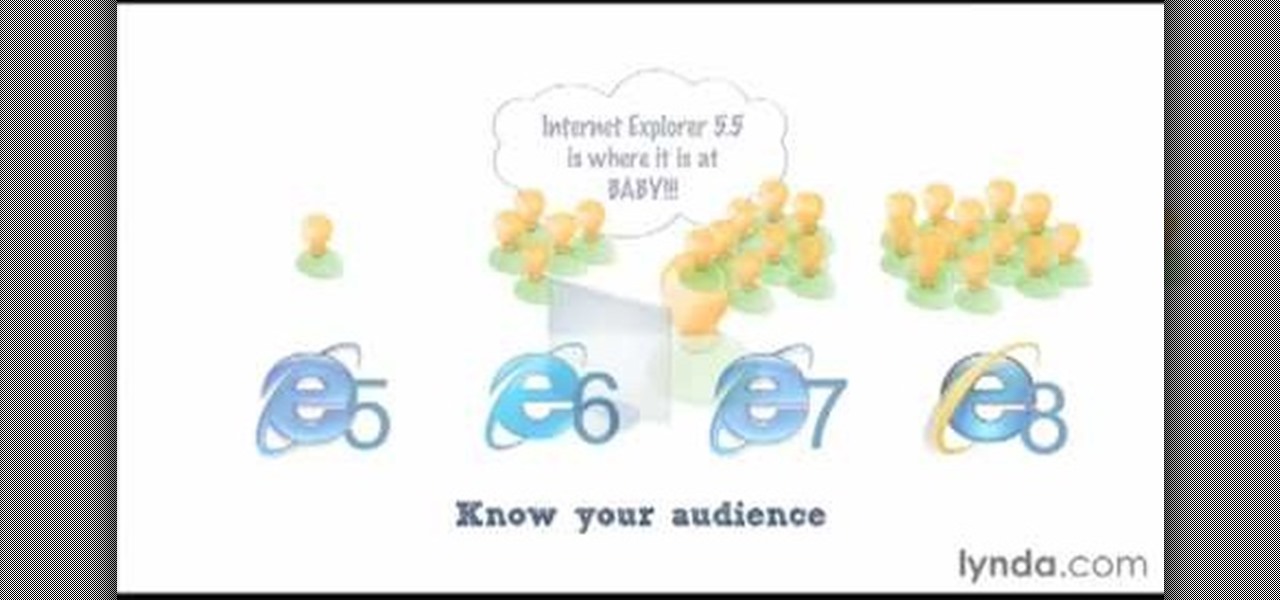
James Williamson for Lynda demonstrates designing for multiple browsers. The most frustrating aspects of web design is constantly dealing with the settle and some times not so settle differences in browser rendering. While they moved to a standard spaced, CSS control presentations has made life infinitely easier for web designs. Dealing with bad browser behavior is one of most unfortunate side effects. All browsers render our pages same because each browser reads and renders the HTML and CSS ...

If I were to lose access to the entire internet for the rest of my life, one of the websites I would miss the most would have to be Wikipedia. Wikipedia has ended countless arguments, informed me of how old and single some of my favorite actresses are, and helped me brush up on thousands of historical topics.
Apple's upcoming iPhone update, iOS 13.3, doesn't add as many new features as iOS 13.1 or 13.2, but there's one under-the-radar change you'll love if you use Apple News on a daily basis.

First of all, I would like to apologize for a week long absents for the tutorials of this newly series, Raspberry Pi. But obviously I'm back and I present all you guys a article on turning your Raspberry Pi into a hacking platform. I'm gonna use the platform Kali Linux for the Raspberry Pi. I should note that I'm not gonna go into detail on how to install Kali Linux since OTW already has done a tutorial on how to turn your Raspberry Pi into a Hacking Pi. The point of this particular tutorial ...

The first White Hat Award for Technical Excellence tutorial contest ended last night at midnight! We had many excellent articles submitted, once again re-affirming what an incredible community we have here at Null Byte! We had quite a flurry of great articles in the last few days. Thanks to all of you who submitted such high quality material to our community. Your efforts are appreciated and you have the undying gratitude of our community. We will not forget your efforts. I'll be reading and ...
Procrastination is an ugly beast. At first, it seems so innocent to spend five minutes checking Reddit or Twitter. You'll get started on work right after. Next thing you know, it's 1 a.m. and that paper is due in seven hours. Before you start another YouTube video, know you don't have to be like Spongebob. You can be like me, taking control of your productivity with the right app.

Of all the new features and changes on iOS 16.5, the Apple News app has the most, and there are a few big ones that will change the way you read stories. Some updates even affect Apple News on iPadOS 16.5; the most significant ones apply to both free users and Apple News+ subscribers.

Apple's macOS operating system is just as vulnerable to attacks as any Windows 10 computer or Android smartphone. Hacker's can embed backdoors, evade antivirus with simple commands, and utilize USB flash drives to completely compromise a MacBook. In this always-updated guide, we'll outline dozens of macOS-specific attacks penetration testers should know about.

So many times, you turn on your computer, you open your front door, or you sit down on the couch to watch some well-earned TV, when you think -- Gosh! If only I could do this or this, life could be so much easier! And then, if you were a boring person, you would slouch even further down on the couch and continue to watch those reruns of The Sopranos.

With the whirlwind of noise surrounding the COVID-19 virus sweeping the nation, it's not hard to default to panic mode. One of the best ways to avoid panicking, however, is to follow trusted sources of information and avoid all of the opinions and trolls that don't reflect reality.

Hello everyone! I hope you are having a great day so far. Today, instead of caring about networks we are going to talk about subnetting based on host requirements as promised in my first article about subnetting. Just like in the previous articles we will jump right into the examples because that's the best way to learn.

I have been on Null Byte for a long time, a very long time and. I havent always had an account here, ive like many of you also have, been looking and decided to make a profile to contribute.

Since I first announced the new Null Byte recognition for excellence a few weeks ago, several of you have written me asking, "How can I study for this certification exam, and what material will be covered on the exam?" Now I have an answer for you. The White Hat Hacker Associate (CWA) will cover 14 domains or areas. Everything you need to know is here on Null Byte. There will be no questions that are not covered here on this site, guaranteed.

Audiobooks are great because they require little-to-no effort on your behalf. When driving in traffic, why not listen to George R.R. Martin's lengthy A Feast for Crows instead of repetitive, commercial-laden radio? Maybe it harks back to prepubescent bedtime readings, but having things read to me is a very satisfying experience.

"You can never know too much" is a saying you hear all the time. Funny thing is, I have no idea where it originated, and neither do most of the people who continually say it. Nevertheless, it's a statement that very few would argue with.
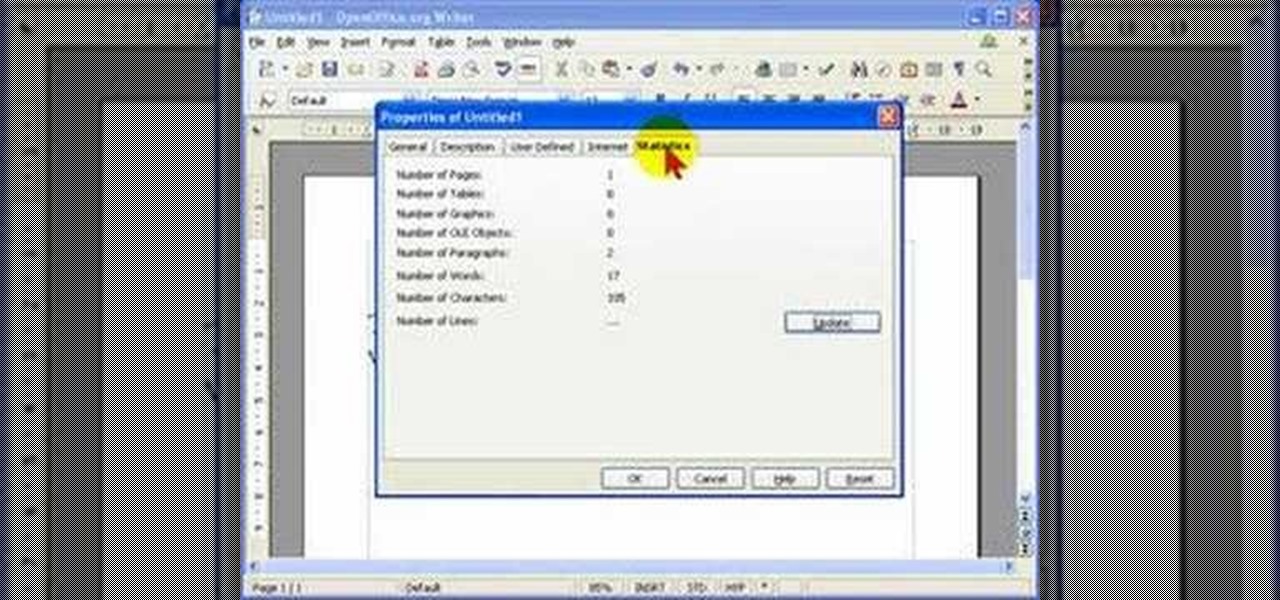
When creating word processed documents, there are often times when it is important that you know exactly how many words you have written - for example, student writing their dissertation, and journalists writing articles.

The conversation of which operating system is most secure, macOS vs. Windows, is an ongoing debate. Most will say macOS is more secure, but I'd like to weigh in by showing how to backdoor a MacBook in less than two minutes and maintain a persistent shell using tools already built into macOS.
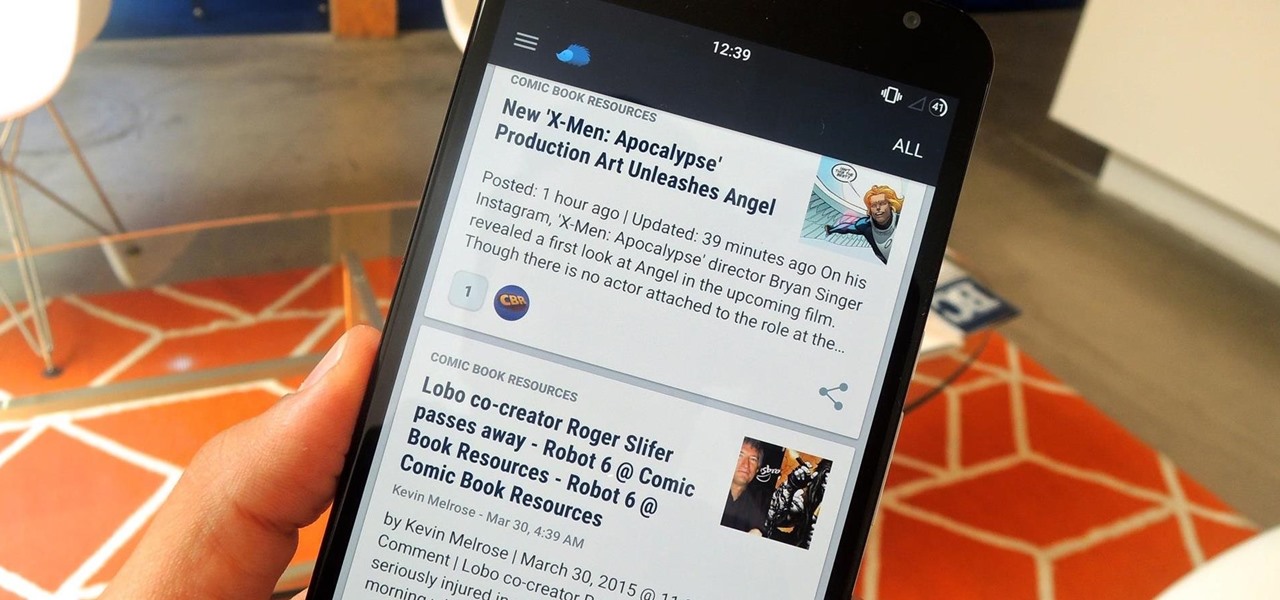
Serving as the primary tool of distribution for many websites, social media is how most of us catch up what's going on around the world. While there is a bunch of clickbait going around on Facebook and Twitter, there are plenty of genuinely interesting articles being shared.
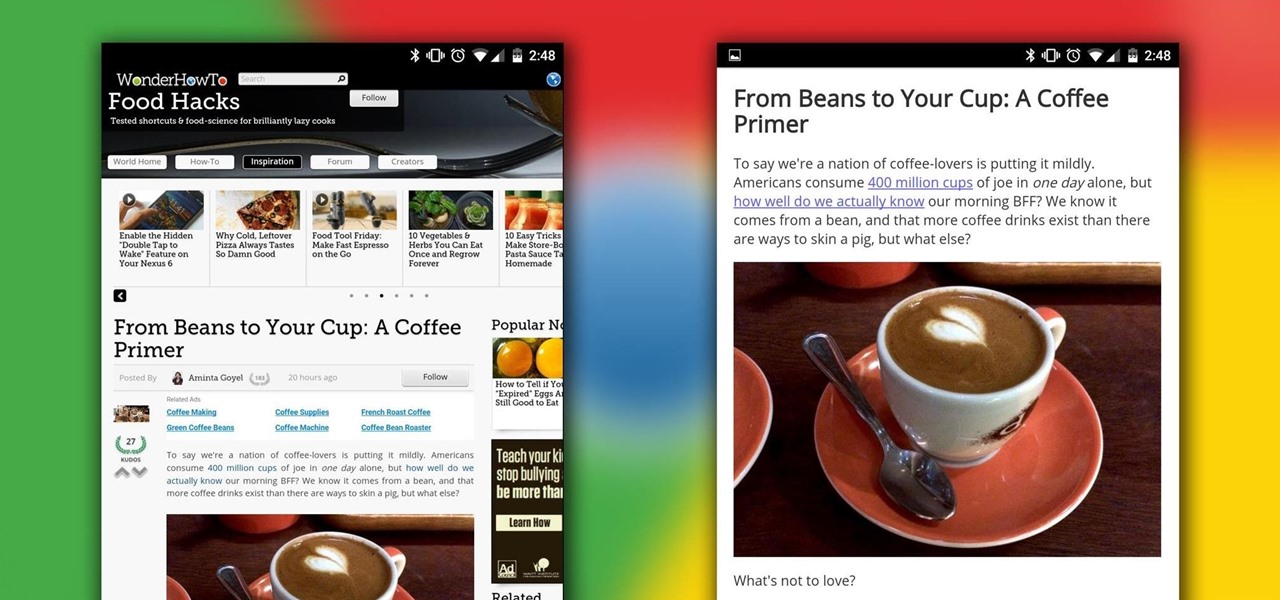
Reading articles on an Android phone using Chrome Browser can be a little bit of a battle; it often times requires adjusting the page to fit the screen in order to make it easier to read and scroll through. I sometimes lose this struggle and give up trying to read on my device, saving the article for a later time when I'm on my laptop.

In this Quick Clip, I'll be showing you how a supercooled soda is transformed into a slushy "slurpee" in under 4 seconds. I was inspired to do this little soda trick by The Super Effect's video on YouTube from a few years ago.

There are thousands of articles published every day about smartphones, tablets, eReaders, and any other kind of gadgets you can think of. The problem is that most people only really care about news related to the devices they actually own. So how do you filter out all of the stuff you don't care about? That's what Drippler does. It pulls news, tips, and app reviews and recommendations from all over the web and puts them all in one place, but only for the devices you want to read about. You te...

The Google Feed is a great source for relevant news articles from your search history, package delivery updates, and much more. Now known as the "Discover" page, many Android users turn to this useful menu on a daily basis. However, as Google recently pointed out, the all-white theme is not ideal for battery life, nor is it easy on the eyes at night.

Null Byte users have often requested video content, but the question has always been what format would best serve our community. This week, we partnered with Null Space Labs, a hackerspace in Los Angeles, to test the waters by hosting a series of talks on ethical hacking for students in Pasadena Computer Science Club. We invited students and Null Byte writers to deliver talks on Wi-Fi hacking, MITM attacks, and rogue devices like the USB Rubber Ducky.

Step 1: What Exploit Development Is and Why Should I Be Interested on About This Topic

Why I split it into two articles: I love images and I'm sure lots of us do. I decided to put in a lot of images as examples rather than have paragraph upon paragraph of boring text. Also, I don't think any of us like overly long articles; but if you think it's better to have it all in one article, let me know

We've all had to write an essay or research paper at some point, and undoubtedly the hardest part about it is always the citation, right? If you ask me, it's a huge pain in the arse. Even more so if you're gathering your facts from a huge variety of sources.

Welcome back, my greenhorn hackers! Several of you have you have emailed me asking whether it's possible to install a keylogger on a victim’s computer using Metasploit. The answer is a resounding "YES"!

These days, news papers, online editorials and magazines are filled with news on Iran and Syria. Of course, that is expected, as such sources need to stay current to stay in the game. My concern is that most of these articles talk about what to do about these situations.

A low tunnel is a kind of mini-greenhouse for your garden. Growing vegetables in a low tunnel requires proper ventilation. In this tutorial, you'll learn how to provide the right ventilation for your low tunnel, keeping your plants happy and healthy.

Garlic is great for spicing up your meals (and keeping vampires away!) and fall is a great time to grow it. In this video tutorial, you'll learn how to grow garlic in your garden. Get some garlic bulbs from a seed catalog, nursery or organic grower, and you'll soon have a garlic crop to be proud of.

Come the fall, your garden is probably going to be looking pretty spare. But it doesn't have to be that way. There are vegetables that will thrive in the fall. In this Growing Wisdom gardening tutorial, you'll learn how to grow vegetables in the cooler months.

Autumn leaves may be beautiful, but they can also be incredibly annoying as they pile up around your garden. But there are things you can do with autumn leaves, like mulching them, composting them and turning them into a living fence. In this episode of Growing Wisdom, Dave Epstein walks you through how to make a leaf fence.

With iOS 17, Apple News integrates more deeply with Apple Podcasts and Apple Stocks and has become a bit more fun thanks to new crossword puzzles. But that's not all that appears in the updated News app.

There's a growing sentiment around the web that when it comes to Android, stock is best. Many people prefer the clean look of Google's vision for Android, but manufacturers like LG will add features and themes on top of this base to differentiate themselves from the pack. But these OEM skins, as they're called, aren't always as overbearing as you might think.

Welcome back, my greenhorn hackers, and happy New Year! Now that your heads have recovered from your New Year's Eve regaling, I'd like to grab your attention for just a moment to preview 2015 here at Null Byte. I hope you will add your comments as to what you would like to see, and I'll try to honor as many requests as I can.
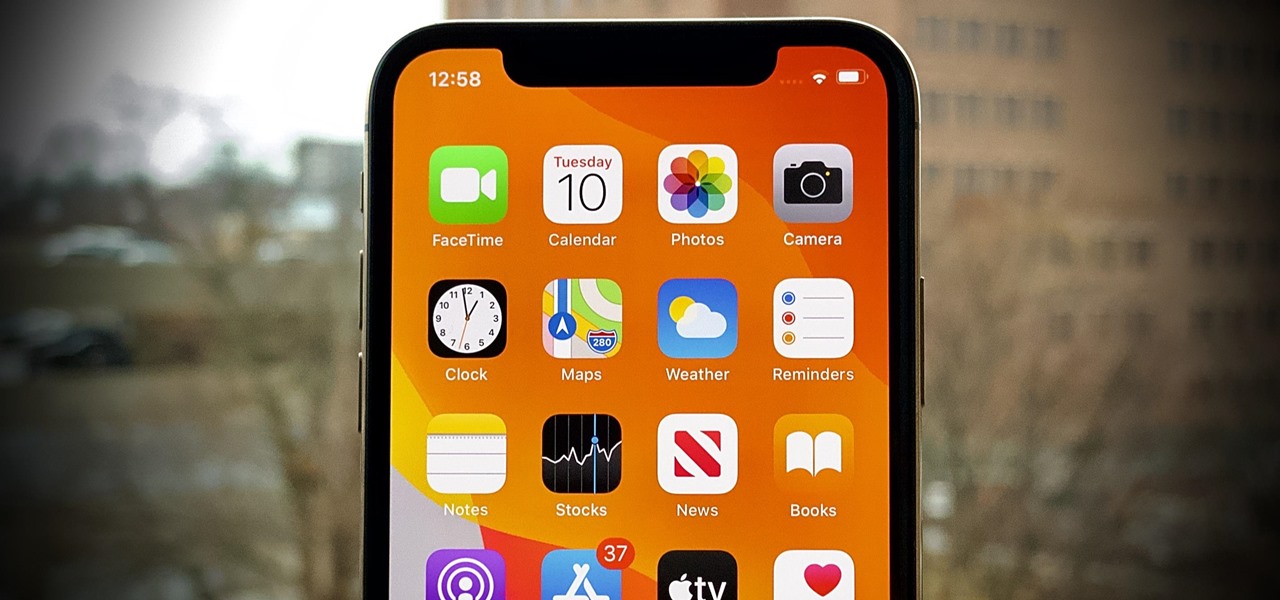
Apple seeded the official version of iOS 13 to compatible iPhones on Sept. 19. Since then, we've seen two major updates — iOS 13.1, which, by our count, introduced 22 new features, and iOS 13.2, which also added 22 new features. Today, Dec. 10, Apple introduced the third major update: iOS 13.3.
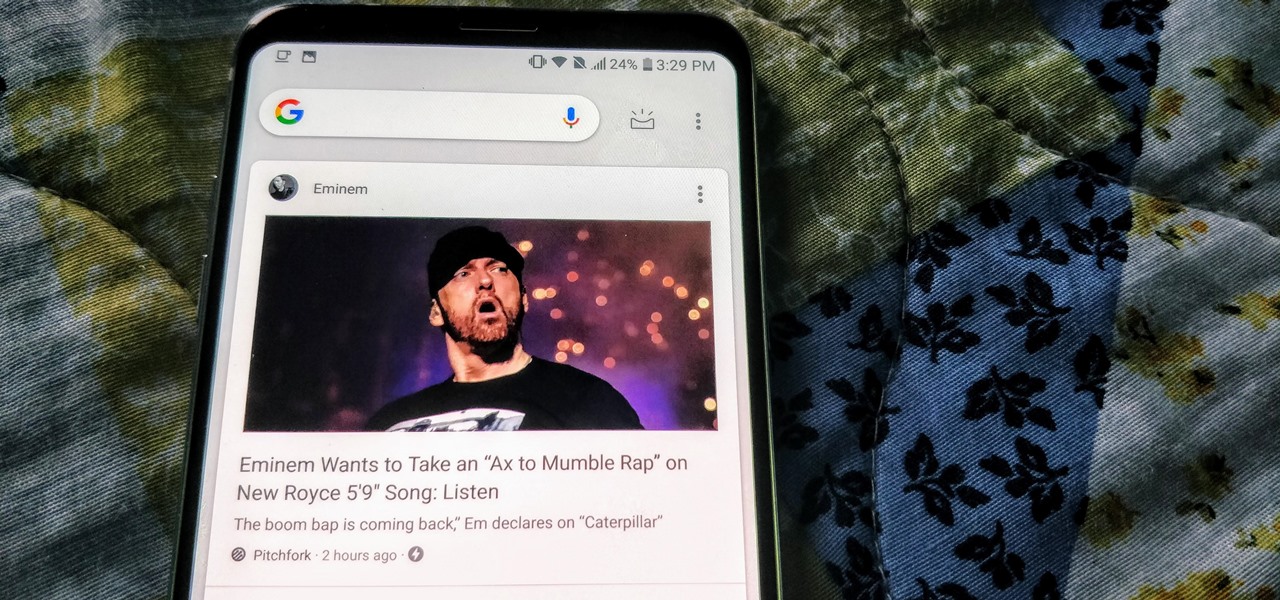
One of the better additions in the stock Android launcher is the Google Now page. Residing to the left of the home screen, this page presents a host of information based on the user's interests, which Google bases on analyzed data. Recently, the Google Now page design received a makeover which Nova Launcher users can now enjoy.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!