Many new parents will tell you how hard it is to name a baby. Some have stories of how they knew what the name of their child would be from before conception, only to change their mind when they were born. Sometimes new babies can go weeks without a name since there is an endless selection to choose from.

When the "Just another day in the office at Magic Leap" video was released last year, it was called a mind-blowing, stunning, and breathtaking take on mixed reality gaming. It was a great presentation of what the technology could be, but not for a second did I think it was anything other than a concept video, and I'm not the only one who thought that. This was a goal to reach for mixed reality, not the reality.

GitHub is an extremely popular site that allows developers to store source code and interact with other users about their projects. Anyone can download public, open-source files on GitHub manually or with Git, and anyone can fork off someone's project to expand or improve it into its own project. It's a really great site for programmers, developers, and even inspiring hackers.
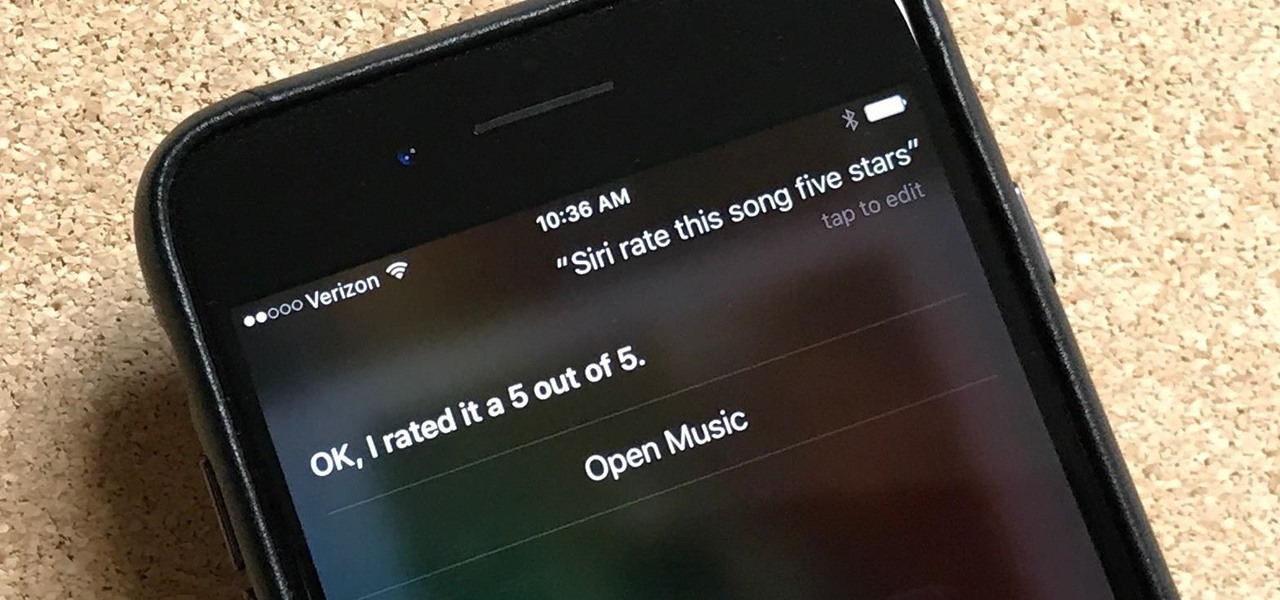
Can't figure out how to give songs star ratings anymore in your iPhone's Music app? That's because Apple removed the ability to do so from the new iOS 10 update, just as I expected they would. It's still possible to rate songs, it's just very irritating.

The new iOS 10 won't be released to the public until September 13 via an OTA update, but the Gold Master edition is available right now. Essentially, it's the same version that Apple will release on the 13th, but only for developers so they can get their apps up to snuff before everyone updates. Users on the iOS 10 public beta will not be getting this GM update.
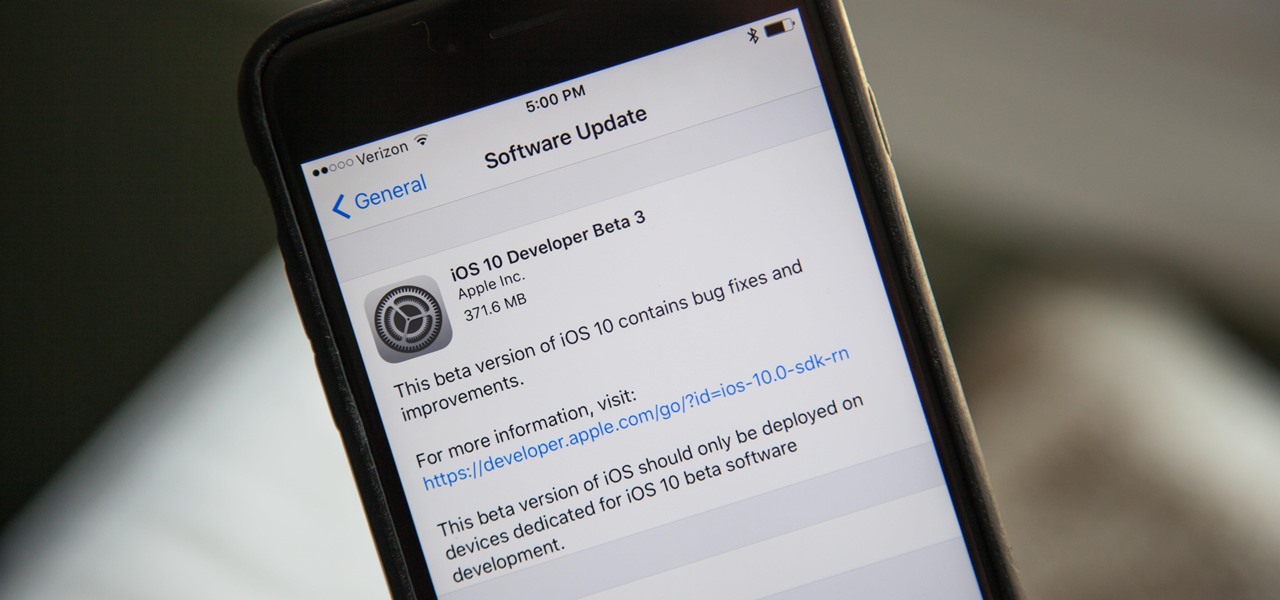
With the next iPhone release around the corner, Apple is hard at work getting iOS 10 squared away. On Monday, July 18, they issued the third beta of iOS 10 to developers, which should be released within a few days to those using the iOS 10 public beta.

I have came across a lot of members on the forum that didn't have a clear idea of what port forwarding is and what it does. So...Let's get started...

Virtual reality is all the rage these days, especially with devices like the Oculus Rift, Gear VR, and HTC Vive hitting shelves lately. But before any of those fancy, expensive headsets ever made it to the market, Google came up with a thrifty and inventive substitute in the form of Google Cardboard.

Out of nowhere, Google released a preview build of the upcoming Android N release back in March—a full two months early. As if that weren't enough excitement for one day, they topped themselves by following up that announcement with the debut of a new "Android Beta" program that allows users with eligible devices receive preview builds as a regular OTA update, meaning no losing data or manual installation.

In my last tutorial, I talked about creating a virus inside of a Word Document in the scenario of a mass-mailer attack. In this post, however, I'm going to be covering creating a fake image or screenshot with a meterpreter backdoor hidden inside to be used in a similar scenario. Step 1: Creating the Virus

Welcome back, my greenhorn hackers! As expected with Null Byte's dramatic growth over the last year, we have added many new aspiring hackers who are still lacking in the basics of networking. In addition, with the new "White Hat" certifications coming out shortly, the exam will require some basic networking skills and knowledge to pass.

Samy Kamkar, the security researcher known for the MySpace Worm and his combination lock cracking skills (using an online calculator), is back—and this time, he's after your credit cards!

OR rather How to make the Backdoor Persistent: Hello, my Cold and Merciless Hackers,

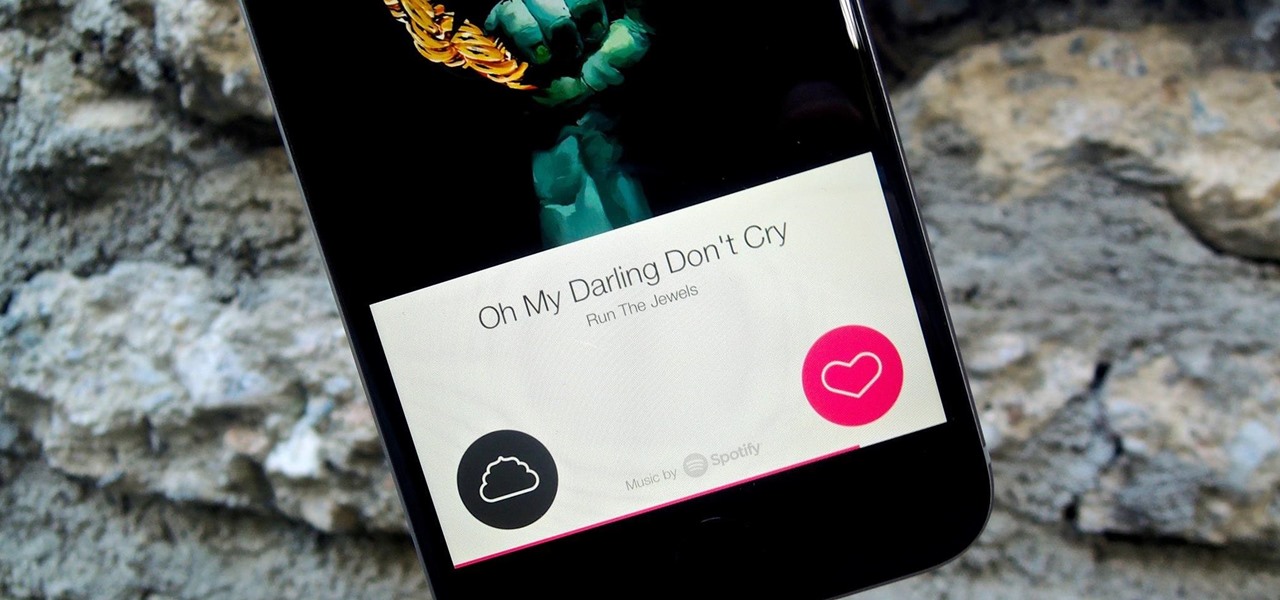
Everyone's a music aficionado these days. Whether you're having a party or on a road trip with friends, someone is always complaining about the music. There's no possible way to satisfy everyone, so instead of having your music drowned out by persistent nagging, turn Spotify into a democracy, allowing the consensus to pick what plays.

Seldom in recent history has a cyber security event caused so much media stir (maybe because it happened to a media company?) and international relations upheaval. Cyber security breaches seem to take place daily of major corporations, but the Sony hack seems to have captured the American imagination and, for that matter, the whole world's attention.

Coffee shops are a relaxing place to get work done on your laptop; there's free Wi-Fi, fresh coffee, and people generally leave you alone. Inevitably, those cups of coffee will go straight through you, resulting in a much-needed bathroom break. But while you're attending to your bodily functions, who's attending to your MacBook?

While the adoption of Apple's newest mobile operating system, iOS 8, was smoother than its predecessor, there were still a lot of bugs and features that needed ironed out. There were lost cellular signals, missing Camera Rolls, a confusing iCloud Drive, and no functioning Apple Pay yet, among other things. Now it's just over a month later from its first release to the public and things are finally looking pretty good.

The biggest hurdle faced when text messaging (besides more convincing lies) is accurately communicating our emotion and tone. Anything we say can be interpreted in various subjective ways by the recipient, and that's why we have emoji—to illustrate what we actually want to say.

It was a chilly but otherwise beautiful night at YouTube Spaces LA—food trucks, ping pong, a photo booth, and the chance to view film school projects created completely with Glass. About a year ago, the Glass Creative Partnership was formed to explore how Glass could be used in filmmaking, with partnerships spanning from the American Film Institute to CalArts and UCLA. On July 16, 2014, the products of that partnership were screened under the Southern California night sky. Three films were sh...

Whether you're a celebrity or someone with something to hide, Facebook allows you to keep your "friends list" private so you can protect the identities of your Facebook friends. But it only kind of protects them.

Currently in its alpha stage, Facebook has pushed forward a redesigned mobile app for Android users that provides a flat user interface and rearranged navigation tools.

I love cryptography. It is like a great gigantic puzzle for me to solve. However, it is more important than that. It is also how we keep secrets safe. Not just sorta safe either, but really safe.

Welcome back, my novice hackers! I've written a couple of articles on reconnaissance and its importance, and as I've said before, a good hacker will spend 3 to 4 more times doing reconnaissance than actually exploiting the system. If your recon isn't good, you'll likely fail, or worse—end up serving time and becoming Bubba's wife for a couple years. I can't say it enough—recon is critical.

The long standing popularity of 4chan has been due to the entirely anonymous setup. The site's anonymous community and culture has provoked media attention, in turn inciting larger audiences. On the other side of the spectrum is Facebook—popular for its connectivity and easily identifiable names. With the brush of keyboard stroke, you can be connected with your entire high school class in a matter of seconds.

Yes, you read that right—you can now get Google Maps back on your iPhone again. It may not be officially replacing Apple's notorious Maps app, but it sure is a sight for sore eyes.

Hello! This post is not about craft, it's about cyber bullying. If you ever had such an experience, that an unknown hacker was bullying you for no reason at all, please follow my words. Thank you! Step 1: Let All the People You Know That Your Are Being Harassed.

Hello! I want to share a few hints about staying literally cool when the temperature of the air outside rises incredibly. So, if you're in a very hot area, please continue reading!

Do the cops think you had too much too drink? Not on Playbook's Matt Bean's watch! Find out what to do if you get caught drunk in public from Former NYPD Detective Scott Androvic.

Computer pranks are some of the most insidious because computer are so expensive, necessary, and misunderstood by the general public. This video will show you how to take advantage of all of that by writing a quick script that will cause a computer's disc drive to open and close apparently of it's own free will. Great for messing with friends and coworkers at the office.

At Daily Mugshots, you will be able to save your own mug shot. The first thing that you will have to do is sign up for an account. You will need a Flash Player in order to use this site. After you have your account set up, you can take a picture from your computer. You can also upload pictures that you have taken elsewhere. When you save your picture, you will have to wait until it is finished processing. When the blue bar is filled, then it will be stored in your mug show.

Isn't it annoying when you want to check your Facebook or MySpace but you are at school and hit a big giant Websense blocker? Well, if you are stuck in a library or somewhere else where there are filters on your surf-ability, check out this tutorial for a useful hack.

Check out this awesome tip from CNET on getting FREE eBooks of the web and onto your Amazon Kindle for easy and cheap reading. They show you the exact process for getting free ebooks for your Kindle, so watch and learn. It's worth it!

HighQuality Tutorials demonstrates how to change your iPod Touch alpine default password. Changing the default password is useful when using your iPod Touch in a public setting to make it less vulnerable to hacking. To change the default password, first open up your internet connection and search for Putty. Download the Putty program. Open and run the Putty program. Your host name will be your IP address for your iPod Touch. Select port 22 and SSH and open up the program. Log in as root and c...

Contemplating divorce but not sure you're ready? The best way to deal with marital problems is to file for a legal separation. This tutorial will take you step by step through this difficult, emotional process.

Worried your canine might bite somebody? Afraid to take them on walks anymore because of what could happen if a child walks past you? Afraid of a lawsuit? These are the worries associated with overly aggressive dogs. But with proper training, an aggressive dog can be transformed into a well-behaved companion you'll love having at your side.

A Facebook page formatted specifically for non-profits can be created in a matter of minutes with this video tutorial from John Haydon. The first step you need to take is to search for any page. In this tutorial, Haydon searches for the page "Facebook Pages/Public Profiles" to use as the example. On the bottom left (of any Facebook page), you will notice that there is a link for "Create a Page for My Business." Click on that link, which allows you to begin the page creation process. Non-profi...

Is someone threatening, following, or preventing you from carrying on a normal, healthy safe life? Protect yourself from the threat of injury or physical harm by filing a restraining order. In this video, learn what steps are needed to file a restraining order.

With the growing popularity of digital downloads, it's important for aspiring musicians to have some sort of download available of their music. If you're an unsigned musician, selling your music on iTunes might seem daunting, but it's actually very easy! Learn how to do it in this video.

Separate restroom hygiene fact from fiction – here's how. You Will Need